Match the Azure networking service to the appropriate description.
To answer, drag the appropriate service from the column on the left to its description on the right. Each service may be used once, more than once, or not at all.
NOTE: Each correct match is worth one point.

Which Microsoft 365 feature can you use to restrict users from sending email messages that contain lists of customers and their associated credit card numbers?
Which Azure Active Directory (Azure AD) feature can you use to restrict Microsoft Intune-managed devices from accessing corporate resources?
What can you protect by using the information protection solution in the Microsoft 365 compliance center?
Which Microsoft Defender for Cloud metric displays the overall security health of an Azure subscription?
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

What are two reasons to deploy multiple virtual networks instead of using just one virtual network? Each correct answer presents a complete solution.
NOTE; Each correct selection is worth one point.
Which security feature is available in the free mode of Microsoft Defender for Cloud?
When security defaults are enabled for an Azure Active Directory (Azure AD) tenant, which two requirements are enforced? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Match the types of Conditional Access signals to the appropriate definitions.
To answer, drag the appropriate Conditional Access signal type from the column on the left to its definition on the right. Each signal type may be used once, more than once, or not at all.
NOTE: Each correct match is worth one point.

Which two types of resources can be protected by using Azure Firewall? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

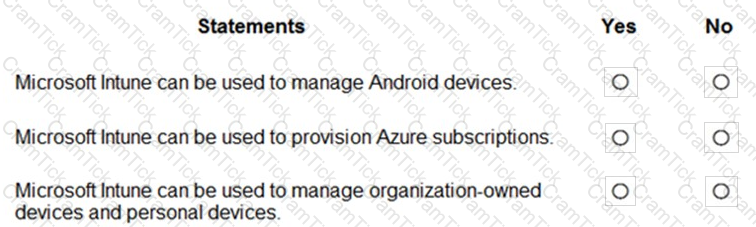
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point
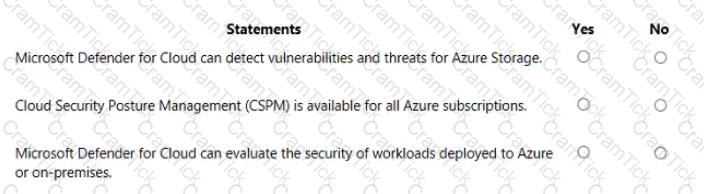
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
What feature in Microsoft Defender for Endpoint provides the first line of defense against cyberthreats by reducing the attack surface?
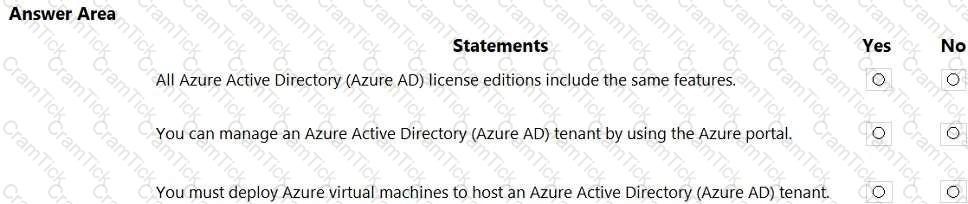
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
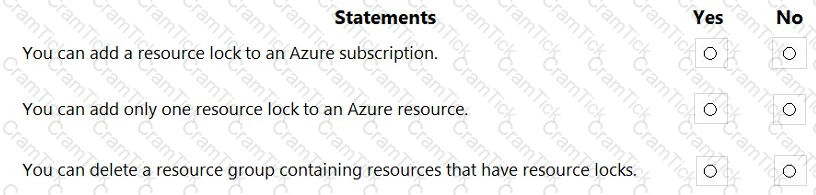
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Which Azure Active Directory (Azure AD) feature can you use to evaluate group membership and automatically remove users that no longer require membership in a group?
When you enable Azure AD Multi-Factor Authentication (MFA), how many factors are required for authentication?
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
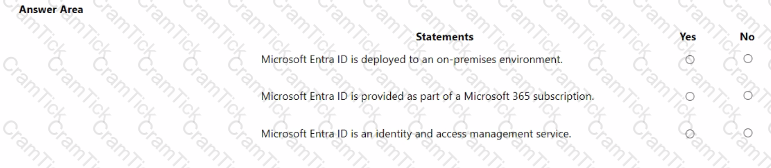
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
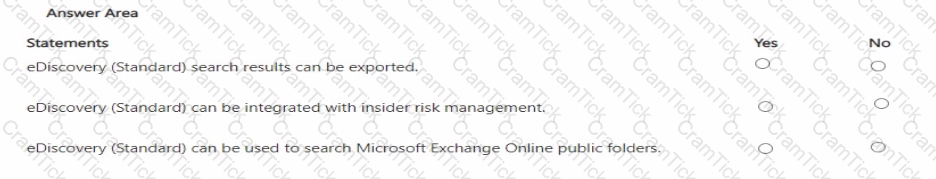
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

What are three uses of Microsoft Cloud App Security? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
Which feature provides the extended detection and response (XDR) capability of Azure Sentinel?
You have a Microsoft 365 E3 subscription.
You plan to audit user activity by using the unified audit log and Basic Audit.
For how long will the audit records be retained?
Which two cards are available in the Microsoft 365 Defender portal? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point.
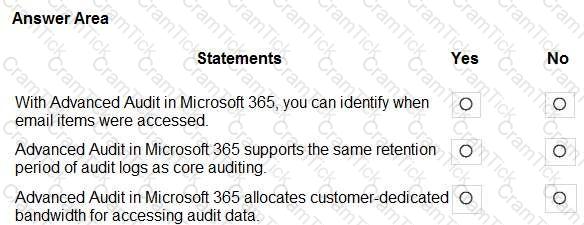
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point

For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

What should you use in the Microsoft 365 security center to view security trends and track the protection status of identities?
Which Microsoft 365 feature can you use to restrict communication and the sharing of information between members of two departments at your organization?
Microsoft Certified: Security Compliance and Identity Fundamentals | SC-900 Exam Topics | SC-900 Questions answers | SC-900 Test Prep | Microsoft Security Compliance and Identity Fundamentals Exam Questions PDF | SC-900 Online Exam | SC-900 Practice Test | SC-900 PDF | SC-900 Test Questions | SC-900 Study Material | SC-900 Exam Preparation | SC-900 Valid Dumps | SC-900 Real Questions | Microsoft Certified: Security Compliance and Identity Fundamentals SC-900 Exam Questions


