Users have reported an issue when they are trying to access a server on your network. The requests aren’t taking the expected route. You discover that there are two different static routes on the firewall for the server. What is used to determine which route has priority?
A consultant advises a client on designing an explicit Web Proxy deployment on PAN-OS 11 0 The client currently uses RADIUS authentication in their environment
Which two pieces of information should the consultant provide regarding Web Proxy authentication? (Choose two.)
An administrator is troubleshooting intermittent connectivity problems with a user's GlobalProtect connection. Packet captures at the firewall reveal missing UDP packets, suggesting potential packet loss on the connection. The administrator aims to resolve the issue by enforcing an SSL tunnel over TCP specifically for this user.
What configuration change is necessary to implement this troubleshooting solution for the user?
Which tool can gather information about the application patterns when defining a signature for a custom application?
A customer wants to deploy User-ID on a Palo Alto Network NGFW with multiple vsys. One of the vsys will support a GlobalProtect portal and gateway. the customer uses Windows
An administrator pushes a new configuration from Panorama to a par of firewalls that are configured as an active/passive HA pair. Which NGFW receives the from Panorama?
An administrator has configured a pair of firewalls using high availability in Active/Passive mode. Link and Path Monitoring is enabled with the Failure Condition set to "any." There is one link group configured containing member interfaces ethernet1/1 and ethernet1/2 with a Group Failure Condition set to "all."
Which HA state will the Active firewall go into if ethernet1/1 link goes down due to a failure?'
An administrator troubleshoots an issue that causes packet drops.
Which log type will help the engineer verify whether packet buffer protection was activated?
An administrator is receiving complaints about application performance degradation. After checking the ACC, the administrator observes that there is an excessive amount of VoIP traffic.
Which three elements should the administrator configure to address this issue? (Choose three.)
Which Panorama mode should be used so that all logs are sent to. and only stored in. Cortex Data Lake?
An engineer troubleshooting a VPN issue needs to manually initiate a VPN tunnel from the CLI Which CLI command can the engineer use?
Based on the graphic which statement accurately describes the output shown in the Server Monitoring panel?
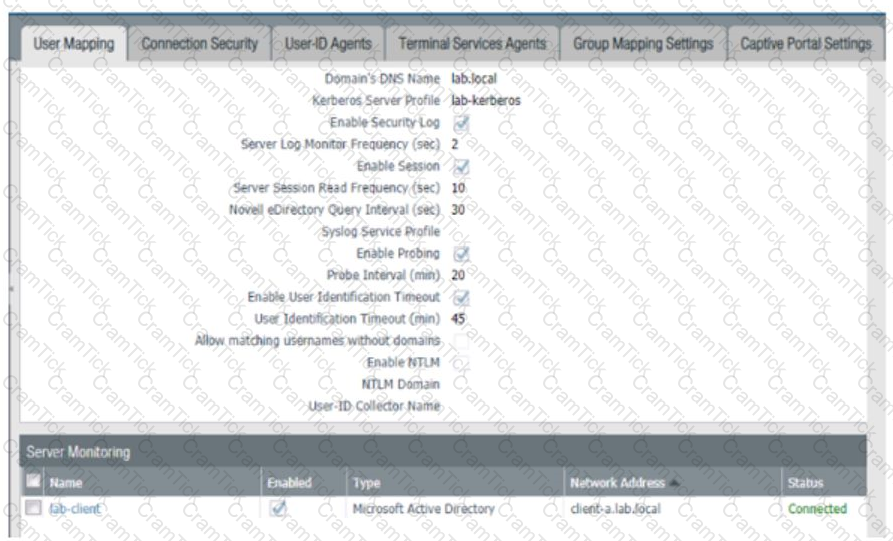
Why are external zones required to be configured on a Palo Alto Networks NGFW in an environment with multiple virtual systems?
Which function does the HA4 interface provide when implementing a firewall cluster which contains firewalls configured as active-passive pairs?
Which DoS Protection Profile detects and prevents session exhaustion attacks against specific destinations?
Which three multi-factor authentication methods can be used to authenticate access to the firewall? (Choose three.)
What happens, by default, when the GlobalProtect app fails to establish an IPSec tunnel to the GlobalProtect gateway?
If an administrator wants to apply QoS to traffic based on source, what must be specified in a QoS policy rule?
An administrator is informed that the engineer who previously managed all the VPNs has left the company. According to company policies the administrator must update all the IPSec VPNs with new pre-shared keys Where are the pre-shared keys located on the firewall?
A firewall administrator has been tasked with ensuring that all Panorama configuration is committed and pushed to the devices at the end of the day at a certain time. How can they achieve this?
An administrator is required to create an application-based Security policy rule to allow Evernote. The Evernote application implicitly uses SSL and web browsing.
What is the minimum the administrator needs to configure in the Security rule to allow only Evernote?
Four configuration choices are listed, and each could be used to block access to a specific URL.
If you configured each choice to block the same URL, then which choice would be evaluated last in the processing order to block access to the URL?
Which action can be taken to immediately remediate the issue of application traffic with a valid use case triggering the decryption log message, "Received fatal alert UnknownCA from client"?
A security engineer needs to mitigate packet floods that occur on a RSF servers behind the internet facing interface of the firewall. Which Security Profile should be applied to a policy to prevent these packet floods?
An organization wants to begin decrypting guest and BYOD traffic.
Which NGFW feature can be used to identify guests and BYOD users, instruct them how to download and install the CA certificate, and clearly notify them that their traffic will be decrypted?
Which two items must be configured when implementing application override and allowing traffic through the firewall? (Choose two.)
All firewall at a company are currently forwarding logs to Palo Alto Networks log collectors. The company also wants to deploy a sylog server and forward all firewall logs to the syslog server and to the log collectors. There is known logging peak time during the day, and the security team has asked the firewall engineer to determined how many logs per second the current Palo Alto Networking log processing at that particular time. Which method is the most time-efficient to complete this task?
Which two profiles should be configured when sharing tags from threat logs with a remote User-ID agent? (Choose two.)
What would allow a network security administrator to authenticate and identify a user with a new BYOD-type device that is not joined to the corporate domain?
A company requires that a specific set of ciphers be used when remotely managing their Palo Alto Networks appliances.
Which profile should be configured in order to achieve this?
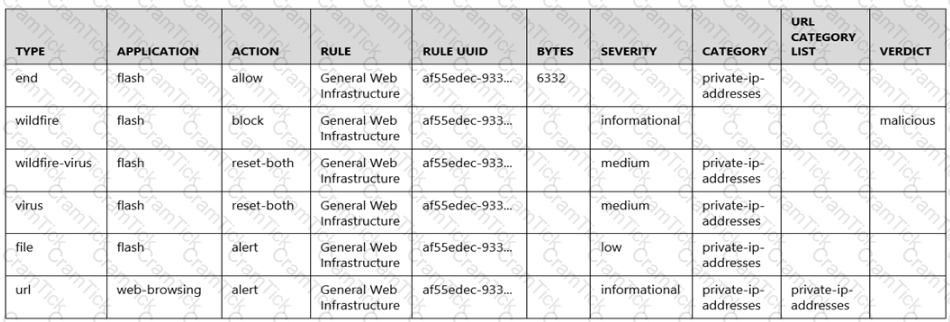
Given the following snippet of a WildFire submission log, did the end user successfully download a file?
An administrator needs to gather information about the CPU utilization on both the management plane and the data plane. Where does the administrator view the desired data?
An administrator needs to build Security rules in a Device Group that allow traffic to specific users and groups defined in Active Directory. What must be configured in order to select users and groups for those rules from Panorama? The Security rules must be targeted to a firewall in the device group and have Group Mapping configured.
When backing up and saving configuration files, what is achieved using only the firewall and is not available in Panorama?
A firewall administrator has confirm reports of a website is not displaying as expected, and wants to ensure that decryption is not causing the issue. Which three methods can the administrator use to determine if decryption is causing the website to fail? (Choose three.)
A firewall administrator configures the HIP profiles on the edge firewall where GlobalProtect is enabled, and adds the profiles to security rules. The administrator wants to redistribute the HIP reports to the data center firewalls to apply the same access restrictions using HIP profiles. However, the administrator can only see the HIP match logs on the edge firewall but not on the data center firewall
What are two reasons why the administrator is not seeing HIP match logs on the data center firewall? (Choose two.)
A security team has enabled real-time WildFire signature lookup on all its firewalls. Which additional action will further reduce the likelihood of newly discovered malware being allowed through the firewalls?
A network administrator is trying to prevent domain username and password submissions to phishing sites on some allowed URL categories
Which set of steps does the administrator need to take in the URL Filtering profile to prevent credential phishing on the firewall?
A firewall administrator is configuring an IPSec tunnel between a company's HQ and a remote location. On the HQ firewall, the interface used to terminate the IPSec tunnel has a static IP. At the remote location, the interface used to terminate the IPSec tunnel has a DHCP assigned IP address.
Which two actions are required for this scenario to work? (Choose two.)
An engineer is configuring a firewall with three interfaces:
• MGT connects to a switch with internet access.
• Ethernet1/1 connects to an edge router.
• Ethernet1/2 connects to a visualization network.
The engineer needs to configure dynamic updates to use a dataplane interface for internet traffic. What should be configured in Setup > Services > Service Route Configuration to allow this traffic?
After implementing a new NGFW, a firewall engineer sees a VoIP traffic issue going through the firewall After troubleshooting the engineer finds that the firewall performs NAT on the voice packets payload and opens dynamic pinholes for media ports
What can the engineer do to solve the VoIP traffic issue?
A customer wants to enhance the protection provided by their Palo Alto Networks NGFW deployment to cover public-facing company-owned domains from misconfigurations that point records to third-party sources. Which two actions should the network administrator perform to achieve this goal? (Choose two)
Which type of policy in Palo Alto Networks firewalls can use Device-ID as a match condition?
An administrator is tasked to provide secure access to applications running on a server in the company's on-premises datacenter.
What must the administrator consider as they prepare to configure the decryption policy?
Which two actions must an engineer take to configure SSL Forward Proxy decryption? (Choose two.)
Which three authentication types can be used to authenticate users? (Choose three.)
An administrator needs to assign a specific DNS server to an existing template variable. Where would the administrator go to edit a template variable at the device level?
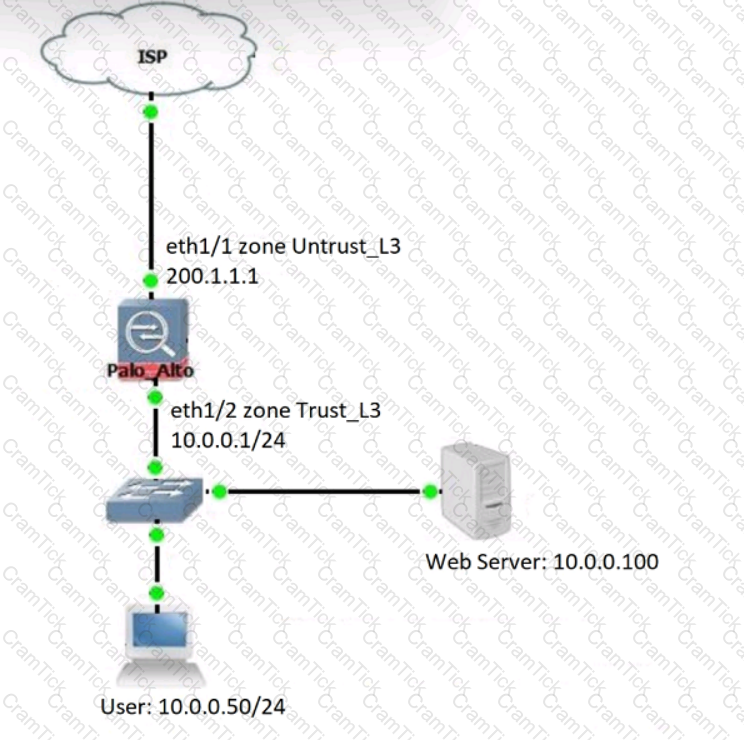
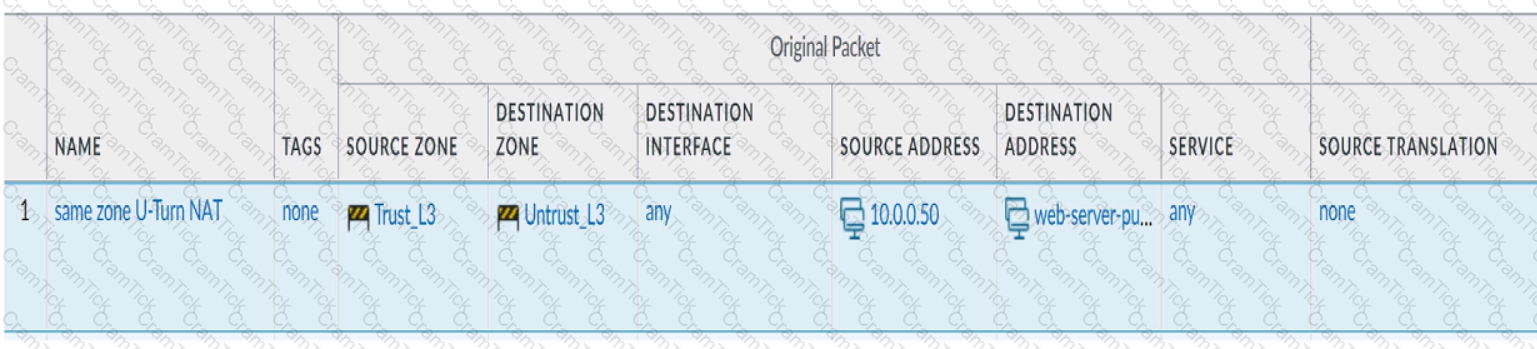
Review the information below. A firewall engineer creates a U-NAT rule to allow users in the trust zone access to a server in the same zone by using an external,
public NAT IP for that server.
Given the rule below, what change should be made to make sure the NAT works as expected?
An administrator receives the following error message:
"IKE phase-2 negotiation failed when processing Proxy ID. Received local id 192.168 33 33/24 type IPv4 address protocol 0 port 0, received remote id 172.16 33.33/24 type IPv4 address protocol 0 port 0."
How should the administrator identify the root cause of this error message?
An engineer reviews high availability (HA) settings to understand a recent HA failover event. Review the screenshot below.
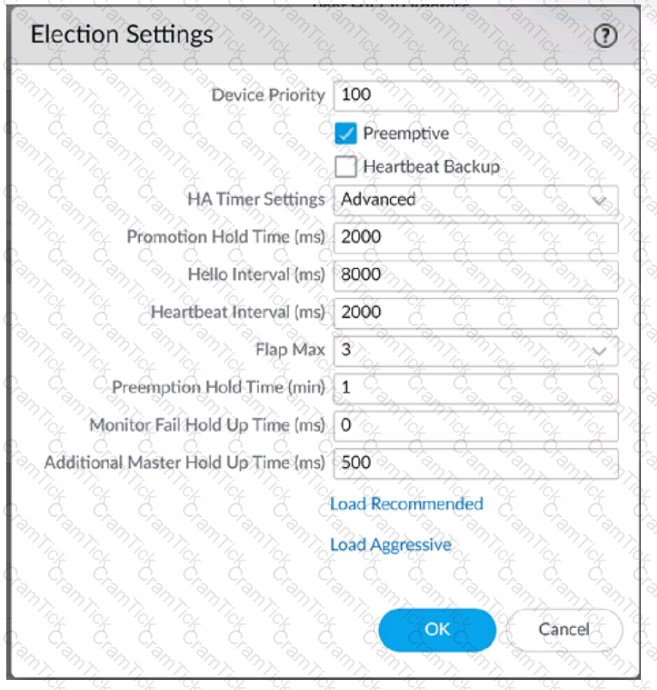
Which timer determines the frequency at which the HA peers exchange messages in the form of an ICMP (ping)
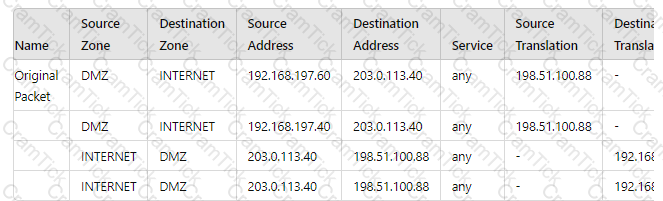
A new application server 192.168.197.40 has been deployed in the DMZ. There are no public IP addresses available resulting in the server sharing MAT IP 198 51 100 B8 with another OMZ serve that uses IP address 192 168 19? 60 Firewall security and NAT rules have been configured The application team has confirmed mat the new server is able to establish a secure connection to an external database with IP address 203.0.113.40. The database team reports that they are unable to establish a secure connection to 196 51 100 88 from 203.0.113.40 However it confirm a successful prig test to 198 51 100 88 Referring to the MAT configuration and traffic logs provided how can the firewall engineer resolve the situation and ensure inbound and outbound connections work concurrently for both DMZ servers?
An administrator has a Palo Alto Networks NGFW. All security subscriptions and decryption are enabled and the system is running close to its resource limits.
Knowing that using decryption can be resource-intensive, how can the administrator reduce the load on the firewall?
What must be taken into consideration when preparing a log forwarding design for all of a customer’s deployed Palo Alto Networks firewalls?
An engineer is configuring Packet Buffer Protection on ingress zones to protect from single-session DoS attacks.
Which sessions does Packet Buffer Protection apply to?
Which three methods are supported for split tunneling in the GlobalProtect Gateway? (Choose three.)
When an engineer configures an active/active high availability pair, which two links can they use? (Choose two)
A firewall engineer at a company is researching the Device Telemetry feature of PAN-OS. Which two aspects of the feature require further action for the company to remain compliant with local laws regarding privacy and data storage? (Choose two.)
Refer to the exhibit.
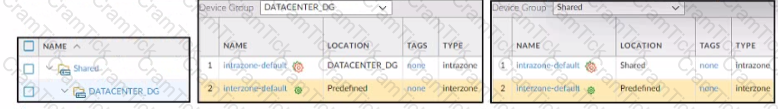
Based on the screenshots above what is the correct order in which the various rules are deployed to firewalls inside the DATACENTER_DG device group?
A firewall administrator is investigating high packet buffer utilization in the company firewall. After looking at the threat logs and seeing many flood attacks coming from a single source that are dropped by the firewall, the administrator decides to enable packet buffer protection to protect against similar attacks.
The administrator enables packet buffer protection globally in the firewall but still sees a high packet buffer utilization rate.
What else should the administrator do to stop packet buffers from being overflowed?
A network security administrator wants to inspect HTTPS traffic from users as it egresses through a firewall to the Internet/Untrust zone from trusted network zones.
The security admin wishes to ensure that if users are presented with invalid or untrusted security certificates, the user will see an untrusted certificate warning.
What is the best choice for an SSL Forward Untrust certificate?
You are auditing the work of a co-worker and need to verify that they have matched the Palo Alto Networks Best Practices for Anti-Spyware Profiles.
For which three severity levels should single-packet captures be enabled to meet the Best Practice standard? (Choose three.)
Panorama is being used to upgrade the PAN-OS version on a pair of firewalls in an active/passive high availability (HA) configuration. The Palo Alto Networks best practice upgrade steps have been completed in Panorama (Panorama upgraded, backups made, content updates, and disabling "Preemptive" pushed), and the firewalls are ready for upgrade. What is the next best step to minimize downtime and ensure a smooth transition?
When using certificate authentication for firewall administration, which method is used for authorization?
An administrator is troubleshooting why video traffic is not being properly classified.
If this traffic does not match any QoS classes, what default class is assigned?
An engineer is configuring secure web access (HTTPS) to a Palo Alto Networks firewall for management.
Which profile should be configured to ensure that management access via web browsers is encrypted with a trusted certificate?
When a new firewall joins a high availability (HA) cluster, the cluster members will synchronize all existing sessions over which HA port?
A firewall engineer creates a source NAT rule to allow the company's internal private network 10.0.0.0/23 to access the internet. However, for security reasons, one server in that subnet (10.0.0.10/32) should not be allowed to access the internet, and therefore should not be translated with the NAT rule.
Which set of steps should the engineer take to accomplish this objective?
A firewall architect is attempting to install a new Palo Alto Networks NGFW. The company has previously had issues moving all administrative functions onto a data plane interface to meet the design limitations of the environment. The architect is able to access the device for HTTPS and SSH; however, the NGFW can neither validate licensing nor get updates. Which action taken by the architect will resolve this issue?
A network administrator is troubleshooting an issue with Phase 2 of an IPSec VPN tunnel The administrator determines that the lifetime needs to be changed to match the peer. Where should this change be made?
Users are intermittently being cut off from local resources whenever they connect to GlobalProtect. After researching, it is determined that this is caused by an incorrect setting on one of the NGFWs. Which action will resolve this issue?
Refer to the diagram. Users at an internal system want to ssh to the SSH server. The server is configured to respond only to the ssh requests coming from IP 172.16.16.1.
In order to reach the SSH server only from the Trust zone, which Security rule and NAT rule must be configured on the firewall?
Which three external authentication services can the firewall use to authenticate admins into the Palo Alto Networks NGFW without creating administrator account on the firewall? (Choose three.)
To ensure that a Security policy has the highest priority, how should an administrator configure a Security policy in the device group hierarchy?
A network security administrator has been tasked with deploying User-ID in their organization.
What are three valid methods of collecting User-ID information in a network? (Choose three.)
Which two policy components are required to block traffic in real time using a dynamic user group (DUG)? (Choose two.)
An administrator plans to install the Windows User-ID agent on a domain member system.
What is a best practice for choosing where to install the User-ID agent?
An administrator needs to build Security rules in a Device Group that allow traffic to specific users and groups defined in Active Directory.
What must be configured in order to select users and groups for those rules from Panorama?
An administrator configures a preemptive active-passive high availability (HA) pair of firewalls and configures the HA election settings on firewall-02 with a device priority value of 100, and firewall-01 with a device priority value of 90.
When firewall-01 is rebooted, is there any action taken by the firewalls?
An engineer is monitoring an active/active high availability (HA) firewall pair.
Which HA firewall state describes the firewall that is currently processing traffic?
An enterprise Information Security team has deployed policies based on AD groups to restrict user access to critical infrastructure systems. However, a recent phishing campaign against the organization has prompted Information Security to look for more controls that can secure access to critical assets. For users that need to access these systems. Information Security wants to use PAN-OS multi-factor authentication (MFA) integration to enforce MFA.
What should the enterprise do to use PAN-OS MFA?
A firewall engineer reviews the PAN-OS GlobalProtect application and sees that it implicitly uses web-browsing and depends on SSL.
When creating a new rule, what is needed to allow the application to resolve dependencies?
When creating a Policy-Based Forwarding (PBF) policy, which two components can be used? (Choose two.)
An administrator wants to add User-ID information for their Citrix MetaFrame Presentation Server (MPS) users.
Which option should the administrator use?
A network security administrator wants to enable Packet-Based Attack Protection in a Zone Protection profile. What are two valid ways to enable Packet-Based Attack Protection? (Choose two.)
An auditor is evaluating the configuration of Panorama and notices a discrepancy between the Panorama template and the local firewall configuration. When overriding the firewall configuration pushed from Panorama, what should you consider?
Information Security is enforcing group-based policies by using security-event monitoring on Windows User-ID agents for IP-to-User mapping in the network. During the rollout, Information Security identified a gap for users authenticating to their VPN and wireless networks.
Root cause analysis showed that users were authenticating via RADIUS and that authentication events were not captured on the domain controllers that were being monitored Information Security found that authentication events existed on the Identity Management solution (IDM). There did not appear to be direct integration between PAN-OS and the IDM solution
How can Information Security extract and learn iP-to-user mapping information from authentication events for VPN and wireless users?
Forwarding of which two log types is configured in Device > Log Settings? (Choose two.)
A firewall administrator has configured User-ID and deployed GlobalProtect, but there is no User-ID showing in the traffic logs.
How can the administrator ensure that User-IDs are populated in the traffic logs?
A network engineer has discovered that asymmetric routing is causing a Palo Alto Networks firewall to drop traffic. The network architecture cannot be changed to correct this.
Which two actions can be taken on the firewall to allow the dropped traffic permanently? (Choose two.)
Palo Alto Certifications and Accreditations | PCNSE Questions Answers | PCNSE Test Prep | Palo Alto Networks Certified Security Engineer (PCNSE) PAN-OS 10.0 Questions PDF | PCNSE Online Exam | PCNSE Practice Test | PCNSE PDF | PCNSE Test Questions | PCNSE Study Material | PCNSE Exam Preparation | PCNSE Valid Dumps | PCNSE Real Questions | Palo Alto Certifications and Accreditations PCNSE Exam Questions


