To manage automated onboarding rules, a CyberArk user must be a member of which group?
You are logging into CyberArk as the Master user to recover an orphaned safe.
Which items are required to log in as Master?
You received a notification from one of your CyberArk auditors that they are missing Vault level audit permissions. You confirmed that all auditors are missing the Audit Users Vault permission.
Where do you update this permission for all auditors?
Which option in the PrivateArk client is used to update users' Vault group memberships?
You receive this error:
“Error in changepass to user domain\user on domain server(\domain.(winRc=5) Access is denied.”
Which root cause should you investigate?
To use PSM connections while in the PVWA, what are the minimum safe permissions a user or group will need?
Which of the Following can be configured in the Master Poky? Choose all that apply.
Which CyberArk group does a user need to be part of to view recordings or live monitor sessions?
An auditor initiates a live monitoring session to PSM server to view an ongoing live session. When the auditor’s machine makes an RDP connection the PSM server, which user will be used?
You have been asked to limit a platform called "Wmdows_Servers" to safes called "WindowsDCT and "WindowsDC2" The platform must not be assigned to any other safe What is the correct way to accomplish this?
You are installing HTML5 gateway on a Linux host using the RPM provided. After installing the Tomcat webapp, what is the next step in the installation process?
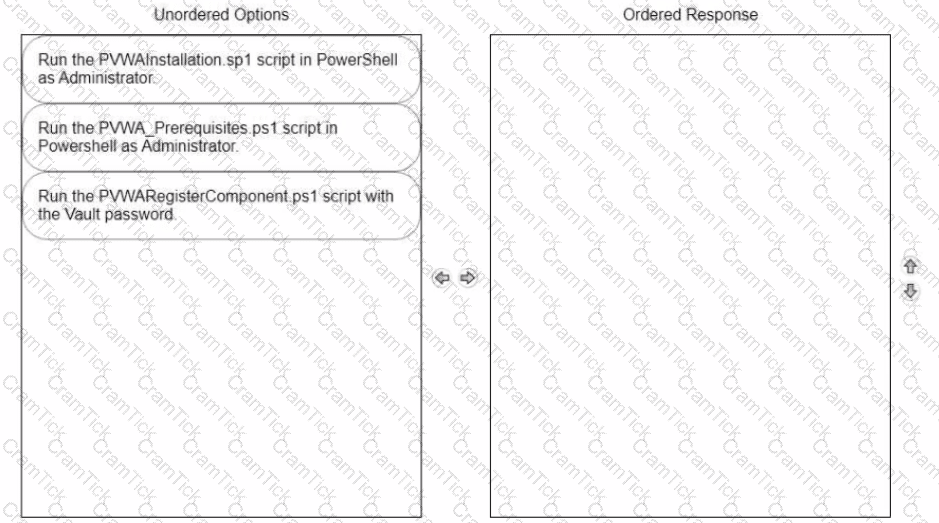
Arrange the steps to install the Password Vault Web Access (PVWA) in the correct sequence
Which Cyber Are components or products can be used to discover Windows Services or Scheduled Tasks that use privileged accounts? Select all that apply.
Which utilities could you use to change debugging levels on the vault without having to restart the vault. Select all that apply.
After installing the first PSM server and before installing additional PSM servers you must ensure the user performing the installation is not a direct owner of which safe?
A user is receiving the error message “ITATS006E Station is suspended for User jsmith” when attempting to sign into the Password Vault Web Access (PVWA). Which utility would a Vault administrator use to correct this problem?
It is possible to restrict the time of day, or day of week that a [b]verify[/b] process can occur
Can the 'Connect' button be used to initiate an SSH connection, as root, to a Unix system when SSH access for root is denied?
Match the Status of Service on a DR Vault to what is displayed when it is operating normally in Replication mode.

Ad-Hoc Access (formerly Secure Connect) provides the following features. Choose all that apply.
Which option in the Private Ark client is used to update users’ Vault group memberships?
If the AccountUploader Utility is used to create accounts with SSH keys, which parameter do you use to set the full or relative path of the SSH private key file that will be attached to the account?
By default, members of which built-in groups will be able to view and configure Automatic Remediation and Session Analysis and Response in the PVWA?
As long as you are a member of the Vault Admins group, you can grant any permission on any safe that you have access to.
Which parameter controls how often the CPM looks for accounts that need to be changed from recently completed Dual control requests.
In your organization the “click to connect” button is not active by default.
How can this feature be activated?
A customer installed multiple PVWAs in the production environment behind a load balancer VIP. They subsequently observed that all incoming traffic from the load balancer VIP goes to only one PVWA, even though all the PVWAs are up and running. What could be the likely cause of this situation?
It is possible to control the hours of the day during which a user may log into the vault.
Which type of automatic remediation can be performed by the PTA in case of a suspected credential theft security event?
A user requested access to view a password secured by dual-control and is unsure who to contact to expedite the approval process. The Vault Admin has been asked to look at the account and identify who can approve their request.
What is the correct location to identify users or groups who can approve?
For a safe with Object Level Access enabled you can turn off Object Level Access Control when it no longer needed on the safe.
Vault admins must manually add the auditors group to newly created safes so auditors will have sufficient access to run reports.
CyberArk implements license limits by controlling the number and types of users that can be provisioned in the vault.
Your customer, ACME Corp, wants to store the Safes Data in Drive D instead of Drive C.
Which file should you edit?
The Vault administrator can change the Vault license by uploading the new license to the system Safe.
Which components can connect to a satellite Vault in distributed Vault architecture?
You need to move a platform from using PMTerminal to using Terminal Plugin Controller (TPC) What must you do?
Your organization requires all passwords be rotated every 90 days.
Where can you set this regulatory requirement?
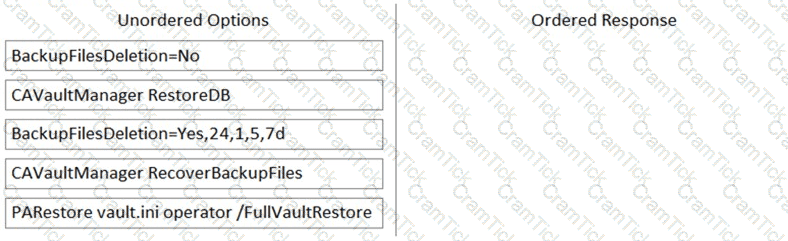
Arrange the steps to restore a Vault using PARestore for a Backup in the correct sequence.
You have been asked to turn off the time access restrictions for a safe.
Where is this setting found?
You are installing PSM for SSH with AD-Bridge in CyberArkSSHD mode for your customer. ACME Corp What do you need to install to meet your customer's needs? (Choose 2)
As vault Admin you have been asked to configure LDAP authentication for your organization's CyberArk users. Which permissions do you need to complete this task?
A user with administrative privileges to the vault can only grant other users privileges that he himself has.


