An OT administrator has configured FSSO and local firewall authentication. A user who is part of a user group is not prompted from credentials during authentication.
What is a possible reason?
An OT network architect needs to secure control area zones with a single network access policy to provision devices to any number of different networks.
On which device can this be accomplished?
With the limit of using one firewall device, the administrator enables multi-VDOM on FortiGate to provide independent multiple security domains to each ICS network. Which statement ensures security protection is in place for all ICS networks?
Refer to the exhibit.

PLC-3 and CLIENT can send traffic to PLC-1 and PLC-2. FGT-2 has only one software switch (SSW-1) connecting both PLC-3 and CLIENT. PLC-3 and CLIENT can send traffic to each other at the Layer 2 level.
What must the OT admin do to prevent Layer 2-level communication between PLC-3 and CLIENT?
An OT supervisor has configured LDAP and FSSO for the authentication. The goal is that all the users be authenticated against passive authentication first and, if passive authentication is not successful, then users should be challenged with active authentication.
What should the OT supervisor do to achieve this on FortiGate?
Refer to the exhibit.
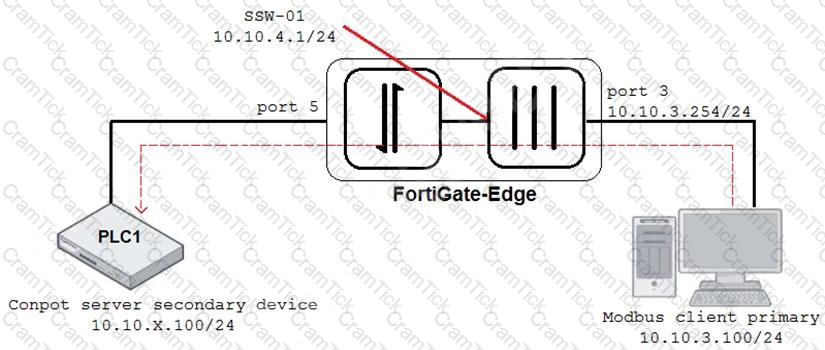
An OT architect has implemented a Modbus TCP with a simulation server Conpot to identify and control the Modus traffic in the OT network. The FortiGate-Edge device is configured with a software switch interface ssw-01.
Based on the topology shown in the exhibit, which two statements about the successful simulation of traffic between client and server are true? (Choose two.)
What are two critical tasks the OT network auditors must perform during OT network risk assessment and management? (Choose two.)
Refer to the exhibit.
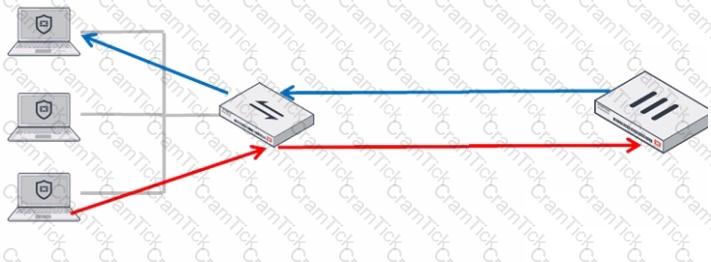
In order for a FortiGate device to act as router on a stick, what configuration must an OT network architect implement on FortiGate to achieve inter-VLAN routing?
Which three common breach points can be found in a typical OT environment? (Choose three.)
The OT network analyst run different level of reports to quickly explore failures that could put the network at risk. Such reports can be about device performance. Which FortiSIEM reporting method helps to identify device failures?
Which type of attack posed by skilled and malicious users of security level 4 (SL 4) of IEC 62443 is designed to defend against intentional attacks?
Refer to the exhibit.
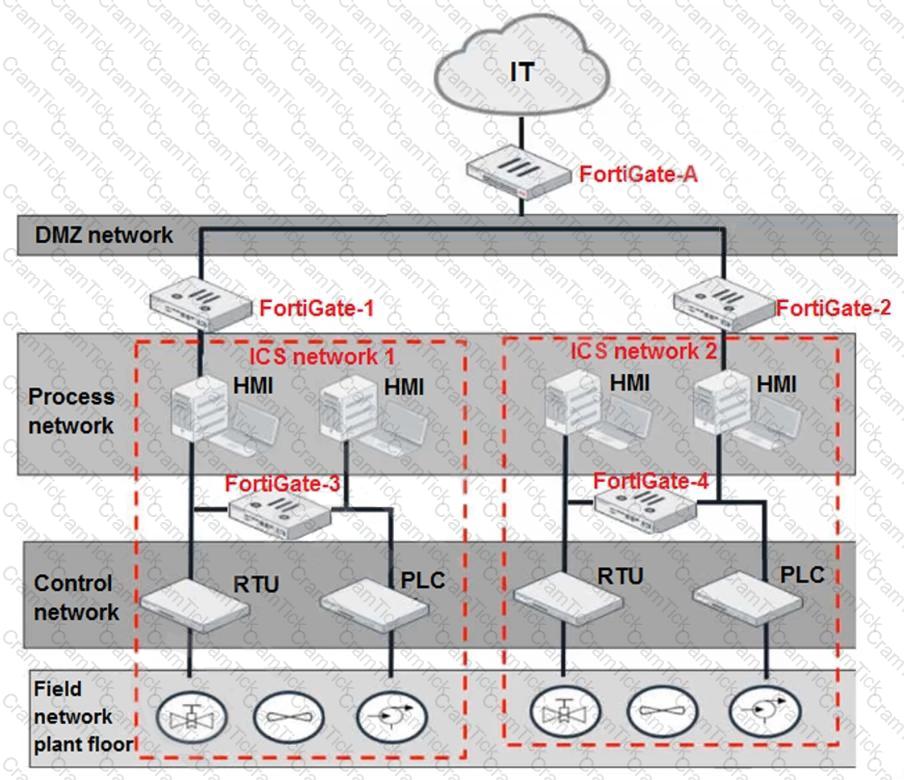
Based on the topology designed by the OT architect, which two statements about implementing OT security are true? (Choose two.)
Refer to the exhibit.
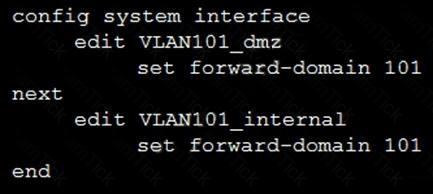
Given the configurations on the FortiGate, which statement is true?


