Click the Exhibit button.

Which two statements are correct about the partial policies shown in the exhibit? (Choose two.)
You want to implement user-based enforcement of security policies without the requirement of certificates and supplicant software.
Which security feature should you implement in this scenario?
You want to verify the peer before IPsec tunnel establishment.
What would be used as a final check in this scenario?
When operating in packet mode, which two services are available on the SRX Series device? (Choose two.)
Your company is adding IP cameras to your facility to increase physical security. You are asked to help protect these loT devices from becoming zombies in a DDoS attack.
Which Juniper ATP feature should you configure to accomplish this task?
You want to provide remote access to an internal development environment for 10 remote developers.
Which two components are required to implement Juniper Secure Connect to satisfy this requirement? (Choose two.)
Which two statements are correct about the default behavior on SRX Series devices? (Choose two.)
Which three Web filtering deployment actions are supported by Junos? (Choose three.)
You are assigned a project to configure SRX Series devices to allow connections to your webservers. The webservers have a private IP address, and the packets must use NAT to be accessible from the Internet. The webservers must use the same address for both connections from the Internet and communication with update servers.
Which NAT type must be used to complete this project?
Which two IKE Phase 1 configuration options must match on both peers to successfully establish a tunnel? (Choose two.)
Which Juniper Networks solution uses static and dynamic analysis to search for day-zero malware threats?
You are configuring an SRX Series device. You have a set of servers inside your private network that need one-to-one mappings to public IP addresses.
Which NAT configuration is appropriate in this scenario?
Which two statements are correct about the integrated user firewall feature?(Choose two.)
Which two IPsec hashing algorithms are supported on an SRX Series device? (Choose two.)
Click the Exhibit button.
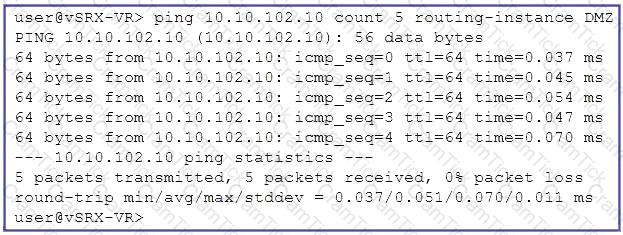
Referring to the exhibit, which two statements are correct about the ping command? (Choose two.)
Which two statements are correct about IPsec security associations? (Choose two.)
Which two features are included with UTM on an SRX Series device? (Choose two.)


