You work as a Software Developer for ManSoft Inc. The company has several branches worldwide. The company uses Visual Studio.NET 2005 as its application development platform. You create an application that will be used by all the branches of the company. You use the Regex class in the application to validate some strings. You want to search an input string for an occurrence of a regular expression. Which of the following methods of the Regex class will you use to accomplish the task?
You work as a Web Application Developer for SunInfo Inc. The company uses Visual Studio 2008 as its application development platform. You create a Web application using .NET Framework 3.5. You use foreach loops to retrieve data from a collection. Now, you want to use LINQ queries instead of foreach loops. Choose the advantages of using LINQ queries over foreach loops.
You work as a Software Developer for ABC Inc. You create an ASP.NET Web application named MyWebApplication. You want to provide secure access to company's customers. You want to enable users to access the site from any browser by providing their user name and password. Which of the following authentication methods will you use to accomplish this task?
You work as a Software Developer for ABC Inc. The company has several branches worldwide. The company uses Visual Studio .NET 2005 as its application development platform. You have received a file in ASCII encoded from one of the company's branch. Therefore, you are required to decode the file encoded in ACSII. Which of the following decoding types will you use to get the correct results?
Each correct answer represents a complete solution. Choose two.
Allen works as a Software Developer for ABC Inc. The company uses Visual Studio.NET as its application development platform. He creates an application using the .NET Framework.. He writes the following code segment in the application:
01 class gClass
02 {
03 public gClass(int k)
04 {
05 //Write code here
06 }
07 }
08 public class gSub : gClass
09 {
10 public static void Main(String[] argv)
11 {
12 gSub gs=new gSub(20);
13 }
14 gSub(int j):base(j)
15 {
16 //Write Code here
17 }
18 gSub(string st, int j):this(j)
19 {
20 gClass ss=new gClass();
21 }
22 }
When you execute the above code segment, you get an error at line 20. Which of the following code segments will he place at line 20 to execute the code successfully?
Each correct answer represents a complete solution. Choose all that apply.
You work as a Software Developer for ABC Inc. The company uses Visual Studio .NET as its application development platform. You create the definition for a Car class by using the following code segment:
public class Car {
[XmlAttribute(AttributeName = "category")]
public string CarType;
public string model;
[XmlIgnore]
public int year;
[XmlElement(ElementName = "mileage")]
public int miles;
public ConditionType condition;
public Car() {
}
public enum ConditionType {
[XmlEnum("Poor")] BelowAverage,
[XmlEnum("Good")] Average,
[XmlEnum("Excellent")] AboveAverage
}}
You create an instance of the Car class. You fill the public fields of the Car class as shown in the table below:
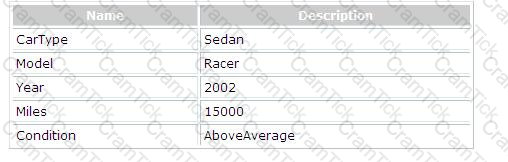
You are required to recognize the XML block that is produced by the Car class after serialization. Which of the following XML blocks represents the output of serializing the Car class?
You work as an ADO.NET Application Developer for ABC Inc. The company uses Microsoft Visual Studio .NET 2008 as its application development platform. You create an ADO.NET application by using .NET Framework 3.5. You are using the System.Linq.Expressions namespace to represent the code expression as objects in the form of expression trees. You want to initialize the members of a newly created object. What will you do to accomplish the task?
Allen works as a Software Developer for ABC Inc. He develops a Windows application. He adds a form to the application named Form1, which contains a Label control named Label1. A text file named File1.txt contains a list of products. File1.txt is located in the application directory. Each product name is listed in a new line in File1.txt. Allen wants to retrieve a list of products from File1.txt and display it in Label1. He adds the following code to the application:
1. StreamReader Reader1 = new StreamReader((Stream)File.OpenText(Server.MapPath
("File1.txt")));
2. Stream MyStream;
3. string InputString;
4. // Insert statement here.
5. while (InputString != null)
6. {
7. Label1.Text = String.Format("{0}{1}", Label1.Text, InputString);
8. Reader1.ReadLine();
9. }
10. Reader1.Close();
Which of the following statements will Allen add at line 4 to accomplish the task?
You work as a Software Developer for ABC Inc. You create a Web page named MyWebPage that displays detailed information of a registered user. The page contains a TextBox Web server control that requires the RangeValidator validation control to validate whether the user has entered the correct date of birth. A validation error message is displayed if the user has entered the value, which is greater than the date of registration. However, you want to ensure that the validation control on the Web page does not occupy any space, but share the same location for the display of error messages on the Web page. You also want to ensure that the layout of the Web page is changed when the error message is displayed. Which of the following actions will you take to accomplish the task?
Allen works as a Software Developer for ABC Inc. The company uses Visual Studio.NET as its application development platform. He creates an application using .NET Framework. He wants to encrypt all his e-mails that he sends to anyone. Which of the following will he use to accomplish the task?
You work as an Application Developer for ABC Inc. You are assigned with developing a Web site that will handle information related to monthly sales of the company. You wish to secure the Web site so that only employees of the Accounts department can view the Web pages. You need to create roles for the employees of this department. The user account information will be stored in a SQL Server database named Database. You decide to do all this by using the Web Site Administration Tool. Which of the following types of security will you use to accomplish the task?
Allen works as a Software Developer for ManSoft Inc. The company uses Visual Studio.NET as its application development platform. He creates an application. He wants to allow remote users to connect and access the application through a dial-up connection via the Internet. All data will be sent across a public network. For security reasons, the management wants to send data through the Internet in an encrypted form. The company plans to use a Layer 2 Tunneling Protocol (L2TP) connection. Which of the following communication protocols will Allen use to accomplish the task?
You work as a Web Application Developer for SunInfo Inc. The company uses Visual Studio 2008 as its application development platform. You create a Windows Forms application using .NET Framework 3.5. You want to create a default event handler for an event in the designer. Which of the following steps will you take to accomplish the task?
Each correct answer represents a part of the solution. Choose all that apply.
You are working on an ASP.NET application that will handle shopping cart for online users. You wish to generate images of all your company's products dynamically on one of the application's Web pages. You need to modify your configuration settings file for this purpose. Which of the following sections of the configuration file will you use to accomplish the task?
You work as a Software Developer for ABC Inc. The company uses Visual Studio .NET as its application development platform. You create a class library using the .NET Framework. The library will be used to open the NSCs of computers. Later, you will set up the class library to the GAC and provide it Full Trust permission. You write down the following code segments for the socket connections:
SocketPermission permission = new SocketPermission(PermissionState.Unrestricted); permission.Assert();
A number of the applications that use the class library may not have the necessary permissions to open the network socket connections. Therefore, you are required to withdraw the assertion. Which of the following code segments will you use to accomplish the task?
George works as a Software Developer for GenTech Inc. He creates an application named App1 using Visual Studio .NET. App1 uses the version 2.0.0.0 of an assembly named Assembly1. However, he wants App1 to use a new version i.e. 2.1.0.0 of Assembly1. Therefore, he needs to specify Assembly1's location so that App1 can use version 2.1.0.0 of Assembly1. What will George use to accomplish the task?
Each correct answer represents a complete solution. Choose all that apply.
You work as a Software Developer for ABC Inc. The company uses Visual Studio .NET as its application development platform. You are creating an assembly named Assem1 using .NET Framework. Assem1 contains a public method. The global cache contains a second assembly named Assem2. You need to ensure that the public method is only called from Assem2. Which of the following permission classes will you use to accomplish the task?
You work as a Web Application Developer for SunInfo Inc. The company uses Visual Studio 2008 as its application development platform. You create a Web application using .NET Framework 3.5. You want to ensure that when an unhandled exception occurs on the site, a custom error page errorpage.aspx is displayed. Also, you want to ensure that when the HTTP 500 error occurs, the servererror.aspx page is displayed. Which of the following settings will you add inside the system.web section of the Web.config file to accomplish the task?
Maria works as a Software Developer for ABC Inc. The company uses Visual Studio .NET 2005 as its application development platform. She creates a Web service and uses a Session object in it. She declares a variable in the Session object. What will be the scope of the variable?
You work as a Windows Application Developer for ABC Inc. The company uses Visual Studio .NET 2008 as its application development platform. You create a Windows application using .NET Framework 3.5. The application captures account information. The account number has the following specifications:
l It holds literal and input characters of the alphanumeric type.
l It has a predefined format.
You must ensure that the account number is in the correct format. You must also ensure that only input characters are accepted from users. What will you do?
You work as a Software Developer for ABC Inc. You use C# .NET to develop a windows application. The application will implement a role-based authorization scheme that is based on a Microsoft SQL Server database of user names. Users will enter their names in a text box named UserName. You must ensure that users are assigned the supervisor role and the PG role by default. Which of the following code segments will you use to accomplish this task?
You work as a Software Developer for ABC Inc. The company uses Visual Studio .NET 2005 as its application development platform. You create a Web service using the .NET Framework 2.0. You call a method in the Web service. The following exception is thrown in the Web service: client.System.Web.Services.Protocols.SoapException: Server was unable to process request. System.NullReferenceException: Object reference not set to an instance of an object. You find out that it is the following line of code that throws the exception: if (Session ["StoredValue"] == null)
You must ensure that the method runs without throwing any exception. What will you do to accomplish this task?
You work as a Software Developer for ABC Inc. The company uses Visual Studio .NET 2008 as its application development platform. You are creating an ASP.NET Web application using .NET Framework 3.5. The application will be deployed on an intranet server of the company. You require that the application meets the following requirements:
l Users can log on to the application by using their Active Directory credentials.
l Each Web page in the application must display user name and password controls for an unauthenticated user.
What will you do to accomplish this?
You work as a Web Application Developer for SunInfo Inc. The company uses Visual Studio 2008 as its application development platform. You create a Web application using .NET Framework 3.5. You want to attach the Visual Studio Debugger to Internet Explorer when the application is running. Which of the following steps will you take to accomplish the task?
Each correct answer represents a part of the solution. Choose all that apply.
You work as a Software Developer for ABC Inc. The company uses Visual Studio.NET 2005 as its application development platform. You are in the process of creating an application that will handle unmanaged code using the .NET Framework 2.0. Which of the following services will you use to provide interoperability with the unmanaged code?
Each correct answer represents a complete solution. Choose two.
You work as a Software Developer for ABC Inc. The company uses Visual Studio .NET 2005 as its application development platform. You are developing an application using .NET Framework 2.0. You are required to use a datatype that will store only the numbers. The numbers should be in positive form and should not be larger than 65,535. Which of the following datatypes will you use to accomplish the task?
Each correct answer represents a complete solution. Choose two.
You work as a Web Application Developer for ABC Inc. The company uses Visual Studio .NET as its application development platform. You create a Web application using .NET Framework 2.0. The application code restricts access to some pages based on the users' credentials. However, you are required to configure IIS to supply the user's Windows credentials to the Web application. All these credentials must be encrypted. What will you do?
You work as a Software Developer for ABC Inc. The company uses Visual Studio.NET as its application development platform. You create an application using the .NET Framework. You need to use the regular expressions to provide a concise and flexible means for identifying strings of text of interest, such as particular characters, words, or patterns of characters. Which operation will you use to construct the regular expressions?
Each correct answer represents a complete solution. Choose all that apply.
Martha works as a Software Developer for NetCom Inc. She develops an application, named App1, using Visual Studio .NET. The application contains a form, named MyForm1. MyForm1 contains several controls including a TextBox, named txtDOB. The txtDOB control is used to accept the date of birth from a user. In order to ensure that a user enters a valid date in txtDOB, Martha adds validation logic to the Validating event of txtDOB. When she tests the form by using some invalid dates in txtDOB, the validation logic does not appear to be working as expected. What is the most likely cause of the issue?
You work as a Windows Application Developer for ABC Inc. The company uses Visual Studio .NET 2008 as its application development platform. You create a Windows application using .NET Framework 3.5. The application uses a SQL Server 2008 database on the network.
You use ADO.NET Data Services that exposes data as resources that are addressable by URIs. You access and change data by using the semantics of representational state transfer (REST), specifically the standard HTTP verbs of GET, PUT, POST, and DELETE. You must ensure that when a service violates any other constraint, the service cannot strictly be referred to as RESTful. What will you do?
You work as a Software Developer for ABC Inc. You create a Console application. You write the following code in the application:
RC2CryptoServiceProvider TestRC2 = new RC2CryptoServiceProvider();
Console.WriteLine(TestRC2.Mode);
What output will the above code display?
Peter works as a Software Developer for PentaSoft Inc. He develops an application, named App1, using Visual C# .NET. The application is intended to deal with several file input and output operations. He uses the following try structure in the application code to handle errors that occur during the execution of App1.
try
{
//Statements that might cause a runtime error.
}
catch (System.IO.FileNotFoundException ex)
{
//Statements
}
catch (System.IO.PathTooLongException ex)
{
//Statements
}
catch (System.IO.IOException ex)
{
//Statements
}
catch (Exception ex)
{
//Statements
}
What will happen if an exception of type System.IO.DirectoryNotFoundException occurs in the try block?
You work as a Software Developer for ABC Inc. The company uses Visual Studio.NET 2005 as its application development platform. You have recently finished development of Web services using the .NET Framework. The access control to Web services is part of your accountability. You are currently revealing an existing class as a XML Web service. You are required to ensure that the XML Web service is exclusively accessible to Web service clients within the ABC Inc. domain. To fulfill this requirement you want to change the access modifiers on methods that must be represented as Web methods. What will you do to accomplish this task?
You work as a Windows Application Developer for ABC Inc. The company uses Visual Studio .NET as its application development platform. You create a Windows application using .NET Framework 2.0. The application allows computer engineers to design circuit boards for different types of hardware. You create a custom control that represents the design surface. You are required to highlight the vacant areas on the design surface where a component can be dropped. Which of the following events will you use to accomplish this task?
You work as a Software Developer for ABC Inc. The company uses Visual Studio .NET 2005 as its application development platform. You are creating an application using .NET Framework 2.0. The application uses serialization to allow users to take an instance of an object and convert it into a format that can be easily transmittable over the network or even stored in a database. You want to provide the base functionality for the common language runtime serialization formatters. Which of the following classes will you use to accomplish the task?
You work as an Enterprise Application Developer for Mansoft Inc. You are participating in the
design for a Web-based Order Management System. There are a few configuration options, such as applicable tax percentage, repeat customer discount percentage, etc., which are applicable to all the users of the Order Management System. However, these configuration options might be changed in the future. Which of the following techniques will you use to maintain this information from the performance and maintenance point of view?
You work as a Windows Application Developer for ABC Inc. The company uses Visual Studio .NET 2008 as its application development platform. You are creating a Windows Forms application using .NET Framework 3.5. You need to develop a new control for the application. You must ensure that the control inherits the TreeView control by adding a custom node tag and a highlight color. What will you do?
Which of the following security methods is used when the code requires a specific set of permissions, which are not known until runtime?
You work as a Software Developer for ABC Inc. The company has several branches worldwide. The company uses Visual Studio.NET 2005 as its application development platform. You are creating an application that generates summary reports. These reports will be viewed by all the chief executives in the Korean branch. Therefore, you need to ensure that the summary reports must contain Korean characters. Which of the following encoding types will you use to accomplish the task?
Each correct answer represents a complete solution. Choose all that apply.
You work as a Software Developer for Mansoft Inc. You create an application and use it to create users as members of the local Users group. Which of the following code snippets imperatively demands that the current user is a member of the local Users group?
Each correct answer represents a complete solution. Choose all that apply.
Allen works as a Software Developer for ManSoft Inc. He develops a Web application using Visual Studio .NET. He adds a Web reference to an XML Web service named MyWebService in the application. MyWebService includes a method named MyMethod, which takes user identification number as a parameter and returns a DataSet object containing user information. The System.ArgumentException is thrown if the user identification number is not positioned between 1 and 500. Allen writes a try/catch block to capture the exceptions thrown by the Web service. Which of the following exceptions will the try/catch block catch if a user calls MyMethod passing 501 as a parameter?
You work as a Software Developer for Webtech Inc. You plan to migrate the existing Active Server Pages (ASP) pages to ASP.NET Web pages in order to implement rich functionalities of a Web browser in your Web pages. Therefore, you want to add controls to Web pages of your existing application named WebApp1. Which of the following controls will be most suitable to implement?
Which of the following classes will you use to specify that a string must be centered when drawn?
You work as a Software Developer for ManSoft Inc. You use C# .NET to create an assembly named TestAssembly that will be used by other applications, including a standard COM client application. You must deploy the assembly on the COM application to a client computer. You must ensure that the COM applications can instantiate components within the assembly as COM components. Which of the following options will you use to accomplish this task?
Smith works as a Software Developer for BlueWell Inc. He develops a Web application named WebApp by using Visual Studio .NET. He wants to deploy WebApp on a target computer. He wants to take precautionary measures in the application so that no issues may arise while deploying it. Which of the following measures will Smith take to accomplish the task?
Each correct answer represents a complete solution. Choose all that apply.
Andrew works as a Software Developer for BlueWell Inc. He develops a Windows-based application, named App1, using Visual Studio .NET. The application uses Microsoft SQL Server as a backend database. Andrew wants to perform security checks on App1. Which of the following statements regarding security checks are true?
Each correct answer represents a complete solution. Choose two.
You work as a Software Developer for ABC Inc. The company uses Visual Studio .NET 2005 as its application development platform. You create an application named MyApplication. MyApplication uses the System.IO namespace. You want to ensure that you are able to use a class that specifies read and write operations either in synchronous or asynchronous manner. Which of the following classes will you use to accomplish the task?
You work as a Software Developer for ABC Inc. The company uses Visual Studio .NET 2005 as its application development platform. You create an application named StringRW using .NET Framework. You store some characters into an array of Unicode characters. You need to write all or some of these characters into a String object. Which of the following code segments will you choose to accomplish this task?
Each correct answer represents a complete solution. Choose all that apply.
You work as a Software Developer for InfoTech Inc. You create a Windows form in a Windows-based application named MyWinApp1. You use graphics in the form. You write the following code in your form:
private void MyMouseEvent1(object sender1, MouseEventArgs event)
{
// Code to handle mouse events
}
You want to implement a property of the MouseEventArgs object. This property will return a Point structure that contains the x-coordinate and y-coordinate of the mouse. Which of the following properties of the MouseEventArgs object will you use to accomplish this?
Charles works as a Web Developer for TechNet Inc. He develops an application named AdAgentsApp for advertising agents by using Visual Studio .NET. AdAgentsApp uses several Web services provided by the company. The employees in the IT department use only the existing port numbers 80 (HTTP protocol) and 443 (HTTPS protocol) for firewall security. However, they are forbidden to open any other new ports. These ports have been used to ensure the highest security level of authentication.
Which of the following actions should Charles take to maintain the highest security?
Each correct answer represents a part of the solution. Choose two.
Peter works as a Software Developer for PaulTech Inc. He develops an application for office management, using Visual C# .NET. He creates an OleDbConnection object, named Pcon. He wants to create an OleDbCommand object to retrieve employee details. Which of the following statements will Peter use to set the CommandText and Connection properties to accomplish the required task?
Each correct answer represents a part of the solution. Choose three.
Samantha works as a Software Developer for InfoWorld Inc. She develops a Web page named SalesReport.aspx for the employees of the company. However, she wants to ensure that all the requests for a particular employee are not stored on the server's memory. She also wants to ensure that no data is lost even after each user session has expired. Which of the following actions will Samantha take to accomplish the task?
You work as a Software Developer for ManSoft Inc. The company has several branches worldwide. The company uses Visual Studio.NET 2005 as its application development platform. You are creating a global application that will be used by all the branches of the company. You want to perform the encoding of Unicode characters with error detection capability. Which of the following classes will you use to accomplish the task?
Each correct answer represents a complete solution. Choose three.
Emily works as a Programmer in an Eye Research Center. The center keeps several records such as case history records for old patients and newly admitted patients, and records for outdoor patients. The Head of the Research Center wants Emily to generate reports for each outdoor patient with minimum network traffic. Emily develops an application named OutdoorPatientReport by using Visual Studio .NET. She needs to utilize the data repository as maintained by the center.
She wants to ensure that the application is displayed to all the doctors. Which of the following actions will Emily take to accomplish this task?
Allen works as a Software Developer for Mansoft Inc. He develops a Web application using Visual Studio .NET. He adds a Web reference to an XML Web service named MyWebService in the application. MyWebService includes a method named MyMethod, which takes user identification number as a parameter and returns a DataSet object containing user information. The System.ArgumentException is thrown if the user identification number does not lie between 1 and 500. Allen writes a try and catch block to capture the exception thrown by the Web service. Which of the following exceptions will the try and catch block catch if a user calls MyMethod passing 501 as a parameter?
You work as a Software Developer for Mansoft Inc. The company uses Visual Studio.NET as its application development platform. You create an application, which will be used for e-commerce.
You want to ensure that the transactions are highly secured. For this purpose, you have to create a system to verify the identity of a potential customer. Which of the following security techniques will you use to accomplish this task?
You work as a Software Developer for ABC Inc. The company uses Visual Studio .NET 2008 as its application development platform. You create an ASP.NET Web application using .NET Framework 3.5. The application is a library application that catalogs Classes and books. The application contains a DataContext object named Classes and a related line of business object named Books. The Classes DataContext object is queried by using the following LINQ query: var query = from class in Classes where class.Books.All(b => b.Price <= 50) select class;
You have to find out the result that will be returned from the query. What will be the result of the query?
You work as a Software Developer for InfoTech Inc. You develop a Windows application named MyWinApp that displays a registration form for users. You want to ensure that whenever a user enters a wrong data in the required TextBox controls, the data will not be accepted by the application. Which of the following actions will you take so that users should enter only valid data?
You work as a Software Developer for ABC Inc. The company uses Visual Studio.NET as its application development platform. You create an application using .NET Framework. The application is used to place an assembly on the intranet. Which of the following classes will you use to test whether or not an assembly was located on the intranet?
Allen works as a Software Developer for ABC Inc. He develops an application using Visual Studio .NET
2005. The application will be used for the registration of employees by filling a form provided in the application. The form contains the following fields:
l First Name
l Last Name
l Date of Birth
l E-mail
He provides a TextBox control for each field. He wants an employee to be able to receive a user-defined error message when he makes a wrong entry. Which of the following properties is mandatory if a
CustomValidator control is used to validate an entry?
Georgina works as a Software Developer for BlueChip Inc. She develops an application named App1 using Visual Studio .NET. The company wants her to deploy App1 to a customer's laptop. Georgina creates an assembly named Assembly1 to be stored in the Global Assembly Cache so that the Common Language Runtime (CLR) can locate and bind Assembly1.
As the application executes, the CLR locates the path of Assembly1 through the codebase setting. But, it finds no
Each correct answer represents a part of the solution. Choose all that apply.
You work as a Software Developer for ABC Inc. The company uses Visual Studio .NET 2005 as its application development platform. You create an application for the company. You need to validate the phone number passed to a class as a parameter in the application. Which of the following is the most effective way to verify that the format of the data matches a phone number?
You work as a Software Developer for ABC Inc. The company uses Visual Studio.NET as its application development platform. You create a Windows service application using the .NET Framework. You are required to synchronize execution of some resources across multiple processes.
What will you do to accomplish this task?
You work as a Windows Application Developer for ABC Inc. The company uses Visual Studio .NET 2008 as its application development platform. You create a Windows Forms application using .NET Framework 3.5. The application needs a thread that accepts an integer parameter. You write the following code segment in the application:
Thread myThread = new Thread(new ParameterizedThreadStart(doWork));
myThread.Start(125);
You are required to declare the signature of the doWork method. Which of the following method signatures will you use?
You work as a Software Developer for ABC Inc. The company has several branches worldwide.
The company uses Visual Studio.NET 2005 as its application development platform. You have recently finished the development of an application using .NET Framework 2.0. The application can be used only for cryptography. Therefore, you have implemented the application on a computer. What will you call the computer that implemented cryptography?
You work as a Software Developer for ABC Inc. The company uses Visual Studio .NET 2008 as its application development platform. You have recently finished development of an ASP.NET Web application using .NET Framework 3.5. The company's sales employees access the application, which is deployed on a Web server. You want to secure the Web server. To secure the Web server, you want to use cookieless forms authentication. Which of the following properties will you use to accomplish the task?
Sam works as a Software Developer for SamTech Inc. He creates an XML Web service, named
WebService1, using Visual Studio .NET. WebService1 uses the .NET Framework security class libraries to implement security. It implements role-based authorization based on a SQL Server database containing user names. Sam adds the following statements to the Web service codE. using System.Security.Principal; using System.Threading;
Sam wants to ensure that only validated users are permitted to access WebService1 by entering their user names and passwords in TextBox controls, named Text1 and Text2. He wants to implement imperative security check on WebService1. He also wants to ensure that users are assigned the Manager role and the Subordinate role by default. Which of the following classes will Sam use to accomplish the task?
Each correct answer represents a part of the solution. Choose two.
GIAC Certification | GSSP-.NET Questions Answers | GSSP-.NET Test Prep | GIAC GIAC Secure Software Programmer - C#.NET Questions PDF | GSSP-.NET Online Exam | GSSP-.NET Practice Test | GSSP-.NET PDF | GSSP-.NET Test Questions | GSSP-.NET Study Material | GSSP-.NET Exam Preparation | GSSP-.NET Valid Dumps | GSSP-.NET Real Questions | GIAC Certification GSSP-.NET Exam Questions


