What are two effects of enabling auto-cache in a FortiAnalyzer report? (Choose two.)
Which FortiAnalyzer feature allows you to use a proactive approach when managing your network security?
You discover that a few reports are taking a long tine lo generate. Which two steps can you Like to troubleshoot? (Choose two.)
After generating a report, you notice the information you where expecting to see is not included in it. However, you confirm that the logs are there.
Exhibit.
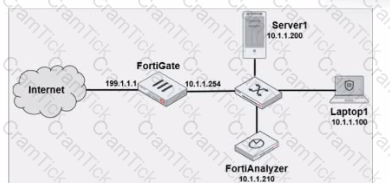
Laptop1 is used by several administrators to manage FotiAnalyzer. You want to configure a generic text filter that matches all login attempts to the web interface generated by any user other than admin’’, and coming from Laptop1.
Which filter will achieve the desired result?
You find that as part of your role as an analyst, you frequently search log View using the same parameters.
Instead of defining your search filters repeatedly, what can you do to save time?
Which two methods can you use to send notifications when an event occurs that matches a configured event handler? (Choose two.)
You are tasked with finding logs corresponding to a suspected attack on your network.
You need to use an interface where all identified threats within timeframe are listed and organized. You also need to be able to quickly export the information to a PDF file.
Where can you go to accomplish this task?
Refer to Exhibit:
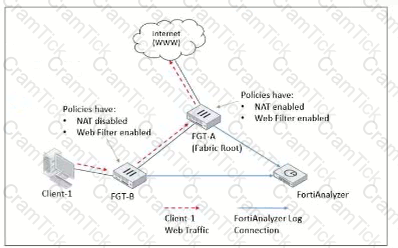
Client-1 is trying to access the internet for web browsing.
All FortiGate devices in the topology are part of a Security Fabric with logging to FortiAnalyzer configured. All firewall policies have logging enabled. All web filter profiles are configured to log only violations.
Which statement about the logging behavior for this specific traffic flow is true?
Which SQL query is in the correct order to query to database in the FortiAnalyzer?