A key risk indicator (KRI) is reported to senior management on a periodic basis as exceeding thresholds, but each time senior management has decided to take no action to reduce the risk. Which of the following is the MOST likely reason for senior management's response?
The MOST important characteristic of an organization s policies is to reflect the organization's:
Which of the following would BEST ensure that identified risk scenarios are addressed?
Which of the following is MOST helpful when determining whether a system security control is effective?
Which of the following is the BEST key performance indicator (KPI) to measure the ability to deliver uninterrupted IT services?
Which of the following changes would be reflected in an organization's risk profile after the failure of a critical patch implementation?
Which of the following is a KEY consideration for a risk practitioner to communicate to senior management evaluating the introduction of artificial intelligence (Al) solutions into the organization?
Which of the following is the BEST way to determine the ongoing efficiency of control processes?
Which of the following is the MOST important consideration when sharing risk management updates with executive management?
While reviewing an organization's monthly change management metrics, a risk practitioner notes that the number of emergency changes has increased substantially Which of the following would be the BEST approach for the risk practitioner to take?
Which of the following offers the SIMPLEST overview of changes in an organization's risk profile?
Which of the following is the PRIMARY role of a data custodian in the risk management process?
An organization practices the principle of least privilege. To ensure access remains appropriate, application owners should be required to review user access rights on a regular basis by obtaining:
Which of the following is the BEST key performance indicator (KPI) to measure the effectiveness of a disaster recovery plan (DRP)?
Which of the following is the GREATEST benefit of a three lines of defense structure?
Which of the following is the MOST important consideration when multiple risk practitioners capture risk scenarios in a single risk register?
Which of the following is the MOST important key performance indicator (KPI) for monitoring the user access management process?
An organization's senior management is considering whether to acquire cyber insurance. Which of the following is the BEST way for the risk practitioner to enable management’s decision?
IT management has asked for a consolidated view into the organization's risk profile to enable project prioritization and resource allocation. Which of the following materials would
be MOST helpful?
An organization maintains independent departmental risk registers that are not automatically aggregated. Which of the following is the GREATEST concern?
Which of the following is the BEST way to reduce the likelihood of an individual performing a potentially harmful action as the result of unnecessary entitlement?
A risk practitioner observes that hardware failure incidents have been increasing over the last few months. However, due to built-in redundancy and fault-tolerant architecture, there have been no interruptions to business operations. The risk practitioner should conclude that:
Which of the following roles would be MOST helpful in providing a high-level view of risk related to customer data loss?
After undertaking a risk assessment of a production system, the MOST appropriate action is for the risk manager to:
Which of the following is the ULTIMATE objective of utilizing key control indicators (KCIs) in the risk management process?
Where is the FIRST place a risk practitioner should look to identify accountability for a specific risk?
Which of the following is the MAIN reason for documenting the performance of controls?
A risk practitioner is assisting with the preparation of a report on the organization s disaster recovery (DR) capabilities. Which information would have the MOST impact on the overall recovery profile?
Which of the following is the MOST important element of a successful risk awareness training program?
Which of the following is the BEST approach when a risk treatment plan cannot be completed on time?
Which of the following should a risk practitioner review FIRST when evaluating risk events associated with the organization's data flow model?
Which of the following is MOST important to ensure when reviewing an organization's risk register?
Which of the following is the MOST effective way to incorporate stakeholder concerns when developing risk scenarios?
A risk practitioner is organizing a training session lo communicate risk assessment methodologies to ensure a consistent risk view within the organization Which of the following i< the MOST important topic to cover in this training?
An assessment of information security controls has identified ineffective controls. Which of the following should be the risk practitioner's FIRST course of action?
Which of the following is the MOST important objective of an enterprise risk management (ERM) program?
An organization's IT infrastructure is running end-of-life software that is not allowed without exception approval. Which of the following would provide the MOST helpful information to justify investing in updated software?
Which of the following is MOST important to the successful development of IT risk scenarios?
Which of the following is the MOST essential factor for managing risk in a highly dynamic environment?
The PRIMARY advantage of involving end users in continuity planning is that they:
Senior management has asked a risk practitioner to develop technical risk scenarios related to a recently developed enterprise resource planning (ERP) system. These scenarios will be owned by the system manager. Which of the following would be the BEST method to use when developing the scenarios?
A risk practitioner identifies a database application that has been developed and implemented by the business independently of IT. Which of the following is the BEST course of action?
Which of the following provides the BEST assurance of the effectiveness of vendor security controls?
Key risk indicators (KRIs) are MOST useful during which of the following risk management phases?
Which of the following would be- MOST helpful to understand the impact of a new technology system on an organization's current risk profile?
When reviewing management's IT control self-assessments, a risk practitioner noted an ineffective control that links to several low residual risk scenarios. What should be the NEXT course of action?
Which of the following is the BEST way for a risk practitioner to help management prioritize risk response?
Which of the following should be the PRIMARY consideration when implementing controls for monitoring user activity logs?
Which of the following BEST protects an organization against breaches when using a software as a service (SaaS) application?
To reduce costs, an organization is combining the second and third tines of defense in a new department that reports to a recently appointed C-level executive. Which of the following is the GREATEST concern with this situation?
Which of the following is the BEST course of action to help reduce the probability of an incident recurring?
A robotic process automation (RPA) project has implemented new robots to enhance the efficiency of a sales business process. Which of the following provides the BEST evidence that the new controls have been implemented successfully?
In addition to the risk exposure, which of the following is MOST important for senior management to understand prior to approving the use of artificial intelligence (Al) solutions?
An enterprise has taken delivery of software patches that address vulnerabilities in its core business software. Prior to implementation, which of the following is the MOST important task to be performed?
A global organization has implemented an application that does not address all privacy requirements across multiple jurisdictions. Which of the following risk responses has the organization adopted with regard to privacy requirements?
Which of the following is MOST likely to introduce risk for financial institutions that use blockchain?
Which of the following is the PRIMARY purpose of periodically reviewing an organization's risk profile?
Which of the following is the PRIMARY reason to perform ongoing risk assessments?
Which of the following elements of a risk register is MOST likely to change as a result of change in management's risk appetite?
Which of the following provides the BEST evidence of the effectiveness of an organization's account provisioning process?
An employee lost a personal mobile device that may contain sensitive corporate information. What should be the risk practitioner's recommendation?
Which of the following is the BEST approach when a risk practitioner has been asked by a business unit manager for special consideration during a risk assessment of a system?
The PRIMARY benefit of maintaining an up-to-date risk register is that it helps to:
An audit reveals that several terminated employee accounts maintain access. Which of the following should be the FIRST step to address the risk?
The analysis of which of the following will BEST help validate whether suspicious network activity is malicious?
Which of the following is the MOST important requirement for monitoring key risk indicators (KRls) using log analysis?
Which of the following is the BEST indication of an effective risk management program?
Which of the following should be the PRIMARY consideration when assessing the automation of control monitoring?
Which of the following would MOST effectively enable a business operations manager to identify events exceeding risk thresholds?
Which of the following BEST facilitates the mitigation of identified gaps between current and desired risk environment states?
Which of the following is the MOST important factor when deciding on a control to mitigate risk exposure?
The PRIMARY benefit of using a maturity model is that it helps to evaluate the:
Calculation of the recovery time objective (RTO) is necessary to determine the:
Improvements in the design and implementation of a control will MOST likely result in an update to:
Of the following, who is accountable for ensuing the effectiveness of a control to mitigate risk?
An information system for a key business operation is being moved from an in-house application to a Software as a Service (SaaS) vendor. Which of the following will have the GREATEST impact on the ability to monitor risk?
Legal and regulatory risk associated with business conducted over the Internet is driven by:
An IT risk practitioner has been asked to regularly report on the overall status and effectiveness of the IT risk management program. Which of the following is MOST useful for this purpose?
Which of the following practices BEST mitigates risk related to enterprise-wide ethical decision making in a multi-national organization?
A risk practitioner has been asked by executives to explain how existing risk treatment plans would affect risk posture at the end of the year. Which of the following is MOST helpful in responding to this request?
The BEST indication that risk management is effective is when risk has been reduced to meet:
An organization has initiated a project to launch an IT-based service to customers and take advantage of being the first to market. Which of the following should be of GREATEST concern to senior management?
Which of the following BEST represents a critical threshold value for a key control indicator (KCI)?
Which of the following is the BEST recommendation to senior management when the results of a risk and control assessment indicate a risk scenario can only be partially mitigated?
The PRIMARY reason a risk practitioner would be interested in an internal audit report is to:
The risk associated with an asset before controls are applied can be expressed as:
A trusted third-party service provider has determined that the risk of a client's systems being hacked is low. Which of the following would be the client's BEST course of action?
A web-based service provider with a low risk appetite for system outages is reviewing its current risk profile for online security. Which of the following observations would be MOST relevant to escalate to senior management?
Which of the following BEST facilities the alignment of IT risk management with enterprise risk management (ERM)?
Which of the following is the BEST way to validate the results of a vulnerability assessment?
Which of the following would be a risk practitioners’ BEST recommendation for preventing cyber intrusion?
A risk heat map is MOST commonly used as part of an IT risk analysis to facilitate risk:
Which of the following is the MOST cost-effective way to test a business continuity plan?
When formulating a social media policy lo address information leakage, which of the following is the MOST important concern to address?
A department allows multiple users to perform maintenance on a system using a single set of credentials. A risk practitioner determined this practice to be high-risk. Which of the following is the MOST effective way to mitigate this risk?
Which of the following would be MOST helpful to a risk practitioner when ensuring that mitigated risk remains within acceptable limits?
Which of the following is the MOST effective way to help ensure future risk levels do not exceed the organization's risk appetite?
An application owner has specified the acceptable downtime in the event of an incident to be much lower than the actual time required for the response team to recover the application. Which of the following should be the NEXT course of action?
When reviewing the business continuity plan (BCP) of an online sales order system, a risk practitioner notices that the recovery time objective (RTO) has a shorter lime than what is defined in the disaster recovery plan (DRP). Which of the following is the BEST way for the risk practitioner to address this concern?
Which of the following controls will BEST detect unauthorized modification of data by a database administrator?
Reviewing results from which of the following is the BEST way to identify information systems control deficiencies?
A risk practitioner discovers several key documents detailing the design of a product currently in development have been posted on the Internet. What should be the risk practitioner's FIRST course of action?
Which risk response strategy could management apply to both positive and negative risk that has been identified?
Following an acquisition, the acquiring company's risk practitioner has been asked to update the organization's IT risk profile What is the MOST important information to review from the acquired company to facilitate this task?
A recent vulnerability assessment of a web-facing application revealed several weaknesses. Which of the following should be done NEXT to determine the risk exposure?
Which of the following would BEST facilitate the implementation of data classification requirements?
Which of the following BEST enables a risk practitioner to understand management's approach to organizational risk?
Senior management is deciding whether to share confidential data with the organization's business partners. The BEST course of action for a risk practitioner would be to submit a report to senior management containing the:
The PRIMARY objective of collecting information and reviewing documentation when performing periodic risk analysis should be to:
An organization has used generic risk scenarios to populate its risk register. Which of the following presents the GREATEST challenge to assigning of the associated risk entries?
Which of the following is MOST helpful in identifying new risk exposures due to changes in the business environment?
Which of the following is MOST important to understand when determining an appropriate risk assessment approach?
Which of the following is the BEST metric to demonstrate the effectiveness of an organization's change management process?
The MAIN reason for prioritizing IT risk responses is to enable an organization to:
Of the following, who is BEST suited to assist a risk practitioner in developing a relevant set of risk scenarios?
Which of the following is the PRIMARY factor in determining a recovery time objective (RTO)?
Which of the following will BEST help mitigate the risk associated with malicious functionality in outsourced application development?
What are the MOST essential attributes of an effective Key control indicator (KCI)?
Which of the following is MOST helpful in preventing risk events from materializing?
An IT department has provided a shared drive for personnel to store information to which all employees have access. Which of the following parties is accountable for the risk of potential loss of confidential information?
Which of the following controls BEST enables an organization to ensure a complete and accurate IT asset inventory?
An organization's risk register contains a large volume of risk scenarios that senior management considers overwhelming. Which of the following would BEST help to improve the risk register?
An organization has detected unauthorized logins to its client database servers. Which of the following should be of GREATEST concern?
Which of the following controls BEST helps to ensure that transaction data reaches its destination?
Several network user accounts were recently created without the required management approvals. Which of the following would be the risk practitioner's BEST recommendation to address this situation?
Which of the following is the BEST key control indicator (KCI) for risk related to IT infrastructure failure?
Which of the following is the MOST important consideration when selecting key risk indicators (KRIs) to monitor risk trends over time?
A systems interruption has been traced to a personal USB device plugged into the corporate network by an IT employee who bypassed internal control procedures. Of the following, who should be accountable?
A global company s business continuity plan (BCP) requires the transfer of its customer information….
event of a disaster. Which of the following should be the MOST important risk consideration?
Which of the following s MOST likely to deter an employee from engaging in inappropriate use of company owned IT systems?
Which of the following will BEST quantify the risk associated with malicious users in an organization?
Which of the following IT controls is MOST useful in mitigating the risk associated with inaccurate data?
An unauthorized individual has socially engineered entry into an organization's secured physical premises. Which of the following is the BEST way to prevent future occurrences?
It is MOST appropriate for changes to be promoted to production after they are:
After a risk has been identified, who is in the BEST position to select the appropriate risk treatment option?
Which of the following is the MOST important consideration for a risk practitioner when making a system implementation go-live recommendation?
Which of the following techniques would be used during a risk assessment to demonstrate to stakeholders that all known alternatives were evaluated?
An organization that has been the subject of multiple social engineering attacks is developing a risk awareness program. The PRIMARY goal of this program should be to:
Which of the following would provide the BEST guidance when selecting an appropriate risk treatment plan?
Establishing and organizational code of conduct is an example of which type of control?
Which of the following is the MOST important benefit of implementing a data classification program?
When an organization's business continuity plan (BCP) states that it cannot afford to lose more than three hours of a critical application's data, the three hours is considered the application’s:
Which of the following should be the PRIMARY input when designing IT controls?
Which of the following would be MOST useful when measuring the progress of a risk response action plan?
Which of the following would BEST help an enterprise prioritize risk scenarios?
Which of the following is the BEST key performance indicator (KPI) to measure the maturity of an organization's security incident handling process?
Which of the following would be MOST important for a risk practitioner to provide to the internal audit department during the audit planning process?
Which of the following would be the BEST recommendation if the level of risk in the IT risk profile has decreased and is now below management's risk appetite?
A risk practitioner is developing a set of bottom-up IT risk scenarios. The MOST important time to involve business stakeholders is when:
The BEST way to mitigate the high cost of retrieving electronic evidence associated with potential litigation is to implement policies and procedures for.
Which of the following would BEST provide early warning of a high-risk condition?
Which of the following is the PRIMARY reason for sharing risk assessment reports with senior stakeholders?
Which of the following BEST mitigates reputational risk associated with disinformation campaigns against an organization?
Which of the following is the BEST method to ensure a terminated employee's access to IT systems is revoked upon departure from the organization?
Which of the following is the BEST approach for an organization in a heavily regulated industry to comprehensively test application functionality?
Which of the following would BEST enable a risk-based decision when considering the use of an emerging technology for data processing?
An organization is implementing robotic process automation (RPA) to streamline business processes. Given that implementation of this technology is expected to impact existing controls, which of the following is the risk practitioner's BEST course of action?
An organization delegates its data processing to the internal IT team to manage information through its applications. Which of the following is the role of the internal IT team in this situation?
Which of the following is the FIRST step in managing the security risk associated with wearable technology in the workplace?
Which of the following helps ensure compliance with a nonrepudiation policy requirement for electronic transactions?
Periodically reviewing and updating a risk register with details on identified risk factors PRIMARILY helps to:
An organization has an approved bring your own device (BYOD) policy. Which of the following would BEST mitigate the security risk associated with the inappropriate use of enterprise applications on the devices?
Which of the following activities would BEST contribute to promoting an organization-wide risk-aware culture?
Which of the following is the PRIMARY reason for a risk practitioner to use global standards related to risk management?
Which of the following is the MOST important data source for monitoring key risk indicators (KRIs)?
During an IT risk scenario review session, business executives question why they have been assigned ownership of IT-related risk scenarios. They feel IT risk is technical in nature and therefore should be owned by IT. Which of the following is the BEST way for the risk practitioner to address these concerns?
Who should be accountable for ensuring effective cybersecurity controls are established?
Management has noticed storage costs have increased exponentially over the last 10 years because most users do not delete their emails. Which of the following can BEST alleviate this issue while not sacrificing security?
A risk practitioner is summarizing the results of a high-profile risk assessment sponsored by senior management. The BEST way to support risk-based decisions by senior management would be to:
Which of the following is the BEST way for a risk practitioner to present an annual risk management update to the board''
Which of the following is the MOST important key performance indicator (KPI) to establish in the service level agreement (SLA) for an outsourced data center?
An organization wants to launch a campaign to advertise a new product Using data analytics, the campaign can be targeted to reach potential customers. Which of the following should be of GREATEST concern to the risk practitioner?
A risk practitioner is performing a risk assessment of recent external advancements in quantum computing. Which of the following would pose the GREATEST concern for the risk practitioner?
Which of the following is the BEST key performance indicator (KPI) for a server patch management process?
Which of the following risk register updates is MOST important for senior management to review?
The number of tickets to rework application code has significantly exceeded the established threshold. Which of the following would be the risk practitioner s BEST recommendation?
A cote data center went offline abruptly for several hours affecting many transactions across multiple locations. Which of the to" owing would provide the MOST useful information to determine mitigating controls?
Which of the following is the BEST indication that key risk indicators (KRls) should be revised?
When developing risk scenario using a list of generic scenarios based on industry best practices, it is MOST imported to:
An organization has decided to postpone the assessment and treatment of several risk scenarios because stakeholders are unavailable. As a result of this decision, the risk associated with these new entries has been;
Which of the following is the MOST important key performance indicator (KPI) to monitor the effectiveness of disaster recovery processes?
Which of the following is the MOST important information to cover a business continuity awareness Ira nine, program for all employees of the organization?
Business management is seeking assurance from the CIO that IT has a plan in place for early identification of potential issues that could impact the delivery of a new application Which of the following is the BEST way to increase the chances of a successful delivery'?
Which of the following is a risk practitioner's MOST important responsibility in managing risk acceptance that exceeds risk tolerance?
The following is the snapshot of a recently approved IT risk register maintained by an organization's information security department.
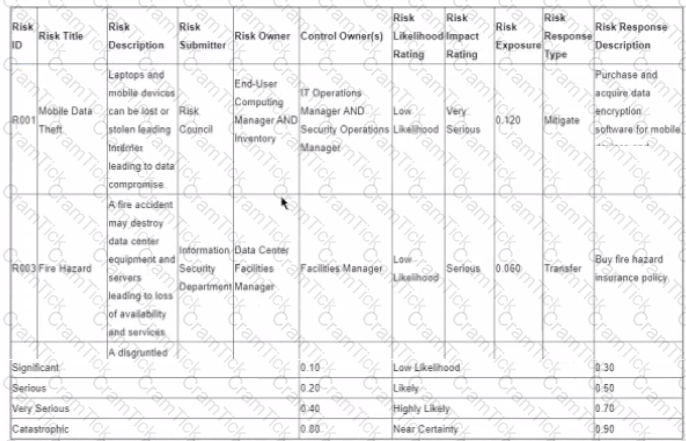
After implementing countermeasures listed in ‘’Risk Response Descriptions’’ for each of the Risk IDs, which of the following component of the register MUST change?
Which of the following is MOST helpful in providing an overview of an organization's risk management program?
Which component of a software inventory BEST enables the identification and mitigation of known vulnerabilities?
A zero-day vulnerability has been discovered in a globally used brand of hardware server that allows hackers to gain
access to affected IT systems. Which of the following is MOST likely to change as a result of this situation?
Which of the following is MOST important to determine when assessing the potential risk exposure of a loss event involving personal data?
A recent big data project has resulted in the creation of an application used to support important investment decisions. Which of the following should be of GREATEST concern to the risk practitioner?
Which of the following would BEST facilitate the implementation of data classification requirements?
Which of the following would be of GREATEST concern regarding an organization's asset management?
What should be the PRIMARY consideration related to data privacy protection when there are plans for a business initiative to make use of personal information?
Which of the following is MOST important information to review when developing plans for using emerging technologies?
Which of the following is the MOST comprehensive resource for prioritizing the implementation of information systems controls?
Which of the following is the MOST effective way 10 identify an application backdoor prior to implementation'?
Which of the following will BEST help to ensure new IT policies address the enterprise's requirements?
After the implementation of internal of Things (IoT) devices, new risk scenarios were identified. What is the PRIMARY reason to report this information to risk owners?
Which of the following sources is MOST relevant to reference when updating security awareness training materials?
A bank recently incorporated Blockchain technology with the potential to impact known risk within the organization. Which of the following is the risk practitioner’s BEST course of action?
The objective of aligning mitigating controls to risk appetite is to ensure that:
In order to determining a risk is under-controlled the risk practitioner will need to
An organization is adopting block chain for a new financial system. Which of the following should be the GREATEST concern for a risk practitioner evaluating the system's production readiness?
Which of the following is the MOST important objective from a cost perspective for considering aggregated risk responses in an organization?
What is the BEST recommendation to reduce the risk associated with potential system compromise when a vendor stops releasing security patches and updates for a business-critical legacy system?
Which of the following would be the BEST way for a risk practitioner to validate the effectiveness of a patching program?
Which of the following is the MOST critical factor to consider when determining an organization's risk appetite?
Which of the following is MOST important when conducting a post-implementation review as part of the system development life cycle (SDLC)?
Which of the following potential scenarios associated with the implementation of a new database technology presents the GREATEST risk to an organization?
Which of the following issues found during the review of a newly created disaster recovery plan (DRP) should be of MOST concern?
Which of the following is the MOST important step to ensure regulatory requirements are adequately addressed within an organization?
Who is BEST suited to provide objective input when updating residual risk to reflect the results of control effectiveness?
An organization wants to grant remote access to a system containing sensitive data to an overseas third party. Which of the following should be of GREATEST concern to management?
When developing a response plan to address security incidents regarding sensitive data loss, it is MOST important
Which of the following BEST facilitates the identification of appropriate key performance indicators (KPIs) for a risk management program?
Which of the following is the MAIN benefit to an organization using key risk indicators (KRIs)?
Which of the following should be used as the PRIMARY basis for evaluating the state of an organization's cloud computing environment against leading practices?
Which of the following has the GREATEST influence on an organization's risk appetite?
Who should be responsible (of evaluating the residual risk after a compensating control has been
An internal audit report reveals that a legacy system is no longer supported Which of the following is the risk practitioner's MOST important action before recommending a risk response'
Which of the following BEST helps to identify significant events that could impact an organization?
When performing a risk assessment of a new service to support a core business process, which of the following should be done FIRST to ensure continuity of operations?
An organization has experienced several incidents of extended network outages that have exceeded tolerance. Which of the following should be the risk practitioner's FIRST step to address this situation?
A multinational organization is considering implementing standard background checks to' all new employees A KEY concern regarding this approach
Which of the following would MOST effectively reduce risk associated with an increase of online transactions on a retailer website?
Which of the following is the MOST important reason to validate that risk responses have been executed as outlined in the risk response plan''
An organization is considering outsourcing user administration controls tor a critical system. The potential vendor has offered to perform quarterly sett-audits of its controls instead of having annual independent audits. Which of the following should be of GREATEST concern to me risk practitioner?
Which stakeholder is MOST important to include when defining a risk profile during me selection process for a new third party application'?
Which of the following is the MOST effective way to reduce potential losses due to ongoing expense fraud?
Which of the following provides the MOST useful information for developing key risk indicators (KRIs)?
What is the PRIMARY reason an organization should include background checks on roles with elevated access to production as part of its hiring process?
A control process has been implemented in response to a new regulatory requirement, but has significantly reduced productivity. Which of the following is the BEST way to resolve this concern?
A highly regulated enterprise is developing a new risk management plan to specifically address legal and regulatory risk scenarios What should be done FIRST by IT governance to support this effort?
During an acquisition, which of the following would provide the MOST useful input to the parent company's risk practitioner when developing risk scenarios for the post-acquisition phase?
When establishing an enterprise IT risk management program, it is MOST important to:
An organization has restructured its business processes, and the business continuity plan (BCP) needs to be revised accordingly. Which of the following should be identified FIRST?
Which of the following is a risk practitioner's BEST course of action after identifying risk scenarios related to noncompliance with new industry regulations?
An organization has been experiencing an increasing number of spear phishing attacks Which of the following would be the MOST effective way to mitigate the risk associated with these attacks?
Which of the following should be the MOST important consideration when determining controls necessary for a highly critical information system?
An organization has just started accepting credit card payments from customers via the corporate website. Which of the following is MOST likely to increase as a result of this new initiative?
Which of the following should a risk practitioner do FIRST to support the implementation of governance around organizational assets within an enterprise risk management (ERM) program?
A bank recently incorporated blockchain technology with the potential to impact known risk within the organization. Which of the following is the risk practitioner's BEST course of action?
Which of the following is MOST important to review when an organization needs to transition the majority of its employees to remote work during a crisis?
An organization has outsourced its customer management database to an external service provider. Of the following, who should be accountable for ensuring customer data privacy?
The PRIMARY benefit of selecting an appropriate set of key risk indicators (KRIs) is that they:
Which of the following is the MOST important course of action to foster an ethical, risk-aware culture?
An organization's risk management team wants to develop IT risk scenarios to show the impact of collecting and storing credit card information. Which of the following is the MOST comprehensive approach to capture this scenario?
Which of the following is the ULTIMATE goal of conducting a privacy impact analysis (PIA)?
An assessment of information security controls has identified ineffective controls. Which of the following should be the risk practitioner's FIRST course of action?
Which strategy employed by risk management would BEST help to prevent internal fraud?
Which of the following is the MOST important consideration when selecting digital signature software?
Which of the following activities is a responsibility of the second line of defense?
Who is PRIMARILY accountable for identifying risk on a daily basis and ensuring adherence to the organization's policies?
Which of the following factors will have the GREATEST impact on the implementation of a risk mitigation strategy for an organization?
In the three lines of defense model, a PRIMARY objective of the second line is to:
WhichT5f the following is the MOST effective way to promote organization-wide awareness of data security in response to an increase in regulatory penalties for data leakage?
A failure in an organization s IT system build process has resulted in several computers on the network missing the corporate endpoint detection and response (EDR) software. Which of the following should be the risk practitioner’s IMMEDIATE concern?
An incentive program is MOST likely implemented to manage the risk associated with loss of which organizational asset?
What is the MOST important consideration when selecting key performance indicators (KPIs) for control monitoring?
What would be MOST helpful to ensuring the effective implementation of a new cybersecurity program?
A risk practitioner has been notified of a social engineering attack using artificial intelligence (Al) technology to impersonate senior management personnel. Which of the following would BEST mitigate the impact of such attacks?
Which of the following is the MOST useful information for prioritizing risk mitigation?
Which of the following is the MOST likely reason an organization would engage an independent reviewer to assess its IT risk management program?
A risk practitioner's BEST guidance to help an organization develop relevant risk scenarios is to ensure the scenarios are:
After the announcement of a new IT regulatory requirement, it is MOST important for a risk practitioner to;
An organization has been made aware of a newly discovered critical vulnerability in a regulatory reporting system. Which of the following is the risk practitioner's BEST course of action?
Which of the following management actions will MOST likely change the likelihood rating of a risk scenario related to remote network access?
The operational risk associated with attacks on a web application should be owned by the individual in charge of:
Who is BEST suited to provide information to the risk practitioner about the effectiveness of a technical control associated with an application?
The PRIMARY reason for communicating risk assessment results to data owners is to enable the:
An organization uses one centralized single sign-on (SSO) control to cover many applications. Which of the following is the BEST course of action when a new application is added to the environment after testing of the SSO control has been completed?
Which of the following analyses is MOST useful for prioritizing risk scenarios associated with loss of IT assets?
A risk practitioner notes control design changes when comparing risk response to a previously approved action plan. Which of the following is MOST important for the practitioner to confirm?
The cost of maintaining a control has grown to exceed the potential loss. Which of the following BEST describes this situation?
The risk to an organization's reputation due to a recent cybersecurity breach is PRIMARILY considered to be:
Warning banners on login screens for laptops provided by an organization to its employees are an example of which type of control?
An organization has established workflows in its service desk to support employee reports of security-related concerns. Which of the following is the MOST efficient approach to analyze these concerns?
Which of the following is the GREATEST benefit of updating the risk register to include outcomes from a risk assessment?
Which of the following should a risk practitioner do NEXT after learning that Internet of Things (loT) devices installed in the production environment lack appropriate security controls for
sensitive data?
The BEST way to determine the likelihood of a system availability risk scenario is by assessing the:
Which of the following is the MOST effective key performance indicator (KPI) for change management?
The BEST metric to monitor the risk associated with changes deployed to production is the percentage of:
Which of the following is the BEST way for an organization to enable risk treatment decisions?
An organization discovers significant vulnerabilities in a recently purchased commercial off-the-shelf software product which will not be corrected until the next release. Which of the following is the risk manager's BEST course of action?
An organization has implemented a preventive control to lock user accounts after three unsuccessful login attempts. This practice has been proven to be unproductive, and a change in the control threshold value has been recommended. Who should authorize changing this threshold?
Which of the following BEST assists in justifying an investment in automated controls?
Winch of the following is the BEST evidence of an effective risk treatment plan?
Which of the following roles is BEST suited to help a risk practitioner understand the impact of IT-related events on business objectives?
A newly hired risk practitioner finds that the risk register has not been updated in the past year. What is the risk practitioner's BEST course of action?
Several newly identified risk scenarios are being integrated into an organization's risk register. The MOST appropriate risk owner would be the individual who:
Which of the following should be the PRIMARY goal of developing information security metrics?
Which of the following is the GREATEST benefit of incorporating IT risk scenarios into the corporate risk register?
Which of the following is the MOST important outcome of reviewing the risk management process?
An organization's decision to remain noncompliant with certain laws or regulations is MOST likely influenced by:
Which of the following BEST indicates the effectiveness of anti-malware software?
In an organization where each division manages risk independently, which of the following would BEST enable management of risk at the enterprise level?
Which of the following will be the GREATEST concern when assessing the risk profile of an organization?
While reviewing the risk register, a risk practitioner notices that different business units have significant variances in inherent risk for the same risk scenario. Which of the following is the BEST course of action?
A deficient control has been identified which could result in great harm to an organization should a low frequency threat event occur. When communicating the associated risk to senior management the risk practitioner should explain:
Which of We following is the MOST effective control to address the risk associated with compromising data privacy within the cloud?
Which of the following should be the MOST important consideration when performing a vendor risk assessment?
Which of the following is a PRIMARY reason for considering existing controls during initial risk assessment?
Which of the following would BEST facilitate the maintenance of data classification requirements?
An organization has identified the need to implement an asset tiering model to establish the appropriate level of impact. Which of the following is the MOST effective risk assessment methodology for a risk practitioner to use for this initiative?
When assessing the maturity level of an organization's risk management framework, which of the following should be of GREATEST concern to a risk practitioner?
Of the following, whose input is ESSENTIAL when developing risk scenarios for the implementation of a third-party mobile application that stores customer data?
Which of the following should be done FIRST when a new risk scenario has been identified
Which of the following is the PRIMARY purpose for ensuring senior management understands the organization’s risk universe in relation to the IT risk management program?
Which of the following BEST helps to mitigate risk associated with excessive access by authorized users?
Which of the following is the BEST key performance indicator (KPI) to measure how effectively risk management practices are embedded in the project management office (PMO)?
Who is the BEST person to an application system used to process employee personal data?
Which of the following provides the MOST mitigation value for an organization implementing new Internet of Things (loT) devices?
An organization's IT department wants to complete a proof of concept (POC) for a security tool. The project lead has asked for approval to use the production data for testing purposes as it will yield the best results. Which of the following is the risk practitioner's BEST recommendation?
Which of the following is the GREATEST concern associated with the use of artificial intelligence (AI) language models?
When implementing an IT risk management program, which of the following is the BEST time to evaluate current control effectiveness?
A service organization is preparing to adopt an IT control framework to comply with the contractual requirements of a new client. Which of the following would be MOST helpful to the risk practitioner?
Which of the following events is MOST likely to trigger the need to conduct a risk assessment?
Which of the following should be accountable for ensuring that media containing financial information are adequately destroyed per an organization's data disposal policy?
Concerned about system load capabilities during the month-end close process, management requires monitoring of the average time to complete tasks and monthly reporting of the findings. What type of measure has been established?
Which of the following BEST enables the integration of IT risk management across an organization?
Which of the following is MOST important to include when reporting the effectiveness of risk management to senior management?
Which of the following is MOST important to identify when developing top-down risk scenarios?
If concurrent update transactions to an account are not processed properly, which of the following will MOST likely be affected?
Which of the following is the BEST response when a potential IT control deficiency has been identified?
Which of the following is the MOST important technology control to reduce the likelihood of fraudulent payments committed internally?
In an organization dependent on data analytics to drive decision-making, which of the following would BEST help to minimize the risk associated with inaccurate data?
Which of the following provides the MOST useful information to determine risk exposure following control implementations?
Which of the following is the GREATEST benefit to an organization when updates to the risk register are made promptly after the completion of a risk assessment?
Which of the following should be an element of the risk appetite of an organization?
Risk acceptance of an exception to a security control would MOST likely be justified when:
Analyzing trends in key control indicators (KCIs) BEST enables a risk practitioner to proactively identify impacts on an organization's:
The PRIMARY objective for requiring an independent review of an organization's IT risk management process should be to:
Which of the following would BEST indicate to senior management that IT processes are improving?
Which of the following provides the MOST up-to-date information about the effectiveness of an organization's overall IT control environment?
A risk manager has determined there is excessive risk with a particular technology. Who is the BEST person to own the unmitigated risk of the technology?
A PRIMARY advantage of involving business management in evaluating and managing risk is that management:
Which of the following approaches will BEST help to ensure the effectiveness of risk awareness training?
Which of the following should be of GREATEST concern lo a risk practitioner reviewing the implementation of an emerging technology?
Which of the following BEST enforces access control for an organization that uses multiple cloud technologies?
When reviewing a business continuity plan (BCP). which of the following would be the MOST significant deficiency?
Which of the following is the MOST important component in a risk treatment plan?
Which of the following is the MOST important objective of establishing an enterprise risk management (ERM) function within an organization?
When of the following provides the MOST tenable evidence that a business process control is effective?
Which of the following would BEST help an enterprise define and communicate its risk appetite?
Which of the following should be the FIRST consideration when a business unit wants to use personal information for a purpose other than for which it was originally collected?
Which of the following BEST indicates the risk appetite and tolerance level (or the risk associated with business interruption caused by IT system failures?
Which of the following is the MOST important input when developing risk scenarios?
Which of the following provides the BEST evidence that risk mitigation plans have been implemented effectively?
Which of the following is MOST important to sustainable development of secure IT services?
An organization has completed a project to implement encryption on all databases that host customer data. Which of the following elements of the risk register should be updated the reflect this change?
Which of the following IT key risk indicators (KRIs) provides management with the BEST feedback on IT capacity?
Which of the following is MOST important to understand when developing key risk indicators (KRIs)?
A risk practitioner is reporting on an increasing trend of ransomware attacks in the industry. Which of the following information is MOST important to include to enable an informed response decision by key stakeholders?
Due to a change in business processes, an identified risk scenario no longer requires mitigation. Which of the following is the MOST important reason the risk should remain in the risk register?
When testing the security of an IT system, il is MOST important to ensure that;
Which of the following conditions presents the GREATEST risk to an application?
A monthly payment report is generated from the enterprise resource planning (ERP) software to validate data against the old and new payroll systems. What is the BEST way to mitigate the risk associated with data integrity loss in the new payroll system after data migration?
Which of the following would be MOST helpful to a risk owner when making risk-aware decisions?
Which of the following would provide the MOST objective assessment of the effectiveness of an organization's security controls?
Which of the following would be of GREATEST assistance when justifying investment in risk response strategies?
Which of the following is the BEST indicator of the effectiveness of a control action plan's implementation?
A company has located its computer center on a moderate earthquake fault. Which of the following is the MOST important consideration when establishing a contingency plan and an alternate processing site?
Which of the following is the BEST course of action when risk is found to be above the acceptable risk appetite?
An organization is planning to outsource its payroll function to an external service provider Which of the following should be the MOST important consideration when selecting the provider?
Which of the following will BEST ensure that information security risk factors are mitigated when developing in-house applications?
Controls should be defined during the design phase of system development because:
Which of the following methods would BEST contribute to identifying obscure risk scenarios?
Which of the following key risk indicators (KRIs) is MOST effective for monitoring risk related to a bring your own device (BYOD) program?
A key risk indicator (KRI) indicates a reduction in the percentage of appropriately patched servers. Which of the following is the risk practitioner's BEST course of action?
Which of the following would be MOST beneficial as a key risk indicator (KRI)?
Which of the following controls would BEST reduce the likelihood of a successful network attack through social engineering?
Which of the following would offer the MOST insight with regard to an organization's risk culture?
Which of the following is MOST important for developing effective key risk indicators (KRIs)?
What is the GREATEST concern with maintaining decentralized risk registers instead of a consolidated risk register?
A risk practitioner has observed that risk owners have approved a high number of exceptions to the information security policy. Which of the following should be the risk practitioner's GREATEST concern?
A large organization is replacing its enterprise resource planning (ERP) system and has decided not to deploy the payroll module of the new system. Instead, the current payroll system will continue to be
used. Of the following, who should own the risk if the ERP and payroll system fail to operate as expected?
Which of the following is the BEST approach for determining whether a risk action plan is effective?
After migrating a key financial system to a new provider, it was discovered that a developer could gain access to the production environment. Which of the following is the BEST way to mitigate the risk in this situation?
An organization is measuring the effectiveness of its change management program to reduce the number of unplanned production changes. Which of the following would be the BEST metric to determine if the program is performing as expected?
Which of the following is MOST important for a risk practitioner to consider when evaluating plans for changes to IT services?
A recent audit identified high-risk issues in a business unit though a previous control self-assessment (CSA) had good results. Which of the following is the MOST likely reason for the difference?
A risk practitioner is reviewing the status of an action plan to mitigate an emerging IT risk and finds the risk level has increased. The BEST course of action would be to:
Who is MOST likely to be responsible for the coordination between the IT risk strategy and the business risk strategy?
Which of the following BEST contributes to the implementation of an effective risk response action plan?
What should a risk practitioner do FIRST upon learning a risk treatment owner has implemented a different control than what was specified in the IT risk action plan?
The PRIMARY reason for periodic penetration testing of Internet-facing applications is to:
Which of the following is the BEST indication of the effectiveness of a business continuity program?
A newly enacted information privacy law significantly increases financial penalties for breaches of personally identifiable information (Pll). Which of the following will MOST likely outcome for an organization affected by the new law?
What should a risk practitioner do FIRST when vulnerability assessment results identify a weakness in an application?
A bank has outsourced its statement printing function to an external service provider. Which of the following is the MOST critical requirement to include in the contract?
Which of the following indicates an organization follows IT risk management best practice?
Which of the following methods is the BEST way to measure the effectiveness of automated information security controls prior to going live?
Which of the following is the MOST important consideration when determining whether to accept residual risk after security controls have been implemented on a critical system?
Which of the following BEST helps to balance the costs and benefits of managing IT risk?
A payroll manager discovers that fields in certain payroll reports have been modified without authorization. Which of the following control weaknesses could have contributed MOST to this problem?
Which of the following is the GREATEST concern associated with the transmission of healthcare data across the internet?
Which of the following is MOST helpful to review when identifying risk scenarios associated with the adoption of Internet of Things (loT) technology in an organization?
Which of the following is MOST important to ensure when continuously monitoring the performance of a client-facing application?
An organization's risk practitioner learns a new third-party system on the corporate network has introduced vulnerabilities that could compromise corporate IT systems. What should the risk practitioner do
FIRST?
A bank wants to send a critical payment order via email to one of its offshore branches. Which of the following is the BEST way to ensure the message reaches the intended recipient without alteration?
A control owner responsible for the access management process has developed a machine learning model to automatically identify excessive access privileges. What is the risk practitioner's BEST course of action?
The implementation of a risk treatment plan will exceed the resources originally allocated for the risk response. Which of the following should be the risk owner's NEXT action?
Which of the following is the BEST key performance indicator (KPI) to measure the effectiveness of an anti-virus program?
A software developer has administrative access to a production application. Which of the following should be of GREATEST concern to a risk practitioner?
It is MOST important for a risk practitioner to have an awareness of an organization s processes in order to:
Which of the following will BEST help to ensure that information system controls are effective?
Which of the following is MOST critical to the design of relevant risk scenarios?
Which of the following is MOST helpful to management when determining the resources needed to mitigate a risk?
Which of the following risk register elements is MOST likely to be updated if the attack surface or exposure of an asset is reduced?
For no apparent reason, the time required to complete daily processing for a legacy application is approaching a risk threshold. Which of the following activities should be performed FIRST?
Sensitive data has been lost after an employee inadvertently removed a file from the premises, in violation of organizational policy. Which of the following controls MOST likely failed?
An organization is making significant changes to an application. At what point should the application risk profile be updated?
An organization's HR department has implemented a policy requiring staff members to take a minimum of five consecutive days leave per year to mitigate the risk of malicious insideractivities. Which of the following is the BEST key performance indicator (KPI) of the effectiveness of this policy?
Which of the following is the MOST important objective of embedding risk management practices into the initiation phase of the project management life cycle?
A business manager wants to leverage an existing approved vendor solution from another area within the organization. Which of the following is the risk practitioner's BEST course of action?
Which of the following is the PRIMARY reason to establish the root cause of an IT security incident?
Which of the following is the BEST way to ensure ongoing control effectiveness?
The BEST key performance indicator (KPI) to measure the effectiveness of a vulnerability remediation program is the number of:
It is MOST important to the effectiveness of an IT risk management function that the associated processes are:
What is MOST important for the risk practitioner to understand when creating an initial IT risk register?
Which of the following will be MOST effective to mitigate the risk associated with the loss of company data stored on personal devices?
The MOST important reason to aggregate results from multiple risk assessments on interdependent information systems is to:
Which of the following BEST indicates effective information security incident management?
The PRIMARY reason for periodically monitoring key risk indicators (KRIs) is to:
Before implementing instant messaging within an organization using a public solution, which of the following should be in place to mitigate data leakage risk?
Which of the following would provide the MOST comprehensive information for updating an organization's risk register?
Which of the following should an organization perform to forecast the effects of a disaster?
An organization is increasingly concerned about loss of sensitive data and asks the risk practitioner to assess the current risk level. Which of the following should the risk practitioner do FIRST?
Isaca Certification | CRISC Questions Answers | CRISC Test Prep | Certified in Risk and Information Systems Control Questions PDF | CRISC Online Exam | CRISC Practice Test | CRISC PDF | CRISC Test Questions | CRISC Study Material | CRISC Exam Preparation | CRISC Valid Dumps | CRISC Real Questions | Isaca Certification CRISC Exam Questions


