Following a ransomware incident, the network teamprovided a PCAP file, titled ransom.pcap, located in theInvestigations folder on the Desktop.
What is the full User-Agent value associated with theransomware demand file download. Enter your responsein the field below.
For this question you must log into GreenboneVulnerability Manager using Firefox. The URL is:https://10.10.55.4:9392 and credentials are:
Username:admin
Password:Secure-gvm!
A colleague performed a vulnerability scan but did notreview prior to leaving for a family emergency. It hasbeen determined that a threat actor is using CVE-2021-22145 in the wild. What is the host IP of the machinethat is vulnerable to this CVE?
The CISO has received a bulletin from law enforcementauthorities warning that the enterprise may be at risk ofattack from a specific threat actor. Review the bulletin
named CCOA Threat Bulletin.pdf on the Desktop.
Which of the following domain name(s) from the CCOAThreat Bulletin.pdf was contacted between 12:10 AMto 12:12 AM (Absolute) on August 17, 2024?
Analyze the file titled pcap_artifact5.txt on the AnalystDesktop.
Decode the C2 host of the attack. Enter your responsebelow.
The user of the Accounting workstation reported thattheir calculator repeatedly opens without their input.
Perform a query of startup items for the agent.nameaccounting-pc in the SIEM for the last 24 hours. Identifythe file name that triggered RuleName SuspiciousPowerShell. Enter your response below. Your responsemust include the file extension.
Which type of security model leverages the use of data science and machine learning (ML) to further enhance threat intelligence?
Which of the following should be completedFIRSTin a data loss prevention (OLP) system implementation project?
Which of the following is the PRIMARY purpose for an organization to adopt a cybersecurityframework?
Which of the following has been defined when a disaster recovery plan (DRP) requires daily backups?
Which of the following is MOST likely to result from a poorly enforced bring your own device (8YOD) policy?
Which of the following Is the MOST effective way to ensure an organization's management of supply chain risk remains consistent?
Which of the following is the MOST effective approach for tracking vulnerabilities in an organization's systems and applications?
Which of the following is MOST important for maintaining an effective risk management program?
An organization moving its payment card system into a separate location on its network (or security reasons is an example of network:
Which of the following is a technique for detecting anomalous network behavior that evolves using large data sets and algorithms?
Which of the following cyber crime tactics involves targets being contacted via text message by an attacker posing as a legitimate entity?
An insecure continuous integration and continuous delivery (CI/CD) pipeline would MOST likely lead to:
Which ofthe following is the PRIMARY purpose of load balancers in cloud networking?
A nation-state that is employed to cause financial damage on an organization is BEST categorized as:
The enterprise is reviewing its security posture byreviewing unencrypted web traffic in the SIEM.
How many logs are associated with well knownunencrypted web traffic for the month of December2023 (Absolute)? Note: Security Onion refers to logsas documents.
An employee has been terminated for policy violations.Security logs from win-webserver01 have been collectedand located in the Investigations folder on theDesktop as win-webserver01_logs.zip.
Generate a SHA256 digest of the System-logs.evtx filewithin the win-webserver01_logs.zip file and providethe output below.
The enterprise is reviewing its security posture byreviewing unencrypted web traffic in the SIEM.
How many unique IPs have received well knownunencrypted web connections from the beginning of2022 to the end of 2023 (Absolute)?
Your enterprise has received an alert bulletin fromnational authorities that the network has beencompromised at approximately 11:00 PM (Absolute) onAugust 19, 2024. The alert is located in the alerts folderwith filename, alert_33.pdf.
What is the name of the suspected malicious filecaptured by keyword process.executable at 11:04 PM?
The CISO has received a bulletin from law enforcementauthorities warning that the enterprise may be at risk ofattack from a specific threat actor. Review the bulletin
named CCOA Threat Bulletin.pdf on the Desktop.
Which host IP was targeted during the following timeframe: 11:39 PM to 11:43 PM (Absolute) on August 16,2024?
The network team has provided a PCAP file withsuspicious activity located in the Investigations folderon the Desktop titled, investigation22.pcap.
What date was the webshell accessed? Enter the formatas YYYY-MM-DD.
Analyze the file titled pcap_artifact5.txt on the AnalystDesktop.
Decode the targets within the file pcap_artifact5.txt.
Select the correct decoded targets below.
10cal.com/exam
clOud-s3cure.com
c0c0nutf4rms.net
h3avy_s3as.biz
b4ddata.org
Cyber Analyst Password:
For questions that require use of the SIEM, pleasereference the information below:
https://10.10.55.2
Security-Analyst!
CYB3R-4n4ly$t!
Email Address:
ccoatest@isaca.org
Password:Security-Analyst!
The enterprise has been receiving a large amount offalse positive alerts for the eternalblue vulnerability. TheSIEM rulesets are located in
/home/administrator/hids/ruleset/rules.
What is the name of the file containing the ruleset foreternalblue connections? Your response must includethe file extension.
Following a ransomware incident, the network teamprovided a PCAP file, titled ransom.pcap, located in theInvestigations folder on the Desktop.
What is the name of the file containing the ransomwaredemand? Your response must include the fileextension.
Your enterprise SIEM system is configured to collect andanalyze log data from various sources. Beginning at12:00 AM on December 4, 2024, until 1:00 AM(Absolute), several instances of PowerShell arediscovered executing malicious commands andaccessing systems outside of their normal workinghours.
What is the physical address of the web server that wastargeted with malicious PowerShell commands?
On the Analyst Desktop is a Malware Samples folderwith a file titled Malscript.viruz.txt.
What is the name of the service that the malware attempts to install?
Which ruleset can be applied in the
/home/administrator/hids/ruleset/rules directory?
Double-click each image to view it larger.
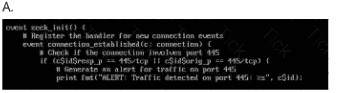
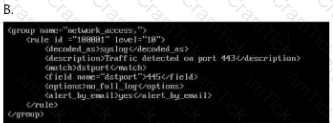
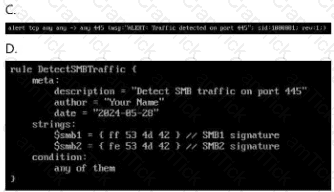
Your enterprise has received an alert bulletin fromnational authorities that the network has beencompromised at approximately 11:00 PM (Absolute) onAugust 19, 2024. The alert is located in the alerts folderwith filename, alert_33.pdf.
Use the IOCs to find the compromised host. Enter thehost name identified in the keyword agent.name fieldbelow.
The user of the Accounting workstation reported thattheir calculator repeatedly opens without their input.
The following credentials are used for thisquestion.
Username:Accounting
Password:1x-4cc0unt1NG-x1
Using the provided credentials, SSH to the Accountingworkstation and generate a SHA256 checksum of the filethat triggered RuleName Suspicious PowerShell usingeither certutil or Get-FileHash of the file causing theissue. Copy the hash and paste it below.
Before performing a penetration test for a client, it is MOST crucial to ensure:


