Scenario: A Citrix Architect needs to design a new Citrix ADC Gateway deployment to provide secure RDP access to backend Windows machines.
Click the Exhibit button to view additional requirements collected by the architect during the design discussions.
To meet the customer requirements, the architect should deploy the RDP proxy through _______, using a _________ solution. (Choose the correct option to complete the sentence.)
Scenario: A Citrix Architect needs to design a hybrid Citrix Virtual App and Citrix Virtual Desktop environment which will include Citrix Cloud as well as resource locations in an on-premises datacenter and Microsoft Azure.
Organizational details and requirements are as follows:
Click the Exhibit button to view the conceptual environment architecture.

The architect should use _____ in Location A, and should use ________ in Location B. (Choose the correct option to complete the sentence.)
Scenario: Based on a discussion between a Citrix Architect and a team of Workspacelab members, the MPX Logical layout for Workspacelab has been created across three (3) sites.
They captured the following requirements during the design discussion held for a Citrix ADC design project:
Which design decision must the architect make to meet the design requirements above?
Which three tasks can a Citrix Architect select and schedule using the Citrix ADC maintenance tasks? (Choose three.)
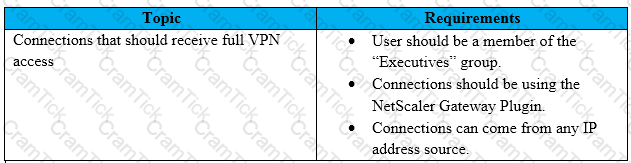
Scenario: A Citrix Architect has met with a team of Workspacelab members for a design discussion. They have captured the following requirements for NetScaler design project:
Which method must the architect utilize for user management between the two domains?
Which four settings can a Citrix Architect use to create a configuration job using Citrix Application Delivery Management? (Choose four.)
Scenario: A Citrix Architect needs to design a new multi-datacenter Citrix ADC deployment. The customer wants Citrix ADC to provide access to various backend resources by using Global Server Load Balancing (GSLB) in an Active-Active deployment. Click the Exhibit button to view additional requirements identified by the architect.

Which GSLB algorithm or method should the architect use for the deployment based on the stated requirements?
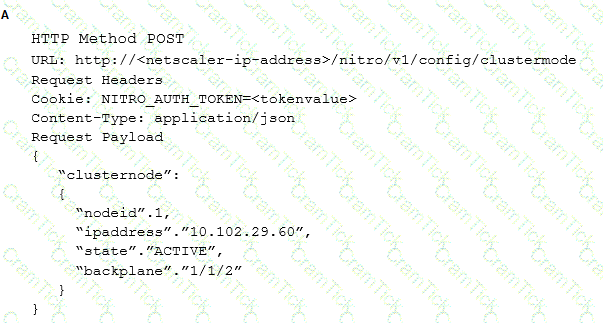
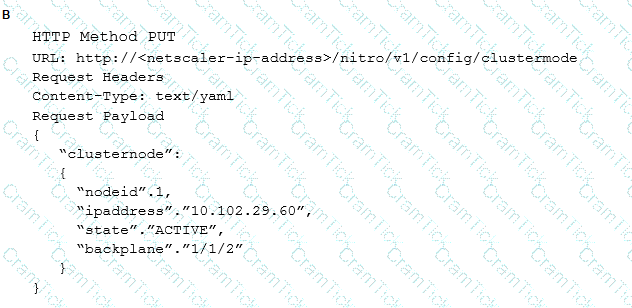
Which request can a Citrix Architect utilize to create a NITRO API command to add a NetScaler appliance with NSIP address 10.102.29.60 to the cluster?


Scenario: A junior Citrix Architect would like to use nFactor to perform authentication based on the domain. The junior architect has reached out to a supervisor for assistance and has been provided with the following step-by-step configuration guide:
What must the junior architect bind In order for the authentication to work correctly?
Scenario: A Citrix Architect needs to design a hybrid XenApp and XenApp and XenDesktop environment which will include Citrix Cloud as well as resource locations in on-premises datacenter and Microsoft Azure.
Organizational details and requirements are as follows:
Click the Exhibit button to view the conceptual environment architecture.

The architect should use ________ in Location A, and should use _________ in Location B. (Choose the correct option to complete the sentence.)
Which StyleBook group should a Citrix Architect use to deploy the configuration for Microsoft SharePoint servers on Citrix ADC Management and Analytics (Citrix Application Delivery Management)?
Scenario: A Citrix Architect needs to deploy a load balancing for an application server on the NetScaler. The authentication must be performed on the NetScaler. After the authentication, the Single Sign-on with the application servers must be performed using Kerberos impersonation.
Which three authentication methods can the Architect utilize to gather the credentials from the user in this scenario? (Choose three.)
Scenario: A Citrix Architect has configured two MPX devices in high availability mode with version 12.0.53.13 nc. After a discussion with the security team, the architect enabled the Application Firewall feature for additional protection.
In the initial deployment phase, the following security features were enabled:

What should the architect do to meet these requirements?
Which two methods can a Citrix Architect use to create a Heat Orchestration template? (Choose two)
Scenario: A Citrix Architect has set up NetScaler MPX devices in high availability mode with version 12.0. 53.13 nc. These are placed behind a Cisco ASA 5505 Firewall is configured to block traffic using access control lists. The network address translation (NAT) is also performed on the firewall.
The following requirements were captured by the architect during the discussion held as part of the NetScaler security implementation project with the customer’s security team:
The NetScaler device:
Which two security features should the architect configure to meet these requirements? (Choose two.)
Scenario: A Citrix Architect has sent the following request to the NetScaler:

Which response would indicate the successful execution of the NITRO command?
Which two settings must a Citrix Architect enable to deploy a shared VLAN on Citrix ADC VPX instance on an ESX platform? (Choose two.)
Which three parameters must a Citrix Architect designate when creating a new session policy? (Choose three.)
Scenario: A Citrix Architect and a team of Workspacelab members met to discuss a Citrix ADC design project. They captured the following requirements from this design discussion:
Click the Exhibit button to view the logical representation of the network.

On which firewall should the architect configure the access policy to permit the MEP communication between the sites?
Which three methods can a Citrix Architect use to assess the capabilities of a network infrastructure? (Choose three.)
Scenario: A Citrix Architect needs to design a NetScaler deployment in Microsoft Azure. An Active-Passive NetScaler VPX pair will provide load balancing for three distinct web applications. The architect has identified the following requirements:
For this deployment, the architect should configure each NetScaler VPX machine to have ______ network interface(s) and configure IP address by using ________. (Choose the correct option to complete the sentence).
Which two options should a Citrix Architect evaluate during a capabilities assessment? (Choose two.)
Scenario: A Citrix Architect needs to design a new NetScaler Gateway deployment to provide secure RDP access to backend Windows machines.
Click the Exhibit button to view additional requirements collected by the architect during the design discussions.

To meet the customer requirements, the architect should deploy the RDP proxy through ______ using a________ solution. (Choose the correct option to complete the sentence.)
What are three potential risks when examining the disaster recovery plan and implementation for a company? (Choose three)
Which two parameters are required to ensure that after authentication, the cookies can be transferred from browser to non-browser applications? (Choose two.)
Which three steps should a Citrix Architect complete to configure session settings for different user accounts or groups? (Choose three.)
Which session parameter does the default authorization setting control when authentication, authorization, and auditing profiles are configured?
Scenario: A Citrix Architect needs to assess an existing NetScaler Gateway deployment. During the assessment, the architect collected key requirements for VPN users, as well as the current session profile settings that are applied to those users.
Click the Exhibit button to view the information collected by the architect.
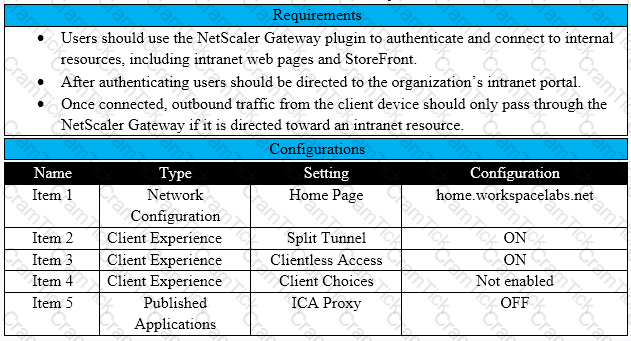
Which configurations should the architect change to meet all the stated requirements?
Scenario: A Citrix Architect has deployed Authentication for the SharePoint server through NetScaler. In order to ensure that users are able to edit or upload documents, the architect has configured persistent cookies on the NetScaler profile.
Which action should the architect take to ensure that cookies are shared between the browser and non-browser applications?
A Citrix Architect has deployed Citrix Application Delivery Management to monitor a high availability pair of Citrix ADC VPX devices.
The architect needs to deploy automated configuration backup to meet the following requirements:
Which SNMP trap will trigger the configuration file backup?
Under which two circumstances will a service be taken out of the slow start phase with automated slow start? (Choose Two)
Which step does a Citrix Architect need to ensure during the Define phase when following the Citrix Methodology?
Which session parameter does the default authorization setting control when authentication, authorization, and auditing profiles are configured?
A Citrix Architect can execute a configuration job using a DeployMasterConfiguration template on a NetScaler_________deployed_________. (Choose the correct option to complete sentence.)
Scenario: A Citrix Architect has met with a team of Workspacelab members for a design discussion They have captured the following requirements for the Citrix ADC design project:
The authentication must be deployed for the users from the workspacelab com and vendorlab com domains.
Which method must the architect utilize for user management between the two domains?
Scenario: A Citrix Architect needs to design a new Citrix Gateway deployment for a customer. During the design discussions, the architect documents the key
requirements for the Citrix Gateway.

Click the Exhibit button to view the key requirements.
The architect should configure Citrix Gateway for __________________in order to meet the stated requirements. (Choose the correct option to complete the
sentence.)
What can help a Citrix Architect prepare to discuss time scales and resource requirements?
Scenario: A Citrix Architect is asked by management at the Workspacelab organization to review their existing configuration and make the necessary upgrades. The architect recommends small changes to the pre-existing Citrix ADC configuration. Currently, the Citrix ADC MPX devices are configured in a high availability pair, and the outbound traffic is load balanced between two Internet service providers (ISPs). However, the failover is NOT happening correctly. The following requirements were discussed during the design requirement phase:
• The return traffic for a specific flow should be routed through the same path while using Link Load Balancing.
• The link should fail over even if the ISP router is up and intermediary devices to an ISP router are down.
• Traffic going through one ISP router should fail over to the secondary ISP, and the traffic should NOT flow through both routers simultaneously. What should the architect configure to meet this requirement?
A Citrix Architect needs to define the architect and operational processes required to implement and maintain the production environment.
In which phase of the Citrix Methodology will the architect define this?
Scenario: A Citrix Architect has configured two MPX devices in high availability mode with version 12.0.53.13 nc. After a discussion with the security team, the architect enabled the Application Firewall feature for additional protection.
In the initial deployment phase, the following security features were enabled:
After deployment in pre-production, the team identifies the following additional security features and changes as further requirements:
Click the Exhibit button to view an excerpt of the existing configuration.

What should the architect do to meet these requirements?
Scenario: Based on a discussion between a Citrix Architect and a team of Workspacelab members, the MPX Logical layout for Workspacelab has been created across three (3) sites.
The requirements captured during the design discussion held for a NetScaler design project are as follows:
How many Citrix ADC MPX appliances should the architect deploy at each site to meet the design requirements above?
CCE-N | 1Y0-440 Questions Answers | 1Y0-440 Test Prep | Architecting a Citrix Networking Solution Questions PDF | 1Y0-440 Online Exam | 1Y0-440 Practice Test | 1Y0-440 PDF | 1Y0-440 Test Questions | 1Y0-440 Study Material | 1Y0-440 Exam Preparation | 1Y0-440 Valid Dumps | 1Y0-440 Real Questions | CCE-N 1Y0-440 Exam Questions


