Fill in the blank RADIUS Accounting gets_____data from requests generated by the accounting client
Which of the following is used to extract state related information from packets and store that information in state tables?
Fill in the blank: Permanent VPN tunnels can be set on all tunnels in the community, on all tunnels for specific gateways, or__________.
When configuring Anti-Spoofing, which tracking options can an Administrator select?
Consider the Global Properties following settings:
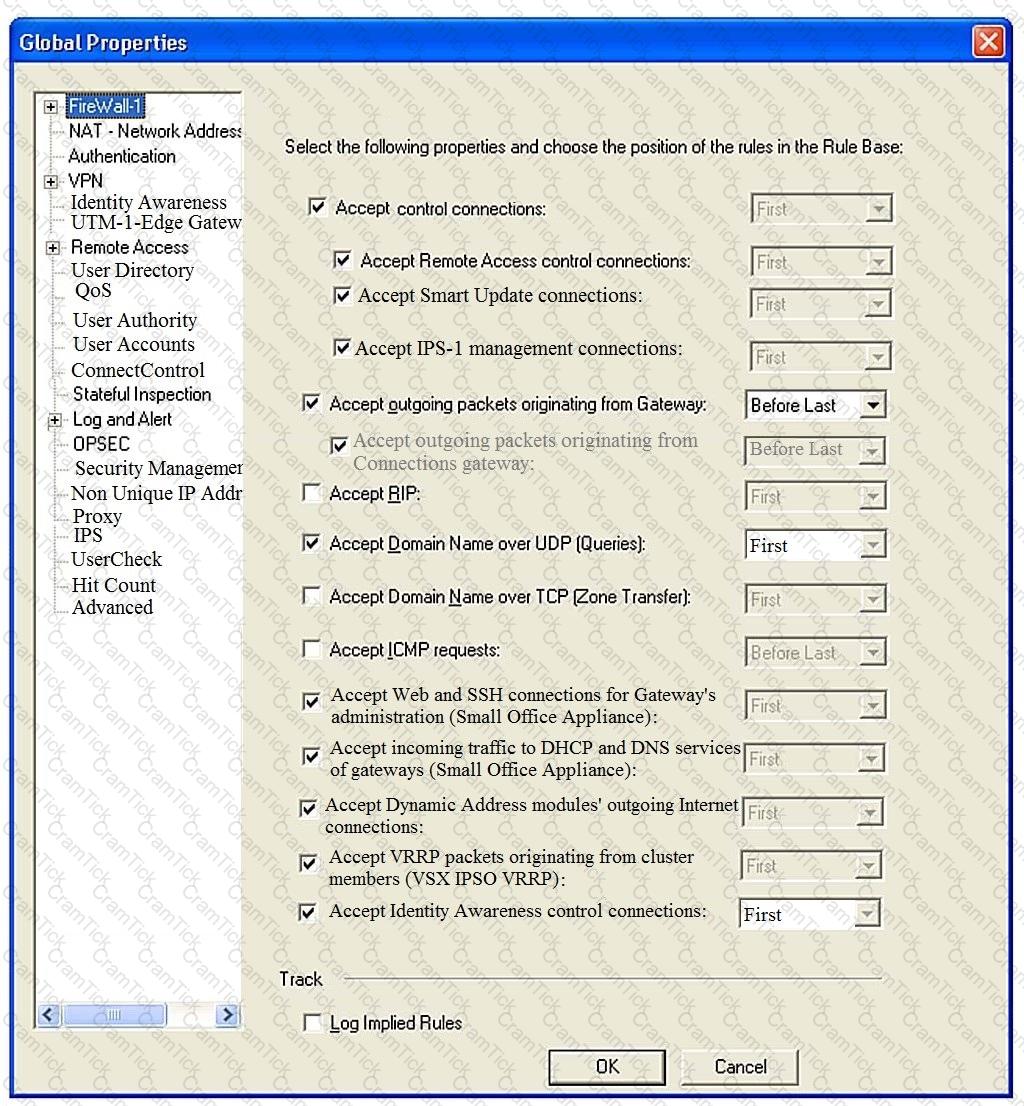
The selected option “Accept Domain Name over UDP (Queries)” means:
Which information is included in the “Extended Log” tracking option, but is not included in the “Log” tracking option?
Fill in the blank: When a policy package is installed, ________ are also distributed to the target installation Security Gateways.
When connected to the Check Point R80 Management Server using the SmartConsole the first administrator to connect has a lock on:
An administrator wishes to enable Identity Awareness on the Check Point firewalls. However they allow users to use company issued or personal laptops. Since the administrator cannot manage the personal laptops, which of the following methods would BEST suit this company?
You want to verify if there are unsaved changes in GAiA that will be lost with a reboot. What command can be used?
True or False: In a Distributed Environment, a Central License can be installed via CLI on a Security Gateway
In Logging and Monitoring, the tracking options are Log, Detailed Log and Extended Log. Which of the following options can you add to each Log, Detailed Log and Extended Log?
Due to high CPU workload on the Security Gateway, the security administrator decided to purchase a new multicore CPU to replace the existing single core CPU. After installation, is the administrator required to perform any additional tasks?
Identity Awareness allows the Security Administrator to configure network access based on which of the following?
Which Threat Prevention Software Blade provides comprehensive protection against malicious and unwanted network traffic, focusing on application and server vulnerabilities?
Which of the following statements about Site-to-Site VPN Domain-based is NOT true?
Route-based— The Security Gateways will have a Virtual Tunnel Interface (VTI) for each VPN Tunnel with a peer VPN Gateway. The Routing Table can have routes to forward traffic to these VTls. Any traffic routed through a VTI is automatically identified as VPN Traffic and is passed through the VPN Tunnel associated with the VTI.
The Online Activation method is available for Check Point manufactured appliances. How does the administrator use the Online Activation method?
Which option, when applied to a rule, allows all encrypted and non-VPN traffic that matches the rule?
Customer’s R80 management server needs to be upgraded to R80.10. What is the best upgrade method when the management server is not connected to the Internet?
What type of NAT is a one-to-one relationship where each host is translated to a unique address?
Session unique identifiers are passed to the web api using which http header option?
Gaia includes Check Point Upgrade Service Engine (CPUSE), which can directly receive updates for what components?
Which type of Endpoint Identity Agent includes packet tagging and computer authentication?
In Unified SmartConsole Gateways and Servers tab you can perform the following functions EXCEPT ________.
When a Security Gateway sends its logs to an IP address other than its own, which deployment option is installed?
Which Check Point software blade provides Application Security and identity control?
You have enabled "Extended Log" as a tracking option to a security rule. However, you are still not seeing any data type information. What is the MOST likely reason?
Which Check Point software blade prevents malicious files from entering a network using virus signatures and anomaly-based protections from ThreatCloud?
Tom has connected to the Management Server remotely using SmartConsole and is in the process of making some Rule Base changes, when he suddenly loses connectivity. Connectivity is restored shortly afterward. What will happen to the changes already made?
Bob and Joe both have Administrator Roles on their Gaia Platform. Bob logs in on the WebUI and then Joe logs in through CLI. Choose what BEST describes the following scenario, where Bob and Joe are both logged in:
How many users can have read/write access in Gaia Operating System at one time?
The ______ software blade package uses CPU-level and OS-level sandboxing in order to detect and block malware.
The Gateway Status view in SmartConsole shows the overall status of Security Gateways and Software Blades. What does the Status Attention mean?
Which method below is NOT one of the ways to communicate using the Management API’s?
Fill in the blank: The_____is used to obtain identification and security information about network users.
A Check Point Software license consists of two components, the Software Blade and the Software Container. There are ______ types of Software Containers: ________.
When URL Filtering is set, what identifying data gets sent to the Check Point Online Web Service?
You are asked to check the status of several user-mode processes on the management server and gateway. Which of the following processes can only be seen on a Management Server?
Examine the sample Rule Base.
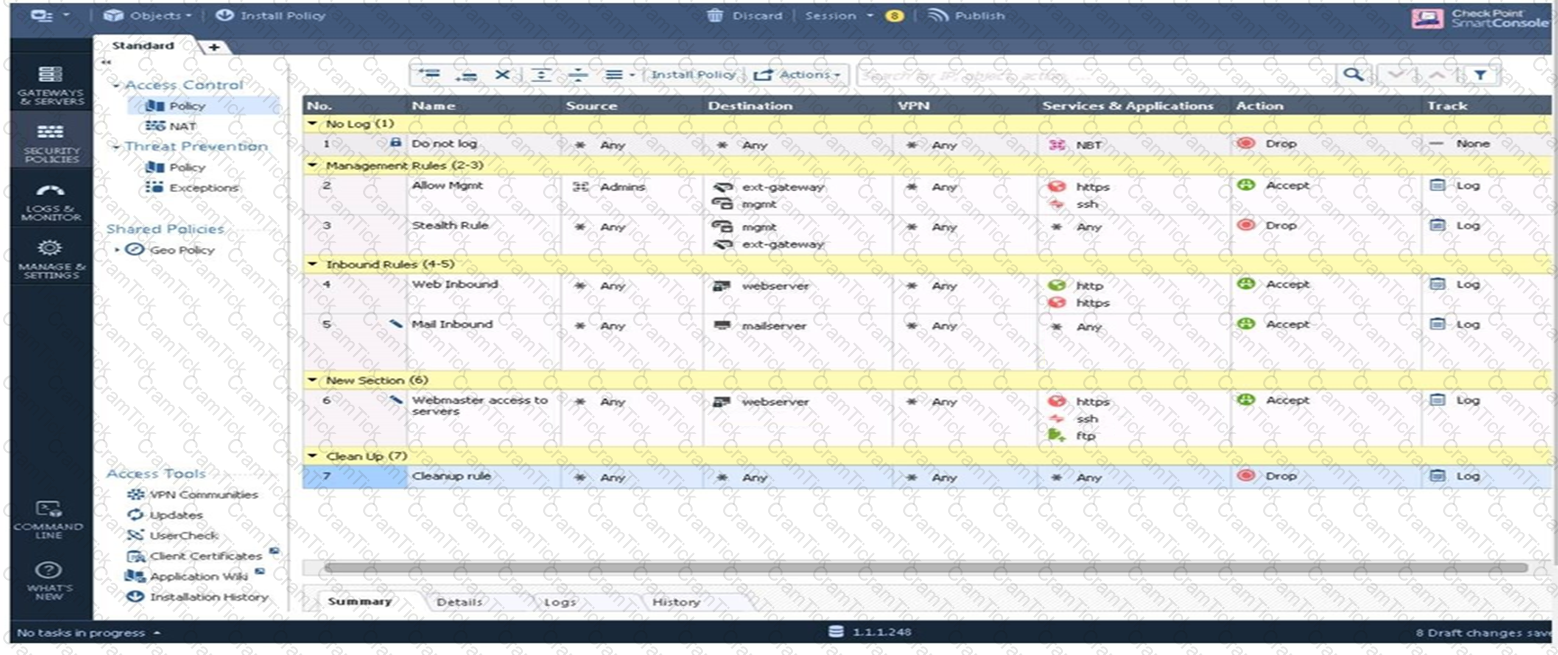
What will be the result of a verification of the policy from SmartConsole?
To ensure that VMAC mode is enabled, which CLI command you should run on all cluster members? Choose the best answer.
When you upload a package or license to the appropriate repository in SmartUpdate. where is the package or license stored?
When a SAM rule is required on Security Gateway to quickly block suspicious connections which are not restricted by the Security Policy, what actions does the administrator need to take?
CPU-level of your Security gateway is peaking to 100% causing problems with traffic. You suspect that the problem might be the Threat Prevention settings.
The following Threat Prevention Profile has been created.
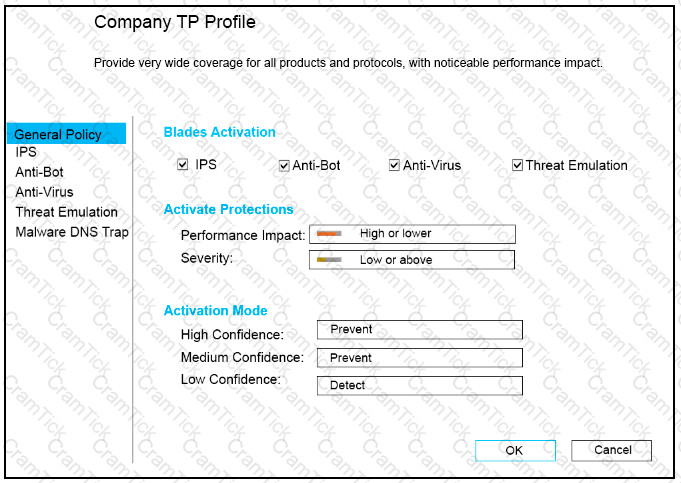
How could you tune the profile in order to lower the CPU load still maintaining security at good level? Select the BEST answer.
In R80 Management, apart from using SmartConsole, objects or rules can also be modified using:
Fill in the blank: The _____ feature allows administrators to share a policy with other policy packages.
What are valid authentication methods for mutual authenticating the VPN gateways?
When logging in for the first time to a Security management Server through SmartConsole, a fingerprint is saved to the:
Fill in the blank: A(n)_____rule is created by an administrator and configured to allow or block traffic based on specified criteria.
What are the software components used by Autonomous Threat Prevention Profiles in R8I.20 and higher?
From the Gaia web interface, which of the following operations CANNOT be performed on a Security Management Server?
The “Hit count” feature allows tracking the number of connections that each rule matches. Will the Hit count feature work independently from logging and Track the hits even if the Track option is set to “None”?
URL Filtering employs a technology, which educates users on web usage policy in real time. What is the name of that technology?
SmartConsole provides a consolidated solution for everything that is necessary for the security of an organization, such as the following
Which of the following is considered to be the more secure and preferred VPN authentication method?
When a Security Gateway communicates about its status to an IP address other than its own, which deployment option was chosen?
Fill in the blank: To create policy for traffic to or from a particular location, use the _____________.
Which option will match a connection regardless of its association with a VPN community?
Which single Security Blade can be turned on to block both malicious files from being downloaded as well as block websites known to host malware?
Fill in the blank: Each cluster, at a minimum, should have at least ___________ interfaces.
Of all the Check Point components in your network, which one changes most often and should be backed up most frequently?
In which scenario is it a valid option to transfer a license from one hardware device to another?
A stateful inspection firewall works by registering connection data and compiling this information. Where is the information stored?
Which one of the following is the preferred licensing model? Select the BEST answer
A layer can support different combinations of blades What are the supported blades:
Which is a main component of the Check Point security management architecture?
What are two basic rules Check Point recommending for building an effective security policy?
Rugged appliances are small appliances with ruggedized hardware and like Quantum Spark appliance they use which operating system?
Which type of Check Point license is tied to the IP address of a specific Security Gateway and cannot be transferred to a gateway that has a different IP address?
Which option, when applied to a rule, allows traffic to VPN gateways in specific VPN communities?
If there are two administrators logged in at the same time to the SmartConsole, and there are objects locked for editing, what must be done to make them available to other administrators? Choose the BEST answer
What needs to be configured if the NAT property ‘Translate destination on client side’ is not enabled in Global properties?
CCSA R81 |


