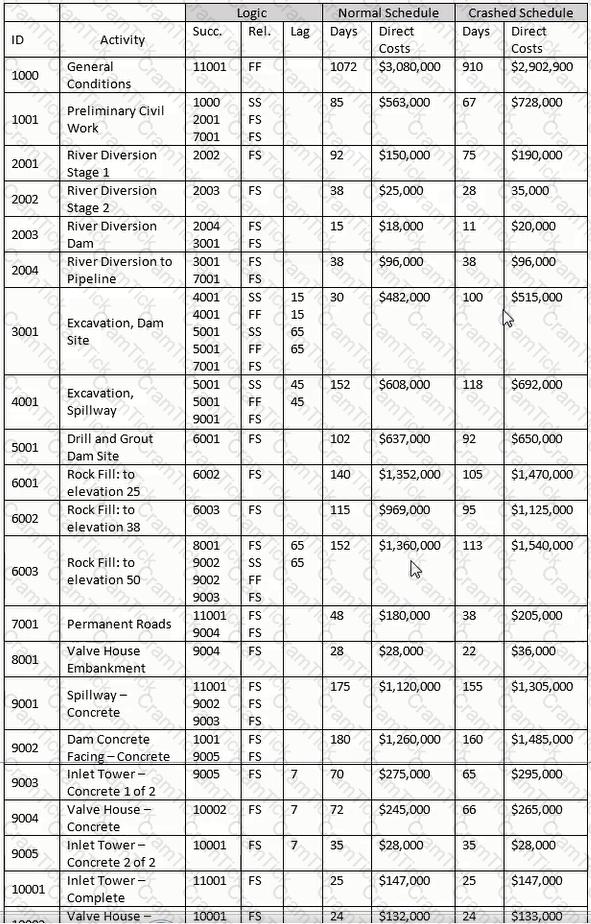
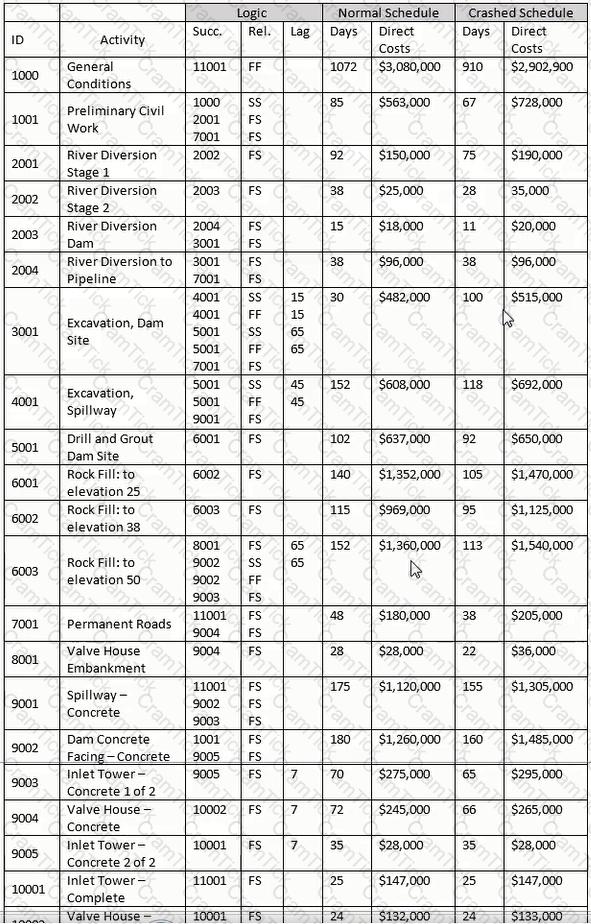
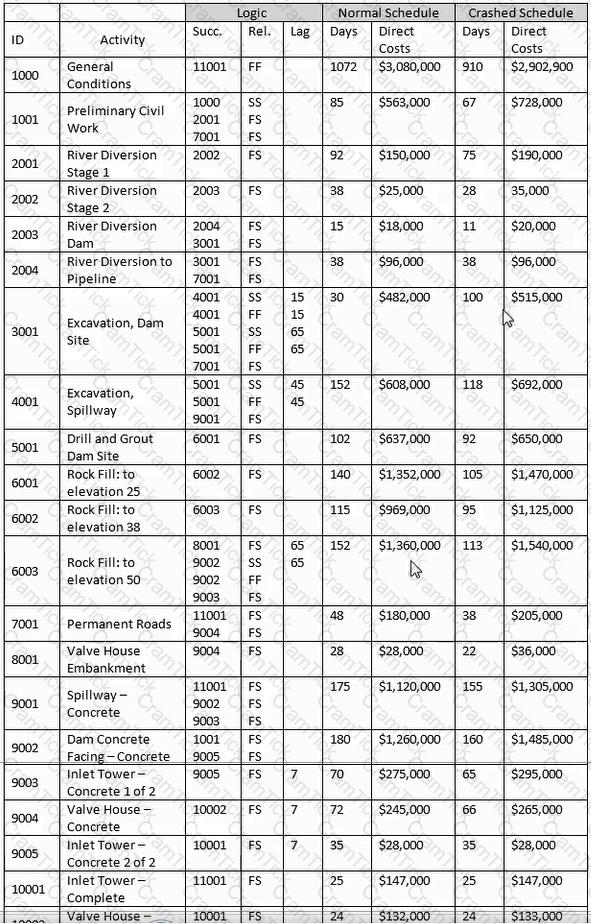
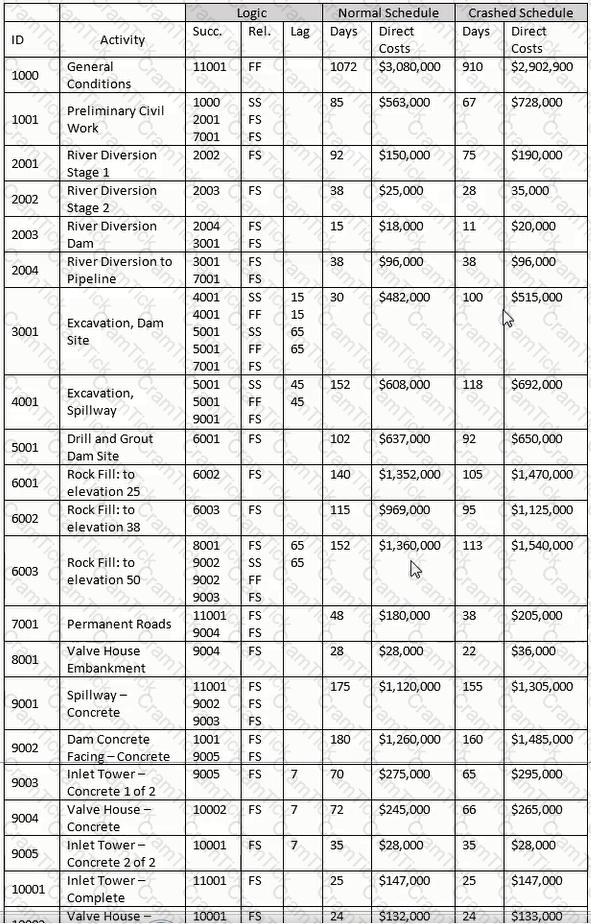
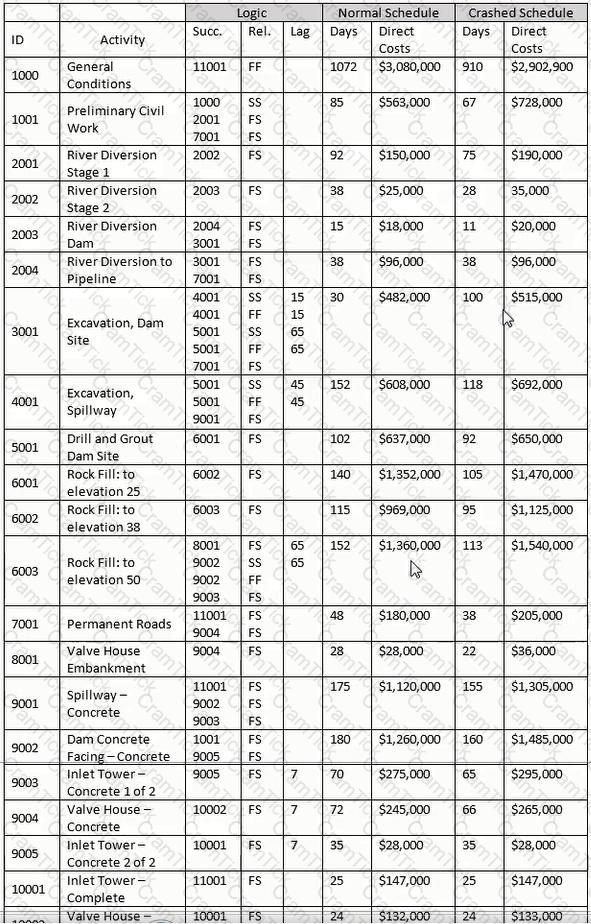
As a change to the network for the current update, activity 6002 is required to begin ten days after the beginning of activity 6001. Which is the simplest logic organization?
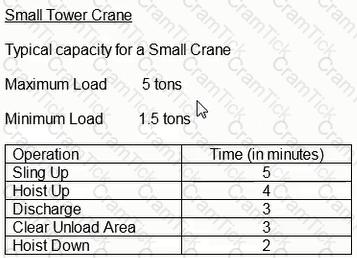
Each column must be poured in one day. Each column requires 2,000 cubic feet of concrete. The lift bucket has a capacity of 40 cubic feet. How many lifts will be required per column pour?
You are developing a detailed critical path schedule for a proposed petrochemical plant. The schedule will become a part of the project baseline document, which will be sent to the company's board of directors for its consideration. What document or resource is likely to be MOST valuable in determining the schedule's work activity durations?
Using the "normal" schedule, and assuming you are billing on the last day of the month for previous month and for appropriate partial months, how many invoices will you have for this project?
Total float is defined as the amount of time an activity can be delayed without impacting
Activity durations are normally estimated in an intuitive and subjective way. All of the following will improve duration accuracy EXCEPT
When using a detailed estimate as the basis for work package/activity durations, which element does NOT need to be identified before the activity durations can be calculated?
Activity 1001 started on the scheduled date but has slipped 10 days. Activity 10002 will slip 35 days. All remaining activities retain their original duration. What is the revised completion date?
Due to a testing delay, release of the product for manufacture is delayed by 5 workdays and the product manual misses its print window at the printer. If the printer is delayed by 10 workdays, what is the delay to produce release?
Using the normal schedule, given Activity 3001 and the relationship with Activity 4001. what is indicated?
If after calculating a schedule an activity exhibits negative total float, which of the following is certain? The activity
Using the "normal" schedule, what is the early finish date of activity 10002 and its total float?
What method would be the best way to determine the most likely as-built critical path of a project that is underway, and the schedule of which has been partially progressed?
Which of the following are NOT normally included in the project scope statement, either directly or by reference?
The expected remaining cost needed to complete an activity, group of activities or the project is the____________.
Which is NOT an industry-recognized methodology for quantifying critical delay?
Select the most appropriate explanation for use of a winter/wet weather seasonal calendar for use in this project?
Which of these letters, symbols or words best approximates the graphical shape of a project's cumulative BCWS?
An earned value-based project control system can use either of which two budgets as the basis of its calculations?
For the late finish for Activity 11001, select the most appropriate response for transitioning from the forward pass.
The sum of all budgets for work scheduled to be accomplished within a given time period is the ____________.
If a new hammock activity covering activities 6001 through 6003 is developed, what are governing predecessor and successor activities?
What day would Activity C complete if the duration of Activity A was reduced by five days?
Based on the stated costs, what percentage of the total cost comes from the 2000 series of activities?
Using the "normal" schedule, theoretically construct a hammock for activities 6001-6003. What is the duration of the hammock?
Professional Level | PSP Questions Answers | PSP Test Prep | Physical Security Professional Exam Questions PDF | PSP Online Exam | PSP Practice Test | PSP PDF | PSP Test Questions | PSP Study Material | PSP Exam Preparation | PSP Valid Dumps | PSP Real Questions | Physical Security Professional PSP Exam Questions


