Which CLI allows you to view the names of SD-WAN policy rules that send traffic to the specified virtual SD-WAN interface, along with the performance metrics?
A)

B)

C)
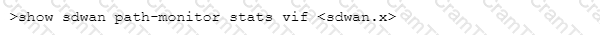
D)
Which of the following statements is valid with regard to Domain Name System (DNS) sinkholing?
Which domain permissions are required by the User-ID Agent for WMI Authentication on a Windows Server? (Choose three.)
What will a Palo Alto Networks next-generation firewall (NGFW) do when it is unable to retrieve a DNS verdict from the DNS cloud service in the configured lookup time?
An endpoint, inside an organization, is infected with known malware that attempts to make a command-and-control connection to a C2 server via the destination IP address
Which mechanism prevents this connection from succeeding?
What will best enhance security of a production online system while minimizing the impact for the existing network?
Which statement best describes the business value of Palo Alto Networks Zero Touch Provisioning (ZTP)?
A potential customer requires an NGFW solution which enables high-throughput, low-latency network security, all while incorporating unprecedented features and technology. They need a solution that solves the performance problems that plague today's security infrastructure.
Which aspect of the Palo Alto Networks NGFW capabilities can you highlight to help them address the requirements?
In Panorama, which three reports or logs will help identify the inclusion of a host source in a command-and-control (C2) incident? (Choose three.)
Select the BOM for the Prisma Access, to provide access for 5500 mobile users and 10 remote locations (100Mbps each) for one year, including Base Support and minimal logging. The customer already has 4x PA5220r 8x PA3220,1x Panorama VM for 25 devices.
An administrator wants to justify the expense of a second Panorama appliance for HA of the management layer.
The customer already has multiple M-100s set up as a log collector group. What are two valid reasons for deploying Panorama in High Availability? (Choose two.)
Which is the smallest Panorama solution that can be used to manage up to 2500 Palo Alto Networks Next Generation firewalls?
A customer is concerned about malicious activity occurring directly on their endpoints and will not be visible to their firewalls.
Which three actions does the Traps agent execute during a security event, beyond ensuring the prevention of this activity? (Choose three.)
Which proprietary technology solutions will allow a customer to identify and control traffic sources regardless of internet protocol (IP) address or network segment?
Which two features are found in a Palo Alto Networks NGFW but are absent in a legacy firewall product? (Choose two.)
A client chooses to not block uncategorized websites.
Which two additions should be made to help provide some protection? (Choose two.)
The firewall includes predefined reports, custom reports can be built for specific data and actionable tasks, or predefined and custom reports can be combined to compile information needed to monitor network security.
The firewall provides which three types of reports? (Choose three.)
What are three purposes for the Eval Systems, Security Lifecycle Reviews and Prevention Posture Assessment tools? (Choose three.)
Which two components must be configured within User-ID on a new firewall that has been implemented? (Choose two.)
What are two core values of the Palo Alto Network Security Operating Platform? (Choose two.}
Which are the three mandatory components needed to run Cortex XDR? (Choose three.)
Which four steps of the cyberattack lifecycle does the Palo Alto Networks Security Operating Platform prevent? (Choose four.)
XYZ Corporation has a legacy environment with asymmetric routing. The customer understands that Palo Alto Networks firewalls can support asymmetric routing with redundancy.
Which two features must be enabled to meet the customer’s requirements? (Choose two.)
In which two cases should the Hardware offering of Panorama be chosen over the Virtual Offering? (Choose two.)
The need for a file proxy solution, virus and spyware scanner, a vulnerability scanner, and HTTP decoder for URL filtering is handled by which component in the NGFW?
Which option is required to Activate/Retrieve a Device Management License on the M-100 Appliance after the Auth Codes have been activated on the Palo Alto Networks Support Site?
The Palo Ao Networks Cloud Identity Engino (CIE) includes which service that supports identity Providers (ldP)?
What is the key benefit of Palo Alto Networks Single Pass Parallel Processing design?
Which two methods are used to check for Corporate Credential Submissions? (Choose two.)
Which two configuration elements can be used to prevent abuse of stolen credentials? (Choose two.)
A customer requires an analytics tool with the following attributes:
- Uses the logs on the firewall to detect actionable events on the network
- Automatically processes a series of related threat events that, when combines, indicate a likely comprised host on the network
- Pinpoints the area of risk and allows for assessment of the risk to action can be taken to prevent exploitation of network resources
Which feature of PAN-OS will address these requirements?
A customer worried about unknown attacks is hesitant to enable SSL decryption due to privacy
and regulatory issues. How does the platform address the customer’s concern?
PSE-Strata Professional | PSE-Strata Questions Answers | PSE-Strata Test Prep | Palo Alto Networks System Engineer Professional - Strata Questions PDF | PSE-Strata Online Exam | PSE-Strata Practice Test | PSE-Strata PDF | PSE-Strata Test Questions | PSE-Strata Study Material | PSE-Strata Exam Preparation | PSE-Strata Valid Dumps | PSE-Strata Real Questions | PSE-Strata Professional PSE-Strata Exam Questions


