Which resources can be added in scope while creating a vulnerability policy for continuous integration?
A business unit has acquired a company that has a very large AWS account footprint. The plan is to immediately start onboarding the new company’s AWS accounts into Prisma Cloud Enterprise tenant immediately. The current company is currently not using AWS Organizations and will require each account to be onboarded individually.
The business unit has decided to cover the scope of this action and determined that a script should be written to onboard each of these accounts with general settings to gain immediate posture visibility across the accounts.
Which API endpoint will specifically add these accounts into the Prisma Cloud Enterprise tenant?
Which type of compliance check is available for rules under Defend > Compliance > Containers and Images > CI?
Which role must be assigned to DevOps users who need access to deploy Container and Host Defenders in Compute?
The Prisma Cloud administrator has configured a new policy.
Which steps should be used to assign this policy to a compliance standard?
On which cloud service providers can you receive new API release information for Prisma Cloud?
Which three public cloud providers are supported for VM image scanning? (Choose three.)
You are tasked with configuring a Prisma Cloud build policy for Terraform. What type of query is necessary to complete this policy?
Which file extension type is supported for Malware scanning in Prisma Cloud Data Security (PCDS)?
A customer has a requirement to terminate any Container from image topSecret:latest when a process named ransomWare is executed.
How should the administrator configure Prisma Cloud Compute to satisfy this requirement?
Which two variables must be modified to achieve automatic remediation for identity and access management (IAM) alerts in Azure cloud? (Choose two.)
Which two proper agentless scanning modes are supported with Prisma Cloud? (Choose two).
A DevOps lead reviewed some system logs and notices some odd behavior that could be a data exfiltration attempt. The DevOps lead only has access to vulnerability data in Prisma Cloud Compute, so the DevOps lead passes this information to SecOps.
Which pages in Prisma Cloud Compute can the SecOps lead use to investigate the runtime aspects of this attack?
What is required for Prisma Cloud to successfully execute auto-remediation commands?
A customer wants to monitor its Amazon Web Services (AWS) accounts via Prisma Cloud, but only needs the resource configuration to be monitored at present.
Which two pieces of information are needed to onboard this account? (Choose two.)
Web-Application and API Security (WAAS) provides protection for which two protocols? (Choose two.)
The security auditors need to ensure that given compliance checks are being run on the host. Which option is a valid host compliance policy?
When would a policy apply if the policy is set under Defend > Vulnerability > Images > Deployed?
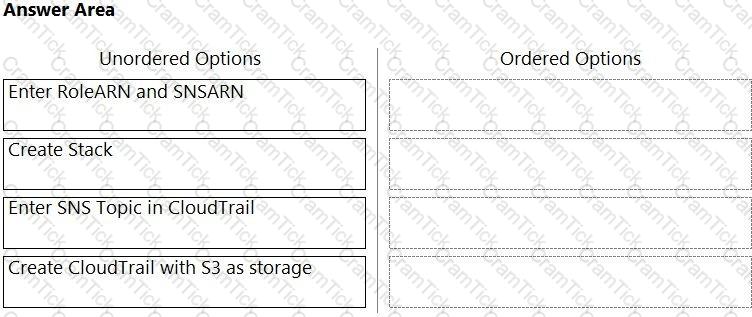
Order the steps involved in onboarding an AWS Account for use with Data Security feature.
If you are required to run in an air-gapped environment, which product should you install?
While writing a custom RQL with array objects in the investigate page, which type of auto-suggestion a user can leverage?
A customer is reviewing Container audits, and an audit has identified a cryptominer attack. Which three options could have generated this audit? (Choose three.)
Which three steps are involved in onboarding an account for Data Security? (Choose three.)
In which Console menu would an administrator verify whether a custom compliance check is failing or passing?
A security team notices a number of anomalies under Monitor > Events. The incident response team works with the developers to determine that these anomalies are false positives.
What will be the effect if the security team chooses to Relearn on this image?
A customer has a development environment with 50 connected Defenders. A maintenance window is set for Monday to upgrade 30 stand-alone Defenders in the development environment, but there is no maintenance window available until Sunday to upgrade the remaining 20 stand-alone Defenders.
Which recommended action manages this situation?
A customer does not want alerts to be generated from network traffic that originates from trusted internal networks.
Which setting should you use to meet this customer’s request?
Which three fields are mandatory when authenticating the Prisma Cloud plugin in the IntelliJ application? (Choose three.)
What is the maximum number of access keys a user can generate in Prisma Cloud with a System Admin role?
Which action must be taken to enable a user to interact programmatically with the Prisma Cloud APIs and for a nonhuman entity to be enabled for the access keys?
An administrator has access to a Prisma Cloud Enterprise.
What are the steps to deploy a single container Defender on an ec2 node?
What should be used to associate Prisma Cloud policies with compliance frameworks?
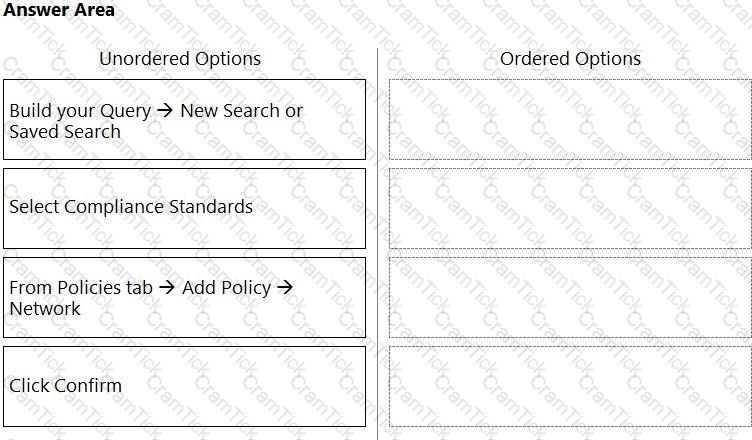
What is the order of steps to create a custom network policy?
(Drag the steps into the correct order of occurrence, from the first step to the last.)
Creation of a new custom compliance standard that is based on other individual custom compliance standards needs to be automated.
Assuming the necessary data from other standards has been collected, which API order should be used for this new compliance standard?
An S3 bucket within AWS has generated an alert by violating the Prisma Cloud Default policy “AWS S3 buckets are accessible to public”. The policy definition follows:
config where cloud.type = 'aws' AND api.name='aws-s3api-get-bucket-acl' AND json.rule="((((acl.grants[? (@.grantee=='AllUsers')] size > 0) or policyStatus.isPublic is true) and publicAccessBlockConfiguration does not exist) or ((acl.grants[?(@.grantee=='AllUsers')] size > 0) and publicAccessBlockConfiguration.ignorePublicAcis is false) or (policyStatus.isPublic is true and publicAccessBlockConfiguration.restrictPublicBuckets is false)) and websiteConfiguration does not exist"
Why did this alert get generated?
An administrator needs to detect and alert on any activities performed by a root account.
Which policy type should be used?
Given the following information, which twistcli command should be run if an administrator were to exec into a running container and scan it from within using an access token for authentication?
• Console is located at https://prisma-console.mydomain.local
• Token is: TOKEN_VALUE
• Report ID is: REPORTJD
• Container image running is: myimage:latest
Which three types of buckets exposure are available in the Data Security module? (Choose three.)
Which three actions are available for the container image scanning compliance rule? (Choose three.)
Which policy type provides information about connections from suspicious IPs in a customer database?
Which three OWASP protections are part of Prisma Cloud Web-Application and API Security (WAAS) rule? (Choose three.)
In Azure, what permissions need to be added to Management Groups to allow Prisma Cloud to calculate net effective permissions?
What improves product operationalization by adding visibility into feature utilization and missed opportunities?
A customer has serverless functions that are deployed in multiple clouds.
Which serverless cloud provider is covered be “overly permissive service access” compliance check?
Which three actions are required in order to use the automated method within Azure Cloud to streamline the process of using remediation in the identity and access management (IAM) module? (Choose three.)
A container and image compliance rule has been configured by enabling all checks; however, upon review, the container's compliance view reveals only the entries in the image below.
What is the appropriate action to take next?
What factor is not used in calculating the net effective permissions for a resource in AWS?
Given the following RQL:
event from cloud.audit_logs where operation IN (‘CreateCryptoKey’, ‘DestroyCryptoKeyVersion’, ‘v1.compute.disks.createSnapshot’)
Which audit event snippet is identified?
A)
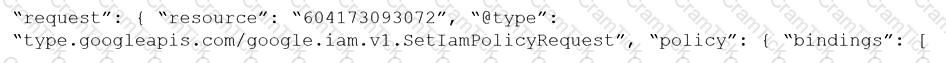
B)
C)
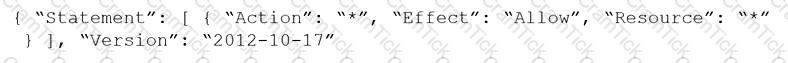
D)

An administrator has been tasked with creating a custom service that will download any existing compliance report from a Prisma Cloud Enterprise tenant.
In which order will the APIs be executed for this service?
(Drag the steps into the correct order of occurrence, from the first step to the last.)

What must be created in order to receive notifications about alerts generated when the operator is away from the Prisma Cloud Console?
Given an existing ECS Cluster, which option shows the steps required to install the Console in Amazon ECS?
What will happen when a Prisma Cloud Administrator has configured agentless scanning in an environment that also has Host and Container Defenders deployed?
A Prisma Cloud administrator is onboarding a single GCP project to Prisma Cloud. Which two steps can be performed by the Terraform script? (Choose two.)
Which policy type should be used to detect and alert on cryptominer network activity?
Which three options for hardening a customer environment against misconfiguration are included in Prisma Cloud Compute compliance enforcement for hosts? (Choose three.)
Which “kind” of Kubernetes object is configured to ensure that Defender is acting as the admission controller?
Which two required request headers interface with Prisma Cloud API? (Choose two.)
Which ROL query is used to detect certain high-risk activities executed by a root user in AWS?
A security team has been asked to create a custom policy.
Which two methods can the team use to accomplish this goal? (Choose two.)
Given the following audit event activity snippet:
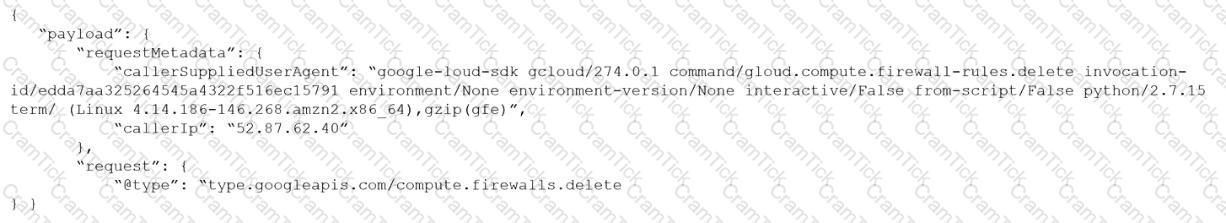
Which RQL will be triggered by the audit event?
A)
B)
C)
D)
Cloud Security Engineer | PCCSE Questions Answers | PCCSE Test Prep | Prisma Certified Cloud Security Engineer Questions PDF | PCCSE Online Exam | PCCSE Practice Test | PCCSE PDF | PCCSE Test Questions | PCCSE Study Material | PCCSE Exam Preparation | PCCSE Valid Dumps | PCCSE Real Questions | Cloud Security Engineer PCCSE Exam Questions


