Exhibit
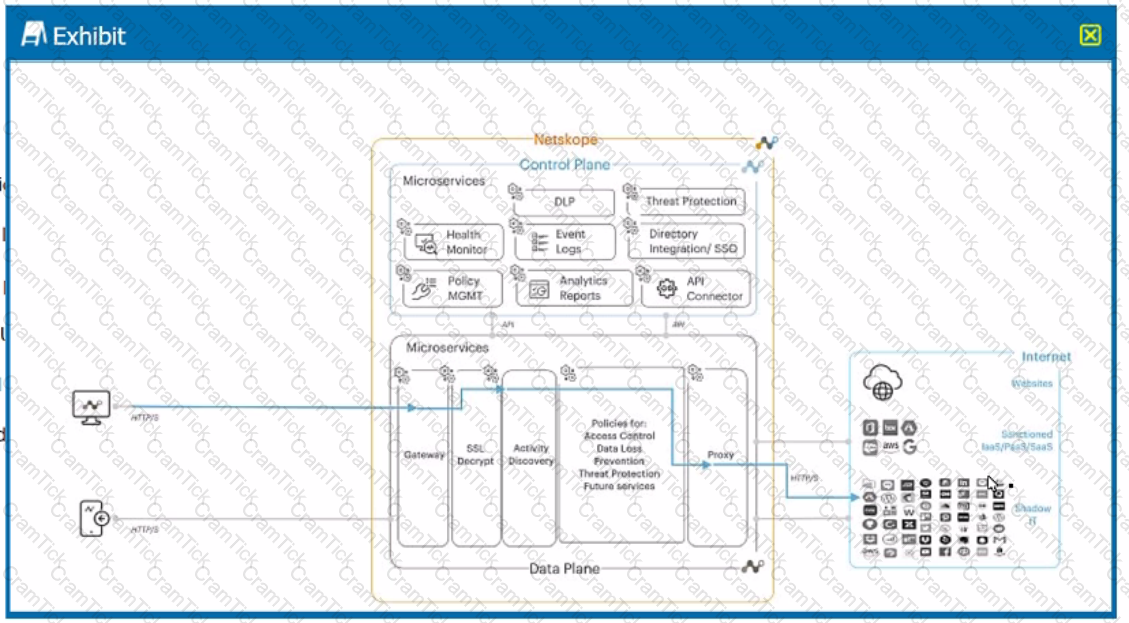
A user is connected to a cloud application through Netskope's proxy.
In this scenario, what information is available at Skope IT? (Choose three.)
A company user cannot open a sports news site. You want to review the category of the website and see how the rules are applied even though this category is allowed. In this scenario, which action will accomplish this task?
Which two statements describe a website categorized as a domain generated algorithm (DGA)? (Choose two.)
Which two functions are available for both inline and API protection? (Choose two.)
Which Netskope component would an administrator use to see an overview of private application usage and performance?
Your department is asked to report on GDPR data publicly exposed in Microsoft 365, Salesforce. and Slack-sanctioned cloud applications. Which deployment model would you use to discover this data?
Which three statements are correct about Netskope's NewEdge Security Cloud Network Infrastructure? (Choose three.)
You are asked to review files affected by malware in your organization. In this scenario, which two actions are possible and would be accessible from the Netskope UI -> Incidents --> Malware? (Choose two)
Which two traffic steering configurations are supported by Netskope? (Choose two.)
Click the Exhibit button.

You configured a set of Cloud Firewall policies as shown in the exhibit and changed your Steering Configuration to All Traffic for Group A and Group B. Users in Group A report that they are unable to access a third-party server using TCP port 3389. Referring to the exhibit, which action correctly describes how you would allow these connections without allowing unnecessary access?
A Netskope administrator wants to create a policy to quarantine files based on sensitive content.
In this scenario, which variable must be included in the policy to achieve this goal?
Click the Exhibit button.
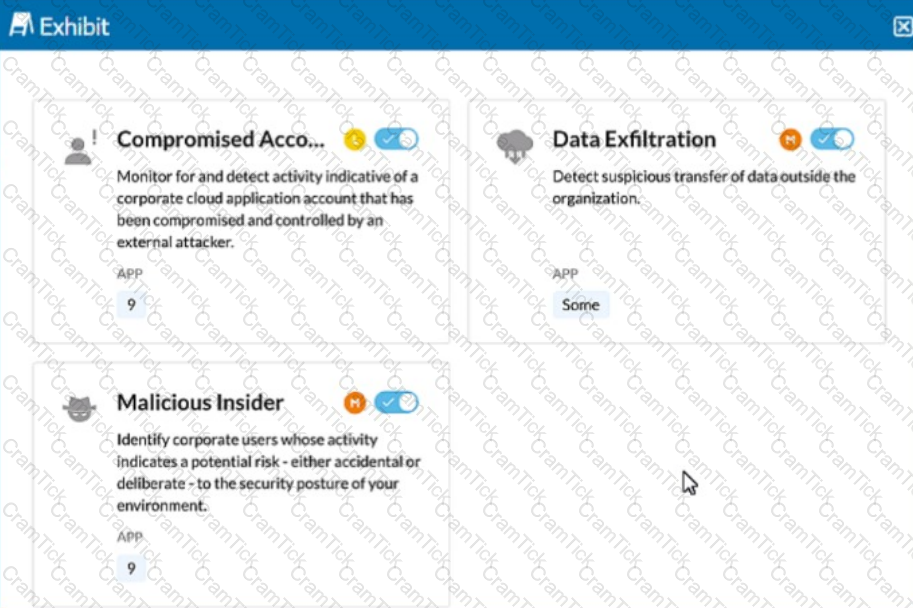
The exhibit shows security rules that are part of which component of the Netskope platform?
What are two correct methods to gather logs from the Netskope Client? (Choose two.)
What are two characteristics of Netskope's Private Access Solution? (Choose two.)
You investigate a suspected malware incident and confirm that it was a false alarm.
You want to take into account some recent adjustments to CCI scoring that were made in your Netskope tenant.
In this scenario, which two CCI attributes in the Ul would be used in a Real-time Protection policy? (Choose two.)
You need to block all users from uploading data files into risky collaboration applications. Which element must you configure within Netskope's CASB to accomplish this task?
You want to set up a Netskope API connection to Box.
What two actions must be completed to enable this connection? (Choose two.)
Click the Exhibit button.
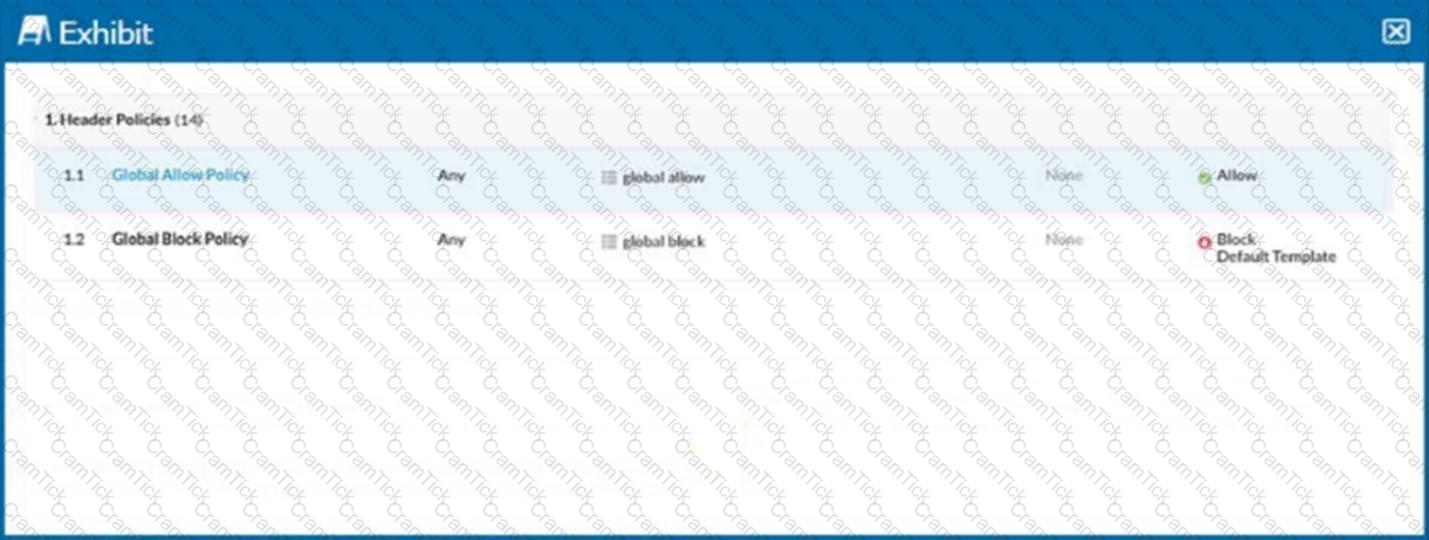
Referring to the exhibit, you have a user reporting that a blocked website is needed for legitimate business reasons. Upon review, you determine that the user has been blocked by the Global Block policy. You need to create an exception forthat domain. You create a custom URL list that includes the domain.
In this scenario, which two actions would allow this access? (Choose two.)
Digital Experience Management (DEM) allows an administrator to monitor which two areas? (Choose two.)
What are two primary advantages of Netskope's Secure Access Service Edge (SASE) architecture? (Choose two.
Which two statements are correct about DLP Incidents in the Netskope platform? (Choose two.)
You are working with traffic from applications with pinned certificates. In this scenario, which statement is correct?
Which two statements are correct about Netskope’s NewEdge Security Cloud Network Infrastructure? (Choose two.)
Click the Exhibit button.
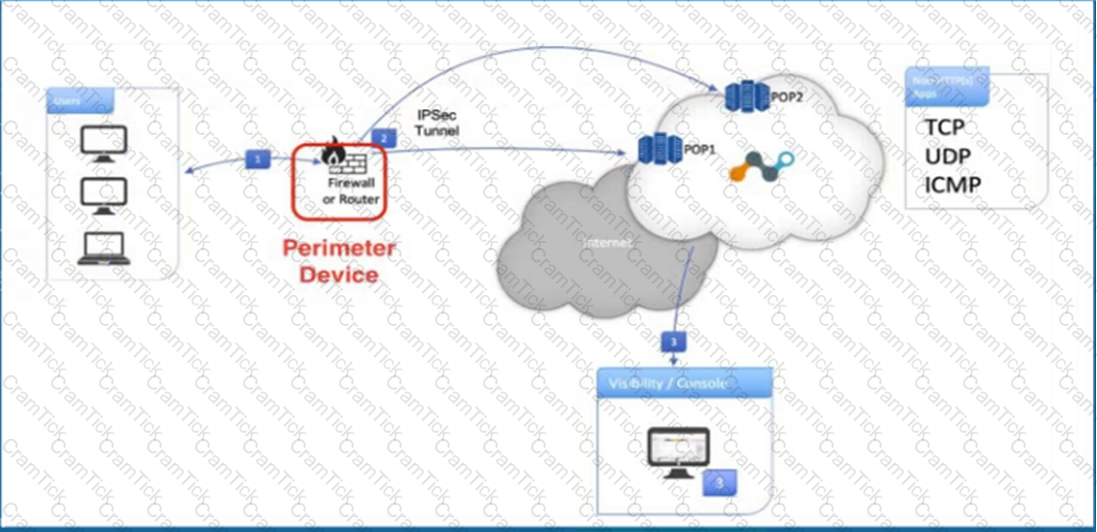
Referring to the exhibit, what are two recommended steps to be set on the perimeter device to monitor IPsec tunnels to a Netskope data plane? (Choose two.)
You just deployed the Netskope client in Web mode and several users mention that their messenger application is no longer working. Although you have a specific real-time policy that allows this application, upon further investigation you discover that it is using proprietary encryption. You need to permit access to all the users and maintain some visibility.
In this scenario, which configuration change would accomplish this task?
What is the limitation of using a legacy proxy compared to Netskope's solution?
Your company asks you to obtain a detailed list of all events from the last 24 hours for a specific user. In this scenario, what are two methods to accomplish this task? (Choose two.)
When using an out-of-band API connection with your sanctioned cloud service, what are two capabilities available to the administrator? (Choose two.)
You have applied a DLP Profile to block all Personally Identifiable Information data uploads to Microsoft 365 OneDrive. DLP Alerts are not displayed and no OneDrive-related activities are displayed in the Skope IT App Events table.
In this scenario, what are two possible reasons for this issue? (Choose two.)
Your company started deploying the latest version of the Netskope Client and you want to track the progress and device count using Netskope.
Which two statements are correct in this scenario? (Choose two.)
Your company has implemented Netskope's Cloud Firewall and requires that all FTP connections are blocked regardless of the ports being used.
Which two statements correctly identify how to block FTP access? (Choose two.)
NCCSA |


