73
If Internet Service is already selected as Source in a firewall policy, which other configuration objects can be added to the Source filed of a firewall policy?
Examine the exhibit, which contains a virtual IP and firewall policy configuration.


The WAN (port1) interface has the IP address 10.200. 1. 1/24. The LAN (port2) interface has the IP address 10.0. 1.254/24.
The first firewall policy has NAT enabled on the outgoing interface address. The second firewall policy is configured with a VIP as the destination address. Which IP address will be used to source NAT the Internet traffic coming from a workstation with the IP address 10.0. 1. 10/24?
113
What inspection mode does FortiGate use if it is configured as a policy-based next-generation firewall (NGFW)?
Refer to the exhibit showing a debug flow output.
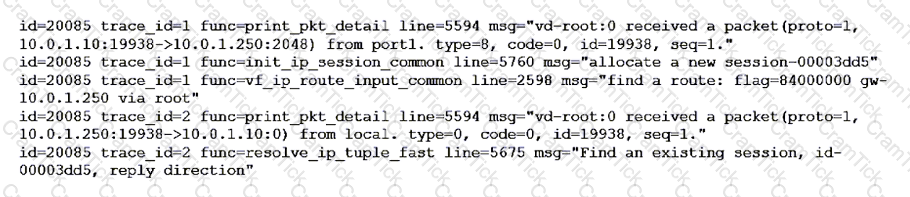
What two conclusions can you make from the debug flow output? (Choose two.)
Refer to the exhibits.
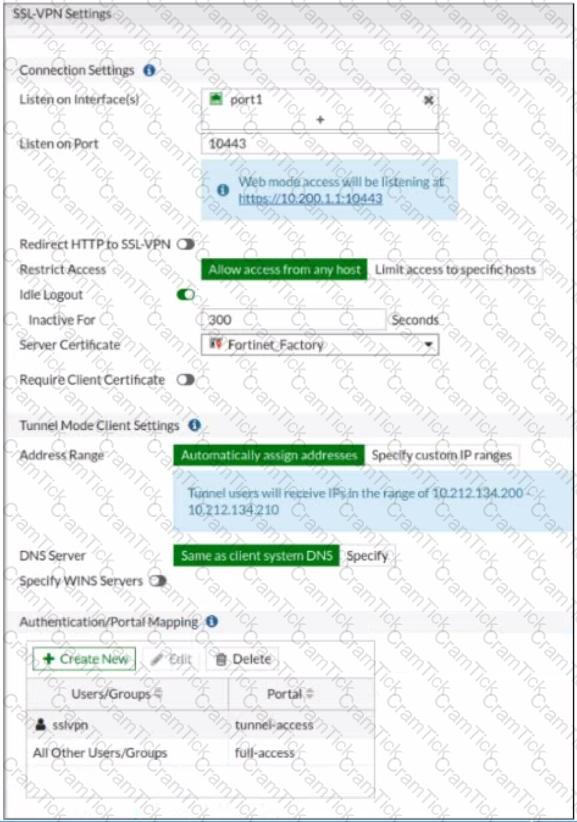
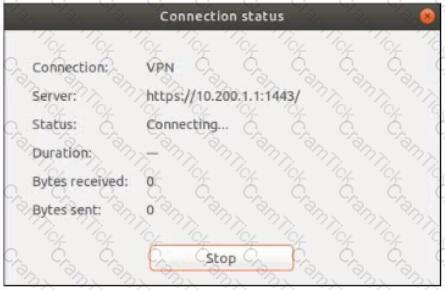
The SSL VPN connection fails when a user attempts to connect to it. What should the user do to successfully connect to SSL VPN?
Refer to the exhibit.
A network administrator is troubleshooting an IPsec tunnel between two FortiGate devices. The administrator has determined that phase 1 status is up, but phase 2 fails to come up.

Based on the phase 2 configuration shown in the exhibit, which configuration change will bring phase 2 up?
32
When configuring a firewall virtual wire pair policy, which following statement is true?
Refer to the exhibit.

Which contains a session diagnostic output. Which statement is true about the session diagnostic output?
Refer to the exhibit.
An administrator added a configuration for a new RADIUS server. While configuring, the administrator selected the Include in every user group option.

What is the impact of using the Include in every user group option in a RADIUS configuration?
40
Which CLI command will display sessions both from client to the proxy and from the proxy to the servers?
Why does FortiGate Keep TCP sessions in the session table for several seconds, even after both sides (client and server) have terminated the session?
Refer to the web filter raw logs.
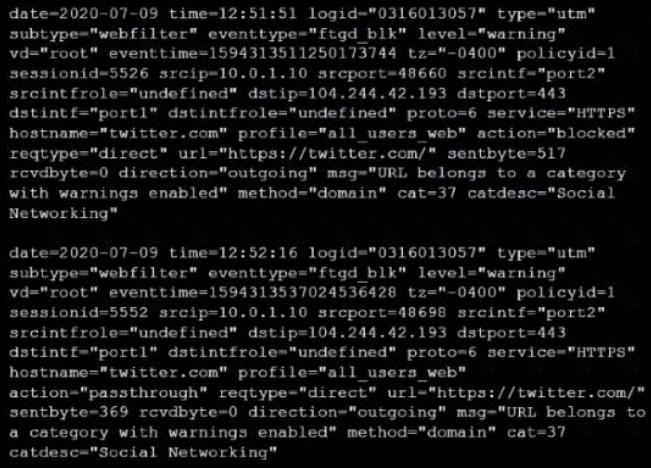
Based on the raw logs shown in the exhibit, which statement is correct?
31
Which CLI command allows administrators to troubleshoot Layer 2 issues, such as an IP address conflict?
An administrator configures outgoing interface any in a firewall policy.
What is the result of the policy list view?
34
The HTTP inspection process in web filtering follows a specific order when multiple features are enabled in the web filter profile. What order must FortiGate use when the web filter profile has features enabled, such as safe search?
Refer to the exhibits.

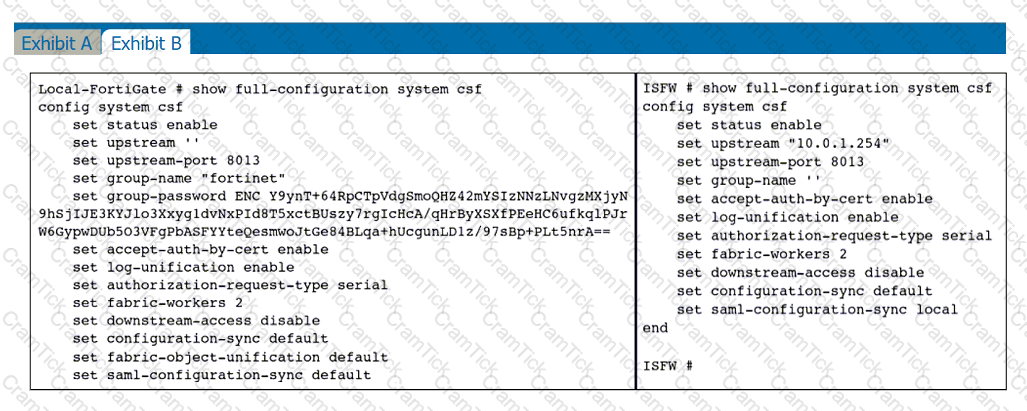
An administrator creates a new address object on the root FortiGate (Local-FortiGate) in the security fabric. After synchronization, this object is not available on the downstream FortiGate (ISFW).
What must the administrator do to synchronize the address object?
Which two settings are required for SSL VPN to function between two FortiGate devices? (Choose two.)
On FortiGate, which type of logs record information about traffic directly to and from the FortiGate management IP addresses?
29
Which two statements are correct about a software switch on FortiGate? (Choose two.)
Refer to the exhibits.
The exhibits show the firewall policies and the objects used in the firewall policies.
The administrator is using the Policy Lookup feature and has entered the search criteria shown in the exhibit.
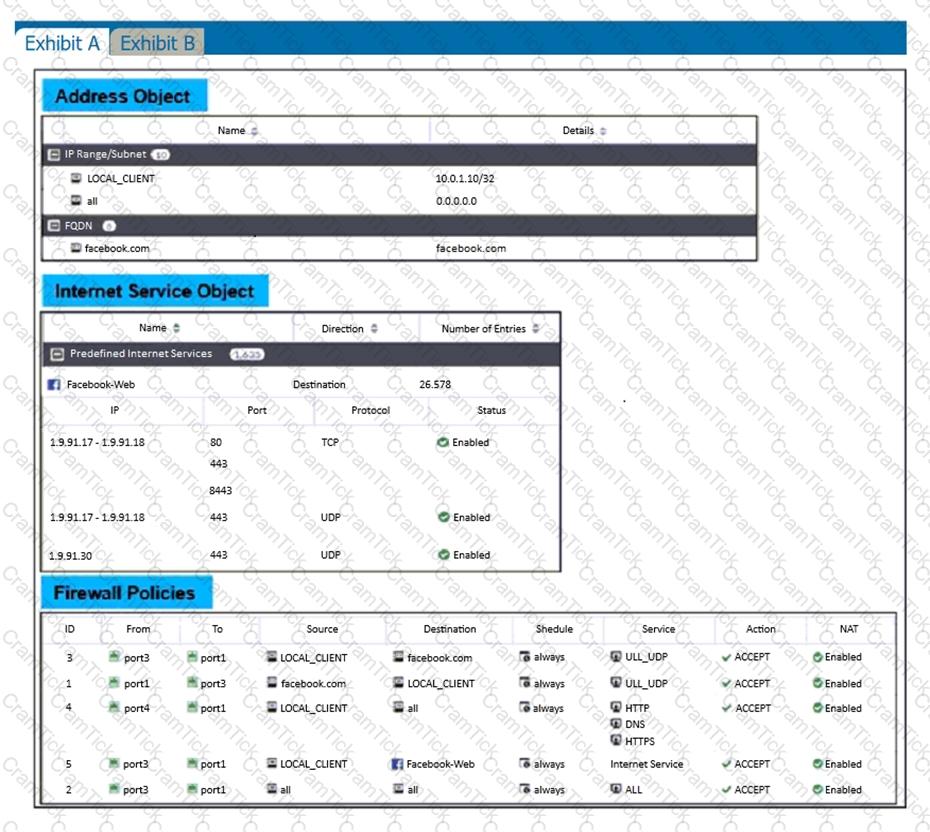

Which policy will be highlighted, based on the input criteria?
109
Why does FortiGate keep TCP sessions in the session table for some seconds even after both sides
(client and server) have terminated the session?
Refer to the exhibits.
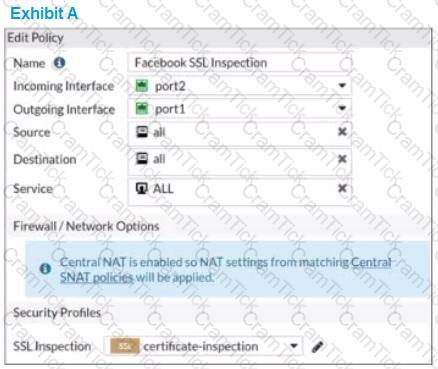

The exhibits show the SSL and authentication policy (Exhibit A) and the security policy (Exhibit B) for Facebook .
Users are given access to the Facebook web application. They can play video content hosted on Facebook but they are unable to leave reactions on videos or other types of posts.
Which part of the policy configuration must you change to resolve the issue?
FortiGate is operating in NAT mode and is configured with two virtual LAN (VLAN) subinterfaces added to the same physical interface.
In this scenario, which statement about VLAN IDs is true?
Refer to the exhibits.
Exhibit A shows a topology for a FortiGate HA cluster that performs proxy-based inspection on traffic. Exhibit B shows the HA configuration and the partial output of the get system ha status command.
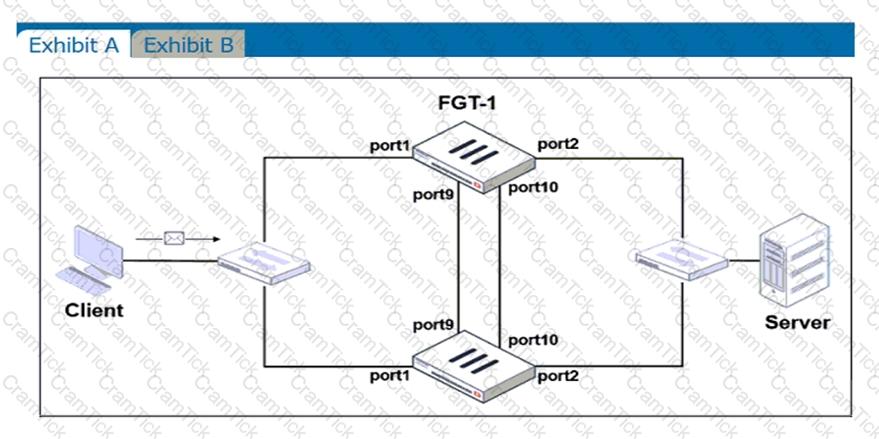
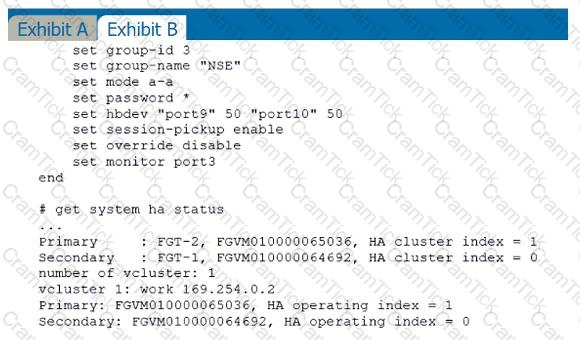
Based on the exhibits, which two statements about the traffic passing through the cluster are true? (Choose two.)
An administrator wants to configure timeouts for users. Regardless of the userTMs behavior, the timer should start as soon as the user authenticates and expire after the configured value.
Which timeout option should be configured on FortiGate?
Which statement correctly describes NetAPI polling mode for the FSSO collector agent?
Refer to the exhibits to view the firewall policy (Exhibit A) and the antivirus profile (Exhibit B).
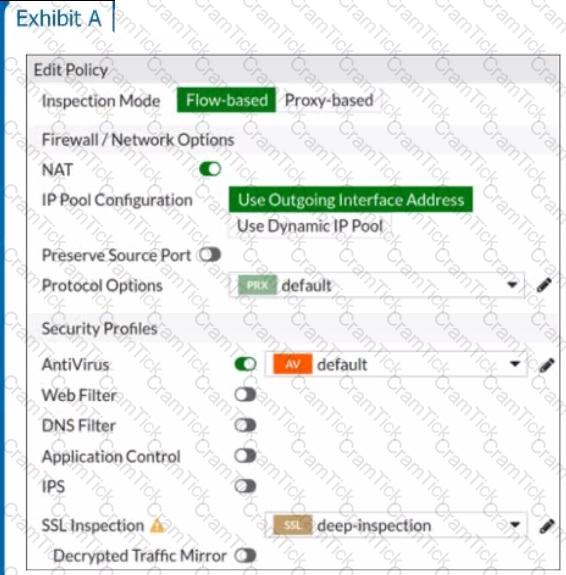
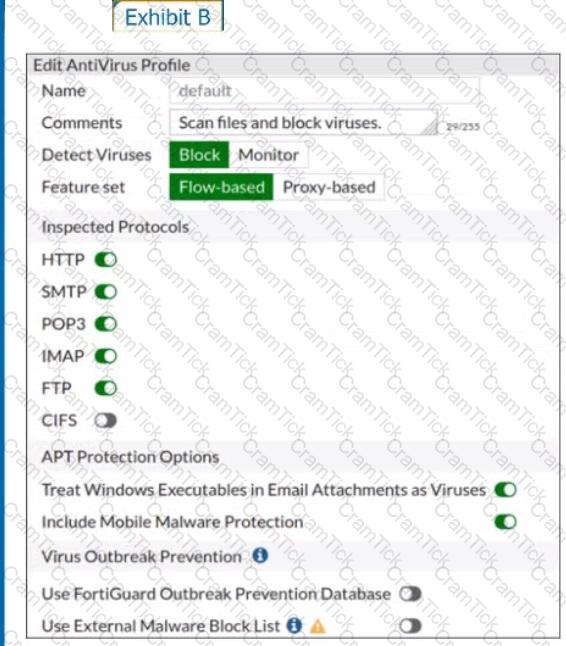
Which statement is correct if a user is unable to receive a block replacement message when downloading an infected file for the first time?
An administrator needs to increase network bandwidth and provide redundancy.
What interface type must the administrator select to bind multiple FortiGate interfaces?
A network administrator wants to set up redundant IPsec VPN tunnels on FortiGate by using two IPsec VPN tunnels and static routes.
* All traffic must be routed through the primary tunnel when both tunnels are up
* The secondary tunnel must be used only if the primary tunnel goes down
* In addition, FortiGate should be able to detect a dead tunnel to speed up tunnel failover
Which two key configuration changes are needed on FortiGate to meet the design requirements? (Choose two,)
30
A team manager has decided that, while some members of the team need access to a particular website, the majority of the team does not Which configuration option is the most effective way to support this request?
A network administrator has enabled SSL certificate inspection and antivirus on FortiGate. When downloading an EICAR test file through HTTP, FortiGate detects the virus and blocks the file. When downloading the same file through HTTPS, FortiGate does not detect the virus and the file can be downloaded.
What is the reason for the failed virus detection by FortiGate?
Refer to the exhibit.

Based on the ZTNA tag, the security posture of the remote endpoint has changed.
What will happen to endpoint active ZTNA sessions?
FortiGuard categories can be overridden and defined in different categories. To create a web rating override for example.com home page, the override must be configured using a specific syntax.
Which two syntaxes are correct to configure web rating for the home page? (Choose two.)
An employee needs to connect to the office through a high-latency internet connection.
Which SSL VPN setting should the administrator adjust to prevent SSL VPN negotiation failure?
Refer to the exhibit.

Given the routing database shown in the exhibit, which two statements are correct? (Choose two.)
Which statement about the deployment of the Security Fabric in a multi-VDOM environment is true?
Which two configuration settings are synchronized when FortiGate devices are in an active-active HA cluster? (Choose two.)
NSE4 |


