What is a weakness introduced into the WLAN environment when WPA2-Personal is used for security?
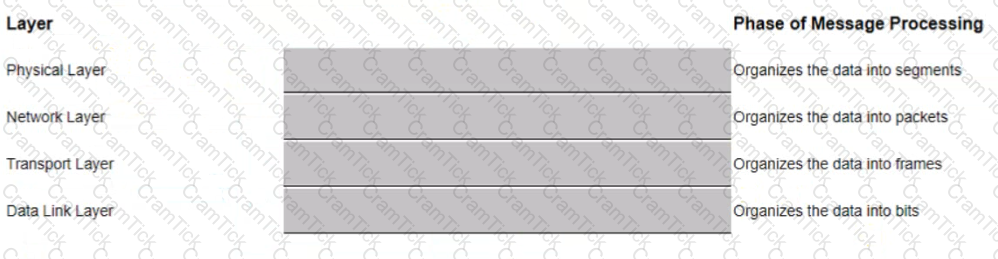
Match the phase of message processing with the Open Systems interconnection (OSl) layer.
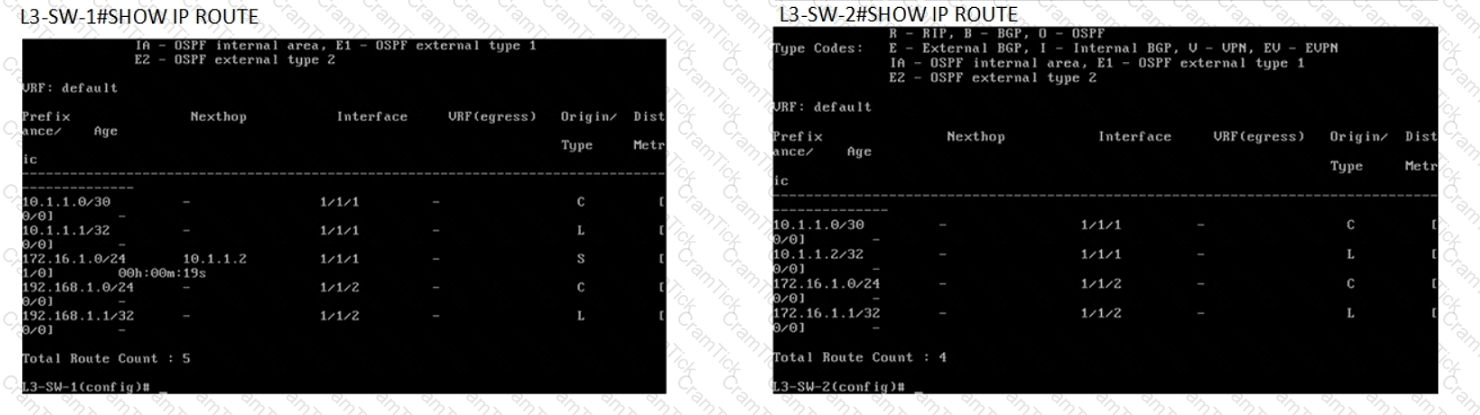
You have been asked to troubleshoot failed connectivity between a local subnet in the HQ Office and a remote subnet in the Branch Office. PC1 is unable to ping PC2.
Use the provided topology and show command output to identify the reason for the failure:
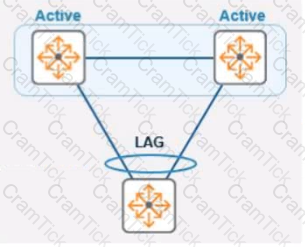
You are working with a pair of 6300M switches in a VSF stack. The switch has 48 SmartRate 5G ports, 2 SFP28 ports, and 2 SFP56 ports. Both SFP56 ports are used for stacking.
You need to provide an LACP connection to another identical stack with the maximum available bandwidth possible. What should you configure?
Refer to the exhibit.
In the given topology, a pair of Aruba CX 8325 switches are in a VSX stack using the active gateway What is the nature and behavior of the Virtual IP for the VSX pair if clients are connected to the access switch using VSX as the default gateway?
A client connects to an Aruba AP in tunnel mode and is assigned to a VLAN based on the client's MAC address.
Which client VLAN assignment was configured?
What does WPA3-Personal use as the source to generate a different Pairwise Master Key (PMK) each time a station connects to the wireless network?
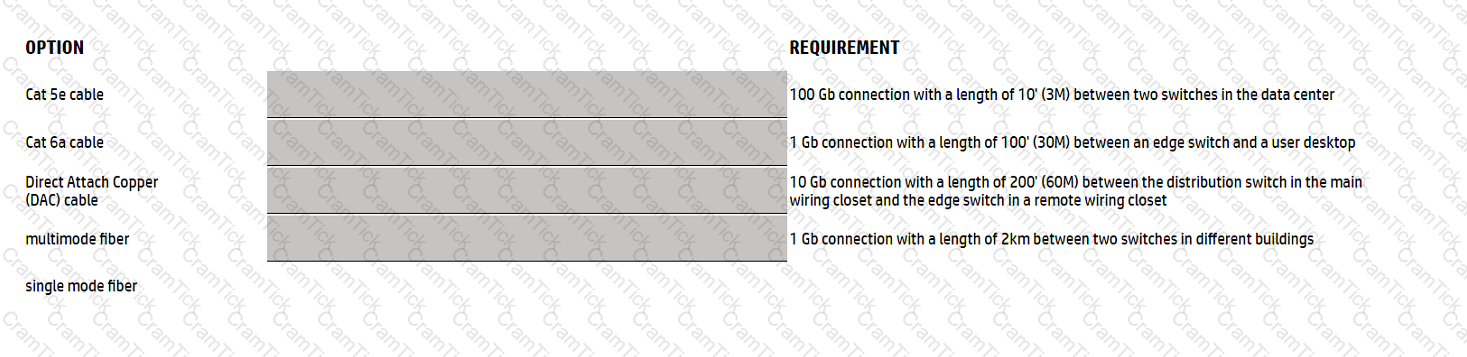
Match the most cost-effective option for cabling each requirement. (All lengths indicate total cable length including patch cable(s), service loops, etc. where used.)
What can be done to dynamically set the PoE Priority on a switch port when deploying IP cameras APs. and other PoE devices?
When does the 802.1x authentication process begin when connecting to a secured enterprise mode WLAN?
A hospital uses a lot of mobile equipment for the diagnosis and documentation of patient data What Is the ideal access switch for this large hospital with distribution racks of over 400 ports in a single VSF stack?
Which type of device type and group persona is required to manage a Microbranch environment?
You are configuring a network with a stacked pair of 6300M switches used for distribution and layer 3 services. You create a new VLAN for users that will be used on multiple access stacks of CX6200 switches connected downstream of the distribution stack You will be creating multiple VLANs/subnets similar to this will be utilized in multiple access stacks
What is the correct way to configure the routable interface for the subnet to be associated with this VLAN?
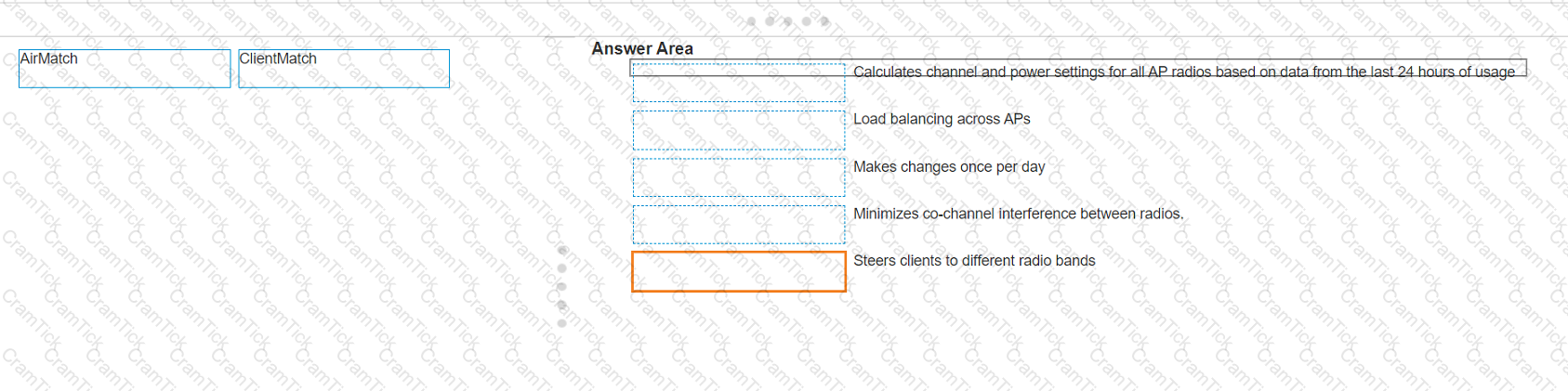
Match the Aruba Central technology to the appropriate feature. (Matches may be used more than once.)
A customer has just implemented user and device certificates via a company-wide Group Based Policy (GPO) Which EAP method requires client certificates when authenticating to the network?
Which Aruba technology will allow for device-specific passphrases to securely add headless devices to the WLAN?
Which flew in a Layer 3 IPv4 packet header is used to mitigate Layer 3 route loops?
The customer has a requirement to create authorization policies for their users with Windows 10 clients, with a requirement Tor authorizing both device and user credentials within one Radius session.
What would be the correct solution for the requirement?
Based on the "snow ip route" output on an AruDaCX 8400. what type of route is "10.1 20 0/24, vrf default via 10.1.12.2. [1/0]"?
When using Aruba Central what can identify recommended steps to resolve network health issues and allows you to share detailed information with support personnel?
A network technician is deploying "headless" devices in the warehouse at the HQ location. So far, an SSID with 802.1X has been configured. However, these new devices lack 802.1X support.
Which option would provide enhanced security for these devices?


