Refer to the exhibit.

A network administrator sets up prioritization for an application that runs between Device 1 and Device 2. However, the QoS for the application is not what the administrator expects.
How can the administrator check if the network infrastructure prioritizes traffic from Device 1 and Device 2?
Refer to the exhibits.
Exhibit 1
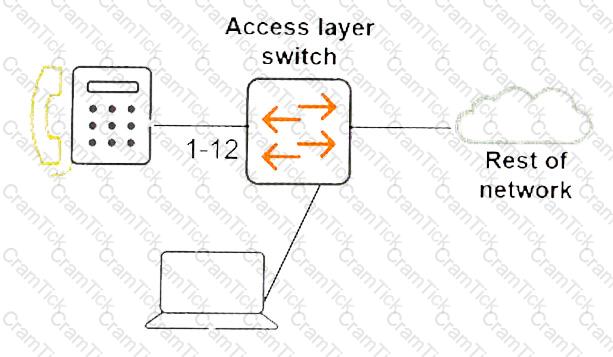
Exhibit 2
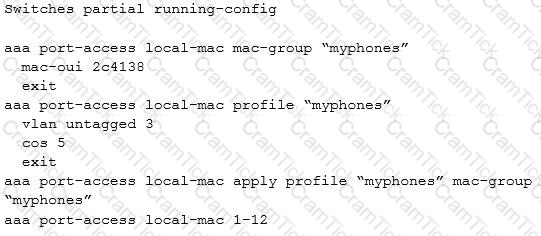
A company does not require authentication for security, but AOS-Switches are set up to use local MAC authentication (LMA) to assign the correct VLAN and priority to IP phones. IP phones and computers belong to different VLANs. Each device is supposed to connect to a specific port, but sometimes users connect their devices to the wrong ports and cannot receive access without help from IT.
How can a network administrator configure the switches to eliminate this issue?
A company has AOS-Switches deployed at sites with inexperienced IT staff. The main office network administrators want to track if configurations change on branch switches.
What should be set up for this purpose?
Refer to the exhibits.
Exhibit 1
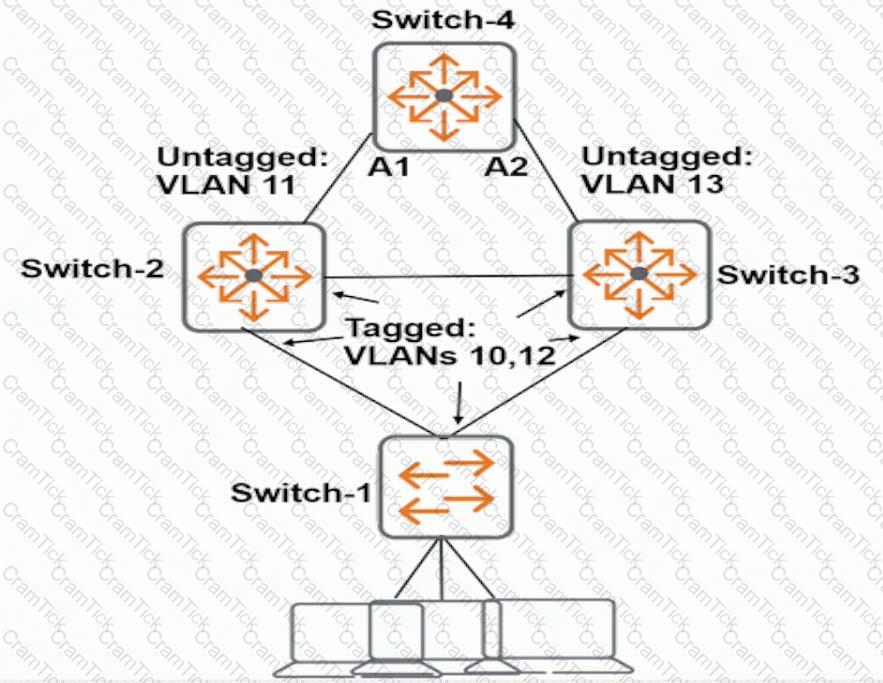
Exhibit 2
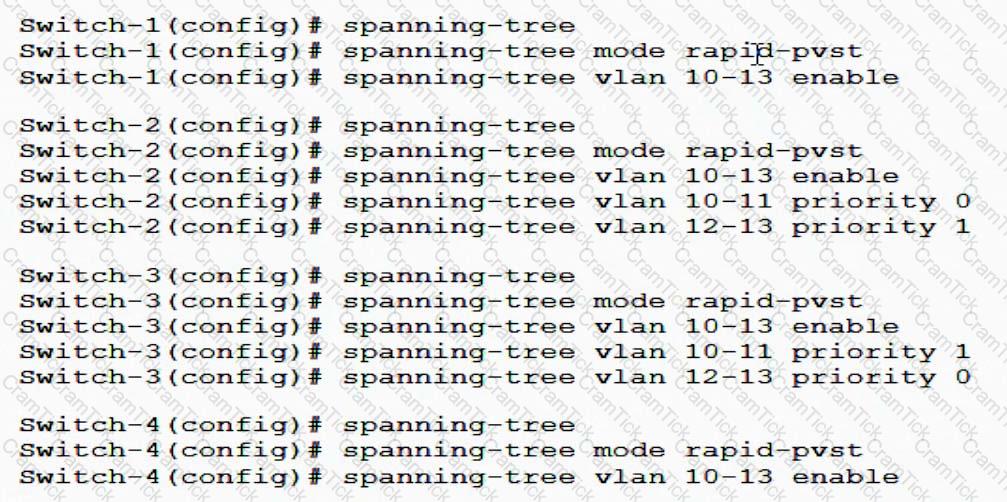
The network administrator enters the commands shown in Exhibit 2. What is the spanning tree status on A1 and A2?
A network administrator configures DHCP snooping on VLAN 2. How does the switch handle DHCP traffic that arrives in this VLAN on an untrusted interface?
Refer to the exhibits.
Exhibit 1
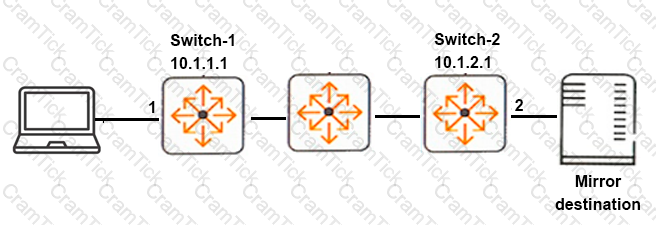
Exhibit 2
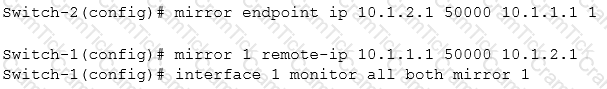
A network administrator wants to set up mirroring of traffic from port 1 on Switch-1 to port 1 on Switch-2. Exhibit-2 shows the commands that the administrator enters. The mirroring does not work correctly.
What must the administrator do to correct the error?
A network administrator enters this command on an AOS-Switch:
Switch(config)# radius-server host 10.1.3.3 time-window 60
Which behavior will the switch show?
A company deploys AOS-Switches at sites with inexperienced IT staff. The main office network administrators want to monitor thresholds to generate alerts on branch switches. What should be set up for this purpose?
A network administrator needs to control traffic based on TCP or UDP application, as well as IP protocol, such as GRE or ICMP. What should the administrator configure for this purpose?
Refer to the exhibits.
Exhibit 1
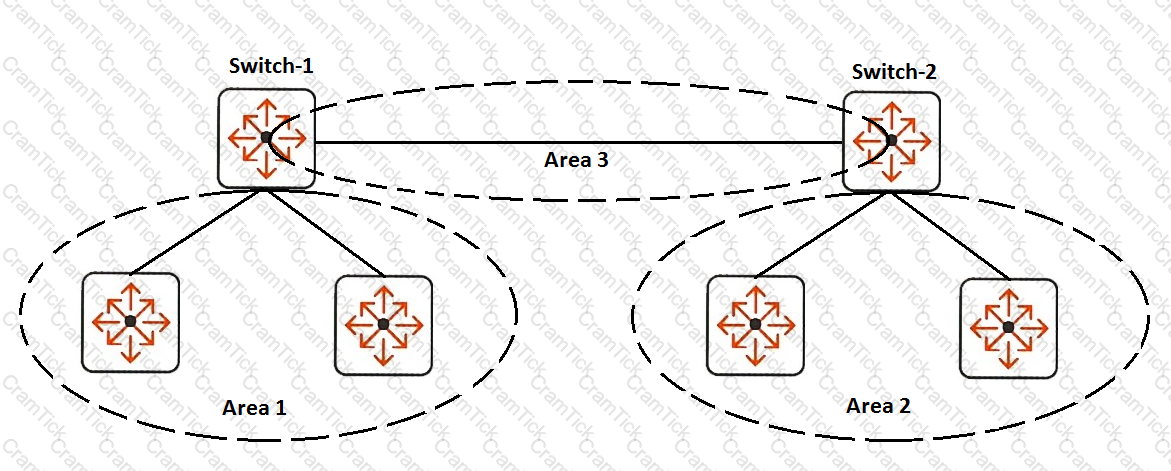
Exhibit 2
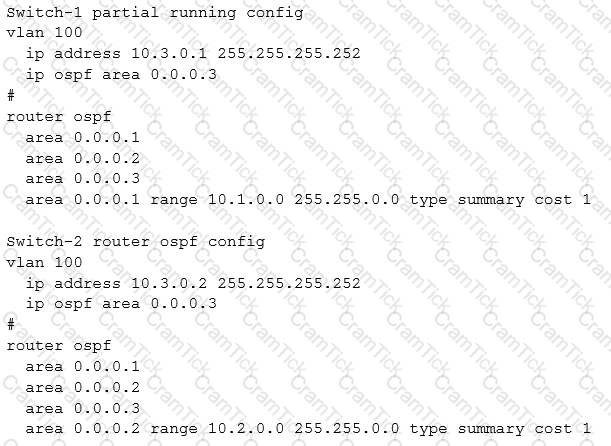
A company has attempted to implement OSPF without success. The devices in Area 1 need to be able to reach Area 2. Routes should be aggregated for advertisement in other areas. What must be changed to meet these requirements?
A company requires AOS-Switches at the campus core. The switches:
VRRP and MSTP are proposed to meet these requirements. What is an issue with this proposal?
What must an OSPF router do to ensure nonstop routing should a standby member take over as commander when the original VSF commander fails?
A network administrator sets up MAC-Auth and captive portal to Aruba ClearPass on AOS-Switches. The solution seems to work for most guests. However, some guests open their browsers and are not redirected to the captive portal.
How should the administrator address the likely cause of the issue?
Refer to the exhibit.
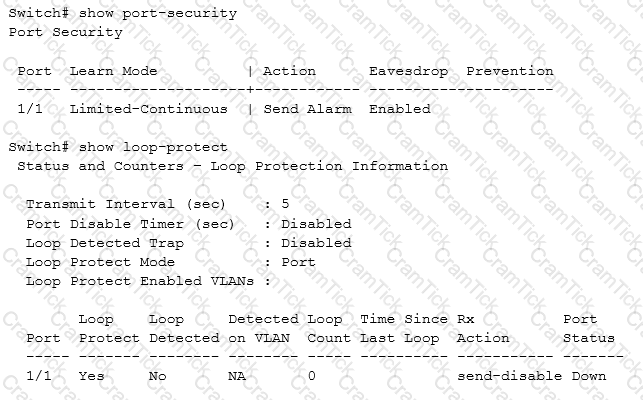
An AOS-Switch connects to an unmanaged switch in a meeting room. The exhibit shows security settings for this port. Users report that they sometimes lose connectivity and then get it back.
Which best practice should network administrators follow to avoid this issue?
Refer to the exhibit.
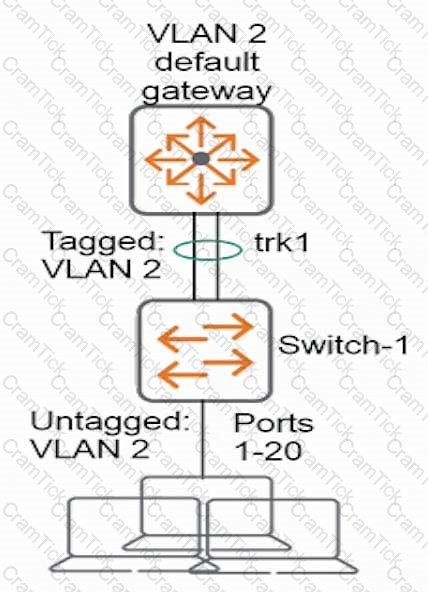
A network administrator wants to prevent endpoints from spoofing the MAC address of the VLAN 2 default gateway. What should the administrator configure on Switch-1?
A network administrator needs to set up an AOS-Switch to use port-based tunneled node for connected devices. However, the administrator wants the switch to forward traffic without tunneling if it cannot reach a tunneled-node server.
What should the administrator do?
Refer to the exhibit.
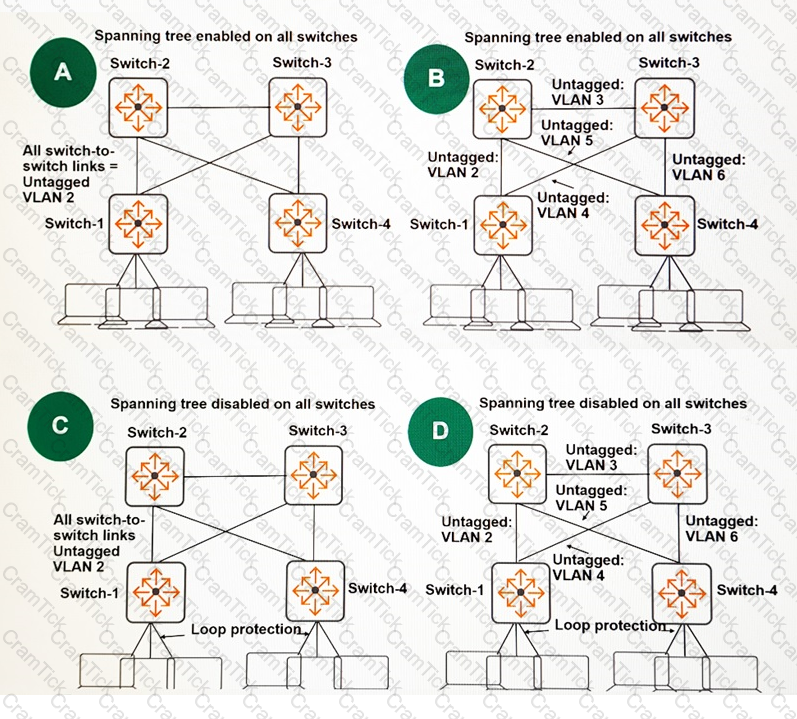
Every switch in the exhibit will route traffic. The company requires a topology in which failover for switch-to-switch links is exclusively handled by the routing protocol and occurs as quickly as possible. Which topology should the administrator use?
A network has high latency on some links. Which application is most likely to experience poor performance?
Refer to the exhibits.
Exhibit 1
Exhibit 2
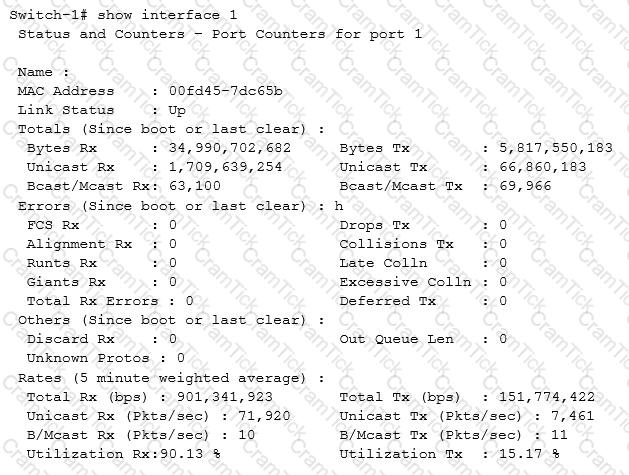
Network administrators are alerted to high interface utilization on a switch by a management solution. They examine the utilization on the uplink interfaces several times an hour during problem times. The exhibit shows output typical of times of congestion. The administrators want to allocate bandwidth fairly and reduce congestion on the uplinks.
What could help meet these requirements?
An AOS-Switch needs to be configured to support tunneled node in role-based mode. The Mobility Controller administrators tell the switch administrators that the AOS-Switch will integrate with a cluster of Mobility Controllers. The cluster virtual IP address is 10.1.1.10.
How should switch administrator integrate the AOS-Switch with the cluster?
Aruba Certified Switching Professional (ACSP) V1 | HPE6-A45 Questions Answers | HPE6-A45 Test Prep | Implementing Aruba Campus Switching Solutions Exam Questions PDF | HPE6-A45 Online Exam | HPE6-A45 Practice Test | HPE6-A45 PDF | HPE6-A45 Test Questions | HPE6-A45 Study Material | HPE6-A45 Exam Preparation | HPE6-A45 Valid Dumps | HPE6-A45 Real Questions | Aruba Certified Switching Professional (ACSP) V1 HPE6-A45 Exam Questions