In BGP, Notification messages are used to request peers to resend routing information after routing policies are changed.
On an IS-IS network, areas are divided by router, and a router can belong to only one area. Therefore, an IS-IS router only needs to maintain the LSDB of its area.
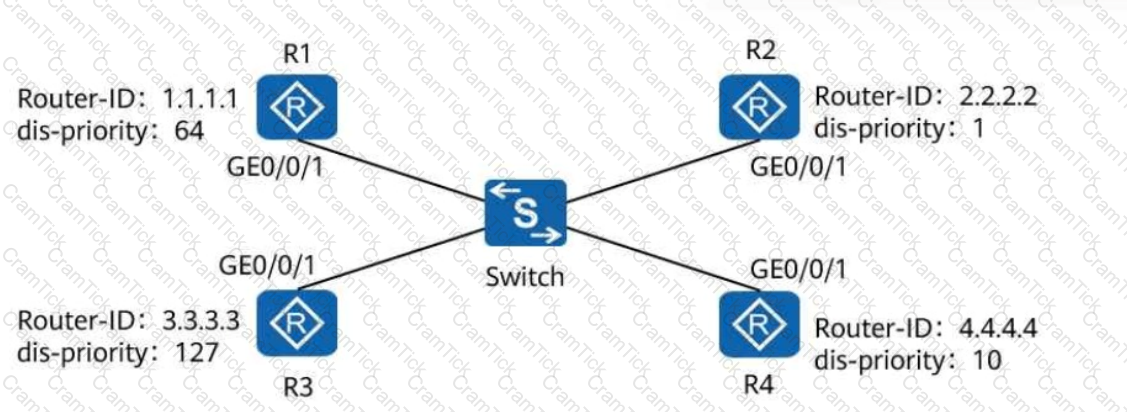
On a broadcast IS-IS network shown in the following figure, a DIS needs to be elected to create and update pseudonodes. Which of the following routers is elected as the DIS?
An enterprise network runs OSPF to implement network communication. Which of the following types of LSAs may be generated by an ABR?
There are two BFD operating modes. In_______mode, the local end sends BFD Control packets at specified intervals, and the remote end checks whether the local end periodically sends BFD Control packets. (Use lowercase letters.)
An enterprise administrator wants to configure single-hop BFD to implement fast detection of direct links. Which of the following configurations are mandatory?
On an OSPF network, an algorithm is used to prevent loops within an area, but loops may occur between areas. Therefore, OSPF defines a loop prevention mechanism for inter-area routes. Which of the following statements are true about the loop prevention mechanism?
When a routing policy is used to filter routes, which of the following route prefixes will be denied by the IP prefix below?

An enterprise administrator configures route summarization on ASBRs to reduce the number of inter-area Type 3 LSAs, which in turn reduces the routing table size and improves device resource utilization.
As a next-generation wireless technology, Wi-Fi 6 greatly improves bandwidth rate and performance. Which of the following statements is false about the features of Wi-Fi 6?
On a broadcast IS-IS network, a DIS needs to be elected to create and update pseudonodes. Which of the following values is the default DIS priority of an IS-IS interface?
A router performs a lookup in its FIB table for a packet. If the tunnel ID in the matching entry is 0, the packet needs to be forwarded through a tunnel, such as an MPLS tunnel.
BFD for OSPF is deployed on a directly connected link. If the physical link is disconnected, drag the following BFD processes to the corresponding sequence numbers.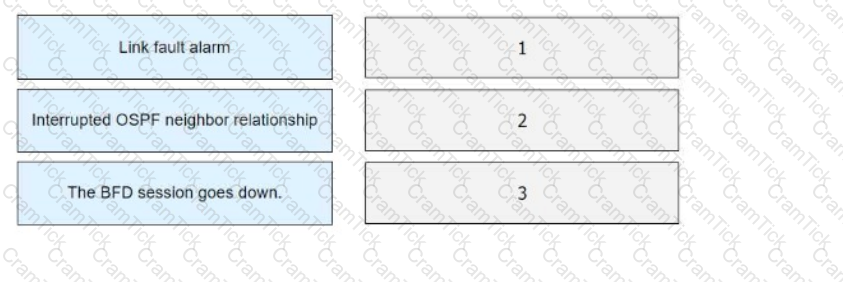
Route attributes are specific descriptions of routes. BGP route attributes can be classified into four types. Which of the following are well-known discretionary attributes?
When a BGP device sends an Open message to establish a peer connection, which of the following information is carried?
Which of the following statements are true about the packet filtering firewall?
The AS_Path attribute is an important BGP attribute used for route selection. Which of the following statements are true about this attribute?
An IP prefix list is configured on a router using the following command:
ip ip-prefix huawei index 10 permit 10.1.1.0 24 greater-equal 26
In this case, the value of greater-equal-value is ____, and the value of less-equal-value is ____.
IGMP has three versions. Different versions support different features. Which of the following features is supported by all versions?
When configuring an ACL on a router, you can specify a unique number or name to identify the ACL. Once a named ACL is created, it cannot be modified. You can only delete the named ACL and reconfigure it.
GRE is a VPN encapsulation technology that is widely used to transmit packets across heterogeneous networks. Which of the following statements is false about GRE?
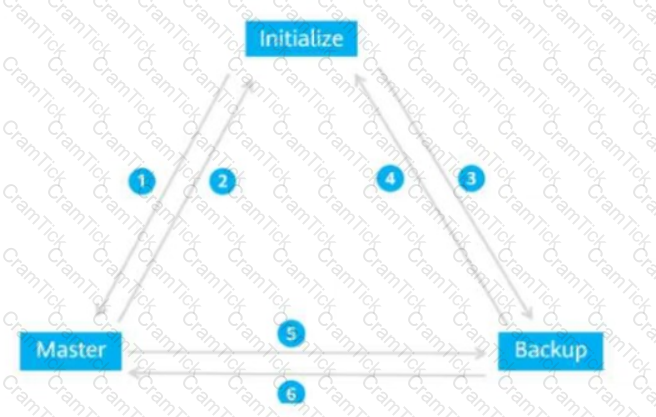
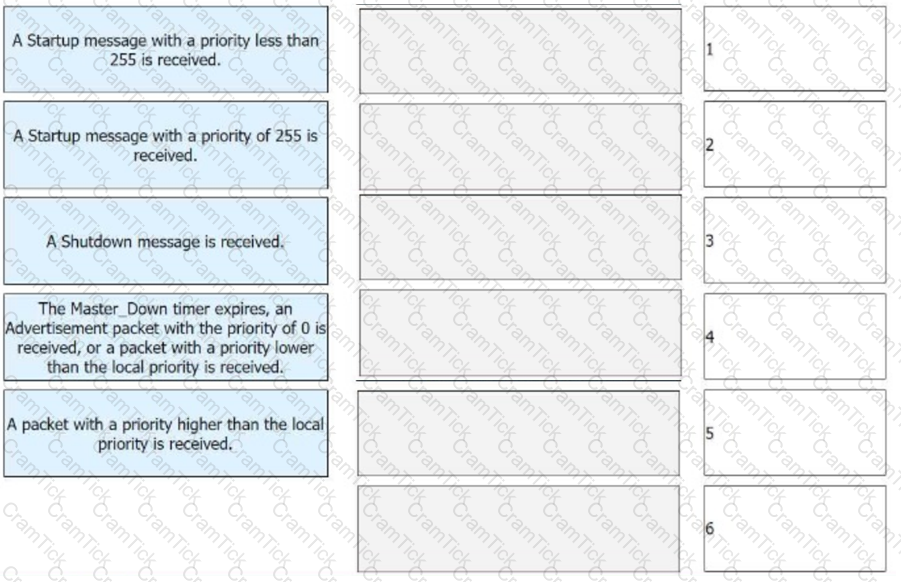
The figure shows the VRRP status switchover events. Match these events with their sequence numbers.
On an IS-IS network, routers send LSPs to exchange link state information. LSPs are classified into Level-1 LSPs and Level-2 LSPs and have the same format. Which of the following parts constitute the LSP ID in an LSP?
In the SNMP management model, which of the following elements defines the attributes of a managed device?
Which of the following statements is false about the session table mechanism on firewalls?
The IP prefix list configuration on a Huawei router is shown below. Which of the following routes can match this IP prefix list?
bash
Copy
[huawei] ip ip-prefix test index 10 permit 10.0.0.0 8 less-equal 32
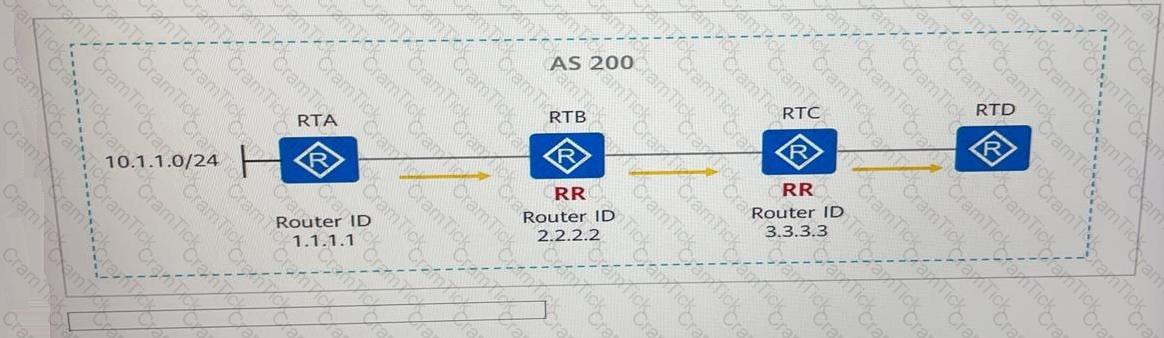
See the following figure. RTA, RTB, RTC, and RTD are in the same AS and establish IBGP peer relationships through direct links. RTB an RTC are route reflectors (RRs), RTA and RTC are the RR clients of RTB, and RTB and RTD are the RR clients of RTC. If RTA advertises the route 10.1.1.0/24 to the BGP process, the Originator ID of the BGP route received by RTD is------------------.
Both MQC and PBR can be applied on device interfaces to filter received and sent packets or control packet forwarding paths.
A router forwards traffic based on a FIB table. Which of the following values of the Flag field in a routing entry indicates that the next hop of the route is the gateway?
Which of the following is the default interval at which the DIS on a broadcast IS_IS network sends CSNPs.
In an OSPF routing domain, two routers must be specified as one DR and one BDR in a broadcast or NBMA network with at least two routers.
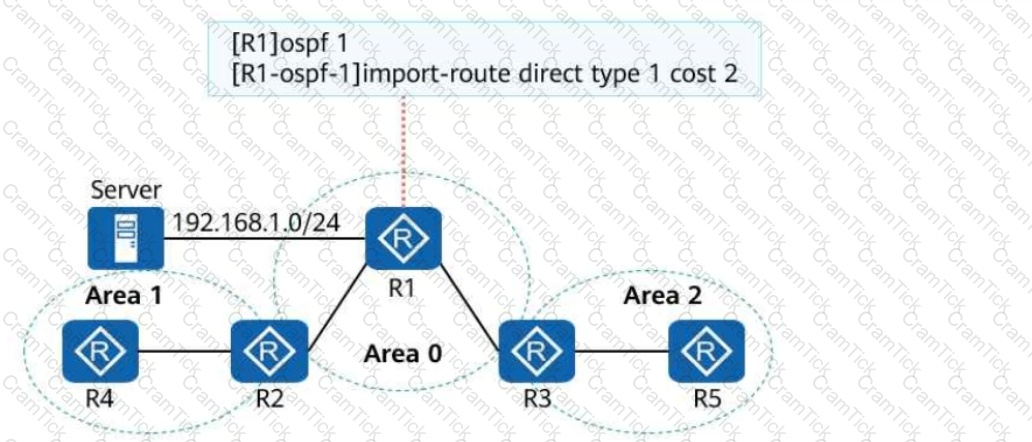
On the campus OSPF network shown in the following figure, the interfaces connecting the five routers are GE interfaces, and their costs are not changed. The import-route command is run on R1. After the network converges, the route to the server at 192.168.1.0/24 is queried on R2. Which of the following is the cost of this route?
As shown in the figure, the stateful inspection firewall forwards the packet because the packet matches the session status of the firewall.
A large number of routes typically exist in a BGP routing table, and transmitting such extensive routing information brings a heavy burden to a device. In order to address this problem, it is necessary to filter those routes to be advertised. You can configure a device to advertise only necessary routes or those that its peers require.
On a network, some switches are enabled with RSTP and some switches are enabled with STP. What will happen?
A route-policy consists of one or more nodes. What is the maximum number of nodes in a route-policy?
On an OSPF network, all OSPF routers generate Router LSAs. If the E bit in a Router LSA is set to 1, the router that generates this LSA is a/an ______.
During routine operation and maintenance, an engineer checks the IGMP configuration on RTA. The configuration is as follows:
Interface information of VPN-Instance: public net
GigabitEthernet0/0/1 (192.168.1.1):
IGMP is enabled
Current IGMP version is 2
IGMP state: up
IGMP group policy: none
IGMP limit: -
Value of query interval for IGMP (negotiated): -
Value of query interval for IGMP (configured): 60 s
Value of other querier timeout for IGMP: 0 s
Value of maximum query response time for IGMP: 10 s
Querier for IGMP: 192.168.1.1 (this router)
Given this, which of the following statements is false?
Which of the following attributes must be carried when BGP sends route update messages?
On an OSPF network, if two routers with the same router ID run in different areas and one of the routers is an ASBR, LSA flapping occurs.
On an OSPF or IS-IS network, the filter-policy import command can be run on a router to filter out the LSAs forwarded by its neighbors.
On an OSPF network, an IR in area 0 must be a BR, but an ASBR may not be an ABR.
Security policy is the core feature of firewalls. Only valid traffic that complies with security policies can be forwarded by firewalls. Which of the following statements are true about security policy matching rules?
An enterprise office network runs OSPF and is divided into multiple OSPF areas. Enterprise network engineers can configure route summarization on ASBRs to reduce the number of inter-area Type 3 LSAs, which in turn reduces the routing table size and improves device resource utilization.
On an OSPF network, if a router functions as an ABR, the router must also be a BR.
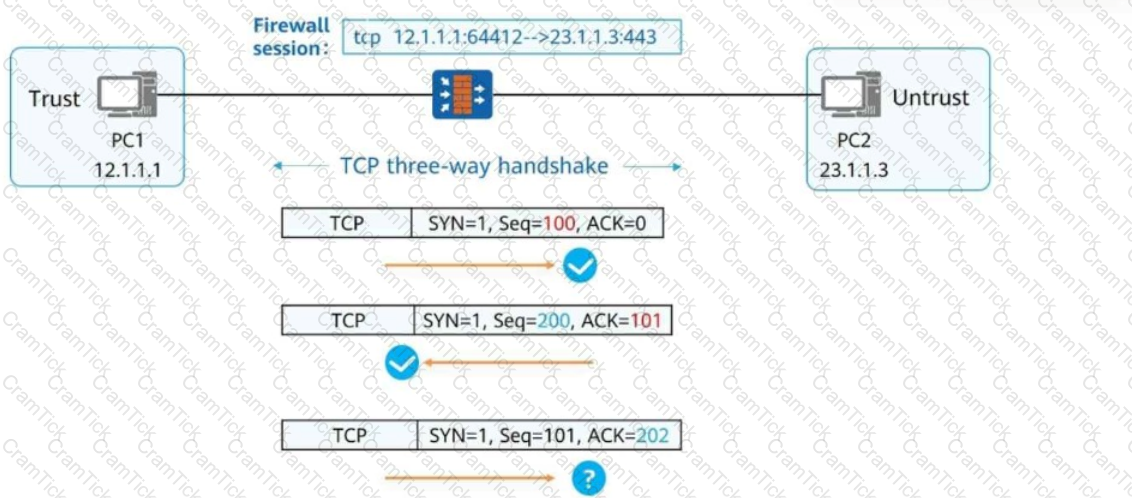
ON a stateful inspection Firewall where there is no session table, when the status detection mechanism is enabled and the second packet (CYN+ACK) of 3-way hadshakes reaches the firewall. Which of the following statements is true?
iMaster NCE-Campus can be used as an authentication server on a WLAN to authenticate STAs.
L2TP does not provide security encryption. Therefore, other security measures, such as IPsec, are required to ensure the security of the entire tunnel for data transmission.
A Layer 2 switch supports multiple types of Ethernet interfaces. Similar to a trunk interface, a hybrid interface allows data frames from multiple VLANs to pass through. In addition, you can determine whether data frames from a VLAN sent out from a hybrid interface are tagged or untagged.
The BFD Echo function checks the connectivity of the forwarding link by looping back packets. Which of the following statements are true about this function?
NETCONF is a network configuration protocol that automates network configuration in a programmable manner, simplifying and accelerating network service deployment. Which of the following operations can be performed by using this protocol?
GRE is a Layer 2 VPN encapsulation technology that encapsulates packets of certain data link layer protocols so that the encapsulated packets can be transmitted over an IP network.
A wide area network (WAN) is a remote network that connects local area networks (LANs) or metropolitan area networks (MANs) in different areas for communication purposes. It is typically used to interconnect campus networks or data center networks.
Which of the following methods is usually used by a network administrator to configure a newly purchased device for the first time?
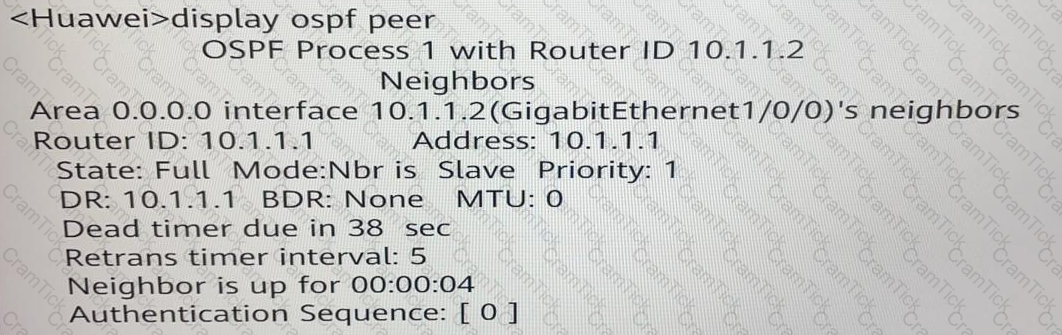
Which of the following statement regarding the display ospf peer command output is true?
IGMPV3 not only supports IGMPv1 General Query and IGMPv2 Group-Specific Query, and also IGMPv3 Source/Group-Specific Query.
Roaming technology is typically used on a large WLAN to ensure that STA (station) services are not interrupted when STAs move between coverage areas of different APs.
Which of the following attributes cannot be directly referenced in an apply clause of a route-policy?
Multicast applies to any point-to-multipoint data transmission. Which of the following types of application data can be forwarded in multicast mode?
When an SSH client accesses an SSH server for the first time and the SSH server's public key is not configured on the SSH client, you can enable first-time authentication on the SSH client. This allows the SSH client to access the SSH server and saves the SSH server's public key on the SSH client. In this way, the next time the SSH client accesses the SSH server, the SSH client can use the saved public key to authenticate the SSH server.
In the OSPF protocol, intra-area route calculation involves only Router LSA, Network LSA, and Summary LSA.
On an RSTP network, port roles are optimized to overcome the disadvantages of STP. Which of the following port roles are supported in RSTP?
ASPF enables the firewall to support multi-channel protocols such as FTP and to define security policies for complex applications.
When multiple access channels are set for the same access requirement, the insecure access channels are not used and secure access channels are selected in normal cases. Which of the following are secure access channels?
Which of the following statements regarding the firewall zone security level is false?
To overcome the disadvantages of STP, RSTP changes the format of configuration BPDUs. Which of the following fields in STP BPDUs is used to specify the port role?
When deploying a VRRP network, an enterprise administrator sets the virtual IP address to 192.168.1.254 and VRID to 1. Which of the following is the virtual MAC address after the network becomes stable?
The VRID of the VRRP virtual router is 3 and the virtual IP address is 100.1.1.10. What is the virtual MAC address?
IPv6 defines multiple types of addresses. Which of the following statements is false about these addresses?
Which of the following configurations are not mandatory when an administrator configures VRRP?
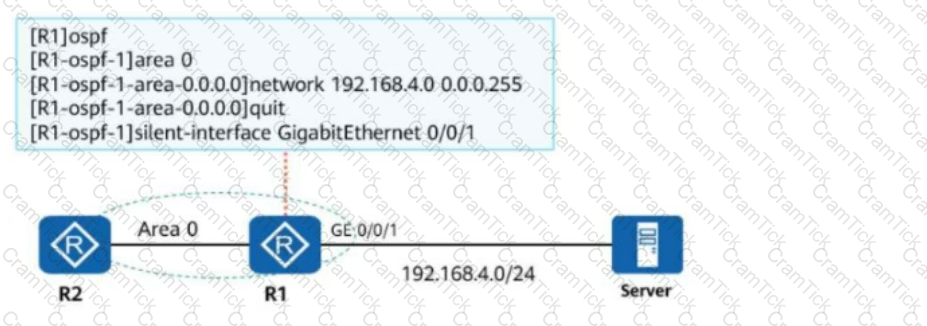
The following figure shows the OSPF network of an enterprise and the OSPF configurations of R1. Which of the following statements is false about the network?
VRF, also called VPN instance, is a network virtualization technology that helps VPN technology to isolate users. In normal cases, multiple VPN instances can be created on a physical device, and each VPN instance has independent entries. Which of the following resources can be independently owned by a VPN instance?
Which of the following messages are sent when BGP establishes peer relationships?
HCIP-Datacom | H12-821_V1.0 Questions Answers | H12-821_V1.0 Test Prep | HCIP-Datacom-Core Technology V1.0 Questions PDF | H12-821_V1.0 Online Exam | H12-821_V1.0 Practice Test | H12-821_V1.0 PDF | H12-821_V1.0 Test Questions | H12-821_V1.0 Study Material | H12-821_V1.0 Exam Preparation | H12-821_V1.0 Valid Dumps | H12-821_V1.0 Real Questions | HCIP-Datacom H12-821_V1.0 Exam Questions


