In which of the following IDS evasion techniques does an attacker deliver data in multiple small sized packets, which makes it very difficult for an IDS to detect the attack signatures of such attacks?
Which of the following firewalls operates at three layers- Layer3, Layer4, and Layer5?
Which of the following tools can be used to check whether the network interface is in promiscuous mode or not?
Which of the following is the purpose of creating a Demilitarized zone (DMZ) in an enterprise network?
Which of the following programs in UNIX is used to identify and fix lost blocks or orphans?
Which of the following tools is an open source network intrusion prevention and detection system that operates as a network sniffer?
Which of the following switches is used with Pslist command on the command line to show the statistics for all active threads on the system, grouping these threads with their owning process?
Mark works as a Network Security Administrator for BlueWells Inc. The company has a Windowsbased network. Mark is giving a presentation on Network security threats to the newly recruited employees of the company. His presentation is about the External threats that the company recently faced in the past. Which of the following statements are true about external threats?
Each correct answer represents a complete solution. Choose three.
Which of the following fields of the IPv6 header is similar to the TTL field of IPv4?
You work as a Network Administrator for NetTech Inc. You want to know the local IP address, subnet mask, and default gateway of a NIC in a Windows 98 computer. Which of the following utilities will you use to accomplish this ?
You work as a Network Administrator for Tech Perfect Inc. The company has a TCP/IP-based network.
You have configured a firewall on the network. A filter has been applied to block all the ports. You want to enable sending and receiving of emails on the network. Which of the following ports will you open?
Each correct answer represents a complete solution. Choose two.
Victor works as a professional Ethical Hacker for SecureNet Inc. He wants to use Steganographic file system method to encrypt and hide some secret information. Which of the following disk spaces will he use to store this secret information?
Each correct answer represents a complete solution. Choose all that apply.
You work as a Computer Hacking Forensic Investigator for SecureNet Inc. You want to investigate Cross-Site Scripting attack on your company's Website. Which of the following methods of investigation can you use to accomplish the task?
Each correct answer represents a complete solution. Choose all that apply.
You are a professional Computer Hacking forensic investigator. You have been called to collect the evidences of Buffer Overflows or Cookie snooping attack. Which of the following logs will you review to accomplish the task?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following types of attacks uses ICMP to consume bandwidth and crash sites?
Which of the following statements are true about an IPv6 network?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following Windows XP system files handles memory management, I/O operations, and interrupts?
Which of the following partitions contains the system files that are used to start the operating system?
Which of the following can be applied as countermeasures against DDoS attacks?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following attacks is designed to deduce the brand and/or version of an operating system or application?
John works as a professional Ethical Hacker. He has been assigned a project to test the security of www.we-are-secure.com. John wants to redirect all TCP port 80 traffic to UDP port 40, so that he can bypass the firewall of the We-are-secure server. Which of the following tools will John use to accomplish his task?
Which of the following tools are used to determine the hop counts of an IP packet?
Each correct answer represents a complete solution. Choose two.
Adam works as a Security Administrator for Umbrella Inc. A project has been assigned to him to secure access to the network of the company from all possible entry points. He segmented the network into several subnets and installed firewalls all over the network. He has placed very stringent rules on all the firewalls, blocking everything in and out except ports that must be used.
He does need to have port 80 open since his company hosts a website that must be accessed from the Internet. Adam is still worried about programs like Hping2 that can get into a network through covert channels.
Which of the following is the most effective way to protect the network of the company from an attacker using Hping2 to scan his internal network?
What is the name of the first computer virus that infected the boot sector of the MS-DOS operating system?
Windump is a Windows port of the famous TCPDump packet sniffer available on a variety of platforms. In order to use this tool on the Windows platform a user must install a packet capture library.
What is the name of this library?
An attacker makes an attempt against a Web server. The result is that the attack takes the form of URLs. These URLs search for a certain string that identifies an attack against the Web server.
Which IDS/IPS detection method do the URLs use to detect and prevent an attack?
Which of the following types of firewall functions at the Session layer of OSI model?
Mark works as a Network administrator for SecureEnet Inc. His system runs on Mac OS X. He wants to boot his system from the Network Interface Controller (NIC). Which of the following snag keys will Mark use to perform the required function?
John, a novice web user, makes a new E-mail account and keeps his password as "apple", his favorite fruit. John's password is vulnerable to which of the following password cracking attacks?
Each correct answer represents a complete solution. Choose all that apply.
You work as a Network Administrator for Net Perfect Inc. The company has a Windows Server 2008 network environment. The network is configured as a Windows Active Directory-based single forest single domain network. Active Directory integrated zone has been configured on the network. You want to create a text file that lists the resource records of a specified zone for your record. Which of the following commands will you use to accomplish the task?
Which method would provide the highest level of protection for all data transmitted on the internal network only? (Click the Exhibit button on the toolbar to see the case study.)
Adam works as a professional Computer Hacking Forensic Investigator. He has been called by the FBI to examine data of the hard disk, which is seized from the house of a suspected terrorist.
Adam decided to acquire an image of the suspected hard drive. He uses a forensic hardware tool, which is capable of capturing data from IDE, Serial ATA, SCSI devices, and flash cards. This tool can also produce MD5 and CRC32 hash while capturing the data. Which of the following tools is Adam using?
Which of the following proxy servers is also referred to as transparent proxies or forced proxies?
Which of the following attacks involves multiple compromised systems to attack a single target?
With reference to the given case study, one of the security goals requires to configure a secure connection between the Boston distribution center and the headquarters. You want to implement IP filter to fulfill the security requirements. How should you implement IP filters at the headquarters?
(Click the Exhibit button on the toolbar to see the case study.)
Adam works as a professional Computer Hacking Forensic Investigator. A project has been assigned to him to investigate a multimedia enabled mobile phone, which is suspected to be used in a cyber crime. Adam uses a tool, with the help of which he can recover deleted text messages, photos, and call logs of the mobile phone. Which of the following tools is Adam using?
Which of the following Denial-of-Service (DoS) attacks employ IP fragmentation mechanism?
Each correct answer represents a complete solution. Choose two.
Which of the following utilities produces the output displayed in the image below?
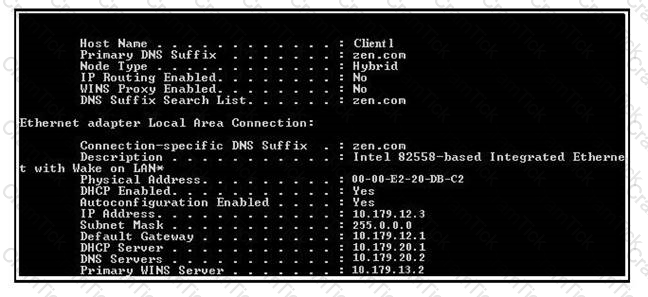
You work as a Network Administrator for McRobert Inc. Your company has a TCP/IP-based network. You have configured a WAN link for the network. You are facing connectivity problem across the WAN link. What will be your first step in troubleshooting the issue?
Which of the following is a correct sequence of different layers of Open System Interconnection (OSI) model?
In which of the following attacks does a hacker imitate a DNS server and obtain the entire DNS database?
Mark works as a Network Administrator for Infonet Inc. The company has a Windows 2000 domainbased network. Mark wants to block all NNTP traffic between the network and the Internet. How will he configure the network?
Which of the following NETSH commands for interface Internet protocol version 4 (IPv4) is used to add a DNS server to a list of DNS servers for a specified interface?
Which of the following sectors on a hard disk contains codes that the computer uses to start the system?
Sandra, a novice computer user, works on Windows environment. She experiences some problem regarding bad sectors formed in a hard disk of her computer. She wants to run CHKDSK command to check the hard disk for bad sectors and to fix the errors, if any, occurred. Which of the following switches will she use with CHKDSK command to accomplish the task?
Which of the following image file formats uses a lossy data compression technique?
You work as a Network Administrator for McRobert Inc. You want to know the NetBIOS name of your computer. Which of the following commands will you use?
An attacker changes the address of a sub-routine in such a manner that it begins to point to the address of the malicious code. As a result, when the function has been exited, the application can be forced to shift to the malicious code. The image given below explains this phenomenon:
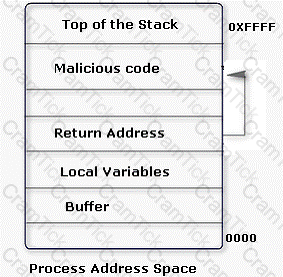
Which of the following tools can be used as a countermeasure to such an attack?
Adam works as a professional Computer Hacking Forensic Investigator. He has been assigned with a project to investigate a computer in the network of SecureEnet Inc. The compromised system runs on Windows operating system. Adam decides to use Helix Live for Windows to gather data and electronic evidences starting with retrieving volatile data and transferring it to server component via TCP/IP. Which of the following application software in Helix Windows Live will he use to retrieve volatile data and transfer it to the server component via TCP/IP?
Which of the following is computed from an arbitrary block of digital data for the purpose of detecting accidental errors?
You are the Administrator for a Windows 2000 based network that uses DHCP to dynamically assign IP addresses to the clients and DNS servers. You want to ensure that the DNS servers can communicate with another DNS server. Which type of query will you run to achieve this?
Which of the following is the correct order of loading system files into the main memory of the system, when the computer is running on Microsoft's Windows XP operating system?
You work as a Network Administrator for McNeil Inc. The company has a TCP/IP-based network.
You are configuring an Internet connection for your company. Your Internet service provider (ISP) has a UNIX-based server. Which of the following utilities will enable you to access the UNIX server, using a text-based connection?
Trinity wants to send an email to her friend. She uses the MD5 generator to calculate cryptographic hash of her email to ensure the security and integrity of the email. MD5 generator, which Trinity is using operates in two steps:
Creates check file
Verifies the check file
Which of the following MD5 generators is Trinity using?
Which of the following utilities is used to verify the existence of a host in a network?
You work as a Network Administrator for Infonet Inc. The company has a Windows Server 2008 Active Directory-based single forest multiple domain IPv4 network. All the DNS servers on the network run Windows Server 2008. The users in the network use NetBIOS name to connect network application on the network. You have migrated the network to IPv6-enabled network. Now you want to enable DNS Server to perform lookups in GlobalNames Zone. Which of the following commands will you use to accomplish the task?
Security Administration | GCIA Questions Answers | GCIA Test Prep | GCIA – GIAC Certified Intrusion Analyst Practice Test Questions PDF | GCIA Online Exam | GCIA Practice Test | GCIA PDF | GCIA Test Questions | GCIA Study Material | GCIA Exam Preparation | GCIA Valid Dumps | GCIA Real Questions | Security Administration GCIA Exam Questions


