Refer to the exhibit.
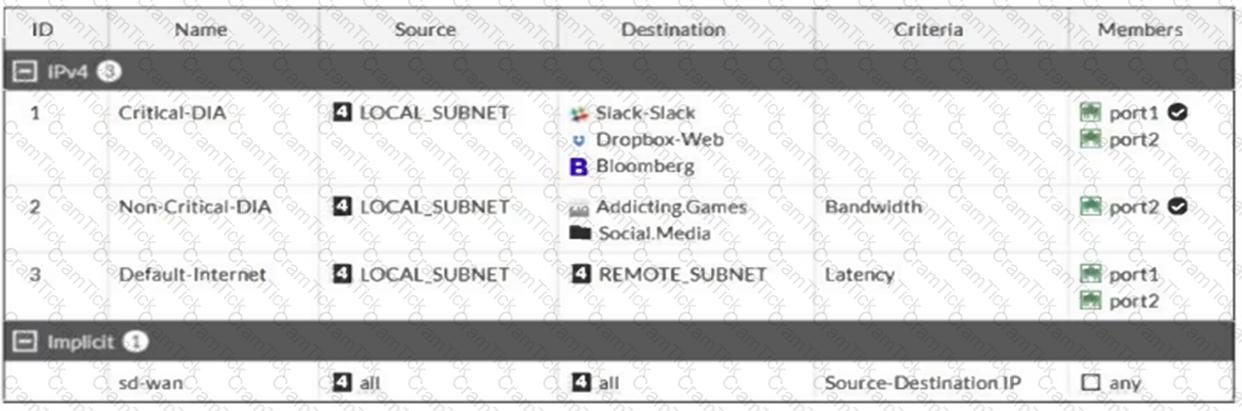
Which algorithm does SD-WAN use to distribute traffic that does not match any of the SD-WAN rules?
Which engine handles application control traffic on the next-generation firewall (NGFW) FortiGate?
Refer to the exhibits, which show the firewall policy and the security profile for Facebook.
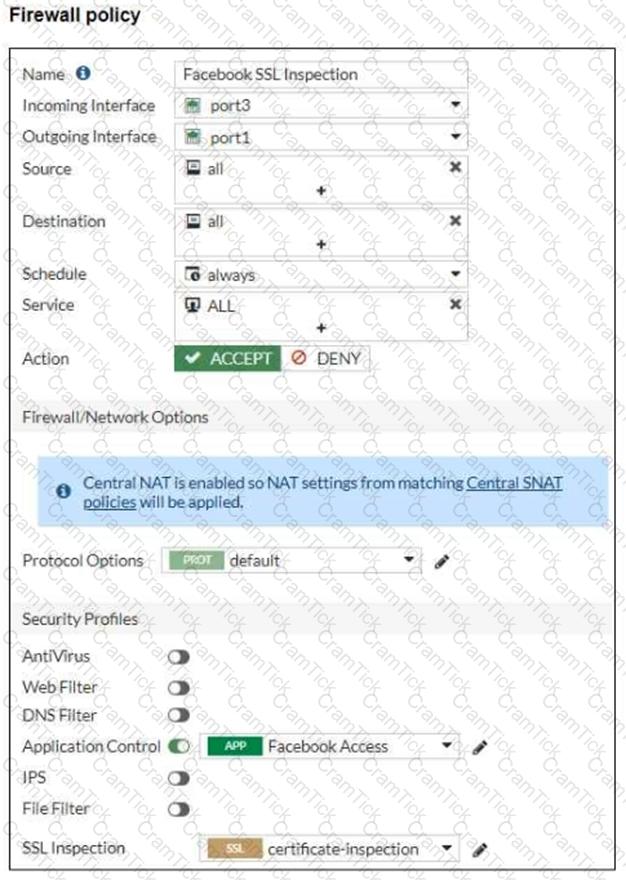
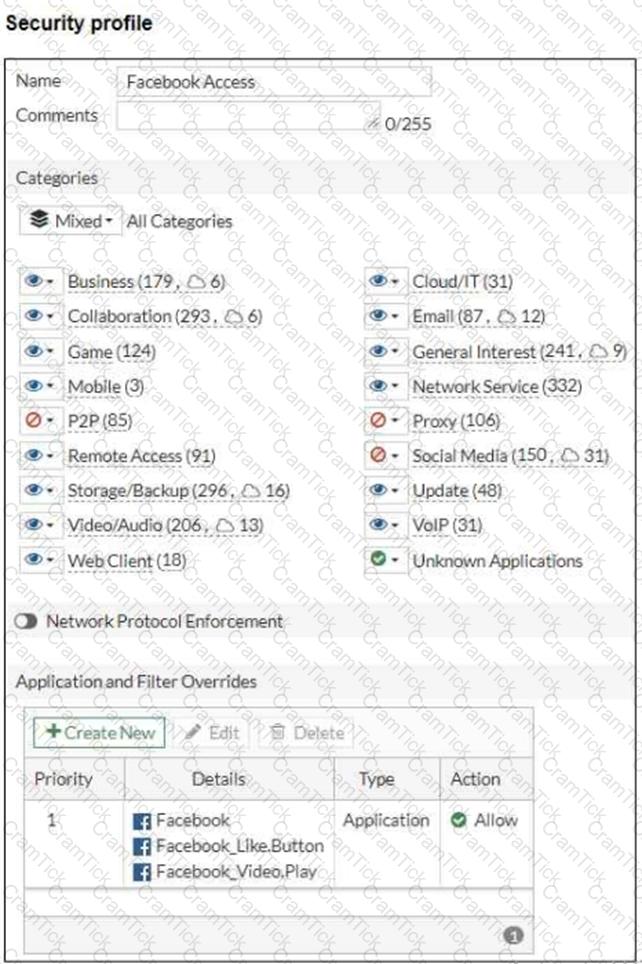
Users are given access to the Facebook web application. They can play video content hosted on Facebook but they are unable to leave reactions on videos or other types of posts.
Which part of the configuration must you change to resolve the issue?
Refer to the exhibit.
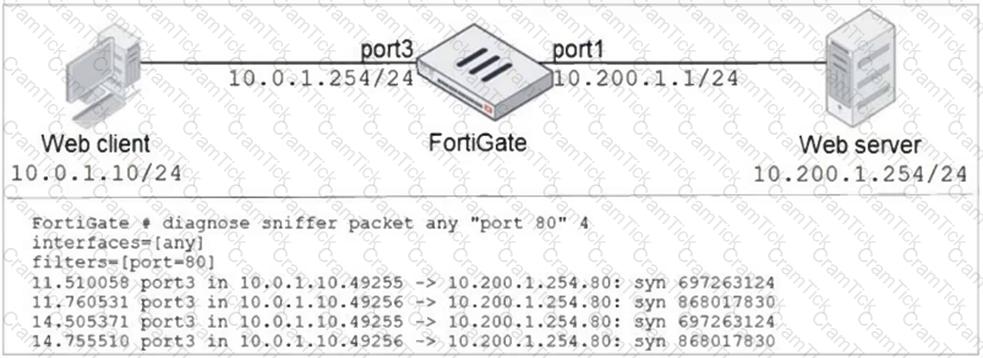
In the network shown in the exhibit, the web client cannot connect to the HTTP web server. The administrator runs the FortiGate built-in sniffer and gets the output shown in the exhibit.
What should the administrator do next, to troubleshoot the problem?
Which two statements about equal-cost multi-path (ECMP) configuration on FortiGate are true? (Choose two.)
A FortiGate firewall policy is configured with active authentication however, the user cannot authenticate when accessing a website.
Which protocol must FortiGate allow even though the user cannot authenticate?
Which two attributes are required on a certificate so it can be used as a CA certificate on SSL inspection? (Choose two.)
An administrator must enable a DHCP server on one of the directly connected networks on FortiGate. However, the administrator is unable to complete the process on the GUI to enable the service on the interface.
In this scenario, what prevents the administrator from enabling DHCP service?
Which three CLI commands, can you use to troubleshoot Layer 3 issues if the issue is in neither the physical layer nor the link layer? (Choose three.)
Refer to the exhibits.

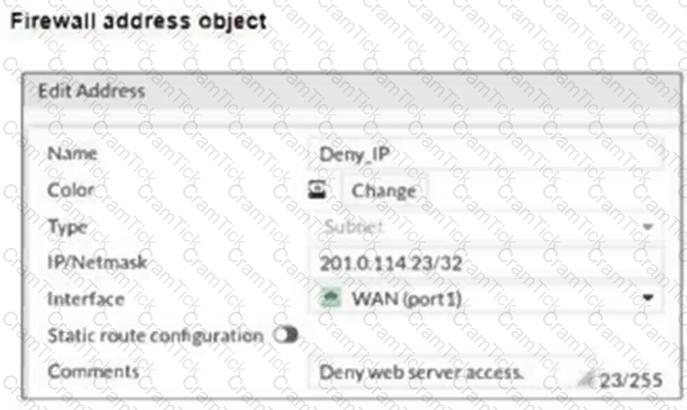
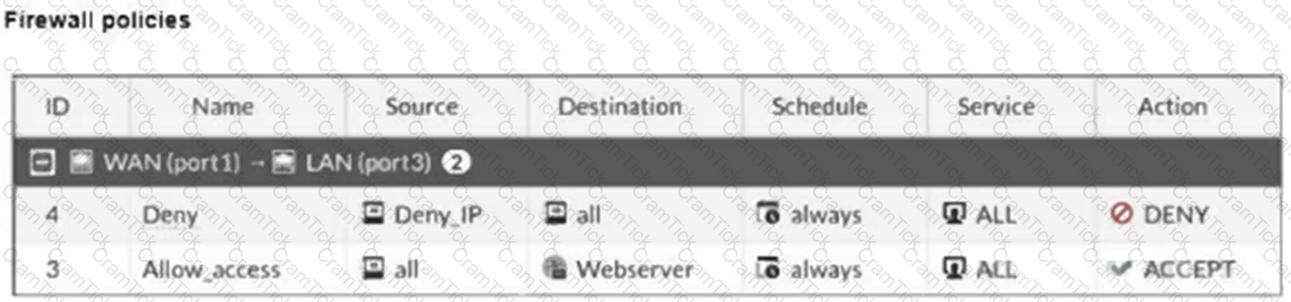
The exhibits show a diagram of a FortiGate device connected to the network, and the firewall configuration.
An administrator created a Deny policy with default settings to deny Webserver access for Remote-User2.
The policy should work such that Remote-User1 must be able to access the Webserver while preventing Remote-User2 from accessing the Webserver.
Which two configuration changes can the administrator make to the policy to deny Webserver access for Remote-User2? (Choose two.)
Refer to the exhibit.

FortiGate has two separate firewall policies for Sales and Engineering to access the same web server with the same security profiles.
Which action must the administrator perform to consolidate the two policies into one?
FortiGate is integrated with FortiAnalyzer and FortiManager.
When a firewall policy is created, which attribute is added to the policy to improve functionality and to support recording logs to FortiAnalyzer or FortiManager?
An administrator is configuring an IPsec VPN between site A and site В. The Remote Gateway setting in both sites has been configured as Static IP Address.
For site A, the local quick mode selector is 192.168.1.0/24 and the remote quick mode selector is 192.168.2.0/24.
Which subnet must the administrator configure for the local quick mode selector for site B?
Refer to the exhibit.
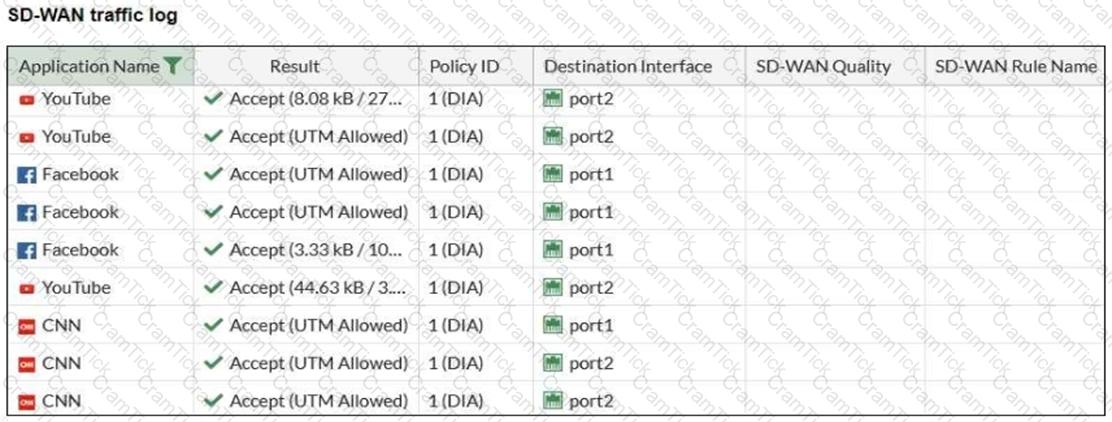
The administrator configured SD-WAN rules and set the FortiGate traffic log page to display SD-WAN-specific columns: SD-WAN Quality and SD-WAN Rule Name.
FortiGate allows the traffic according to policy ID 1. This is the policy that allows SD-WAN traffic.
Despite these settings the traffic logs do not show the name of the SD-WAN rule used to steer those traffic flows.
What can be the reason?


