A developer is sending requests to a SaaS application. The developer becomes unable to send more requests after sending a number of them, but other developers can still send requests. Which of the following is most likely causing the issue?
Which of the following refers to the idea that data should stay within certain borders or territories?
A systems engineer is migrating a batch of 25 VMs from an on-premises compute cluster to a public cloud using the public cloud's migration agent. The migration job shows data
copies at a rate of 250Mbps. After five servers migrate, the data copies at a rate of 25Mbps. Which of the following should the engineer review first to troubleshoot?
A cloud engineer wants to implement a monitoring solution to detect cryptojacking and other cryptomining malware on cloud instances. Which of the following metrics would most likely be used to identify the activity?
Which of the following is an auditing procedure that ensures service providers securely manage the data to protect the interests of the organization and the privacy of its clients?
A high-usage cloud resource needs to be monitored in real time on specific events to guarantee its availability. Which of the following actions should be used to meet this requirement?
A SaaS provider introduced new software functionality for customers as part of quarterly production enhancements. After an update is implemented, users cannot locate certain transactions from an inbound integration. During the investigation, the application owner finds the following error in the logs:
Error: REST API - Deprecated call is no longer supported in this release.
Which of the following is the best action for the application owner to take to resolve the issue?
Which of the following is a customer be responsible for in a provider-managed database service? (Select two).
A cloud deployment uses three different VPCs. The subnets on each VPC need to communicate with the others over private channels. Which of the following will achieve this objective?
A cloud engineer is running a latency-sensitive workload that must be resilient and highly available across multiple regions. Which of the following concepts best addresses these
requirements?
A company has decided to adopt a microservices architecture for its applications that are deployed to the cloud. Which of the following is a major advantage of this type of architecture?
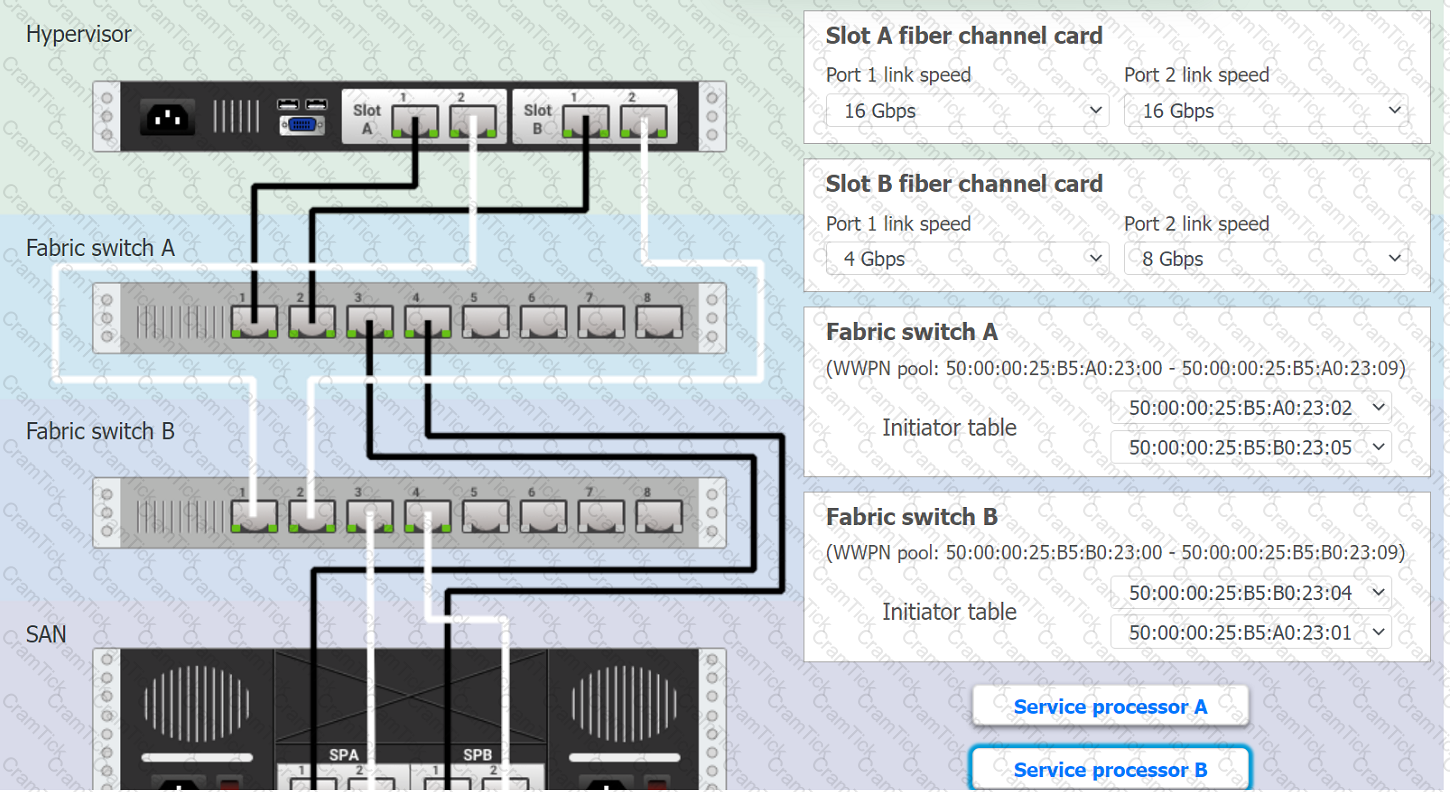
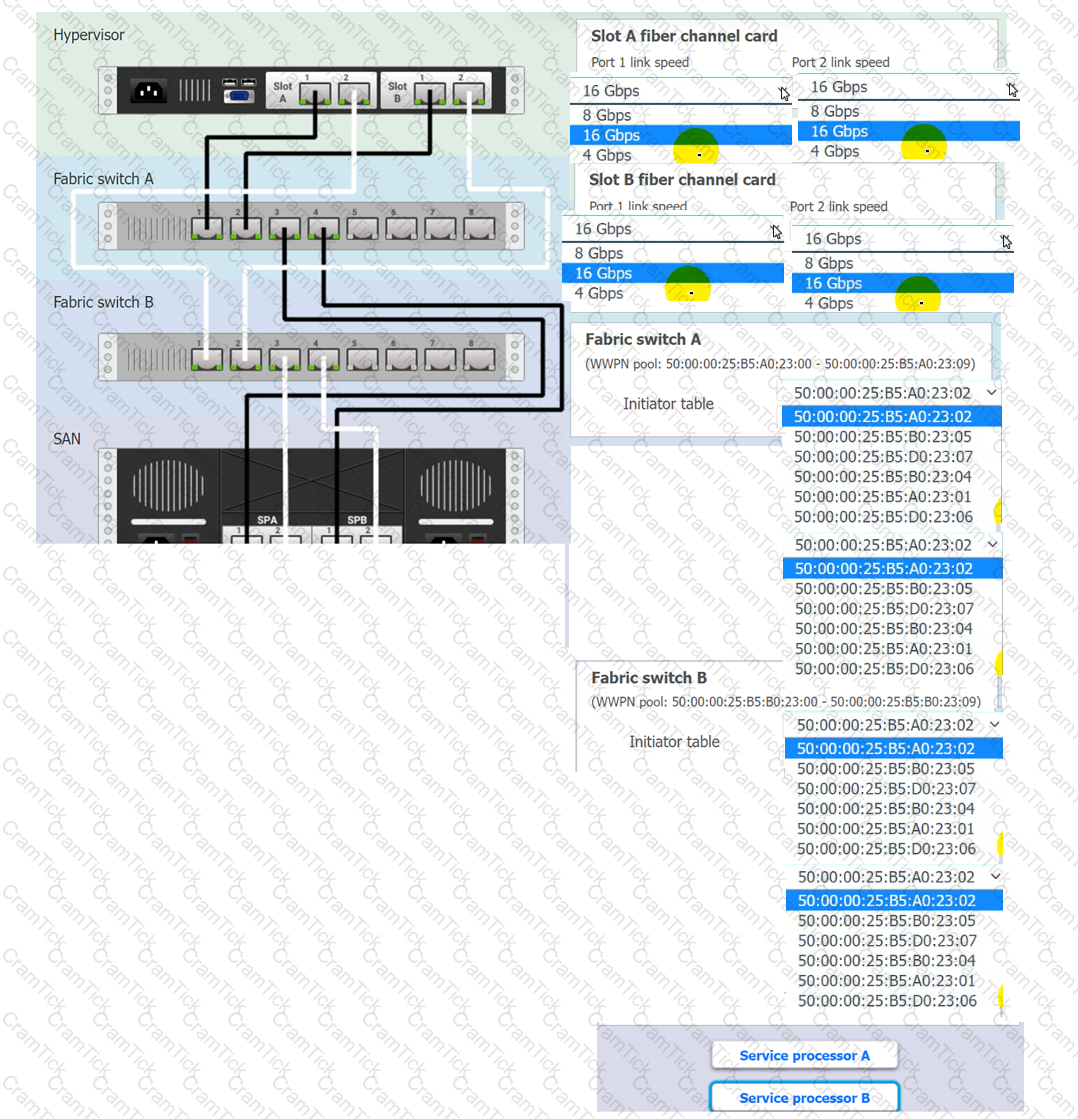
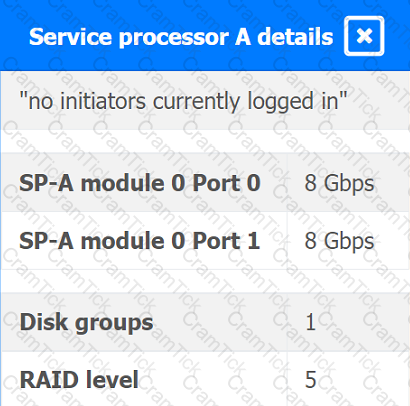
You are a cloud engineer working for a cloud service provider that is responsible for an
IaaS offering.
Your customer, who creates VMs and manages virtual storage, has noticed I/O bandwidth issues and low IOPS (under 9000).
Your manager wants you to verify the proper storage configuration as dictated by your service level agreement (SLA).
The SLA specifies:
. Each SFP on the hypervisor host must be set to the maximum link speed
allowed by the SAN array. . All SAN array disk groups must be configured in a RAID 5.
. The SAN array must be fully configured for redundant fabric paths. . IOPS should not fall below 14000
INSTRUCTIONS
Click on each service processor to review the displayed information. Then click on the drop-down menus to change the settings of each device as necessary to conform to the SLA requirements.

Which of the following communication methods between on-premises and cloud environments would ensure minimal-to-low latency and overhead?
An DevOps engineer is receiving reports that users can no longer access the company's web application after hardening of a web server. The users are receiving the following error:
ERR_SSLJ/ERSION_OR_CIPHER_MISMATCH.
Which of the following actions should the engineer take to resolve the issue?
A cloud architect is preparing environments to develop a new application that will process sensitive data. The project team consists of one internal developer, two external consultants, and three testers. Which of the following is the most important security control for the cloud architect to consider implementing?
An organization's web application experiences penodic bursts of traffic when a new video is launched. Users are reporting poor performance in the middle of the month. Which of the following scaling approaches should the organization use to scale based on forecasted traffic?
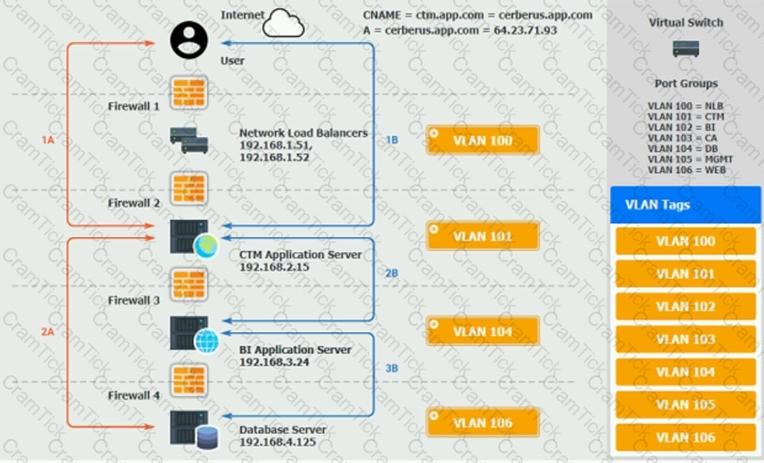
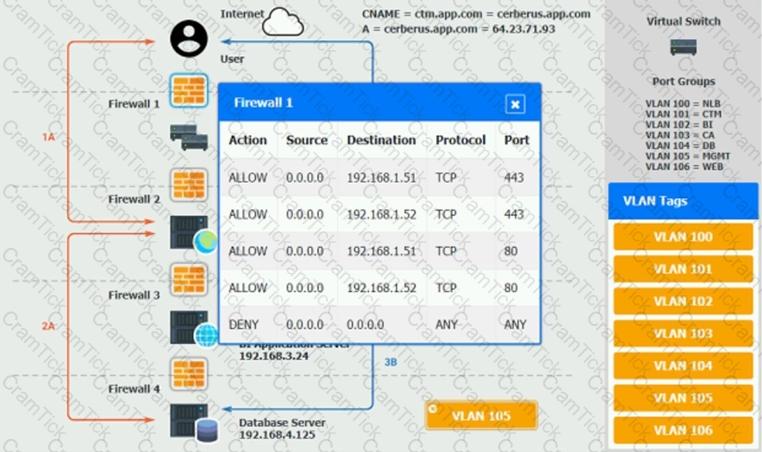
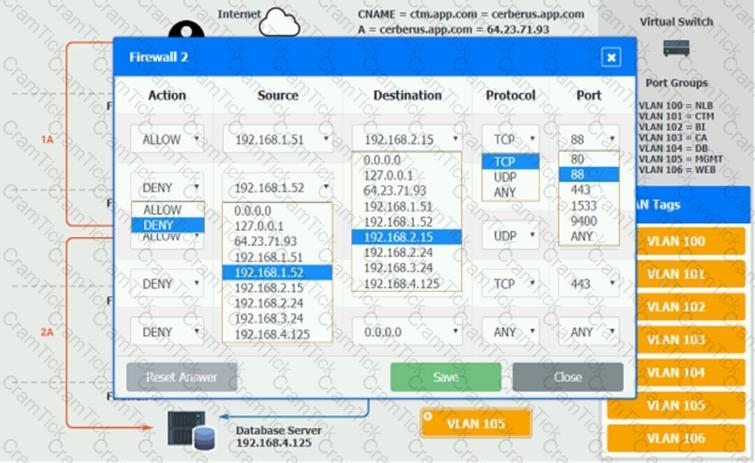
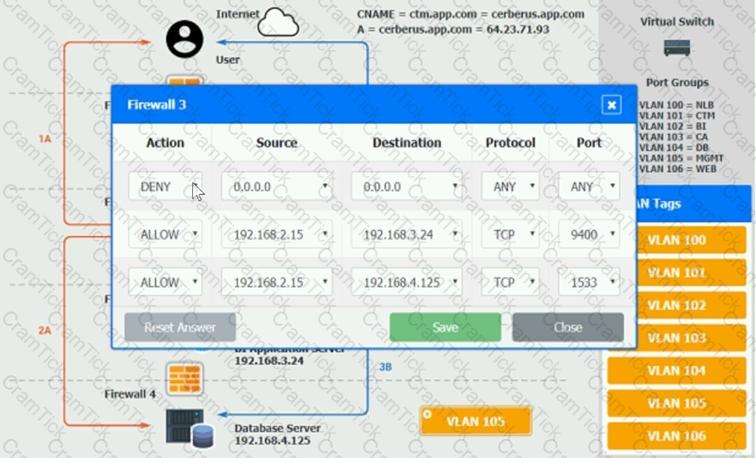
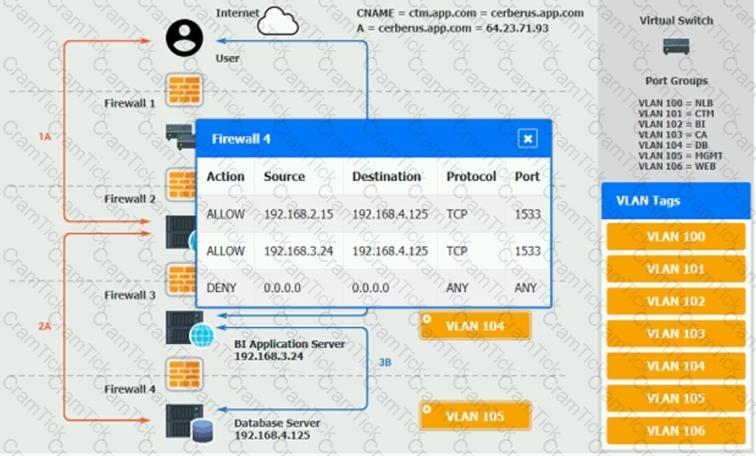
The QA team is testing a newly implemented clinical trial management (CTM) SaaS application that uses a business intelligence application for reporting. The UAT users were instructed to use HTTP and HTTPS.
Refer to the application dataflow:
1A – The end user accesses the application through a web browser to enter and view clinical data.
2A – The CTM application server reads/writes data to/from the database server.
1B – The end user accesses the application through a web browser to run reports on clinical data.
2B – The CTM application server makes a SOAP call on a non-privileged port to the BI application server.
3B – The BI application server gets the data from the database server and presents it to the CTM application server.
When UAT users try to access the application using https://ctm.app.com or http://ctm.app.com, they get a message stating: “Browser cannot display the webpage.” The QA team has raised a ticket to troubleshoot the issue.
INSTRUCTIONS
You are a cloud engineer who is tasked with reviewing the firewall rules as well as virtual network settings.
You should ensure the firewall rules are allowing only the traffic based on the dataflow.
You have already verified the external DNS resolution and NAT are working.
Verify and appropriately configure the VLAN assignments and ACLs. Drag and drop the appropriate VLANs to each tier from the VLAN Tags table. Click on each Firewall to change ACLs as needed.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
A network administrator is budding a site-to-site VPN tunnel from the company's headquarters office 10 the company's public cloud development network. The network administrator confirms the following:
The VPN tunnel is established on the headquarter office firewall.
While inside the office, developers report that they cannot connect to the development network resources.
While outside the office on a client VPN, developers report that they can connect to the development network resources.
The office and the client VPN have different IP subnet ranges.
The firewall flow logs show VPN traffic is reaching the development network from the office.
Which of the following is the next step the next network administrator should take to troubleshoot the VPN tunnel?
A cloud administrator wants to provision a host with two VMs. The VMs require the following:
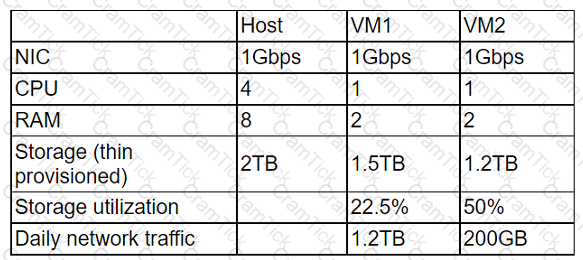
After configuring the servers, the administrator notices that during certain hours of the day, the performance heavily degrades. Which of the following is the best explanation?
Which of the following cloud deployment strategies is best for an organization that wants to run open-source workloads with other organizations that are sharing the cost?
Which of the following application migration strategies will best suit a customer who wants to move a simple web application from an on-premises server to the cloud?
A cloud solutions architect is designing a VM-based solution that requires reducing the cost as much as possible. Which of the following solutions will best satisfy this requirement?
Which of the following do developers use to keep track of changes made during software development projects?
A cloud engineer is receiving multiple alerts from the infrastructure monitoring agent. The alerts state that all the VMs in the public subnet are at 100% CPU utilization. However, when the engineer checks the network utilization of the VMs, the network throughput is at normal levels. Which of the following is the most likely cause of this issue?
An IT security team wants to ensure that the correct parties are informed when a specific user account is signed in. Which of the following would most likely allow an administrator to address this concern?
The change control board received a request to approve a configuration change 10 deploy in the cloud production environment. Which of the following should have already been competed?
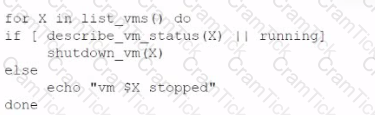
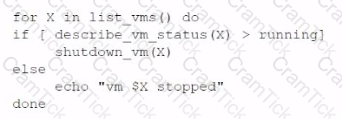
An administrator is creating a cron job that shuts down the virtual machines at night to save on costs. Which of the following is the best way to achieve this task?
A)
B)
C)

D)
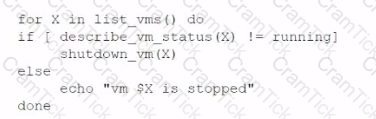
A cloud developer needs to update a REST API endpoint to resolve a defect. When too many users attempt to call the API simultaneously, the following message is displayed:
Error: Request Timeout - Please Try Again Later
Which of the following concepts should the developer consider to resolve this error?
A manager wants information about which users signed in to a certain VM during the past month. Which of the following can the cloud administrator use to obtain this information?
A cloud engineer is collecting web server application logs to troubleshoot intermittent issues. However, the logs are piling up and causing storage issues. Which of the following log
mechanisms should the cloud engineer implement to address this issue?
Which of the following types of releases best describes the update made to a code repository production release when it changes from version 1.0 to version 1.1?
A banking firm's cloud server will be decommissioned after a successful proof of concept using mirrored data. Which of the following is the best action to take regarding the storage used on the decommissioned server?
A customer's facility is located in an area where natural disasters happen frequently. The customer requires the following:
• Data resiliency due to exposure to frequent natural disasters
• Data localization because of privacy regulations in the country
• High availability
Which of the following cloud resources should be provisioned to meet these requirements?
Which of the following vulnerability management concepts is best defined as the process of discovering vulnerabilities?
A video surveillance system records road incidents and stores the videos locally before uploading them to the cloud and deleting them from local storage. Which of the following
best describes the nature of the local storage?
A security engineer Identifies a vulnerability m a containerized application. The vulnerability can be exploited by a privileged process to read tie content of the host's memory. The security engineer reviews the following Dockerfile to determine a solution to mitigate similar exploits:

Which of the following is the best solution to prevent similar exploits by privileged processes?
A company uses containers to implement a web application. The development team completed internal testing of a new feature and is ready to move the feature to the production
environment. Which of the following deployment models would best meet the company's needs while minimizing cost and targeting a specific subset of its users?
A company migrated its CRM system to a SaaS solution. The security team is updating the RAG matrix for the newly migrated CRM. Given the following table:
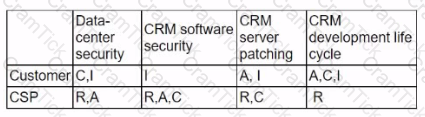
Which of the following responsibility assignments best aligns with the shared responsibility model for the new CRM?
A cloud engineer is developing an operating expense report that will be used to purchase various cloud billing models for virtual machine instances. The cloud billing model must meet the following requirements:
• The instance cannot be ephemeral.
• The minimum life cycle of the instance is expected to be five years.
• The software license is charged per physical CPU count.
Which of the following models would best meet these requirements?
A company is required to save historical data for seven years. A cloud administrator implements a script that automatically deletes data older than seven years. Which of the following concepts best describes why the historical data is being deleted?
An organization has been using an old version of an Apache Log4j software component in its critical software application. Which of the following should the organization use to
calculate the severity of the risk from using this component?
Which of the following requirements are core considerations when migrating a small business's on-premises applications to the cloud? (Select two).
A cloud administrator needs to collect process-level, memory-usage tracking for the virtual machines that are part of an autoscaling group. Which of the following is the best way to
accomplish the goal by using cloud-native monitoring services?
A systems administrator is configuring backups on a VM and needs the process to run as quickly as possible, reducing the bandwidth on the network during all times from Monday through Saturday. In the event of data corruption, the management team expects the mean time to recovery to be as low as possible. Which of the following backup methods can the administrator use to accomplish these goals?
A cloud architect attempts to modify a protected branch but is unable to do so. The architect receives an error indicating the action cannot be completed. Which of the following should the architect try instead''
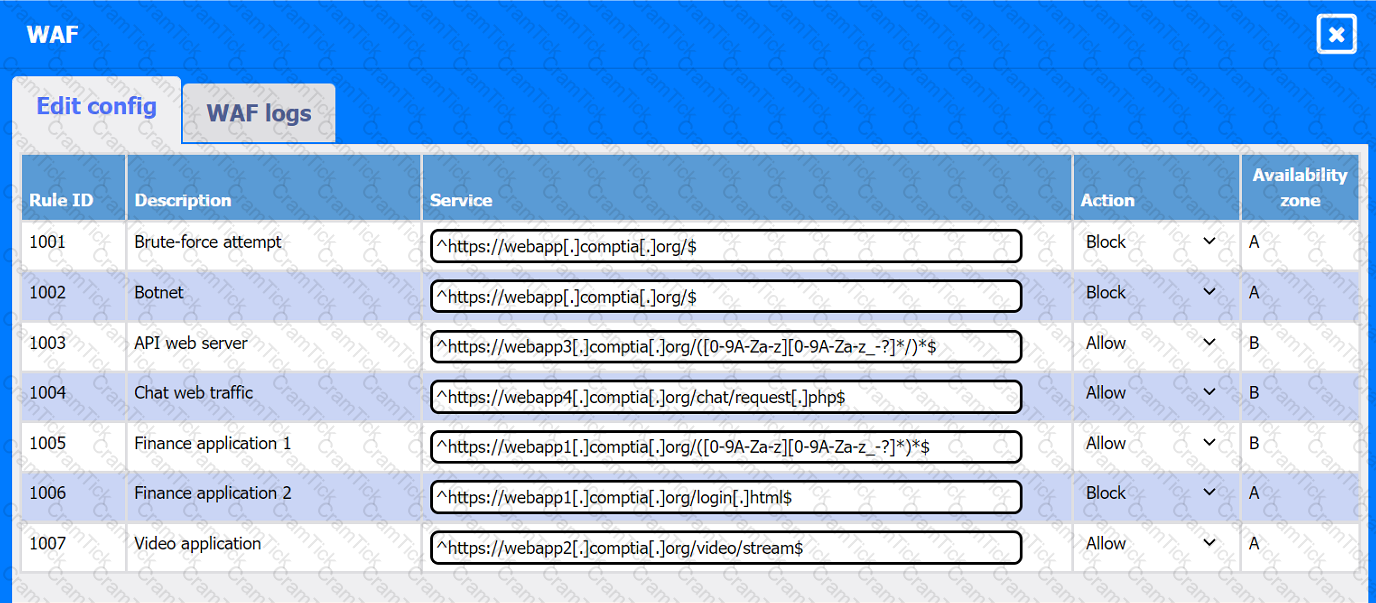
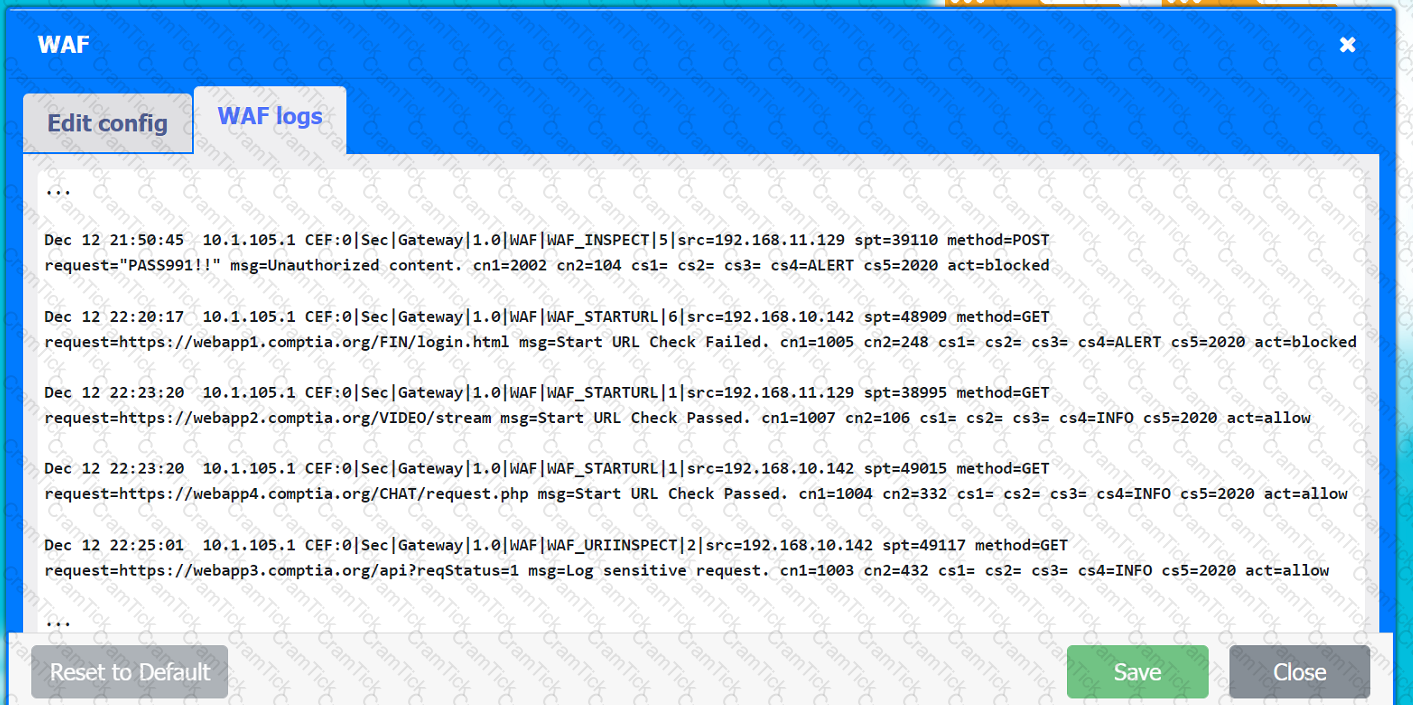
A company hosts various containerized applications for business uses. A client reports that one of its routine business applications fails to load the web-based login prompt hosted in the company cloud.
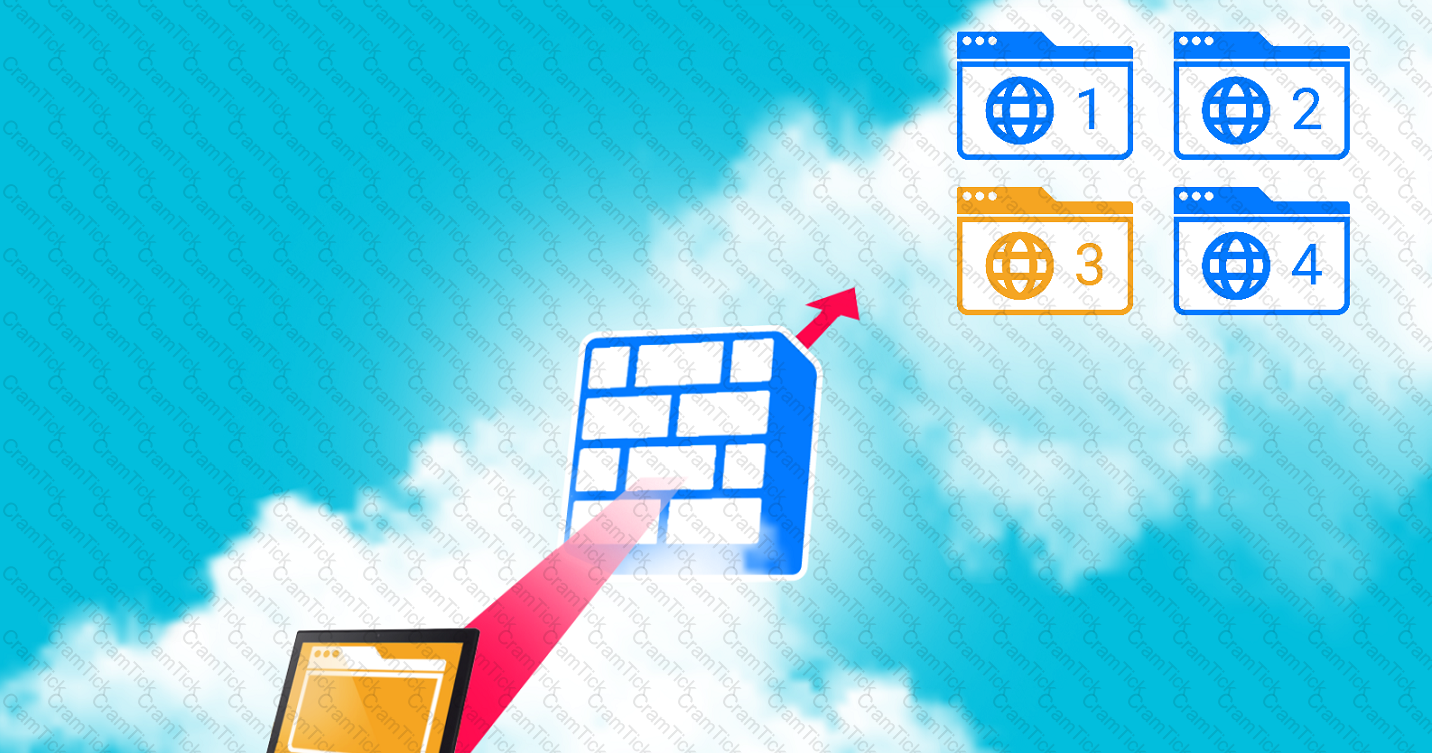
INSTRUCTIONS
Click on each device and resource. Review the configurations, logs, and characteristics of each node in the architecture to diagnose the issue. Then, make the necessary changes to the WAF configuration to remediate the issue.
Web app 1
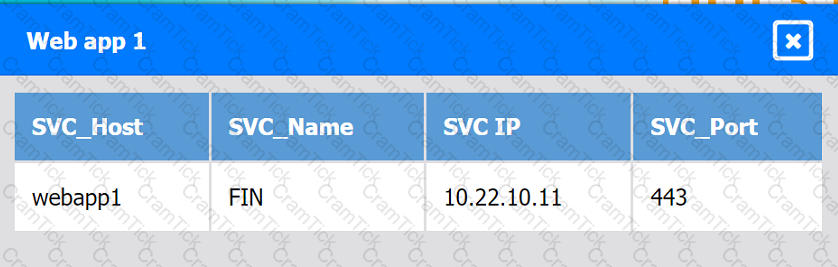
Web app 2

Web app 3
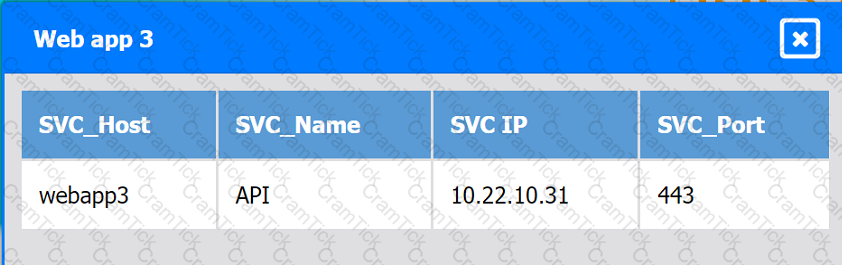
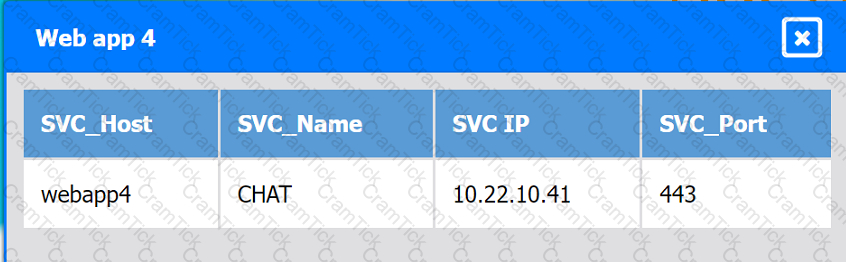
Web app 4
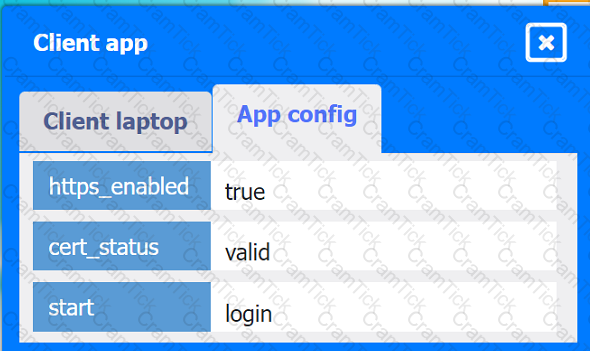
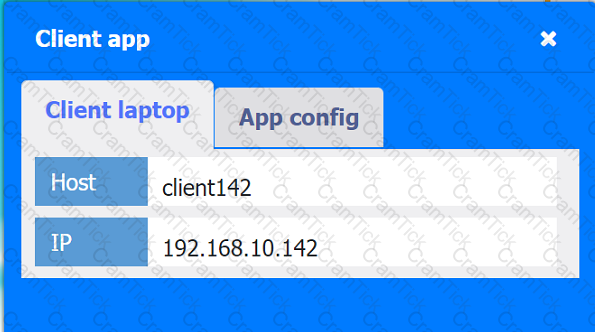
Client app
A cloud engineer needs to deploy a new version of a web application to 100 servers. In the past, new version deployments have caused outages. Which of the following deployment types should the cloud engineer implement to prevent the outages from happening this time?
A cloud engineer is troubleshooting an application that consumes multiple third-party REST APIs. The application is randomly experiencing high latency. Which of the following would best help determine the source of the latency?
Which of the following industry standards mentions that credit card data must not be exchanged or stored in cleartext?
A cloud engineer was deploying the company's payment processing application, but it failed with the following error log:
ERFOR:root: Transaction failed http 429 response, please try again Which of the following are the most likely causes for this error? (Select two).
Which of the following network protocols is generally used in a NAS environment?
A company operates a website that allows customers to upload, share, and retain full ownership of their photographs. Which of the following could affect image ownership as the website usage expands globally?
A cloud engineer wants to deploy a new application to the cloud and is writing the following script:
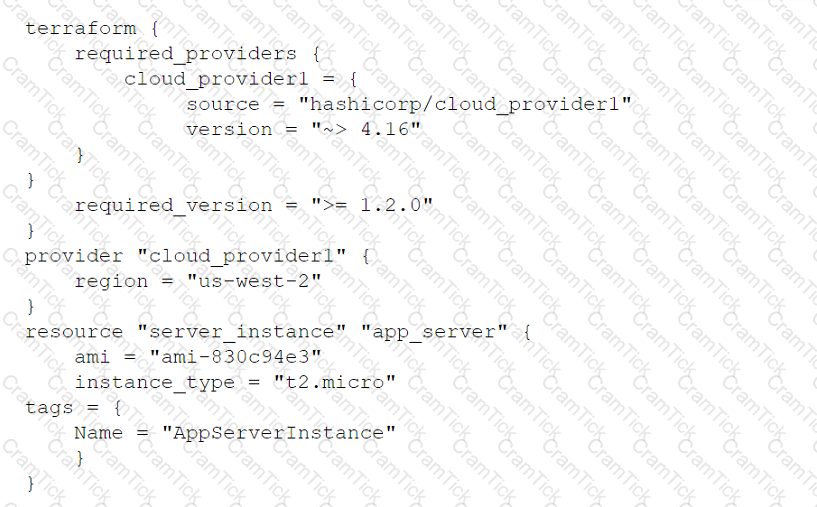
Which of the following actions will this script perform?
A company developed an online trading platform. The engineering team selected event-based scaling for the platform's underlying resources. The platform resources scale up with every 2,000 subscribed users. The engineering team finds out that although compute utilization is low, scaling is still occurring. Which of the following statements best explains why this is the case?
Which of the following technologies should be used by a person who is visually impaired to access data from the cloud?
A cloud engineer is exploring options to reduce the management overhead of the servers and network. Which of the following cloud service models should the engineer implement?
An organization has been using an old version of an Apache Log4j software component in its critical software application. Which of the following should the organization use to calculate the severity of the risk from using this component?
A CI/CD pipeline is used to deploy VMs to an laaS environment. Which of the following can be used to harden the operating system once the VM is running?
A cloud solutions architect needs to design a solution that will collect a report and upload it to an object storage service every time a virtual machine is gracefully or non-gracefully
stopped. Which of the following will best satisfy this requirement?
A developer is building an application that has multiple microservices that need to communicate with each other. The developer currently manually updates the IP address of each service. Which of the following best resolves the communication issue and automates the process?
A company has ten cloud engineers working on different manual cloud deployments. In the past, engineers have had difficulty keeping deployments consistent. Which of the following is the best method to address this issue?
A security team recently hired multiple interns who all need the same level of access. Which of the following controls should the security team implement to provide access to the
cloud environment with the least amount of overhead?
A cloud administrator needs to distribute workloads across remote data centers for redundancy reasons. Which of the following deployment strategies would eliminate downtime, accelerate deployment, and remain cost efficient?