An incident responder is asked to create a disk image of a compromised Linux server. Which of the following commands should be used to do this?
During a malware outbreak, a security analyst has been asked to capture network traffic in hourly increments for analysis by the incident response team. Which of the following tcpdump commands would generate hourly pcap files?
While a network administrator is monitoring the company network, an unknown local IP address is starting to release high volumes of anonymous traffic to an unknown external IP address. Which of the following would indicate to the network administrator potential compromise?
A forensics investigator has been assigned the task of investigating a system user for suspicion of using a company-owned workstation to view unauthorized content. Which of the following would be a proper course of action for the investigator to take?
An organization’s public information website has been defaced. The incident response team is actively engaged in the following actions:
- Installing patches on the web server
- Turning off unnecessary services on web server
- Adding new ACL rules to the WAF
- Changing all passwords on web server accounts
Which of the following incident response phases is the team MOST likely conducting?
A suspicious laptop is found in a datacenter. The laptop is on and processing data, although there is no application open on the screen. Which of the following BEST describes a Windows tool and technique that an investigator should use to analyze the laptop’s RAM for working applications?
An attacker performs reconnaissance on a Chief Executive Officer (CEO) using publicity available resources to gain access to the CEO’s office. The attacker was in the CEO’s office for less than five minutes, and the attack left no traces in any logs, nor was there any readily identifiable cause for the exploit. The attacker in then able to use numerous credentials belonging to the CEO to conduct a variety of further attacks. Which of the following types of exploit is described?
Which of the following could an attacker use to perpetrate a social engineering attack? (Choose two.)
Which of the following are reasons that a hacker would execute a DoS or a DDoS attack? (Choose two.)
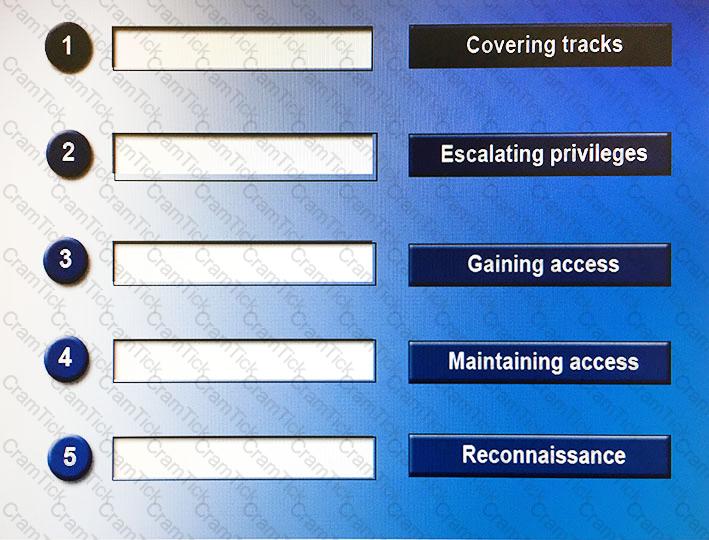
When perpetrating an attack, there are often a number of phases attackers will undertake, sometimes taking place over a long period of time. Place the following phases in the correct chronological order from first (1) to last (5).
CyberSec First Responder | CFR-210 Questions Answers | CFR-210 Test Prep | Logical Operations CyberSec First Responder Questions PDF | CFR-210 Online Exam | CFR-210 Practice Test | CFR-210 PDF | CFR-210 Test Questions | CFR-210 Study Material | CFR-210 Exam Preparation | CFR-210 Valid Dumps | CFR-210 Real Questions | CyberSec First Responder CFR-210 Exam Questions


