You have been assigned to provide security measures for your office's reception area. Although the company needs to provide security measures, costs must be kept to a minimum. Which of the following tools is the most appropriate choice?
You have determined that an attack is currently underway on your database server. An attacker is currently logged in, modifying data. You want to preserve logs, caching and other data on this affected server. Which of the following actions will best allow you to stop the attack and still preserve data?
Your organization has made a particularly unpopular policy decision. Your supervisor fears that a series of attacks may occur as a result. You have been assigned to increase automated auditing on a server. When fulfilling this request, which of the following resources should you audit the most aggressively?
Consider the following image of a packet capture:
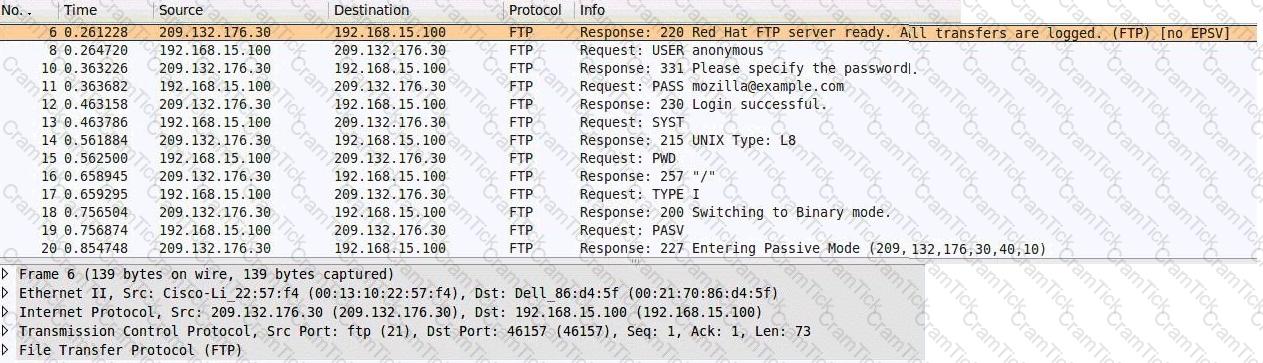

Which of the following best describes the protocol used, along with its primary benefit?
You have discovered that the ls, su and ps commands no longer function as expected. They do not return information in a manner similar to any other Linux system. Also, the implementation of Tripwire you have installed on this server is returning new hash values. Which of the following has most likely occurred?
Web Security Associate | 1D0-571 Questions Answers | 1D0-571 Test Prep | CIW v5 Security Essentials Questions PDF | 1D0-571 Online Exam | 1D0-571 Practice Test | 1D0-571 PDF | 1D0-571 Test Questions | 1D0-571 Study Material | 1D0-571 Exam Preparation | 1D0-571 Valid Dumps | 1D0-571 Real Questions | Web Security Associate 1D0-571 Exam Questions