Which DKEAD category has a risk rating based on the threat exploit's potential level of harm?
Which type of threat exists when an attacker can intercept and manipulate form data after the user clicks the save button but before the request is posted to the API?
Which architecture deliverable identifies the organization's tolerance to security issues and how the organization plans to react if a security issue occurs?
What is a countermeasure to the web application security frame (ASF) data validation/parameter validation threat category?
A security architect is creating a data flow diagram and draws an arrow between two circles.
What does the arrow represent?
A recent vulnerability scan uncovered an XML external entity (XXE) Haw that could allow attackers to return the contents of a system file by including a specific payload in an XML request.
How should the organization remediate this vulnerability?
An individual is developing a software application that has a back-end database and is concerned that a malicious user may run the following SOL query to pull information about all accounts from the database:
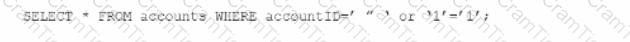
Which technique should be used to detect this vulnerability without running the source codes?
A potential threat was discovered during vulnerability testing when an environment configuration file was found that contained the database username and password stored in plain text.
How should existing security controls be adjusted to prevent this in the future?
Security testers have completed testing and are documenting the results of vulnerability scans and penetration analysis They are also creating documentation lo share with the organization's largest customers.
Which deliverable is being prepared?
During fuzz testing of the new product, an exception was thrown on the order entry view, which caused a full stack dump to be displayed in the browser window that included function names from the source code.
How should existing security controls be adjusted to prevent this in the future?
The software security team prepared a report of necessary coding and architecture changes identified during the security assessment.
Which design and development deliverable did the team prepare?
Company leadership has discovered an untapped revenue stream within its customer base and wants to meet with IT to share its vision for the future and determine whether to move forward.
Which phase of the software development lifecycle (SDLC) is being described?
Which category classifies identified threats that have some defenses in place and expose the application to limited exploits?
Which question reflects the security change management component of the change management process?
Which secure coding best practice says to assume all incoming data should be considered untrusted and should be validated to ensure the system only accepts valid data?
The Chief Information Security Officer (CISO) has recommended contracting with external experts to perform annual reviews of the enterprise's software products, including penetration testing.
Which post-release deliverable is being described?
Which software-testing technique can be automated or semi-automated and provides invalid, unexpected, or random data to the inputs of a computer software program?
The software security group is conducting a maturity assessment using the Open Web Application Security Project Software Assurance Maturity Model (OWASP SAMM). They are currently focused on reviewing design artifacts to ensure they comply with organizational security standards.
Which OpenSAMM business function is being assessed?
Which privacy impact statement requirement type defines how personal information will be protected when authorized or independent external entities are involved?
What is the protection of information and information systems from unauthorized access, use, disclosure, disruption, modification, or distribution to provide confidentiality, integrity, and availability?
The security team is reviewing all noncommercial software libraries used in the new product to ensure they are being used according to the legal specifications defined by the authors.
What activity of the Ship SDL phase is being performed?
Senior IT staff has determined that a new product will be hosted in the cloud and will support web and mobile users. Developers will need to deliver secure REST services. Android and IOS mobile apps. and a web application. Developers are currently determining how to deliver each part of the overall product.
Which phase of the software development lifecycle (SDLC) is being described?
While performing functional testing of the new product from a shared machine, a QA analyst closed their browser window but did not logout of the application. A different QA analyst accessed the application an hour later and was not prompted to login. They then noticed the previous analyst was still logged into the application.
How should existing security controls be adjusted to prevent this in the future?
Which secure coding practice requires users to log in to their accounts using an email address and a password they choose?
Which mitigation technique can be used to light against a threat where a user may gain access to administrator level functionality?
A company is moving forward with a new product. Product scope has been determined, teams have formed, and backlogs have been created. Developers are actively writing code for the new product, with one team concentrating on delivering data via REST services, one Team working on the mobile apps, and a third team writing the web application.
Which phase of the software development lifecycle (SDLC) is being described?
The software security team has been tasked with assessing a document management application that has been in use for many years and developing a plan to ensure it complies with organizational policies.
Which post-release deliverable is being described?
The security software team has cloned the source code repository of the new software product so they can perform vulnerability testing by modifying or adding small snippets of code to see if they can cause unexpected behavior and application failure.
Which security testing technique is being used?
The software security team prepared a detailed schedule napping security development lifecycle phases to the type of analysis they will execute.
Which design and development deliverable aid the team prepare?
The security team contracts with an independent security consulting firm to simulate attacks on deployed products and report results to organizational leadership.
Which category of secure software best practices is the team performing?


