When installing the Vault Conjur Synchronizer, you see this error:
Forbidden
Logon Token is Empty – Cannot logon
Unauthorized
What must you ensure to remediate the issue?
You have a request to protect all the properties around a credential object. When configuring the credential in the Vault, you specified the address, user and password for the credential.
How do you configure the Vault Conjur Synchronizer to properly sync all properties?
A customer wants to ensure applications can retrieve secrets from Conjur in three different data centers if the Conjur Leader becomes unavailable. Conjur Followers are already deployed in each of these data centers.
How should you architect the solution to support this requirement?
You are diagnosing this log entry:
From Conjur logs:
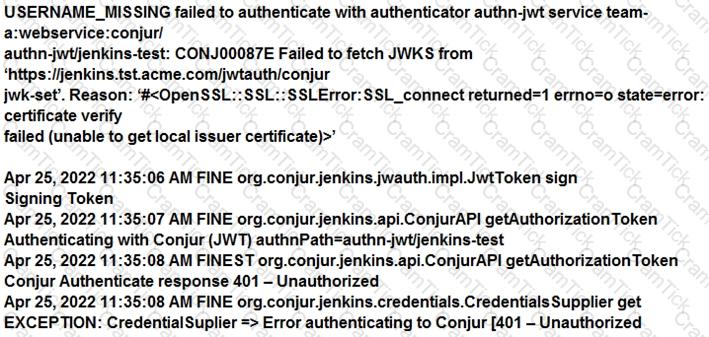
Given these errors, which problem is causing the breakdown?
Which statement is correct about this message?
Message: “[number-of-deleted-rows] rows has successfully deleted “CEADBR009D Finished vacuum”?
When loading policy, you receive a 422 Response from Conjur with a message.
What could cause this issue?
A customer requires high availability in its AWS cloud infrastructure.
What is the minimally viable Conjur deployment architecture to achieve this?
You are deploying Kubernetes resources/objects as Conjur identities.
In addition to Namespace and Deployment, from which options can you choose? (Choose two.)


