You have 50 Azure subscriptions.
You need to monitor resource in the subscriptions for compliance with the ISO 27001:2013 standards. The solution must minimize the effort required to modify the list of monitored policy definitions for the subscriptions.
NOTE: Each correct selection is worth one point.
You design cloud-based software as a service (SaaS) solutions.
You need to recommend ransomware attacks. The solution must follow Microsoft Security Best Practices.
What should you recommend doing first?
You have a Microsoft 365 tenant.
Your company uses a third-party software as a service (SaaS) app named App1 that is integrated with an Azure AD tenant. You need to design a security strategy to meet the following requirements:
• Users must be able to request access to App1 by using a self-service request.
• When users request access to App1, they must be prompted to provide additional information about their request.
• Every three months, managers must verify that the users still require access to Appl.
What should you include in the design?
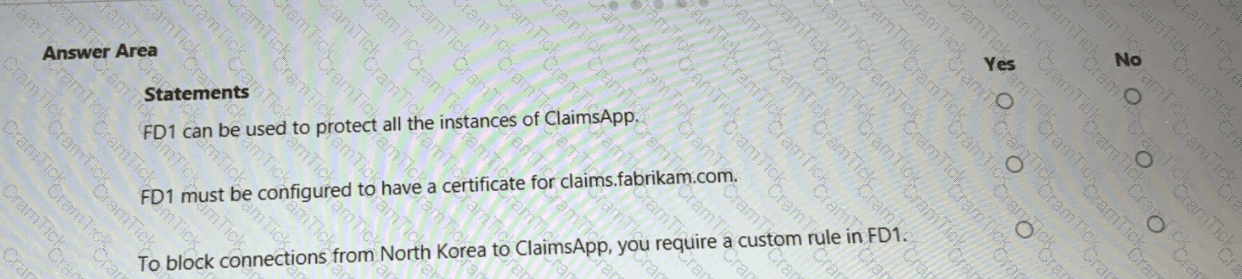
You are evaluating the security of ClaimsApp.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE; Each correct selection is worth one point.
You need to recommend a solution to resolve the virtual machine issue. What should you include in the recommendation? (Choose Two)
You need to recommend a solution to scan the application code. The solution must meet the application development requirements. What should you include in the recommendation?
You need to recommend a solution to meet the security requirements for the virtual machines.
What should you include in the recommendation?
You need to recommend a solution to meet the security requirements for the InfraSec group.
What should you use to delegate the access?
You need to recommend a solution to meet the AWS requirements.
What should you include in the recommendation? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

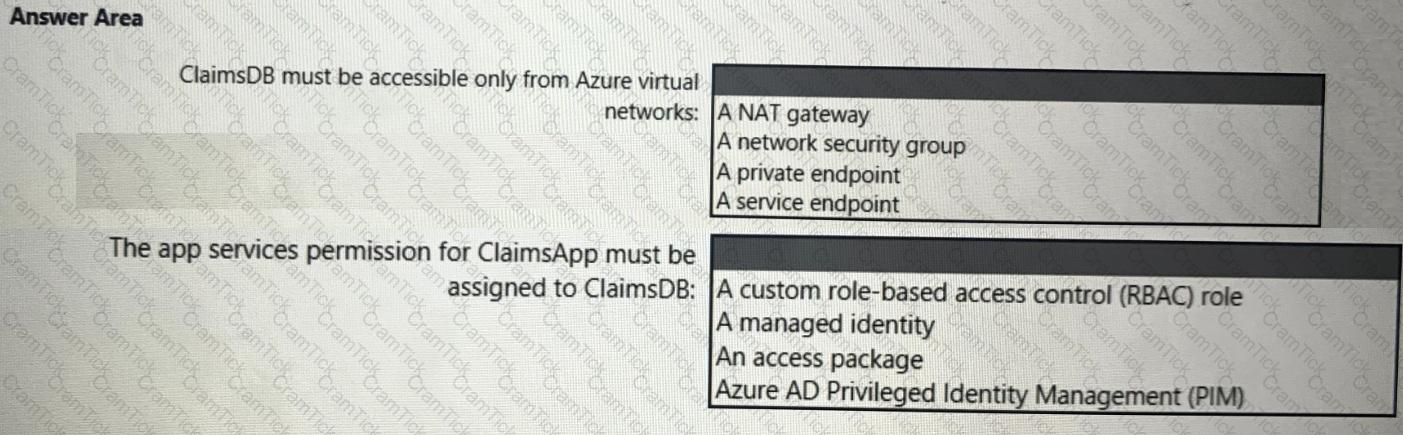
You need to recommend a solution to meet the requirements for connections to ClaimsDB.
What should you recommend using for each requirement? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You need to recommend a solution to secure the MedicalHistory data in the ClaimsDetail table. The solution must meet the Contoso developer requirements.
What should you include in the recommendation?
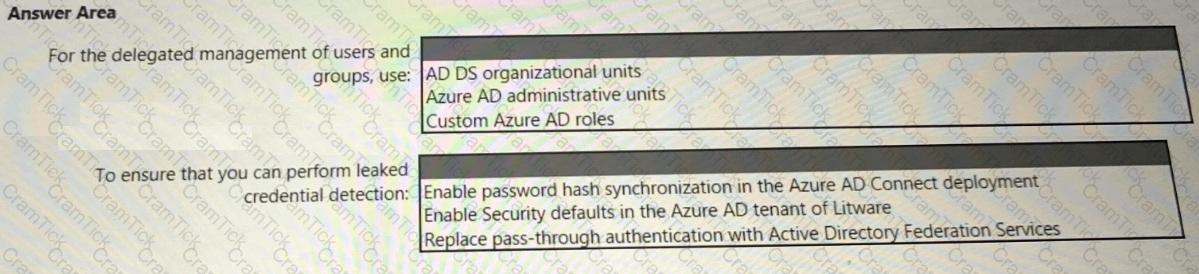
You need to recommend an identity security solution for the Azure AD tenant of Litware. The solution must meet the identity requirements and the regulatory compliance requirements.
What should you recommend? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You need to recommend a strategy for securing the litware.com forest. The solution must meet the identity requirements. What should you include in the recommendation? To answer, select the appropriate options in the answer area. NOTE; Each correct selection is worth one point.
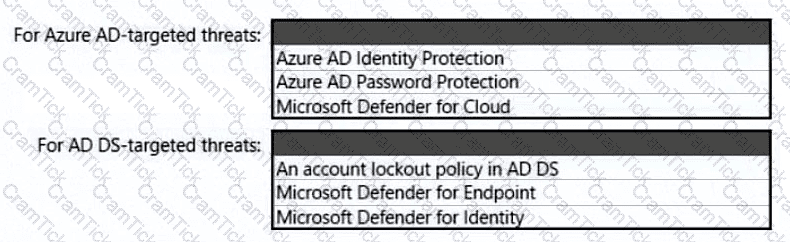
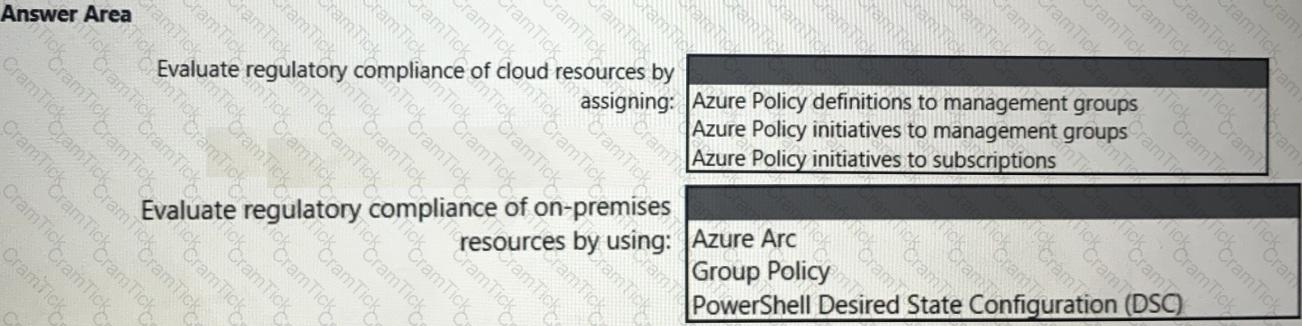
You need to recommend a solution to meet the compliance requirements.
What should you recommend? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You need to recommend a SIEM and SOAR strategy that meets the hybrid requirements, the Microsoft Sentinel requirements, and the regulatory compliance requirements.
What should you recommend? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
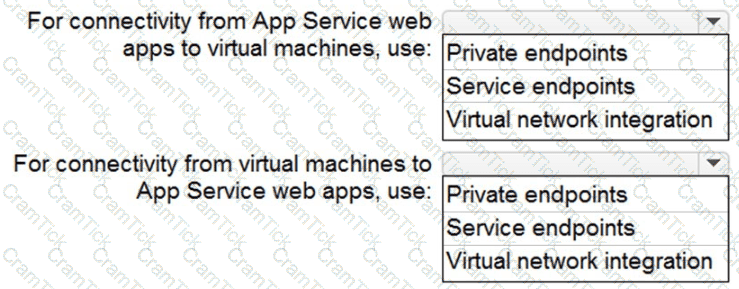
You need to recommend a strategy for App Service web app connectivity. The solution must meet the landing zone requirements. What should you recommend? To answer, select the appropriate options in the answer area. NOTE Each correct selection is worth one point.
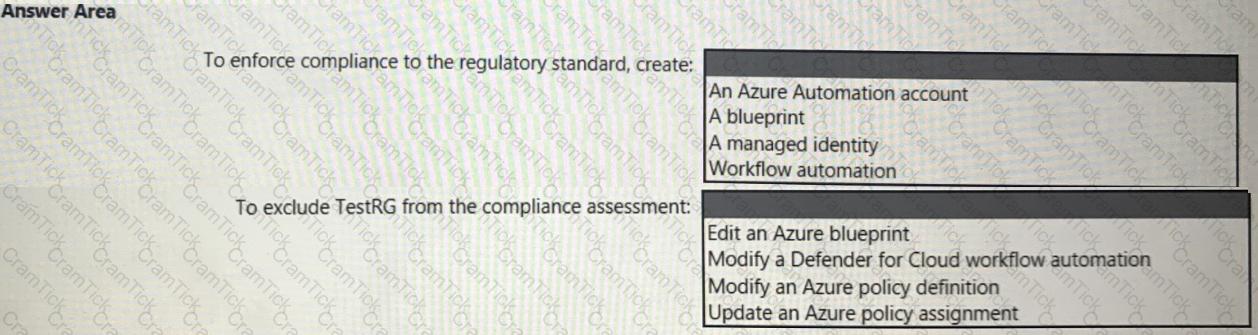
You need to recommend a solution to evaluate regulatory compliance across the entire managed environment. The solution must meet the regulatory compliance requirements and the business requirements.
What should you recommend? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You need to recommend a solution for securing the landing zones. The solution must meet the landing zone requirements and the business requirements.
What should you configure for each landing zone?
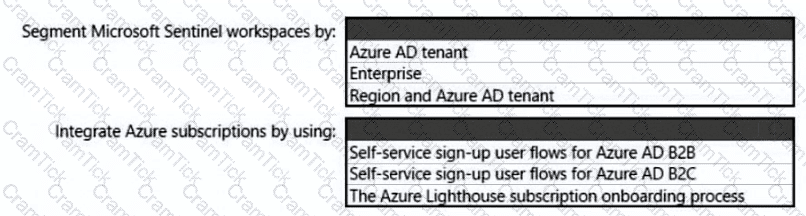
You need to recommend a multi-tenant and hybrid security solution that meets to the business requirements and the hybrid requirements. What should you recommend? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.

You need to design a strategy for securing the SharePoint Online and Exchange Online data. The solution must meet the application security requirements.
Which two services should you leverage in the strategy? Each correct answer presents part of the solution. NOTE; Each correct selection is worth one point.
To meet the application security requirements, which two authentication methods must the applications support? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
Microsoft Certified: Cybersecurity Architect Expert | SC-100 Exam Topics | SC-100 Questions answers | SC-100 Test Prep | Microsoft Cybersecurity Architect Exam Questions PDF | SC-100 Online Exam | SC-100 Practice Test | SC-100 PDF | SC-100 Test Questions | SC-100 Study Material | SC-100 Exam Preparation | SC-100 Valid Dumps | SC-100 Real Questions | Microsoft Certified: Cybersecurity Architect Expert SC-100 Exam Questions


