Following a fire in a data center, the cabling was replaced. Soon after, an administrator notices network issues. Which of the following are the most likely causes of the network issues? (Select two).
A customer recently moved into a new office and notices that some wall plates are not working and are not properly labeled Which of the following tools would be best to identify the proper wiring in the IDF?
A client wants to increase overall security after a recent breach. Which of the following would be best to implement? (Select two.)
A VoIP phone is plugged in to a port but cannot receive calls. Which of the following needs to be done on the port to address the issue?
Early in the morning, an administrator installs a new DHCP server. In the afternoon, some users report they are experiencing network outages. Which of the following is the most likely issue?
A network administrator needs to connect a multimode fiber cable from the MDF to the server room. The administrator connects the cable to Switch 2, but there is no link light. The administrator tests the fiber and finds it does not have any issues. Swapping the connection to Switch 1 in a working port is successful, but the swapped connection does not work on Switch 2. Which of the following should the administrator verify next?
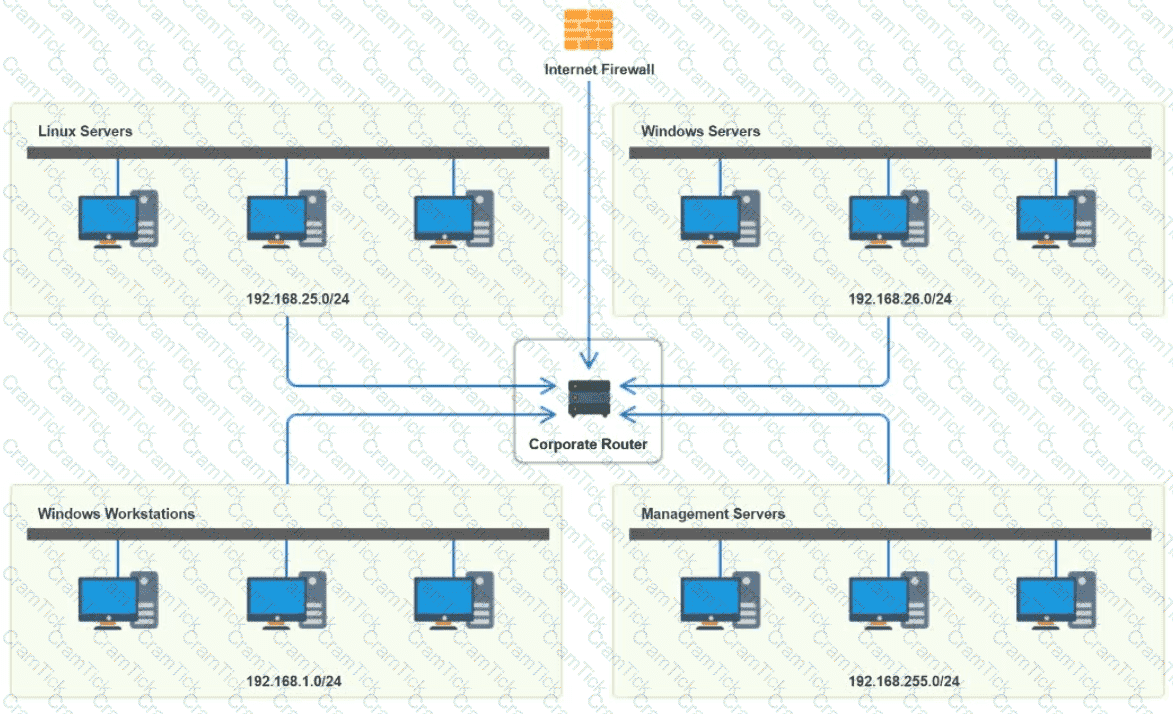
You have been tasked with implementing an ACL on the router that will:
1. Permit the most commonly used secure remote access technologies from the management network to all other local network segments
2. Ensure the user subnet cannot use the most commonly used remote access technologies in the Linux and Windows Server segments.
3. Prohibit any traffic that has not been specifically allowed.
INSTRUCTIONS
Use the drop-downs to complete the ACL
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
A government entity wants to implement technology that can block websites based on country code. Which of the following will best enable this requirement?
A network administrator is conducting an assessment and finds network devices that do not meet standards. Which of the following configurations is considered a set of rules that devices should adhere to?
A network technician is terminating a cable to a fiber patch panel in the MDF. Which of the following connector types is most likely in use?
A network administrator needs to add 255 useable IP addresses to the network. A /24 is currently in use. Which of the following prefixes would fulfill this need?
A network administrator is configuring a network for a new site that will have 150 users. Within the next year, the site is expected to grow by ten users. Each user will have two IP addresses, one for a computer and one for a phone connected to the network. Which of the following classful IPv4 address ranges will be best-suited for the network?
A secure communication link needs to be configured between data centers via the internet. The data centers are located in different regions. Which of the following is the best protocol for the network administrator to use?
A company has been added to an unapproved list because of spam. The network administrator confirmed that a workstation was infected by malware. Which of the following processes did the administrator use to identify the root cause?
Voice traffic is experiencing excessive jitter. A network engineer wants to improve call performance and clarity. Which of the following features should the engineer configure?
Which of the following is the step that a troubleshooter should take immediately after implementing a solution?
Which of the following is created to illustrate the effectiveness of wireless networking coverage in a building?
Which of the following best explains the role of confidentiality with regard to data at rest?
While troubleshooting connectivity issues, a junior network administrator is given explicit instructions to test the host's TCP/IP stack first. Which of the following commands should the network administrator run?
A network administrator needs to monitor data from recently installed firewalls in multiple locations. Which of the following solutions would best meet the administrator's needs?
A wireless technician wants to implement a technology that will allow user devices to automatically navigate to the best available frequency standard. Which of the following technologies should the technician use?
Which of the following is a company most likely enacting if an accountant for the company can only see the financial department's shared folders?
Which of the following is most likely responsible for the security and handling of personal data in Europe?
A network engineer is deploying switches at a new remote office. The switches have been preconfigured with hostnames and STP priority values. Based on the following table:
Switch Name
Priority
core-sw01
24576
access-sw01
28672
distribution-sw01
32768
access-sw02
36864
Which of the following switches will become the root bridge?
After a company installed a new IPS, the network is experiencing speed degradation. A network administrator is troubleshooting the issue and runs a speed test. The results from the different network locations are as follows:
LocationSpeed DownSpeed Up
Wireless laptop4.8 Mbps47.1 Mbps
Wired desktop5.2 Mbps49.3 Mbps
Firewall48.8 Mbps49.5 Mbps
Which of the following is the most likely issue?
A technician needs to identify a computer on the network that is reportedly downloading unauthorized content. Which of the following should the technician use?
A network engineer is now in charge of all SNMP management in the organization. The engineer must use a SNMP version that does not utilize plaintext data. Which of the following is the minimum version of SNMP that supports this requirement?
A major natural disaster strikes a company's headquarters, causing significant destruction and data loss. The company needs to quickly recover and resume operations. Which of the following will a network administrator need to do first?
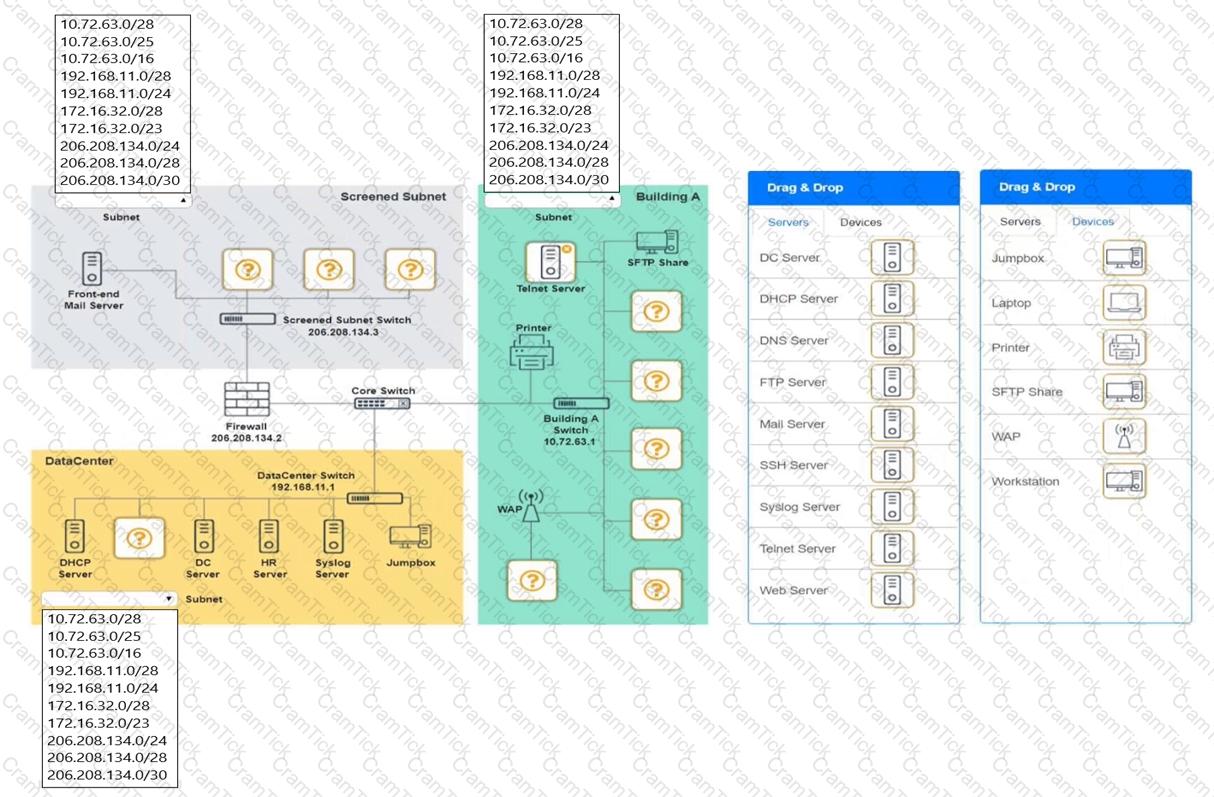
You are tasked with verifying the following requirements are met in order to ensure network security.
Requirements:
Datacenter
Ensure network is subnetted to allow all devices to communicate properly while minimizing address space usage
Provide a dedicated server to resolve IP addresses and hostnames correctly and handle port 53 traffic
Building A
Ensure network is subnetted to allow all devices to communicate properly while minimizing address space usage
Provide devices to support 5 additional different office users
Add an additional mobile user
Replace the Telnet server with a more secure solution
Screened subnet
Ensure network is subnetted to allow all devices to communicate properly while minimizing address space usage
Provide a server to handle external 80/443 traffic
Provide a server to handle port 20/21 traffic
INSTRUCTIONS
Drag and drop objects onto the appropriate locations. Objects can be used multiple times and not all placeholders need to be filled.
Available objects are located in both the Servers and Devices tabs of the Drag & Drop menu.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
A company’s VoIP phone connection is cutting in and out. A senior network engineer is recommending the implementation of a voice VLAN. Which of the following should be configured?
A customer needs six usable IP addresses. Which of the following best meets this requirement?
Which of the following connector types is most commonly associated with Wi-Fi antennas?
Which of the following steps of the troubleshooting methodology comes after testing the theory to determine cause?
A network engineer needs to order cabling to connect two buildings within the same city. Which of the following media types should the network engineer use?
A network manager wants to implement a SIEM system to correlate system events. Which of the following protocols should the network manager verify?
Users are experiencing significant lag while connecting to a cloud-based application during peak hours. An examination of the network reveals that the bandwidth is being heavily utilized. Further analysis shows that only a few users are using the application at any given time. Which of the following is the most cost-effective solution for this issue?
Network administrators are using the Telnet protocol to administer network devices that are on the 192.168.1.0/24 subnet. Which of the following tools should the administrator use to best identify the devices?
A medical clinic recently configured a guest wireless network on the existing router. Since then, guests have been changing the music on the speaker system. Which of the following actions should the clinic take to prevent unauthorized access? (Select two).
A network architect is implementing an off-premises computing facility and needs to ensure that operations will not be impacted by major outages. Which of the following should the architect consider?
A network administrator for a small office is adding a passive IDS to its network switch for the purpose of inspecting network traffic. Which of the following should the administrator use?
A security administrator is creating a new firewall object for a device with IP address 192.168.100.1/25. However, the firewall software only uses dotted decimal notation in configuration fields. Which of the following is the correct subnet mask to use?
A firewall administrator is mapping a server's internal IP address to an external IP address for public use. Which of the following is the name of this function?
A user tries to visit a website, but instead of the intended site, the page displays vmw.cba.com. Which of the following should be done to reach the correct website?
A network technician needs to resolve some issues with a customer's SOHO network.
The customer reports that some of the devices are not connecting to the network, while others appear to work as intended.
INSTRUCTIONS
Troubleshoot all the network components and review the cable test results by Clicking on each device and cable.
Diagnose the appropriate component(s) by identifying any components with a problem and recommend a solution to correct each problem.
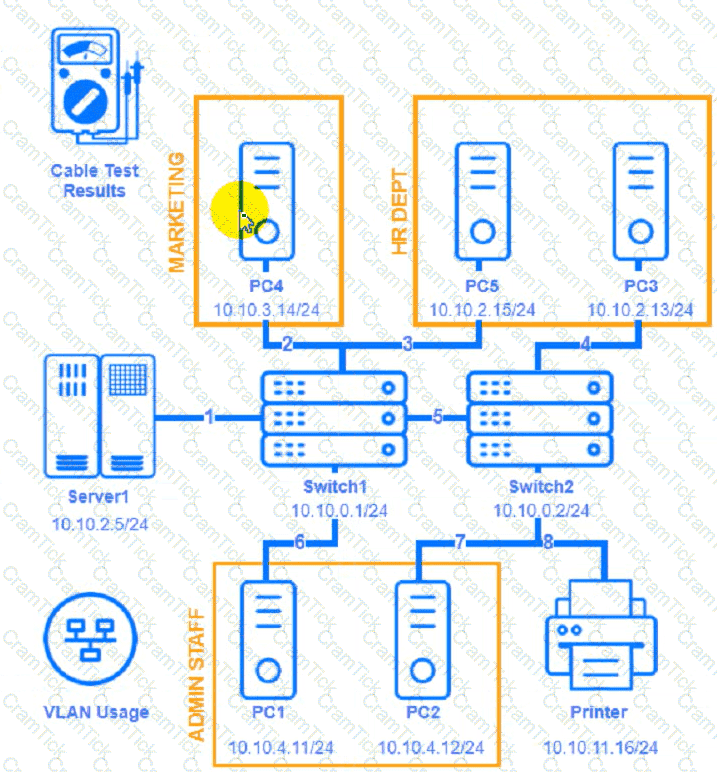


Cable Test Results:
Cable 1:
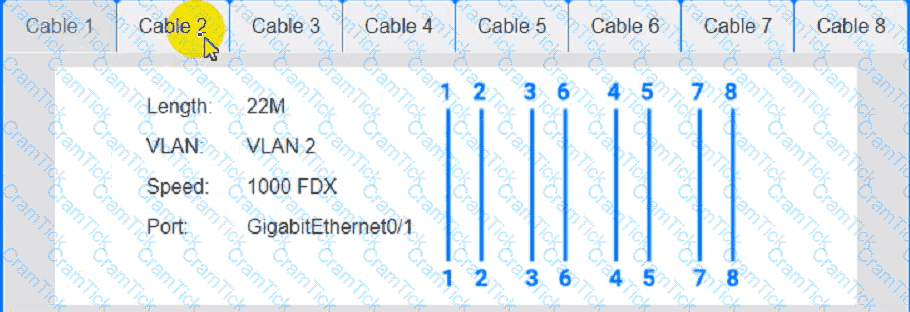
Cable 2:
Cable 3:
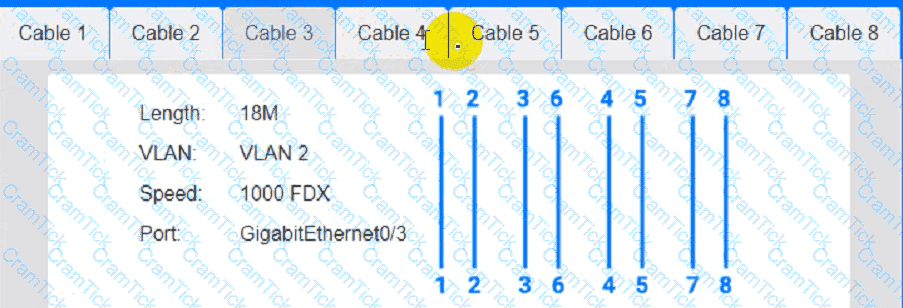
Cable 4:
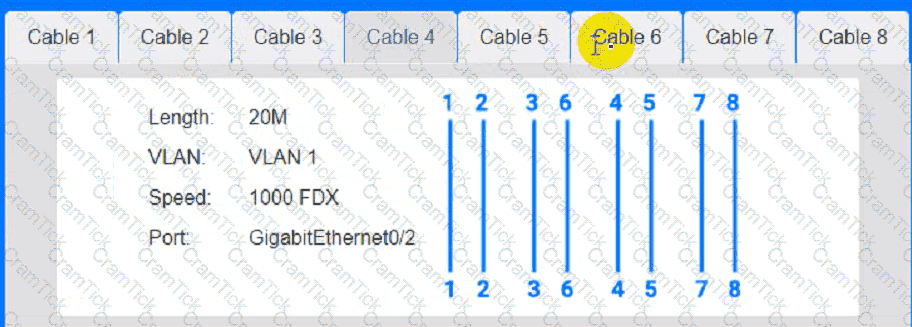
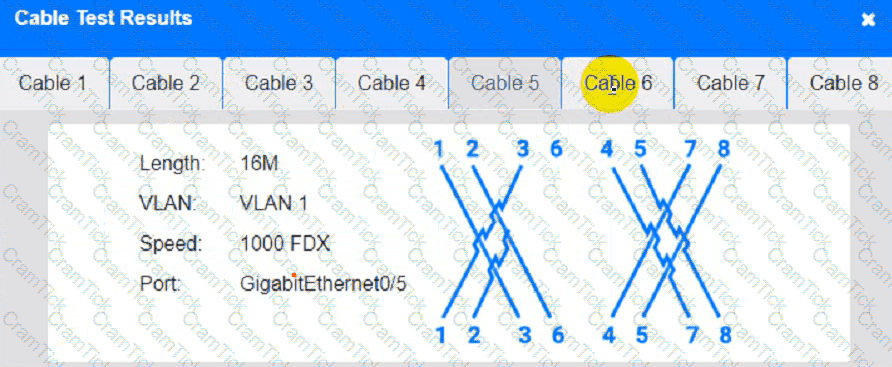
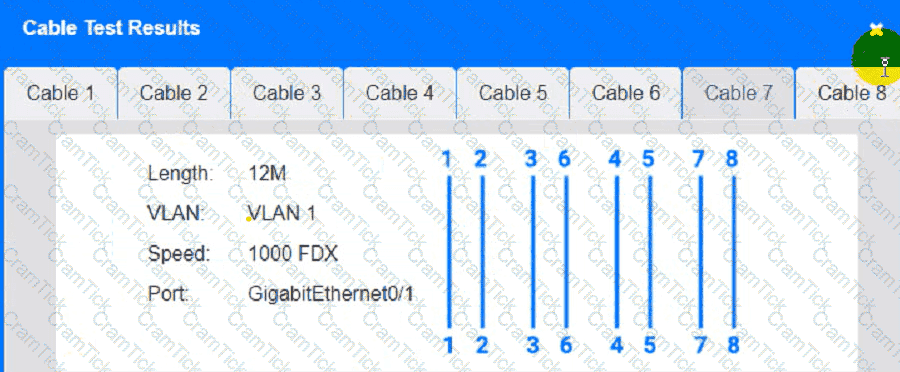
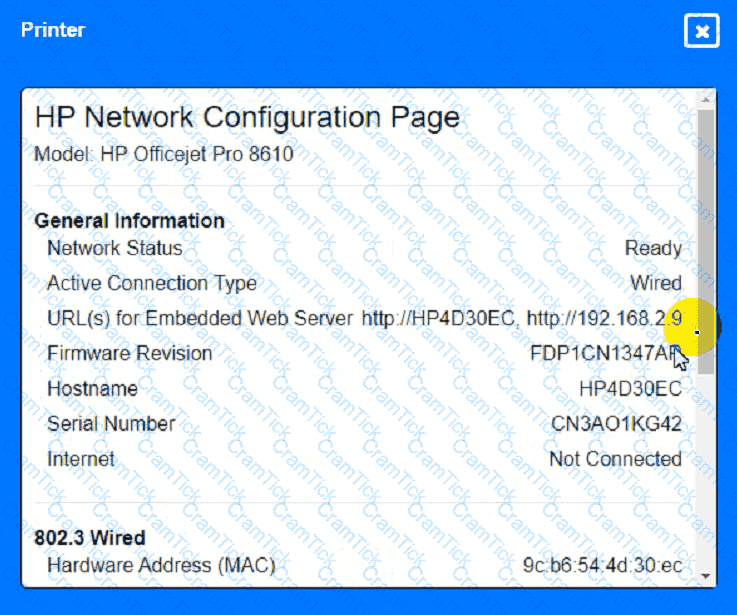
A technician is planning an equipement installation into a rack in a data center that practices hot aisle/cold aise ventilation. Which of the following directions should the equipement exhaust face when installed in the rack?
A network engineer runs ipconfig and notices that the default gateway is 0.0.0.0. Which of the following address types is in use?
Which of the following troubleshooting steps would provide a change advisory board with the information needed to make a decision?
Which of the following disaster recovery metrics is used to describe the amount of data that is lost since the last backup?
Which of the following is most commonly associated with many systems sharing one IP address in the public IP-addressing space?
Which of the following steps of the troubleshooting methodology should a technician take to confirm a theory?
A network technician is troubleshooting a faulty NIC and tests the theory. Which of the following should the technician do next?
Which of the following concepts describes the idea of housing different customers in the same public cloud data center?
A network administrator is setting up a firewall to protect the organization’s network from external threats. Which of the following should the administrator consider first when configuring the firewall?
Which of the following best describes the transmission format that occurs at the transport layer over connectionless communication?
Before using a guest network, an administrator requires users to accept the terms of use Which of the following is the best way to accomplish this goal?
Which of the following is the most likely reason an insurance brokerage would enforce VPN usage?
Which of the following fiber connector types is the most likely to be used on a network interface card?
A company recently rearranged some users' workspaces and moved several users to previously used workspaces. The network administrator receives a report that all of the users who were moved are having connectivity issues. Which of the following is the MOST likely reason?
A company’s Chief Information Security Officer requires that servers and firewalls have accurate timestamps when creating log files so that security analysts can correlate events during incident investigations. Which of the following should be implemented?
Which of the following network traffic type is sent to all nodes on the network?
A systems administrator is investigating why users cannot reach a Linux web server with a browser but can ping the server IP. The server is online, the web server process is running, and the link to the switch is up. Which of the following commands should the administrator run on the server first?
Which of the following routing technologies uses an attribute list for path selection?
Which of the following explains what happens if a packet is lost in transit when using UDP?
A network administrator is notified that a user cannot access resources on the network. The network administrator checks the physical connections to the workstation labeled User 3 and sees the Ethernet is properly connected. However, the network interface’s indicator lights are not blinking on either the computer or the switch. Which of the following Is the most likely cause?
Which of the following kinds of targeted attacks uses multiple computers or bots to request the same resource repeatedly?
Which of the following ports should a network administrator enable for encrypted login to a network switch?
Which of the following is the best networking appliance for interconnecting multiple logical networks and forwarding data packets between them while minimizing latency?
A company is purchasing a 40Gbps broadband connection service from an ISP. Which of the following should most likely be configured on the 10G switch to take advantage of the new service?
Which of the following should a company implement in order to share a single IP address among all the employees in the office?
A junior network technician at a large company needs to create networks from a Class C address with 14 hosts per subnet. Which of the following numbers of host bits is required?
A network administrator is troubleshooting issues with a DHCP server at a university. More students have recently arrived on campus, and the users are unable to obtain an IP address. Which of the following should the administrator do to address the issue?
Which of the following should be used to obtain remote access to a network appliance that has failed to start up properly?
A network administrator needs to implement a solution to filter access to the internet. Which of the following should the administrator most likely implement?
A user submits an escalated ticket regarding failed logins on their laptop. The user states that the time displayed on the laptop is incorrect. An administrator thinks the issue is related to the NTP. Which of the following should the administrator do next?
A network engineer configures a new switch and connects it to an existing switch for expansion and redundancy. Users immediately lose connectivity to the network. The network engineer notes the following spanning tree information from both switches:
Switch 1
Port State Cost
1 Forward 2
2 Forward 2
Switch 2
Port State Cost
1 Forward 2
2 Forward 2
Which of the following best describes the issue?
Which of the following protocols is used to route traffic on the public internet?
An investment bank is seeking a DR backup solution. Which of the following provides the most cost-effective backup site?
A detective is investigating an identity theft case in which the target had an RFID-protected payment card issued and compromised in the same day. The only place the target claims to have used the card was at a local convenience store. The detective notices a video camera at the store is placed in such a way that customers' credentials can be seen when they pay. Which of the following best explains this social engineering technique?
A network administrator suspects users are being sent to malware sites that are posing as legitimate sites. The network administrator investigates and discovers that user workstations are configured with incorrect DNS IP addresses. Which of the following should the network administrator implement to prevent this from happening again?
Which of the following requires network devices to be managed using a different set of IP addresses?
A user cannot access an external server for a client after connecting to a VPN. Which of the following commands would a support agent most likely use to examine the issue? (Select two).
Which of the following is the correct order of components in a bottom-up approach for the three-tier hierarchical model?
A network administrator is connecting two Layer 2 switches in a network. These switches must transfer data in multiple networks. Which of the following would fulfill this requirement?
Which of the following types of attacks is most likely to occur after an attacker sets up an evil twin?
Which of the following IP transmission types encrypts all of the transmitted data?
Which of the following attacks would most likely cause duplicate IP addresses in a network?
A network engineer needs to deploy an access point at a remote office so that it will not communicate back to the wireless LAN controller. Which of the following deployment methods must the engineer use to accomplish this task?
Which of the following is the most cost-effective way for a network administrator to establish a persistent, secure connection between two facilities?
A network technician is troubleshooting network latency and has determined the issue to be occuring two network switches( Switch10 and Switch11). Symptoms reported included poor video performance and slow file copying. Given the following informtion:
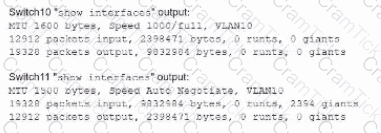
Which of the following should the technician most likely do to resolve the issue?
Which of the following is the most cost-effective way to safely expand outlet capacity in an IDF?
A company is hosting a secure that requires all connections to the server to be encrypted. A junior administrator needs to harded the web server. The following ports on the web server. The following ports on the web server are open:

Which of the following ports should be disabled?
A customer wants to cache commonly used content to reduce the number of full page downloads from the internet. Which of the following should the network administrator recommend?
A network manager connects two switches together and uses two connecting links. Which of the following configurations will prevent Layer 2 loops?
A network engineer receives a vendor alert regarding a vulnerability in a router CPU. Which of the following should the engineer do to resolve the issue?
A network administrator needs to assign IP addresses to a newly installed network. They choose 192.168.1.0/24 as their network address and need to create three subnets with 30 hosts on each subnet. Which of the following is a valid subnet mask that will meet the requirements?
During a recent security assessment, an assessor attempts to obtain user credentials by pretending to be from the organization's help desk. Which of the following attacks is the assessor using?
A newly opened retail shop uses a combination of new tablets, PCs, printers, and legacy card readers. Which of the following wireless encryption types is the most secure and compatible?
Which of the following is the greatest advantage of maintaining a cold DR site compared to other DR sites?
Which of the following cable types allows the use of QSFP ports without requiring transceivers?
Which of the following physical installation factors is the most important when a network switch is installed in a sealed enclosure?
Which of the following disaster recovery concepts is calculated by dividing the total hours of operation by the total number of units?
Which of the following is the next step to take after successfully testing a root cause theory?
A network technician needs to install patch cords from the UTP patch panel to the access switch for a newly occupied set of offices. The patch panel is not labeled for easy jack identification. Which of the following tools provides the easiest way to identify the appropriate patch panel port?
A network administrator is deploying a new switch and wants to make sure that the default priority value was set for a spanning tree. Which of the following values would the network administrator expect to see?
Which of the following steps in the troubleshooting methodology would be next after putting preventive measures in place?
Which of the following allows an organization to map multiple internal devices to a single external-facing IP address?
Which of the following connectors allows a singular QSFP transceiver to have several physical connections?
After running a Cat 8 cable using passthrough plugs, an electrician notices that connected cables are experiencing a lot of cross talk. Which of the following troubleshooting steps should the electrician take first?
Which of the following must be implemented to securely connect a company's headquarters with a branch location?
A network administrator deploys new network hardware. While configuring the network monitoring server, the server could authenticate but could not determine the specific status of the hardware. Which of the following would the administrator most likely do to resolve the issue?
An employee in a corporate office clicks on a link in an email that was forwarded to them. The employee is redirected to a splash page that says the page is restricted. Which of the following security solutions is most likely in place?
A network administrator needs to divide 192.168.1.0/24 into two equal halves. Which of the following subnet masks should the administrator use?
A network technician is configuring the company’s network of 100 Mbps Layer 2 switches. The technician wants increased throughput for the uplinks between switches. The technician connects multiple redundant links between the switches. Which of the following should the technician configure?


