In thefirewall hot standby scenario, in which of the following conditions will the local deviceproactively send VGMP packets?
On a router,SRv6is enabled, and the configurations shown below are performed. Which of the following statements about the configurations are correct?
[Router-segment-routing-ipv6] locator srv6_locator1 ipv6-prefix 2001:DB8:ABCD::/64 static 32
Whenstatic IPsec VPNis used for WAN interconnection in theHuawei CloudCampus Solution, theAP, Router, and ____can be used as egress devices.
Exhibit:
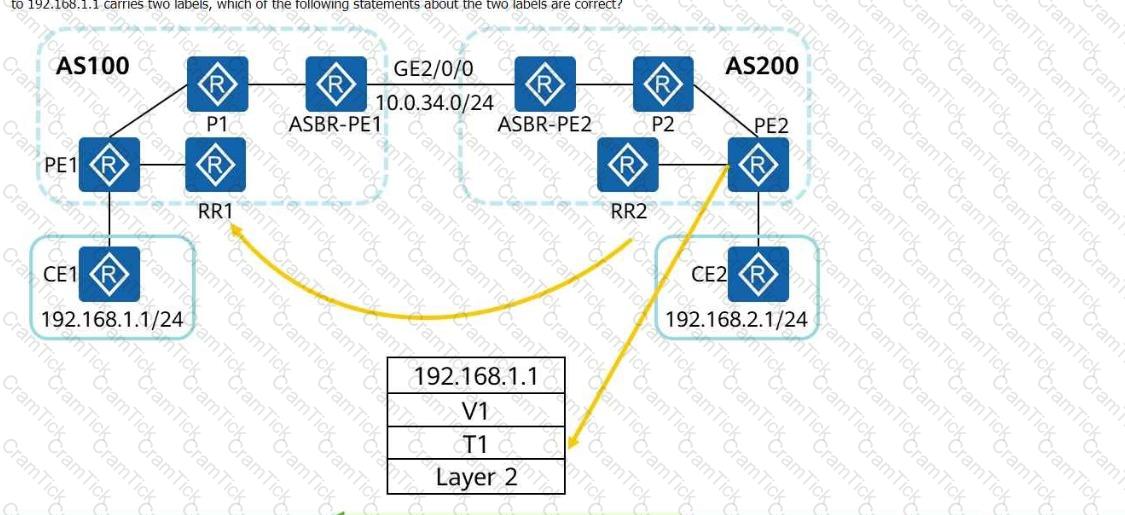
The following figure shows the inter-AS MPLS VPN Option C (solution 2). RRs are deployed, and no traffic passes through the RRs during forwarding. If a data packet sent from PE2 to192.168.1.1carries two labels, which of the following statements about the two labels are correct?
A network administrator runs thedisplay telemetry subscriptioncommand on a device to check telemetry subscription information. The command output is as follows:
[~CE] display telemetry subscription
Sub-name : Sub1
Sensor group:
Sensor-name Sample-interval(ms) State
Sensor1 1000 RESOLVED
Destination group:
Dest-name Dest-IP Dest-port State Vpn-name Protocol
Dest1 192.168.56.1 20000 RESOLVED - GRPC
Sub-state : PASSIVE
Total subscription number is : 1
Which of the following statements is incorrect?
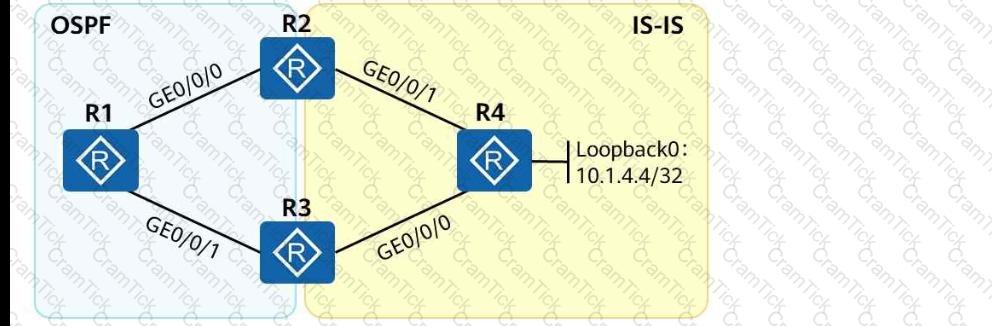
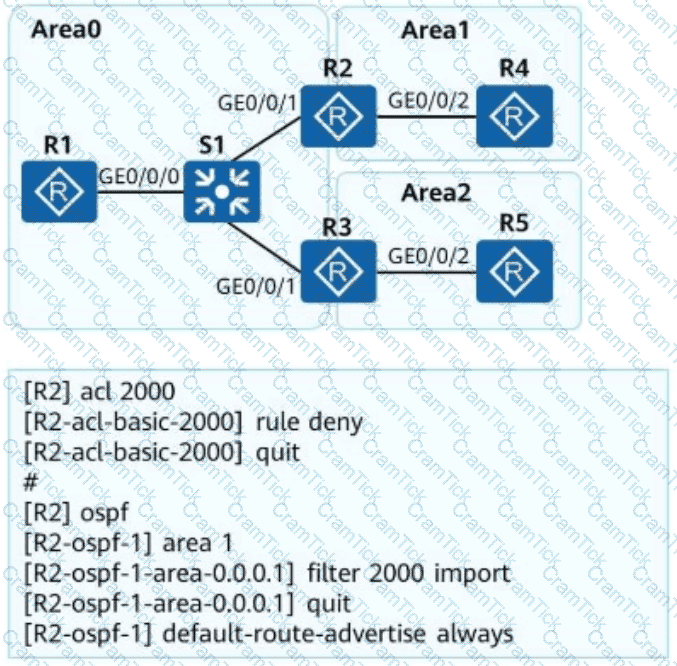
As shown in the following figure, an engineer tests network interconnection between two branches. To implement network interconnection,OSPFis deployed onR1, R2, and R3of branch 1, andIS-ISis deployed onR2, R3, and R4of branch 2. Which of the following operations needs to be performed to allowR1 to access R4's loopback interface address?
In the Huawei SD-WAN Solution, the topologies of different VNs must be the same.
Which of the following statements is incorrect about Authentication Header (AH)?
In Huawei SD-WAN Solution, which of the following tunneling technologies is used to establish data channels?
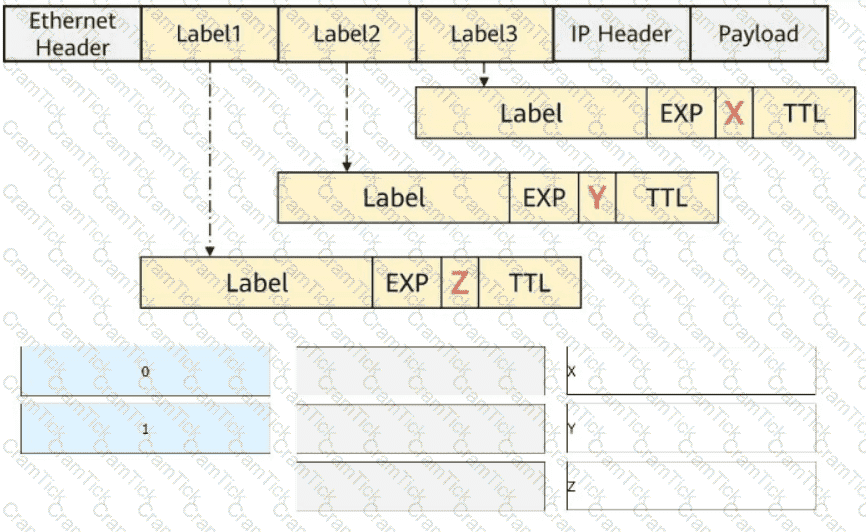
The figure shows a packet that contains three label headers. Select the values (in decimal notation) of the X, Y, and Z fields, respectively.
Which of the following roles is NOT a core role in Huawei's Free Mobility solution?
OSPF is deployed on a campus network to implement network interconnection. The LSDB of R2 is shown in the figure.
What can be determined from the LSDB?
An engineer often remotely logs in to the device to check the device status. The engineer can use the Python Paramiko and telnetlib libraries to implement automatic remote login through Python scripts. The remote login implemented using telnetlib is more secure.
At the NETCONF content layer, the
In the following figure, all routers are running OSPF. Given this, which of the following statements is correct?
In thesmall and midsize campus network designbased on theHuawei CloudCampus Solution, when over100 branchesneed to communicate with each other, which of the following interconnection networking models is recommended?
An SRv6 Policy can be either statically configured on a device or dynamically generated by the controller and then delivered to the device.
Which of the following fields is added to BGP4+ Update packets to advertise IPv6 routes?
Port isolation can be deployed on an Ethernet network to implement both Layer 2 communication and Layer 3 isolation, making the networking more flexible.
On a campus network, which of the following problems may occur when you manually create a static VXLAN tunnel?
In a scenario where a VXLAN tunnel is dynamically established through BGP EVPN, which of the following statements about symmetric IRB forwarding are correct?
On a virtualized network deployed using iMaster NCE-Campus, after creating VNs, you need to configure inter-VN communication. Which of the following configurations is used to achieve VN communication?
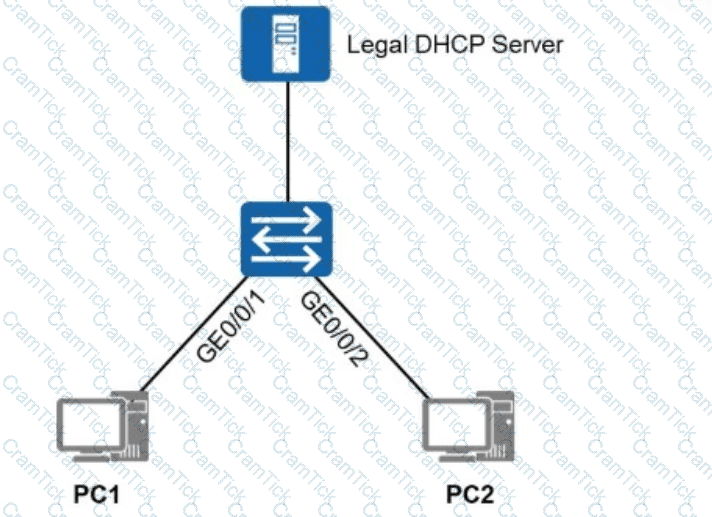
To allow only authorized users (users who obtain IP addresses through authorized DHCP servers or use specified static IP addresses) to access the network shown in the figure, which of the following solutions can be used?
Which of the following intelligent traffic steering policies can be used to fully utilize link bandwidth and implement link bandwidth-based load balancing on an enterprise network with multiple links?
In the figure,SR-MPLSis enabled onR1, R2, and R3. TheSRGB (Segment Routing Global Block) rangeonR3is from20000 to 21000, and theprefix SID indexconfigured on theloopback1 interface of R3 is 30.
In this case, theMPLS label corresponding to the loopback1 interface of R3 is _____.
(Enter anArabic numeralwithout symbols.)
AH is an IP-based transport-layer protocol. The protocol number is _____. (Enter only digits.)
Which of the following statements are correct about the authentication protocols used inPortal authentication?
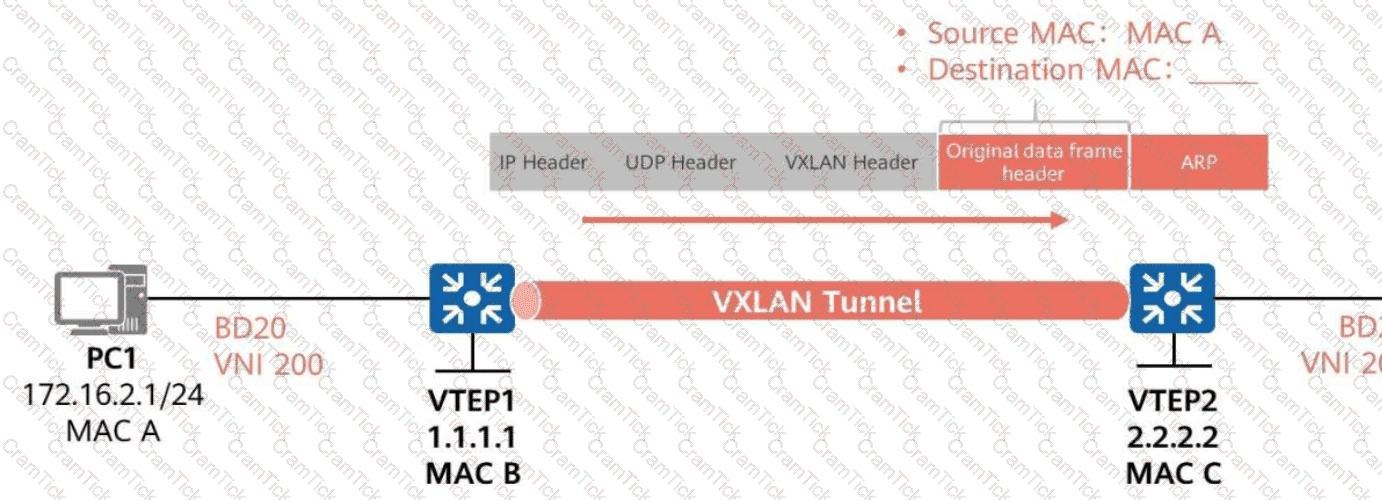
As shown in the figure,ARP broadcast suppression is enabled on VTEP1inBD 20 (VNI 200).
VTEP1 learns ARP informationaboutPC2 through BGP EVPN routes.
WhenVTEP1 forwards the ARP request for PC1’s MAC address to VTEP2,
What is the destination MAC address of the inner data frame?
Which of the following statements regarding OSPF neighbor relationship faults is incorrect?
MPLS supports Forwarding Equivalence Class (FEC). Which of the following cannot be used as a FEC allocation standard?
IPsec uses an asymmetric encryption algorithm to encrypt the symmetric algorithm key, which it uses to encrypt/decrypt data, ensuring security and performance.
The BGP ORF function can be used to control the maximum number of routes that can be sent by a BGP peer. To achieve this, which of the following tools is used to send such a route list to BGP peers?
Which of the following statements is correct about the differences between NSR and NSF?
iMaster NCE-CampusInsightuses SNMP technology to collect metrics and logs of network devices and detects network exceptions based on real service traffic.
The channelized sub-interface and FlexE technologies both can be used to implement network slicing, but the application scenarios of the two technologies are slightly different. Which of the following statements about the two technologies are correct?
IS-IS supports multi-instance and multi-process. Which of the following statements are correct about IS-IS multi-instance and multi-process?
As shown in the figure, when PE1 receives an ARP request packet, it forwards the packet to PE4. The packet then carries two labels. The label value 201 is carried by the EVPN Type ____ route. (Enter only digits.)
What can be determined from the following figure?
Public Routing Table : ISIS
Summary Count: 6
ISIS Routing Table's Status : < Active >
Summary Count: 6
Destination : 3000:FDEA::4
NextHop : FE80::2E0:FCFF:FE98:2577
Cost : 20
Interface : GigabitEthernet0/0/1
PrefixLength : 128
Preference : 15
Protocol : ISIS-L2
Flags : D
Which of the following protocols is used in the Huawei SD-WAN Solution to report device performance data?
In the gRPC-based telemetry protocol, the data model layer consists of theRPC layer,telemetry layer, andservice data layer. Drag the.proto fileto the layer where the file should be located.
On a small- or medium-sized campus network deployed based on the Huawei CloudCampus Solution, an AR functioning as the egress gateway supports web-based network management, registration center query, and DHCP Option 148-based deployment, but does not support CLI-based deployment.
BGP EVPN can be used as the VXLAN control plane protocol to completely prevent traffic flooding, such as broadcast ARP packets, on the VXLAN network.
In an MPLS VPN network, two-layer MPLS labels are added into data packets before they are transmitted over the public network. Which of the following statements regarding data packet processing are correct?
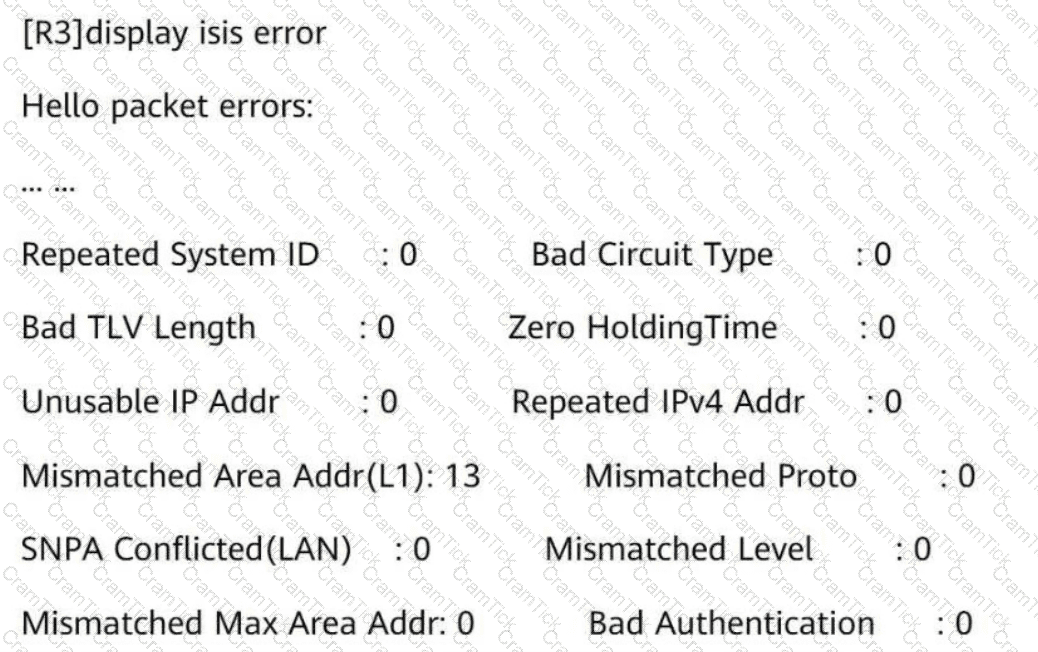
The IS-IS Level-1 neighbor relationship is not established betweenR3andR4. Referring to the following information, what is the possible cause?
In a scenario where a VXLAN tunnel is dynamically established through BGP EVPN, which of the following BGP EVPN routes is used to advertise MAC addresses, ARP entries, and IRB routes?
On an SR-MPLS network, manually configured prefix SIDs on different devices may conflict with each other. Assume that there are four routes (prefix/mask SID) as follows. Which of the following routes will be selected according to the conflict handling principle?
Which of the following statements aboutOPS (Open Programmability System) application scenariosisincorrect?
MPLS supports forwarding equivalence class (FEC). Which of the following cannot be used as an FEC allocation standard?
An engineer uses two routers to perform IPv6 tests and wants to use OSPFv3 for IPv6 network connectivity. Which of the following OSPFv3 configurations for R1 are correct?
The path of an SR-MPLS TE tunnel can be calculated by the controller or tunnel ingress.
SSH connections are usually established based on TCP/IP connections. In specific cases, SSH connections can be established based on UDP connections.
In DU label advertisement mode, if the liberal label retention mode is used, the device reserves labels received from all the LDP peers regardless of whether the LDP peer is the optimal next hop for reaching the destination network.
On a VXLAN-based virtualized campus network, BGP EVPN can be used as the control plane protocol. Which of the following EVPN route types are not used in the virtualized campus network scenario?
Telemetry data must be encoded in GPB binary format. This format reduces the number of bytes in telemetry messages and improves the transmission efficiency compared with messages encoded in JSON format.
In theHuawei CloudCampus Solution, which of the following devices can go online through theregistration query center?
If ISIS is used to transmit SIDs on an SR network, the node SIDs advertised by a Level-2 router are transmitted only within the same area.
In the firewall hot standby scenario, when VGMP works in load balancing mode, which of the following functions must be enabled on the firewalls to prevent the return traffic from being discarded because it does not match any session entry in the case of inconsistent forward and return paths?
Which of the following statements aboutBIER (Bit Index Explicit Replication) and PIM (Protocol Independent Multicast)are correct?
The ________ command can be run to completely isolate Layer 2 and Layer 3 of different interfaces in a VLAN. (Use lowercase letters to supplement the command, which cannot be abbreviated.)
SR-MPLS uses IGP extensions to advertise labels and reserve bandwidth to support high-bandwidth services.
A network administrator runs the display telemetry destination command on a device to check information about a destination group that sampled data is sent to. The command output is as follows. Which of the following statements is incorrect?
[~CE-telemetry-sensor-group-Sensor1]display telemetry destination
Dest-name Dest-addr Dest-port State Vpn-name Protocol
Dest1 192.168.56.1 20000 RESOLVED - GRPC
When static IPsec VPN is used for WAN interconnection in the Huawei CloudCampus Solution, the AP, Router, and _____ can be used as egress devices. (Use full spelling with the first letter capitalized.)
Which of the following headend behaviors can insert SRHs into IPv6 packets? (Select All that Apply)
Which of the following commands are mandatory for configuring an OSPF-based SR-MPLS TE tunnel? (Select All that Apply)
On acampus network,iMaster NCE-Campusis used to deploy twoVNs (Virtual Networks):R&D VNandMarketing VN. Users in these two VNs belong to twoseparate security groups.
The campus network requiresR&D personnel and sales personnel to communicate with each other. To meet this requirement, which of the following tasks does a network administrator need to perform?
OSPF is deployed on a campus network to implement network interconnection. An engineer configures R2 as shown in the figure. Which of the following statements is incorrect about LSAs on the OSPF network?
Which of the following statements about the multicast address used by OSPFv3 are correct?
Congestion management technology can be used to discard data packets in the buffer queue to prevent the buffer queue from being exhausted.
Which of the following are application optimization functions in the Huawei SD-WAN Solution?
When an NVE encapsulates a data frame into a VXLAN packet, information of which of the following protocols is encapsulated between the outer IP header and the VXLAN header?
Among NETCONF operations, the
On a VXLAN-based virtualized network, if the fabric networking mode is centralized gateway networking, the gateway is located on the _____ device. (Capitalize the first letter.)
New IS-IS TLVs are used to carry IPv6 addresses and reachability information to support IPv6 route processing and calculation.
Which of the following statements is incorrect about the user authentication points on the network?
When you configure a virtualized campus network on iMaster NCE-Campus and enable external networks to connect to the Internet, iMaster NCE-Campus will automatically deliver a specific route to direct traffic to the corresponding external network.
Huawei Open Programmability System (OPS)usesstandard HTTP methodsto accessmanaged objectsand manage network devices.
Which of the followingHTTP methodsis used toconfigure the value of a network device’s managed object?
What can be determined from the following figure?
Total Number of Routes: 2
*>i Network : 3002::3
NextHop : 3000:FDEA::3
MED : 0
Path/Orgn : i
*>i Network : 3002::4
NextHop : 3000:FDEA::3
MED : 0
PrefixLen : 128
LocPrf : 100
PrefVal : 0
Path/Orgn : 65001 i
An enterprise has three types of services. Voice and video services are key services and need to be guaranteed, and FTP services are non-key services. Which of the following scheduling modes is optimal for satisfying the service requirements?
Which of the following statements about static VXLAN tunnel configuration are correct?
Exhibit:
A loop occurs because Spanning Tree Protocol (STP) is not enabled on the network. Which of the following symptoms may occur?
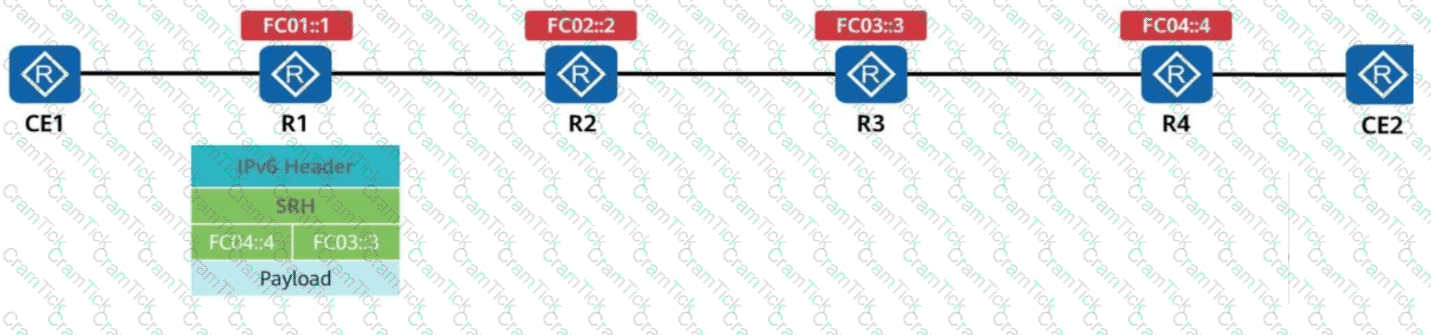
R1 receives a common IPv6 packet from the CE and generates a packet carrying the SRH (Segment Routing Header), as shown in the figure. The packet is forwarded along the path R1 → R2 → R3 → R4. Identify the node type of each device based on their role in SRv6 processing.

On the bearer WAN shown in the figure,SR (Segment Routing)is deployed, and the controller is used to compute paths. Drag network technologies on the left to the corresponding application locations on the right.

HCIE-Datacom | H12-891_V1.0 Questions Answers | H12-891_V1.0 Test Prep | HCIE-Datacom V1.0 Questions PDF | H12-891_V1.0 Online Exam | H12-891_V1.0 Practice Test | H12-891_V1.0 PDF | H12-891_V1.0 Test Questions | H12-891_V1.0 Study Material | H12-891_V1.0 Exam Preparation | H12-891_V1.0 Valid Dumps | H12-891_V1.0 Real Questions | HCIE-Datacom H12-891_V1.0 Exam Questions