In which phase of secure development lifecycle the threat modeling is performed?
Which of the following configuration settings in server.xml will allow Tomcat server administrator to impose limit on uploading file based on their size?
Which of the following method will you use in place of ex.printStackTrace() method to avoid printing stack trace on error?
James is a Java developer working INFR INC. He has written Java code to open a file, read it line by line and display its content in the text editor. He wants to ensure that any unhandled exception raised by the code should automatically close the opened file stream. Which of the following exception handling block should he use for the above purpose?
Jacob, a Security Engineer of the testing team, was inspecting the source code to find security vulnerabilities.
Which type of security assessment activity Jacob is currently performing?
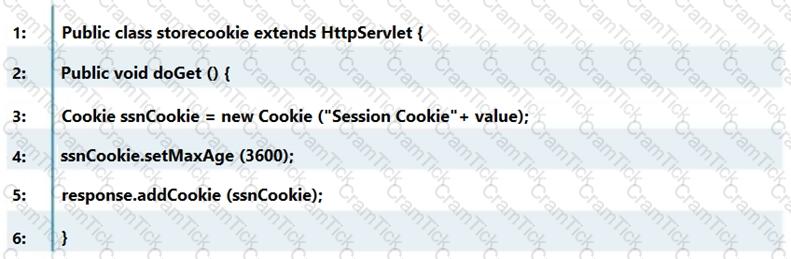
Which line of the following example of Java Code can make application vulnerable to a session attack?
Alice works as a Java developer in Fygo software Services Ltd. He is given the responsibility to design a bookstore website for one of their clients. This website is supposed to store articles in .pdf format. Alice is advised by his superior to design ArticlesList.jsp page in such a way that it should display a list of all the articles in one page and should send a selected filename as a query string to redirect users to articledetails.jsp page.
Alice wrote the following code on page load to read the file name.
String myfilename = request.getParameter("filename");
String txtFileNameVariable = myfilename;
String locationVariable = request.getServletContext().getRealPath("/");
String PathVariable = "";
PathVariable = locationVariable + txtFileNameVariable;
BufferedInputStream bufferedInputStream = null;
Path filepath = Paths.get(PathVariable);
After reviewing this code, his superior pointed out the security mistake in the code and instructed him not repeat the same in future. Can you point the type of vulnerability that may exist in the above code?
Which of the following elements in web.xml file ensures that cookies will be transmitted over an encrypted channel?


