In which of the following incident handling and response stages, the root cause of the incident must be found from the forensic results?
Juliea a SOC analyst, while monitoring logs, noticed large TXT, NULL payloads.
What does this indicate?
John, SOC analyst wants to monitor the attempt of process creation activities from any of their Windows endpoints.
Which of following Splunk query will help him to fetch related logs associated with process creation?
Which of the following technique protects from flooding attacks originated from the valid prefixes (IP addresses) so that they can be traced to its true source?
Which of the following can help you eliminate the burden of investigating false positives?
An attacker exploits the logic validation mechanisms of an e-commerce website. He successfully purchases a product worth $100 for $10 by modifying the URL exchanged between the client and the server.
Original URL: http://www.buyonline.com/product.aspx?profile=12 &debit=100 Modified URL: http://www.buyonline.com/product.aspx?profile=12 &debit=10
Identify the attack depicted in the above scenario.
An organization is implementing and deploying the SIEM with following capabilities.
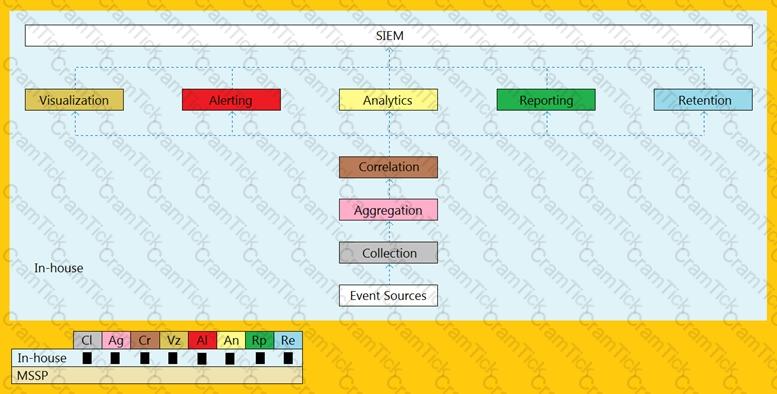
What kind of SIEM deployment architecture the organization is planning to implement?
Which of the following framework describes the essential characteristics of an organization's security engineering process that must exist to ensure good security engineering?
Which of the following threat intelligence helps cyber security professionals such as security operations managers, network operations center and incident responders to understand how the adversaries are expected to perform the attack on the organization, and the technical capabilities and goals of the attackers along with the attack vectors?
Which of the following is a default directory in a Mac OS X that stores security-related logs?
Jony, a security analyst, while monitoring IIS logs, identified events shown in the figure below.

What does this event log indicate?
Bonney's system has been compromised by a gruesome malware.
What is the primary step that is advisable to Bonney in order to contain the malware incident from spreading?
Identify the event severity level in Windows logs for the events that are not necessarily significant, but may indicate a possible future problem.
Sam, a security analyst with INFOSOL INC., while monitoring and analyzing IIS logs, detected an event matching regex /\\w*((\%27)|(\’))((\%6F)|o|(\%4F))((\%72)|r|(\%52))/ix.
What does this event log indicate?
If the SIEM generates the following four alerts at the same time:
I.Firewall blocking traffic from getting into the network alerts
II.SQL injection attempt alerts
III.Data deletion attempt alerts
IV.Brute-force attempt alerts
Which alert should be given least priority as per effective alert triaging?
Daniel is a member of an IRT, which was started recently in a company named Mesh Tech. He wanted to find the purpose and scope of the planned incident response capabilities.
What is he looking for?
Rinni, SOC analyst, while monitoring IDS logs detected events shown in the figure below.

What does this event log indicate?
Which of the following attack can be eradicated by converting all non-alphanumeric characters to HTML character entities before displaying the user input in search engines and forums?
Chloe, a SOC analyst with Jake Tech, is checking Linux systems logs. She is investigating files at /var/log/ wtmp.
What Chloe is looking at?
Which of the following is a correct flow of the stages in an incident handling and response (IH&R) process?
Which of the following steps of incident handling and response process focus on limiting the scope and extent of an incident?
What is the process of monitoring and capturing all data packets passing through a given network using different tools?
Banter is a threat analyst in Christine Group of Industries. As a part of the job, he is currently formatting and structuring the raw data.
He is at which stage of the threat intelligence life cycle?
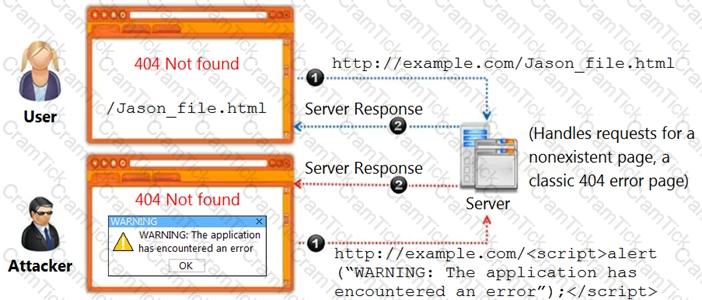
Identify the type of attack, an attacker is attempting on www.example.com website.